| Document ID | CPENG05 |
| Product | Security Gateway |
| Version | R80.10, R80.20, R80.30, R80.40 |
| OS | Gaia |
| Platform / Model | All |
Topology

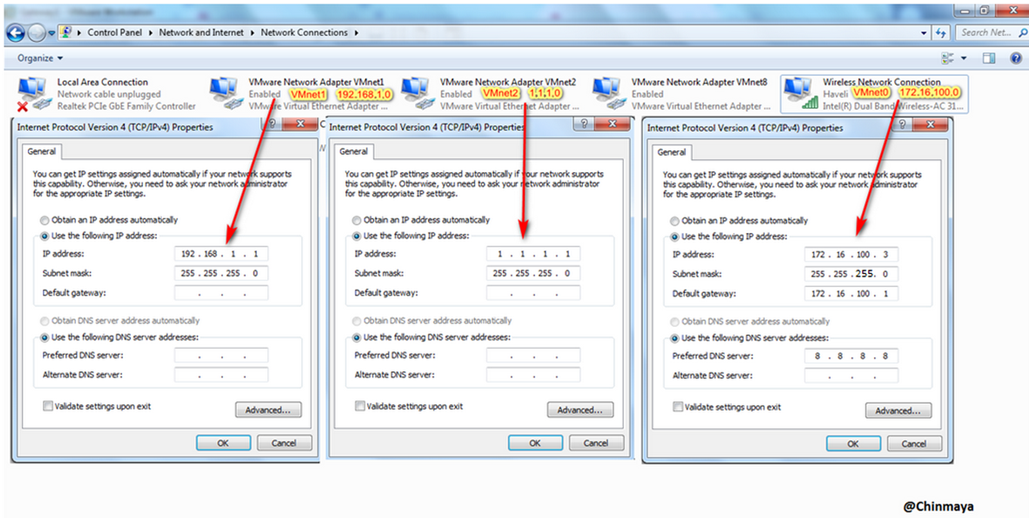
To create a Cluster setup it required 3 interface that need to be configure first.
As per the above diagram we required 3 VMnet (Vmware Networks) to configure three interface.
VMnet1 : 192.168.1.0/24
VMnet2 : 1.1.1.0/24
VMnet0 : 172.16.100.0/24
IP Address Details
Gateway 1 (Active) IP : Internal (eth0) –> 192.168.1.2/24 || External (eth2) –>172.16.100.121/24
Gateway 2 (Standby) IP : Internal (eth0) –> 192.168.1.3/24 || External (eth2) –>172.16.100.122/24
Cluster VIP (Virtual IP) : Internal –> 192.168.1.5/24 || External –> 172.16.100.125/24
Sync IP : Active Gateway (eth1) —> 1.1.1.2/24 || Standby Gateway (eth1) —> 1.1.1.3/24 (NO VIP Required)
Route
Internal LAN (192.168.1.0/24) —-> Default Gateway (VIP : 192.168.1.5/24)
Gateway IP (172.16.100.121/24 & 172.16.100.122/24) —> Default Gateway (VIP:172.16.100.1/24)
HOST Machine (Where VMware is running) —> 192.168.1.1/24
VMNet Details
VMnet0 : Auto-Bridging : External : 172.16.100.0/24
VMnet1 : Host-Only : Internal : 192.168.1.0/24
VMnet2 : Host-Only : Sync : 1.1.1.0/24
STEP 01: Check the IP address of the HOST machine where the VMware is running .By default it take First Host address.
NOTE : VMnet0 is auto bridge ,so basically that connected to my Wifi Network so I can’t give 172.16.100.1 because that already assign to my WiFi Router address so 172.16.100.1 is our default gateway.(Check your “Route Router IP Address”) so basically I assign three free IP address of my WiFi network which I define as External Interface
Check the First Host ID of three VM Network Adapter.
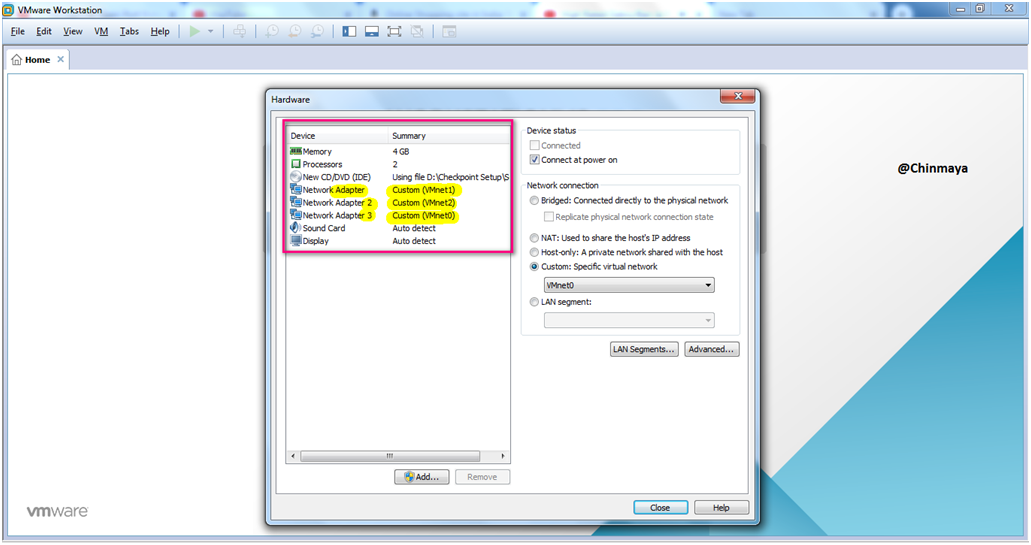
VMware Hardware configuration Details.
Memory : 4GB (Minimum)
Processor : 2 (Minimum)
NOTE: Configuration can be scale its fully depends upon the hardware resources you have , I mention minimum requirement
More details for VMware hardware configuration for gateway1.

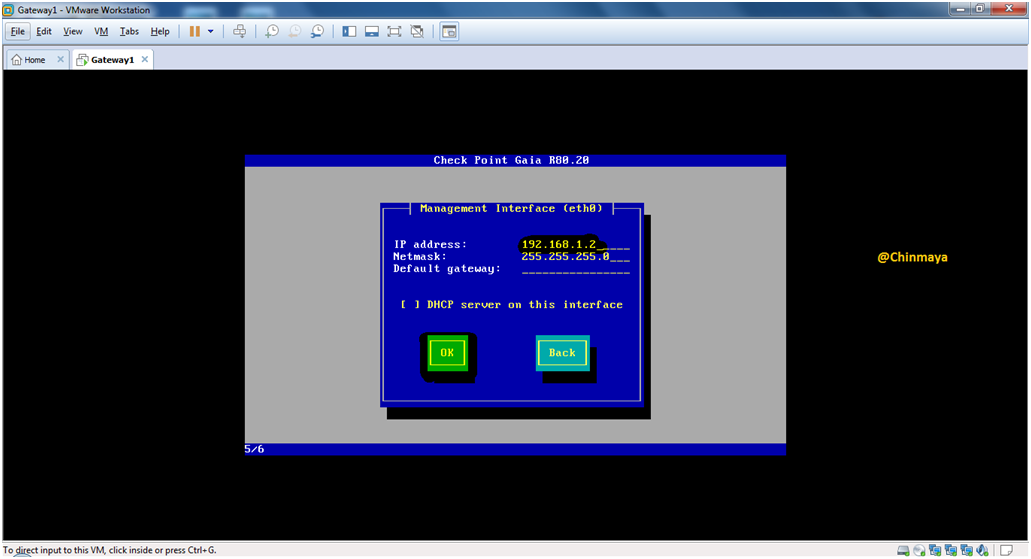
STEP 02: Start the Gateway1 virtual machine.
Asking for the IP address of the eth0 interface which come on Vmnet1 (Network:192.168.1.0/24) then Click “OK”

STEP 03: Assign IP address.
IP Address : eth0 : 192.168.1.2
Netmask : 255.255.255.0
Default Gateway : You can also configure after installation
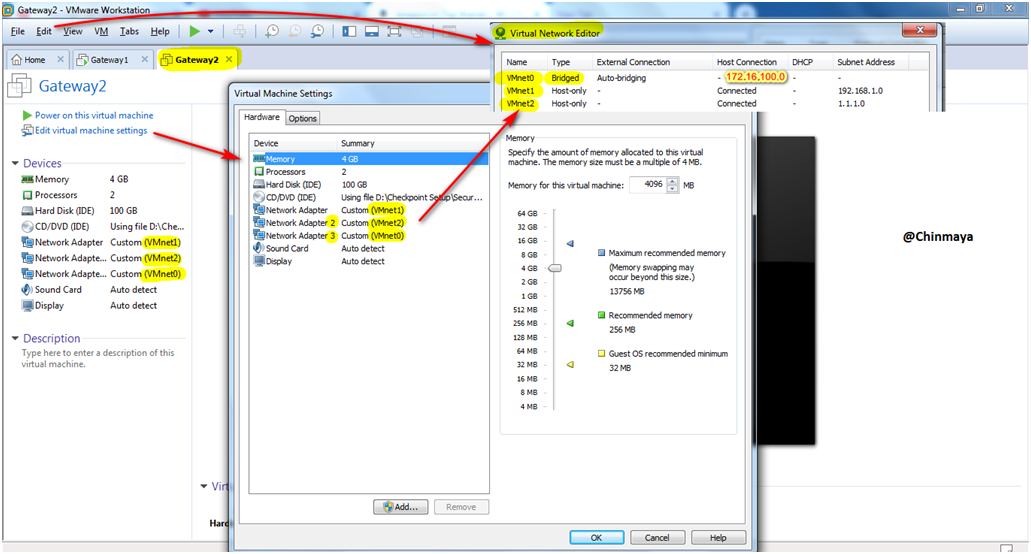
STEP 04 : More details for VMware hardware onfiguration for Gateway 2
STEP 05: Start the Gateway2 virtual machine.
Asking for the IP address of the eth0 interface which come on Vmnet1 (Network:192.168.1.0/24) and then Click “OK”
Note: You can run any gateway VM on my case I first ready the gateway 2 so basically this one I will making as standby gateway.
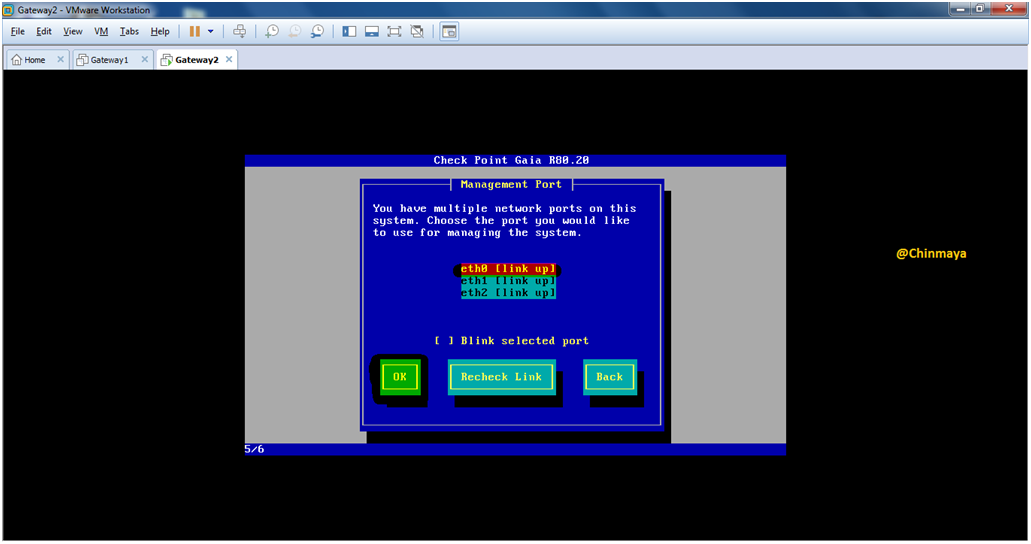
STEP 06: Assign IP address.
IP Address : eth0 : 192.168.1.2
Netmask : 255.255.255.0
Default Gateway : You can configure later after installation
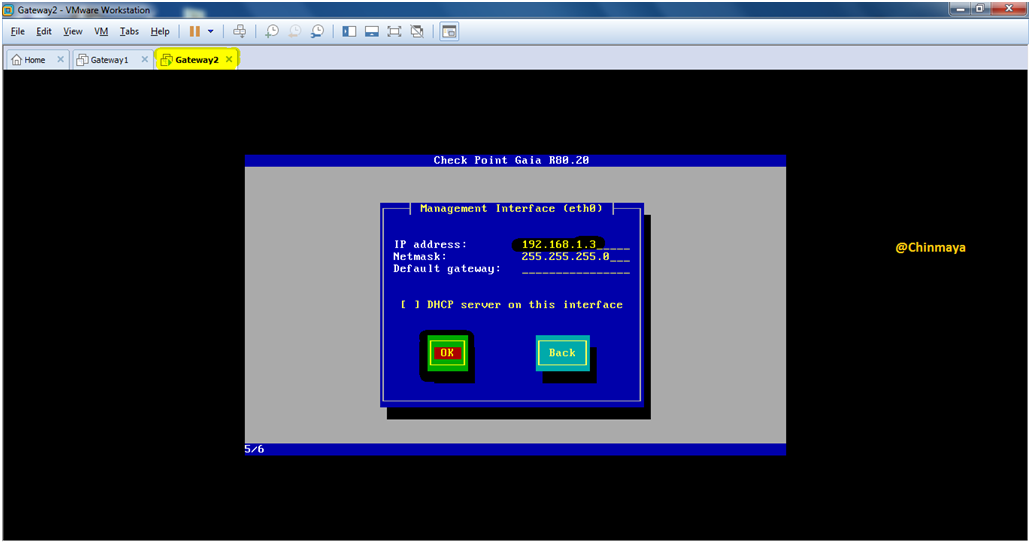
STEP 07: After Power on the Gateway1 VM machine.
Login with below default credentials.
Username : admin | Password : admin
Check the IP address details.
Command : Clish>lock database override
Clish>show configuration interface
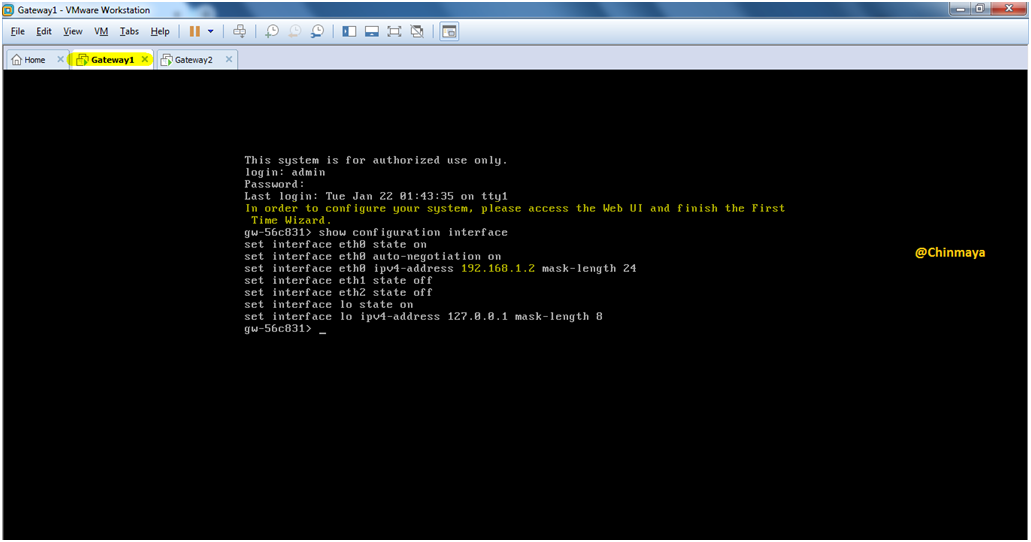
STEP 08: After Power on the Gateway2 VM machine.
Login with below default credentials.
Username : admin | Password :admin
Check the IP address details.
Command : Clish>lock database override
Clish>show configuration interface
Asking to Run the first time configuration wizard

STEP 09: Open the GAIA WebUI for run the First Time Configuration Wizard
Before that ping the IP address of “eth0” interface to check the communication.
login to By Default credentials
username : admin | password: admin and Click “Login”
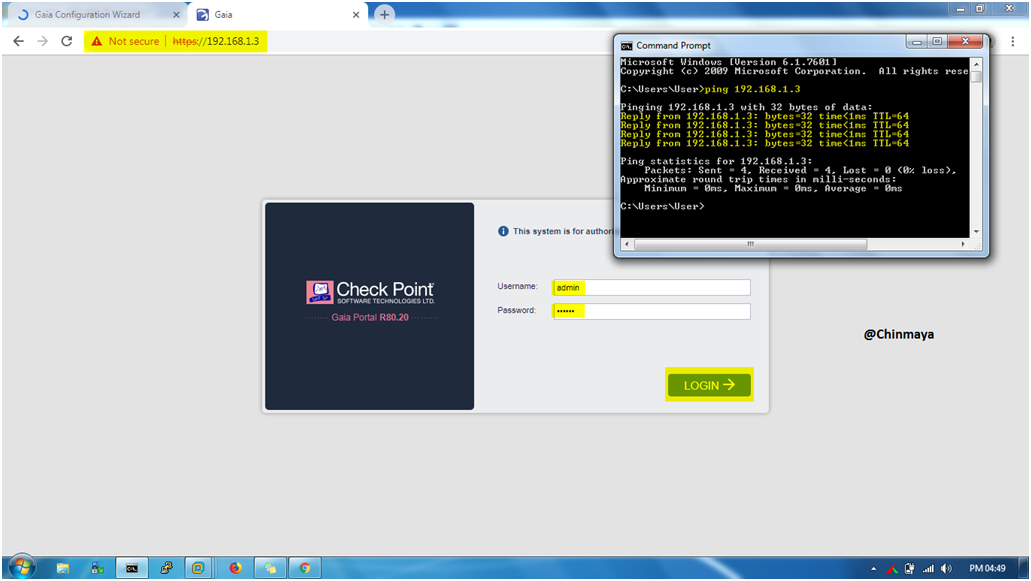
STEP 10: Verify the IP address of Gateway1.
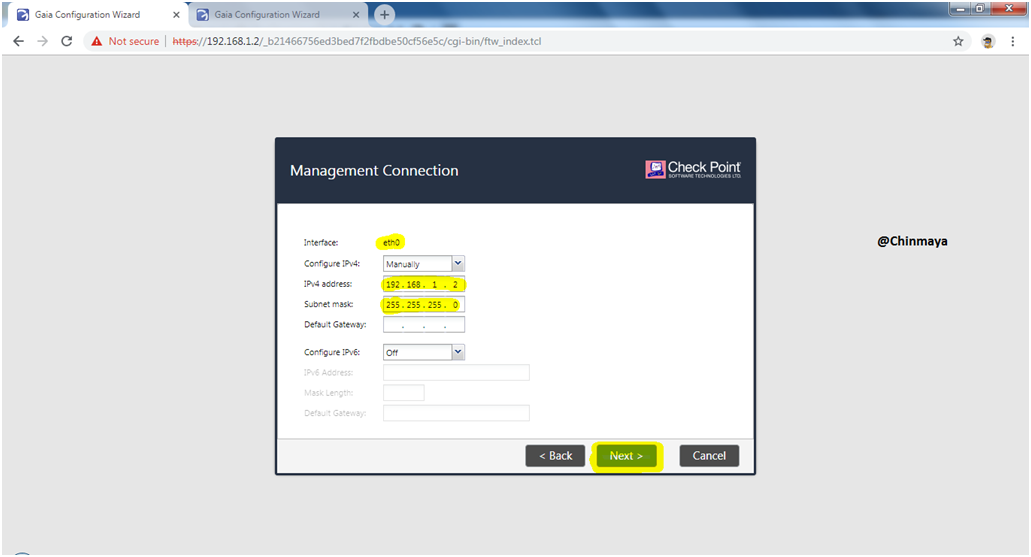
STEP 11: Verify the IP address of Gateway 2.

STEP 12: Assign DNS address to Gateway1.
NOTE : I am using Google DNS
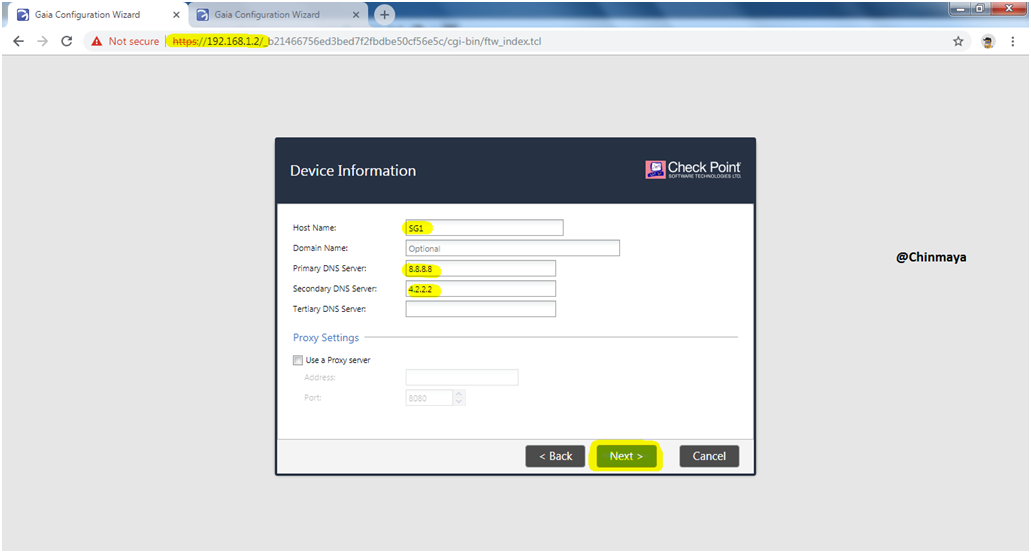
STEP 13: Assign DNS address to Gateway2
NOTE : I am using Google DNS

STEP 14: Select ” Security Gateway and/or Security Management” in Gateway1.
Click “Next”.

STEP 15: Select ” Security Gateway and/or Security Management” in Gateway2.
Click “Next”.
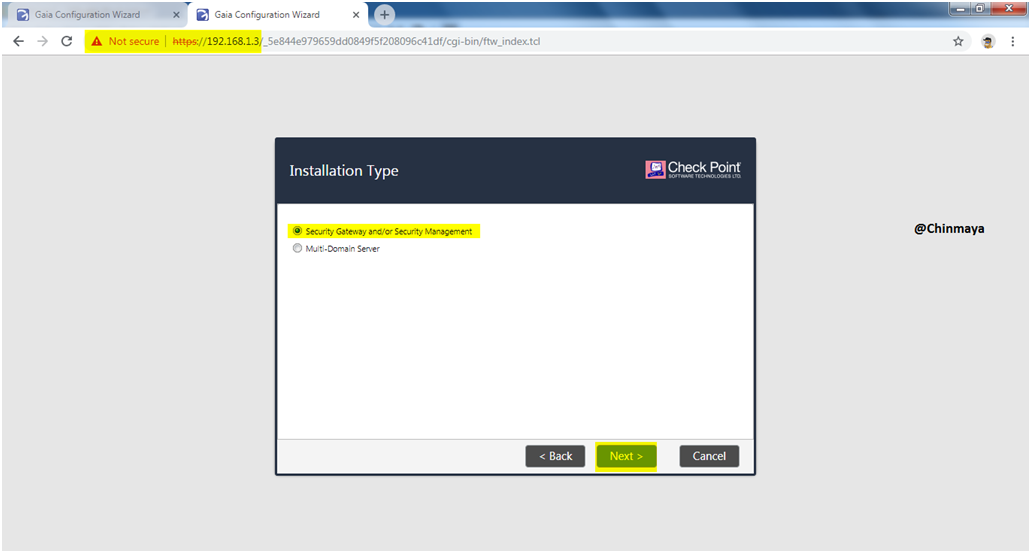
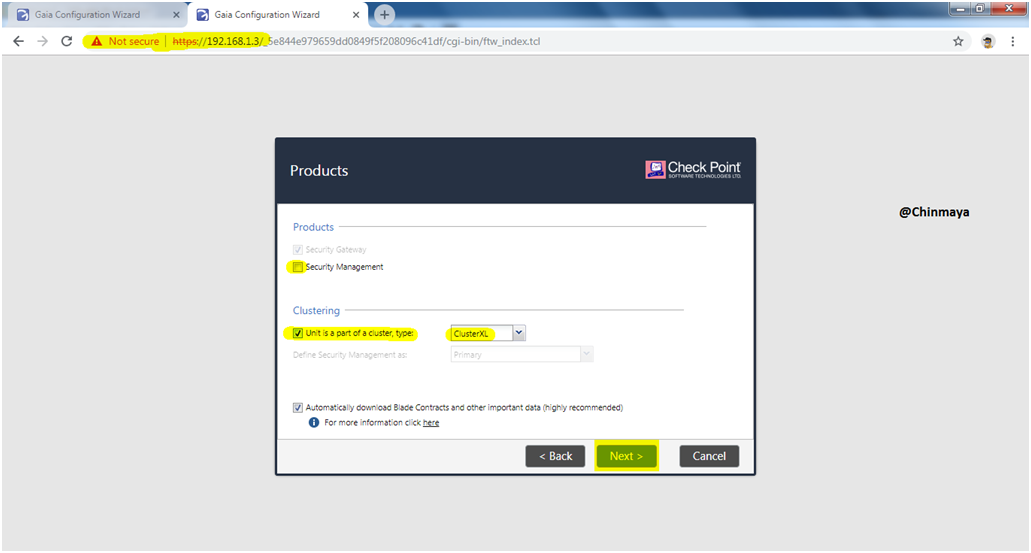
STEP 16: UnMark “Security Management” in Gateway1. (IMP)
Select “Unit is part of a cluster type” as “ClusterXL”
Mark ” Automatically dowload Blade contracts and other iportant data (highnly recommanded)”
NOTE: “Unit is part of a cluster type” optional if you not select during the first time configuration wizard then also we able to configure the Cluster but it will be easy if you select during First Time Configuration Wizard.
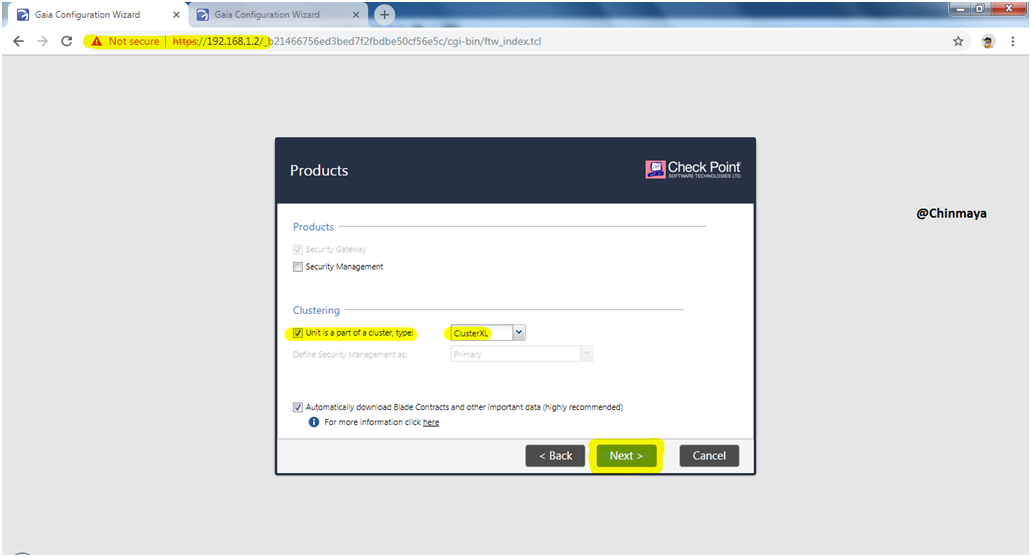
STEP 17: UnMark “Security Management” in Gateway1. (IMP)
Select “Unit is part of a cluster type” as “ClusterXL”
Mark ” Automatically dowload Blade contracts and other iportant data (highnly recommanded)”
NOTE: “Unit is part of a cluster type” optional if you not select during the first time configuration wizard then also we able to configure the Cluster but it will be easy if you select during First Time Configuration Wizard.
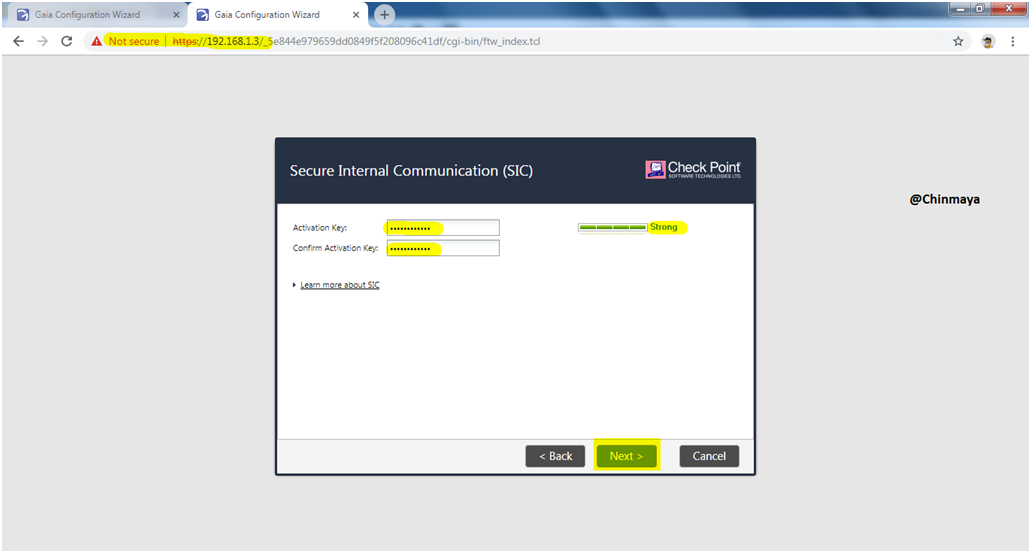
STEP 18: Give a Secure Internal Communication (SIC) key for Gateway1 , this key is required during establish SIC between Security Management Server and Security Gateway so make sure to note this.

STEP 19: Give a Secure Internal Communication (SIC) key for Gateway2 , this key is required during establish SIC between Security Management Server and Security Gateway so make sure to note this.
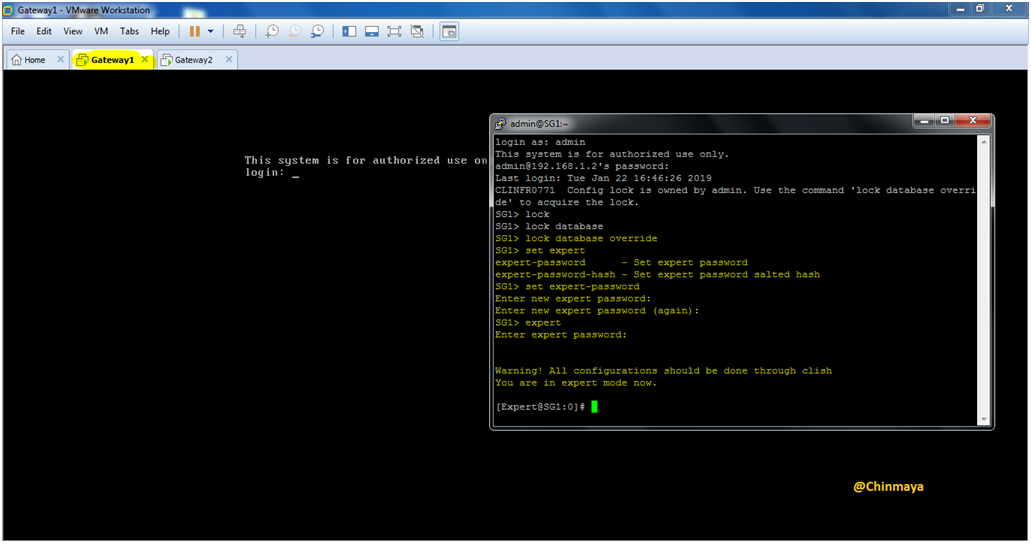
STEP 20: Set a Expert Password for Gateway1
Command : Clich>set expert-password (And then click Enter to set Password for Expert Mode)
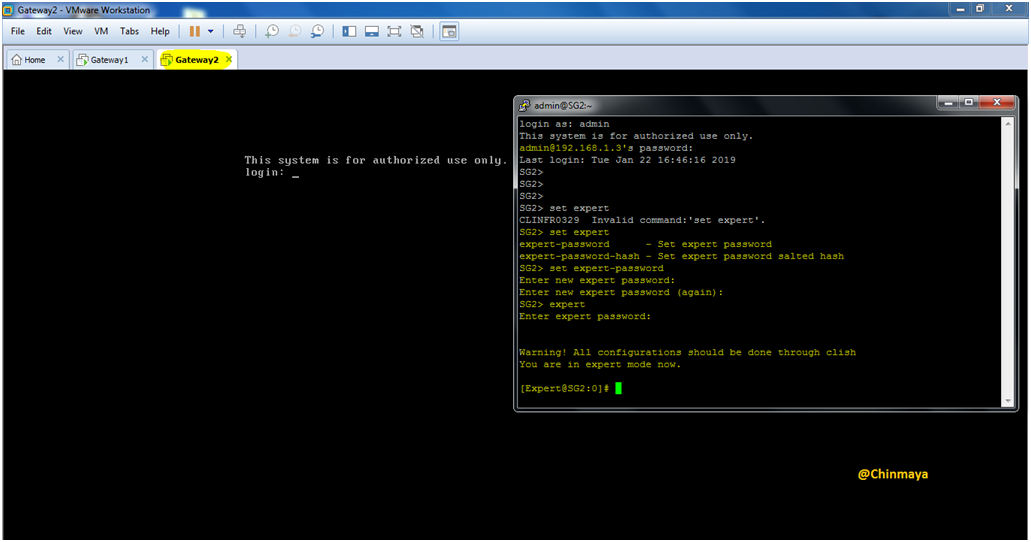
STEP 21: Set a Expert Password for Gateway2
Command : Clich>set expert-password (And then click Enter to set Password for Expert Mode)
STEP 22: Assign the IP address for remaining Sync interface “eth1″(VMnet2:1.1.1.0/24) and external interface “eth2” (VMnet0:172.16.100.0/24).
eth0 : 1.1.1.2/24 and eth1:172.16.100.121/24
Command : Clish>set interface eth1 ip4-address 1.1.1.2 mask-length 24
Clish>set interface eth2 ipv4-address 172.16.100.121 mask-length 24
NOTE : You can also assign the IP address by GAIA WebUI (GAIA PORTAL)

STEP 23: State on the Interface “eth1” and “eth2”.
Command : Clish_SG1>set interface eth1 state on
Clish_SG1>set interface eth2 state on
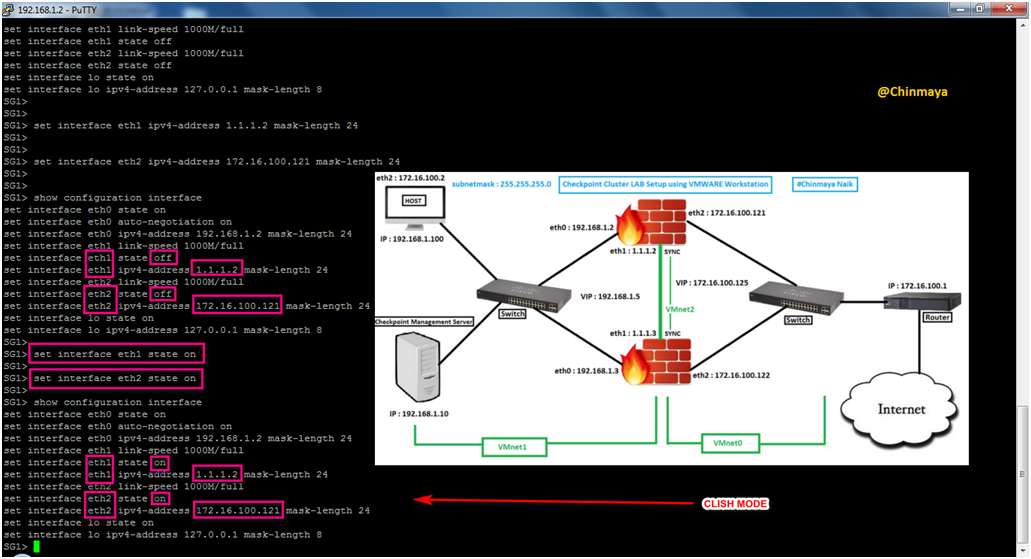
STEP 24: Assign the IP address for like for Sync interface which is “eth1” (VMnet2:1.1.1.0/24) and external interface which is “eth2” (VMnet0:172.16.100.0/24).
Assign IP adress as: eth0 : 1.1.1.3/24 and eth1:172.16.100.122/24
Open GAIA WebUI of Gateway2 —> Network Interface —> Mark “Enable” to UP the interface and assign the IP address with subnet mask.
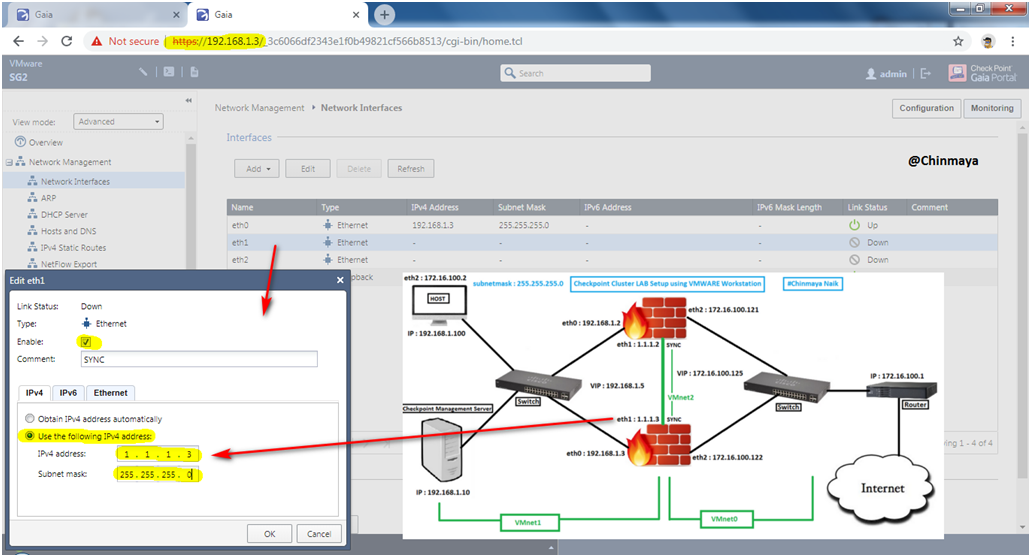
STEP 25: Verify the IP address and interface status.

STEP 26: Assign IP address to the External Interface “eth2”.
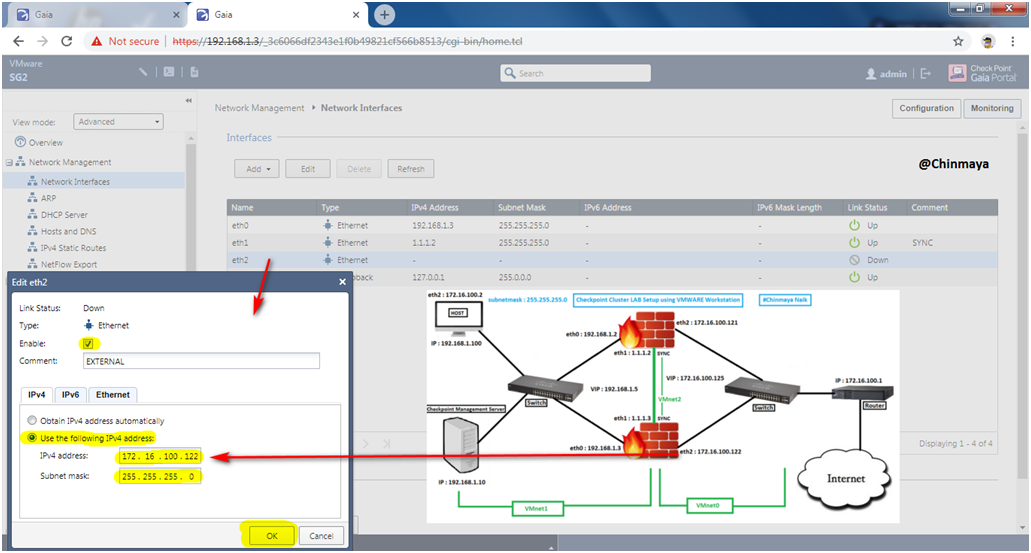
STEP 27: Verify the Interface status with IP address.
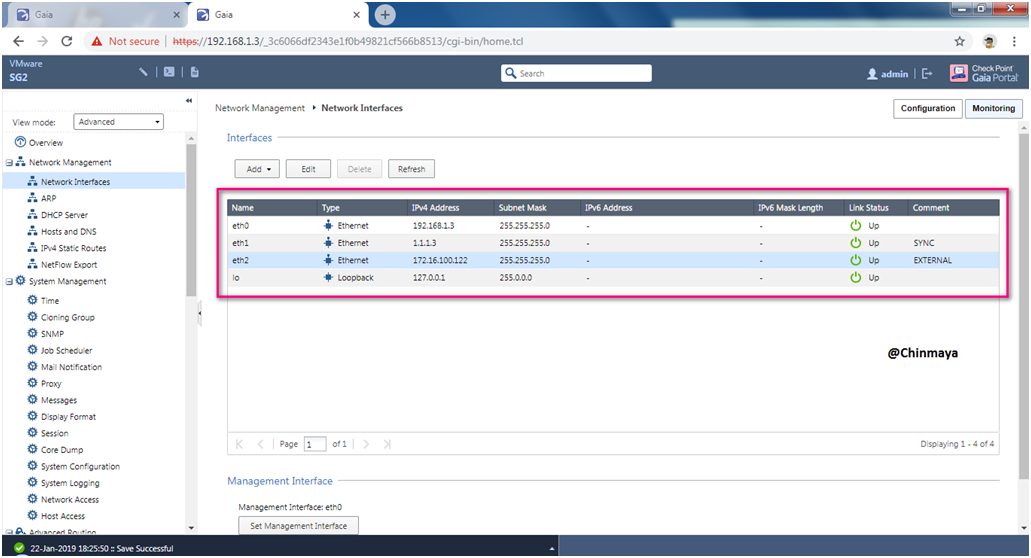
STEP 28: Now Power ON the Management Server if not
We already the configure the Management Server with IP : 192.168.1.10/24.
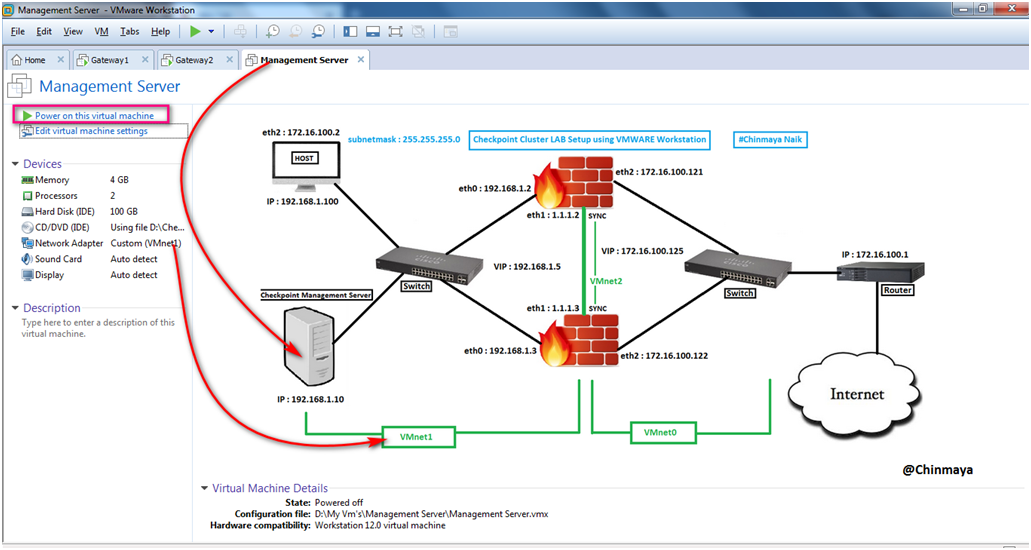
STEP 29: Open the SmartConsole by putting the Management Server IP address with Login credentials.
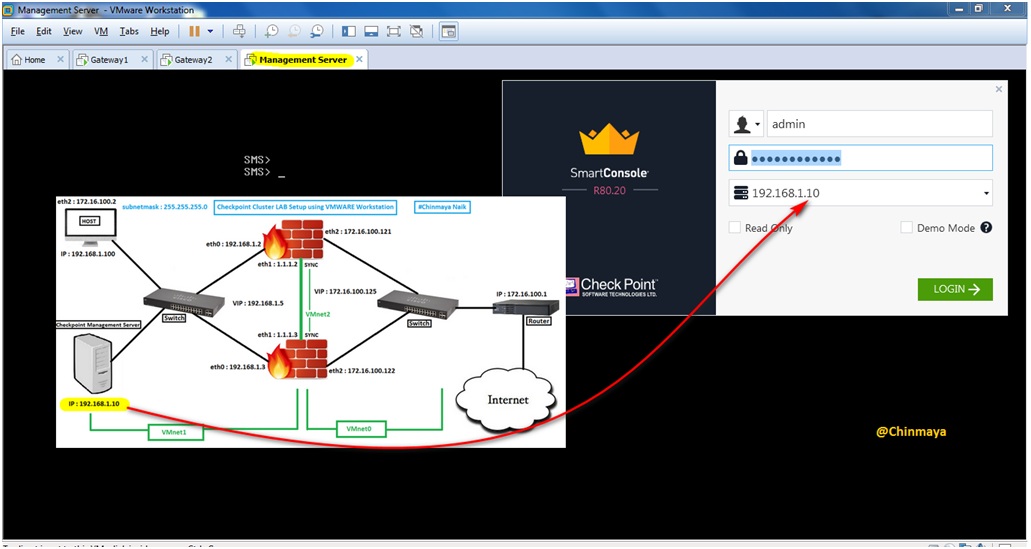
Smart Console is open Successfully.

STEP 30: Now Create a Cluster so for that need to create a Cluster Object.
Location : SmartConsole —> *New —> Network Object —> Gateway and Server —> Cluster —> Cluster…
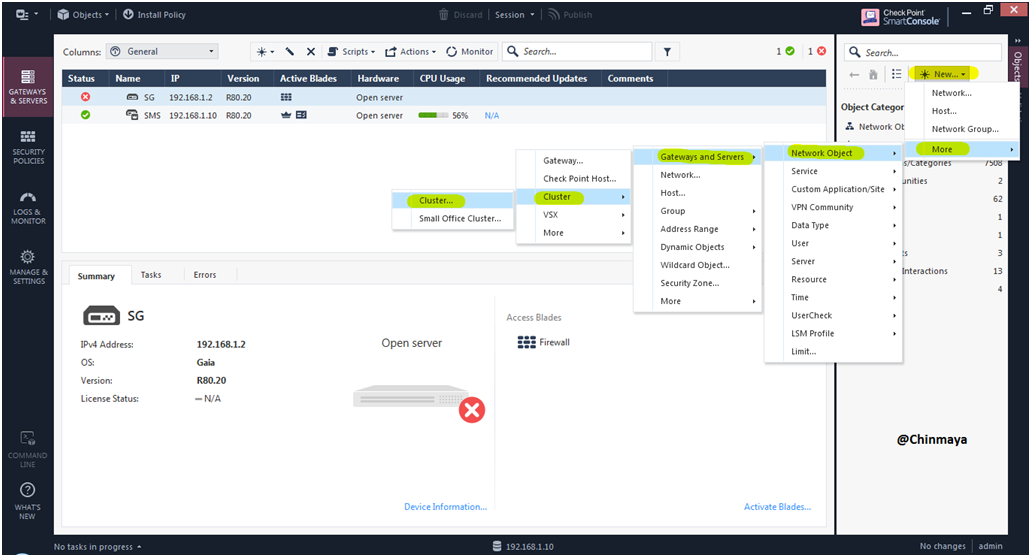
STEP 31: Click “Wizard Mode”
Note : You can also choose Classic Mode to configure but I like Wizard Mode

STEP 32: Cluster Name : CLUSTER (Any Name)
Cluster IPv4 Address : 192.168.1.5 (Assign the Virtual IP Address)
Select “High Availability” like Active/Standby (100%/0%)
Click on “Next”
NOTE : You can also select “Load Sharing” (50%/50% and 70%/30%) but in R80.20/R80.30 still not yet supported for load sharing so if you want this requirements then you need to install the specific Hotfix. in R80.40 it’s already included but please also check the limitations part when using Load Sharing in R840.

STEP 33: Add the Cluster Gateway Member so Select Add —> “New Cluster Member” .
Add Existing Gateway means if you already have Gateway like I have gateway with name “SG” BUT I need to added the new security gateway that I already configured.

STEP 34: Adding Gateway1.
Name : SG1
IPv4 Address : 192.168.1.2 (eth0 interface IP address)
Activation Key : **** (Put the SIC key that you mention during First Time Configuration Wizard).
Confirm Activation Key : **** (Put the Key again)
Click “Initialize”.

SIC is Establish Successfully showing “Thrust established”
NOTE : In case SIC failed then you can recreate a SIC by taking ssh of security gateway and run “cpconfig” utility to reset the SIC.
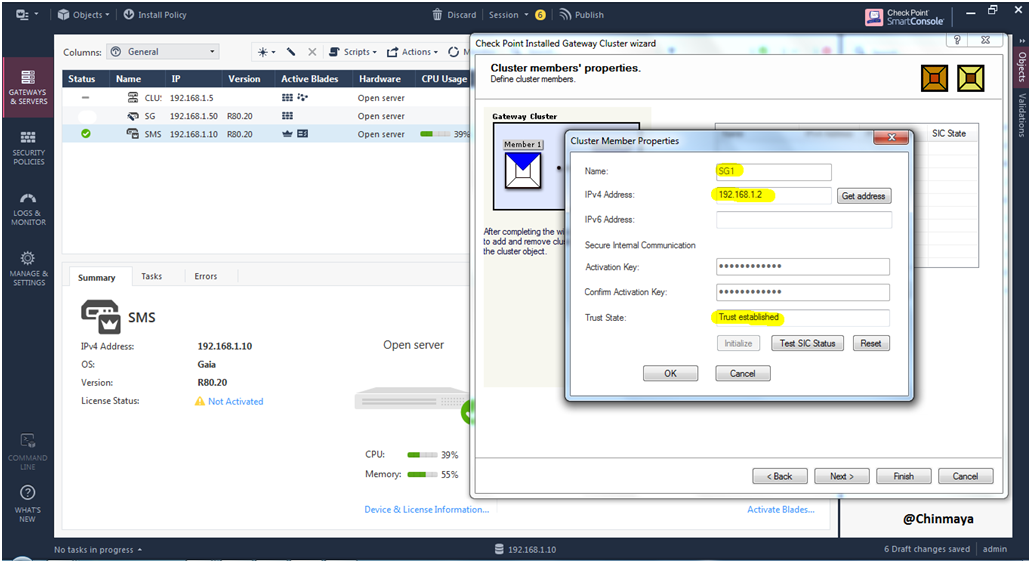
STEP 35: Verify the Security Gateway is added or not.
Showing Gateway Name (SG1) with IP address with SIC Status (Trust established).
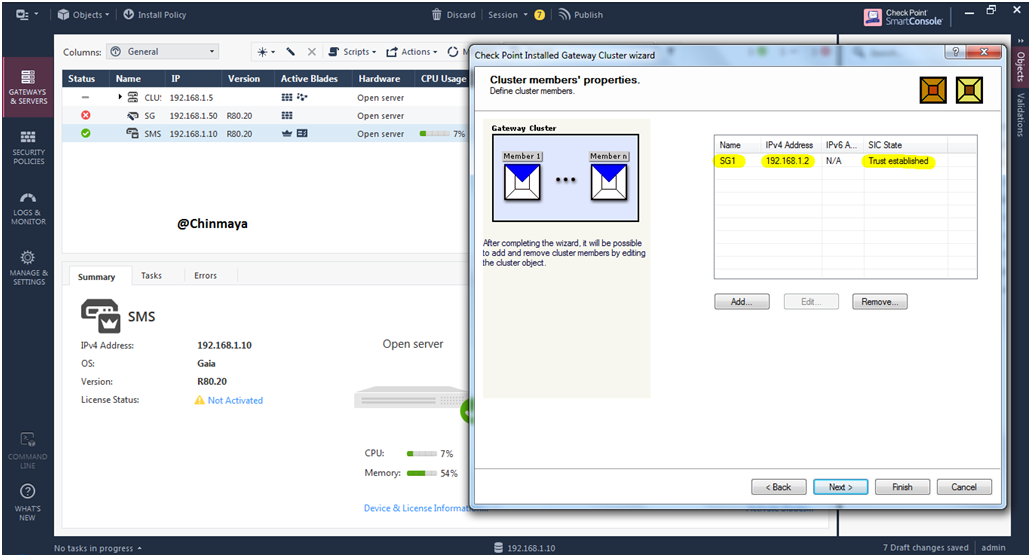
STEP 36: Add the Gateway2
Name : SG2
IPv4 Address : 192.168.1.3 (eth0 interface IP address)
Activation Key : **** (Put the SIC key that give during First Time Configuration Wizard).
Confirm Activation Key : **** (Put the Key again)
Click “Initialize”.

STEP 37: Verify the Security Gateway is added or not.
Showing Gateway Name (SG2) with IP address with SIC Status (Trust established).
NOTE : In case SIC failed then you can recreate a SIC by taking ssh of security gateway and run “cpconfig” utility to reset the SIC.

STEP 38: Click “Next”
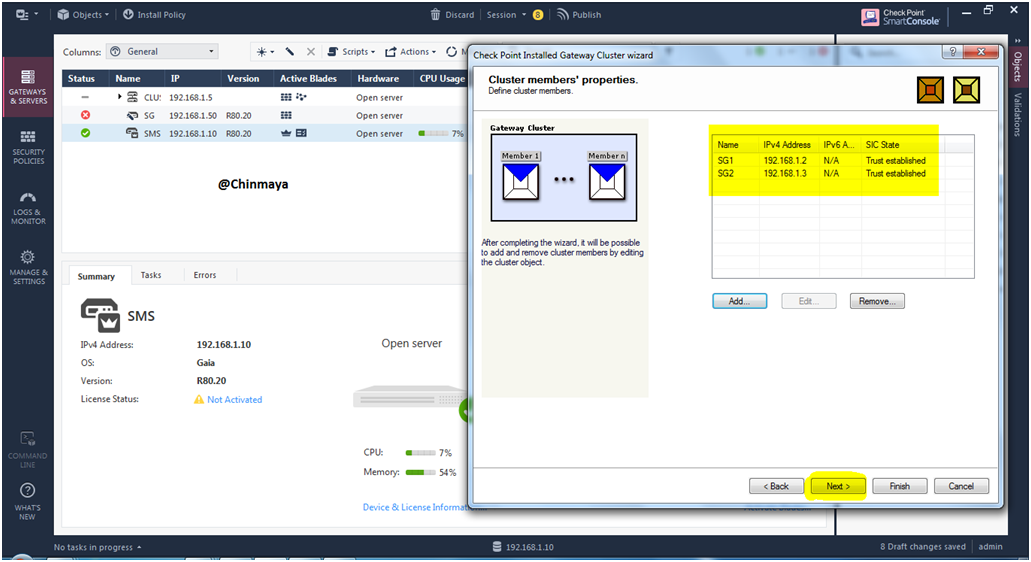
STEP 39: Click “Next” to configure the topology of the cluster.
STEP 40: Put the External Virtual IP Address : eth2 : 172.16.100.125 | Net Mask : 255.255.255.0
Click “Next”
NOTE : IPv4 Network Address : 172.16.100.0 will automatically come because we already define that IP address.
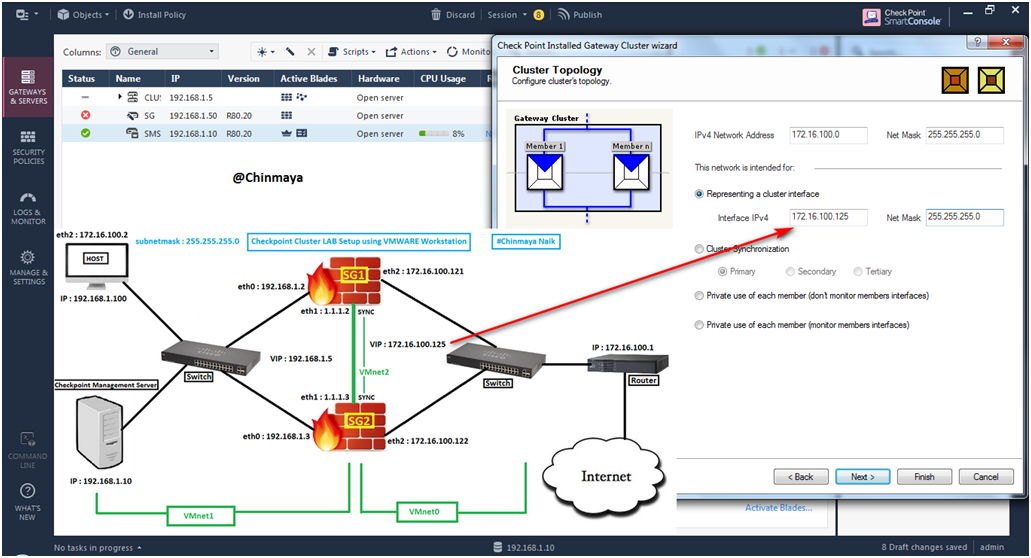
STEP 41: Select option “Cluster Synchronization” as “Primary” because the IPv4 Network Address show 1.1.1.0/24 network.
Click : “Next”

STEP 42: Put the Internal Virtual IP Address : eth2 : 192.168.1.5 | Net Mask : 255.255.255.0
Click “Next”
NOTE : IPv4 Network Address : 192.168.1.0 will automatically come because I already define that IP address.
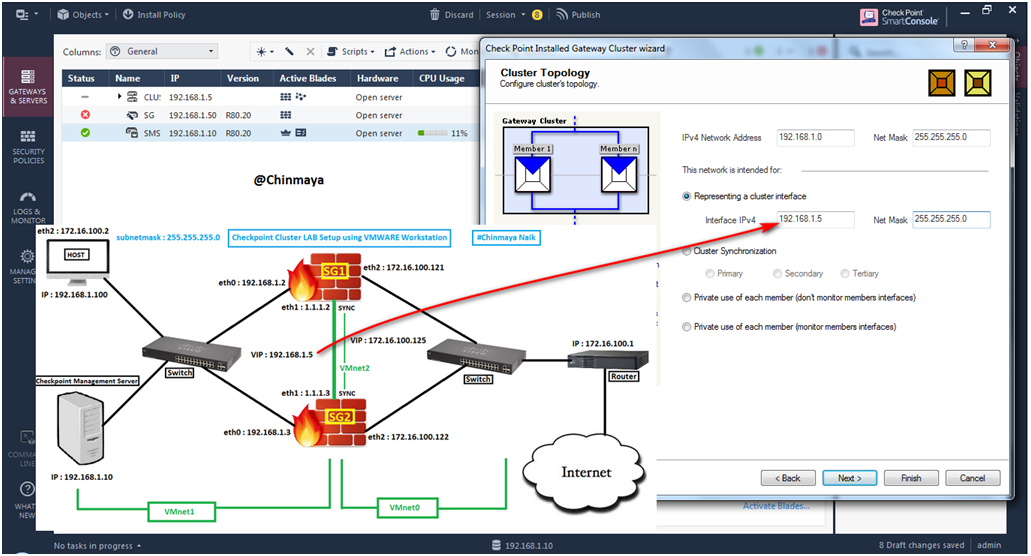
STEP 43: Select “Edit Cluster’s Properties”. and Click “Finish”.
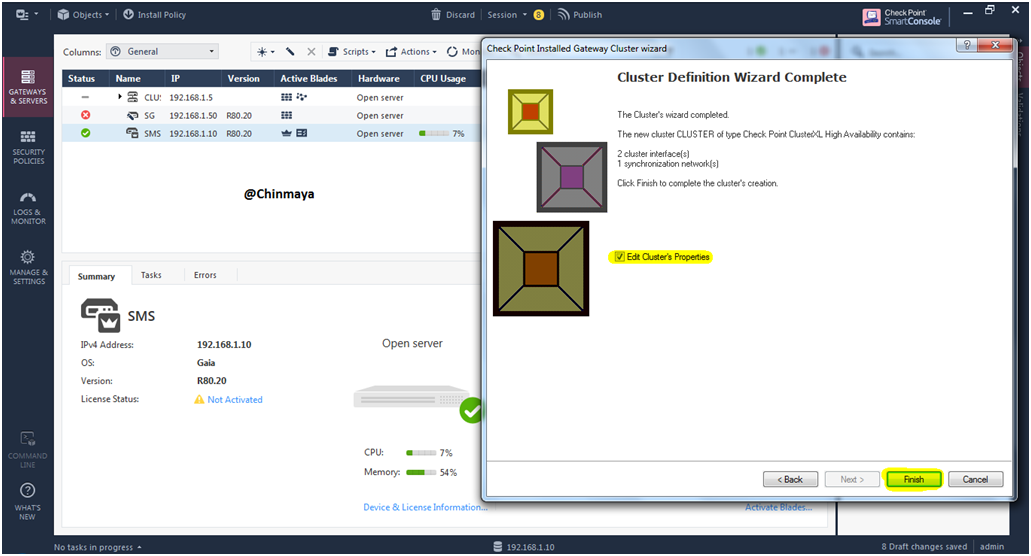
STEP 44: Showing General Properties of Cluster.
Make sure that only Firewall blade should enabled if other blade such as “IPSec VPN” is enabled then Unselect it.
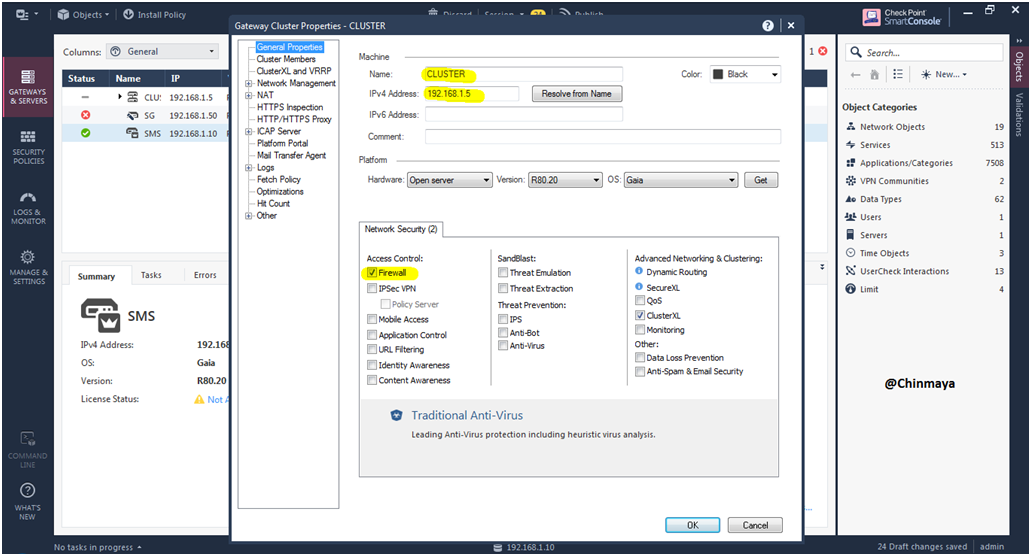
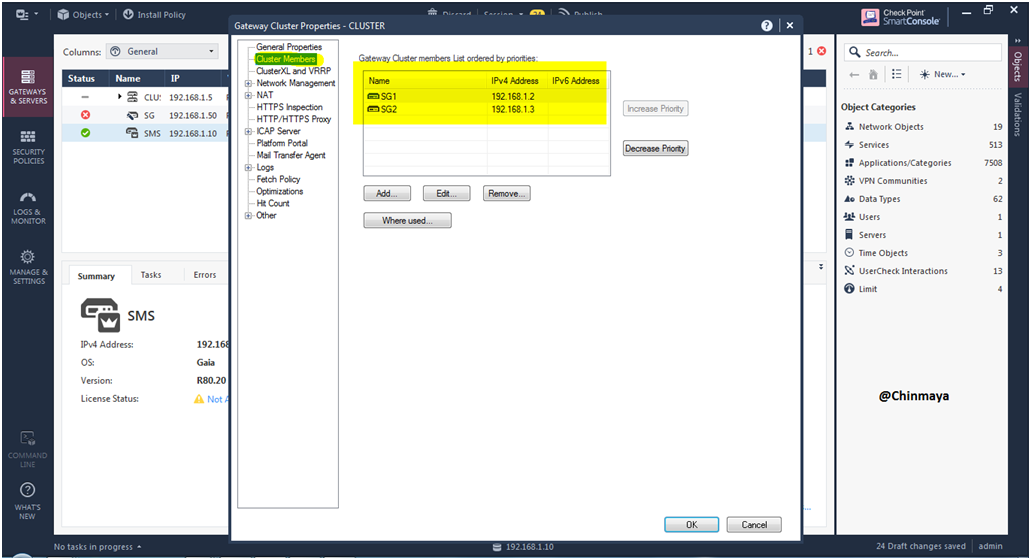
STEP 45: Check the Cluster Member should be able to see the both Gateway object.
Location : Cluster —> Properties —> Cluster Member
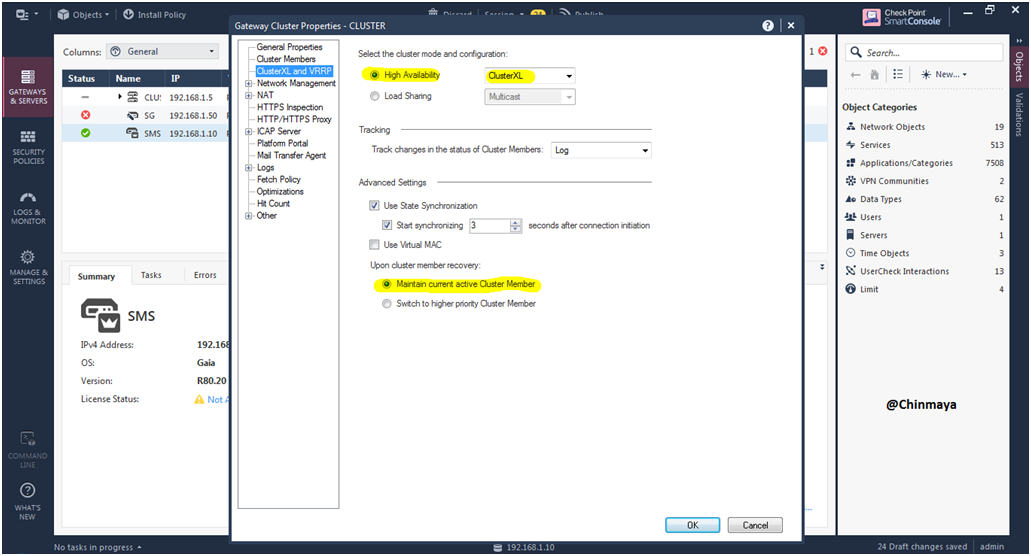
STEP 46: We configure High Availability as ClusterXL (Active/Standby)
Select the “Maintain current active Cluster Member” (No Priority)
Location : Cluster —> Properties —> ClusterXL and VRRP
Showing IP address but still not showing the Interface name because still we not fetch the Topology.
Location : Cluster —> Properties —> Network Management

STEP 47: Select “Get interface with Topology” to fetch topology.
NOTE : If you select “Get interface with Topology” then Anti-Spoofing mode set to prevent on all interface also its recommended.
You can also select the ” Get interface without Topology ” but this time Anti_spoofing will not work which will be security risk.
Don’t select this “Get interface with Topology “option during the Production
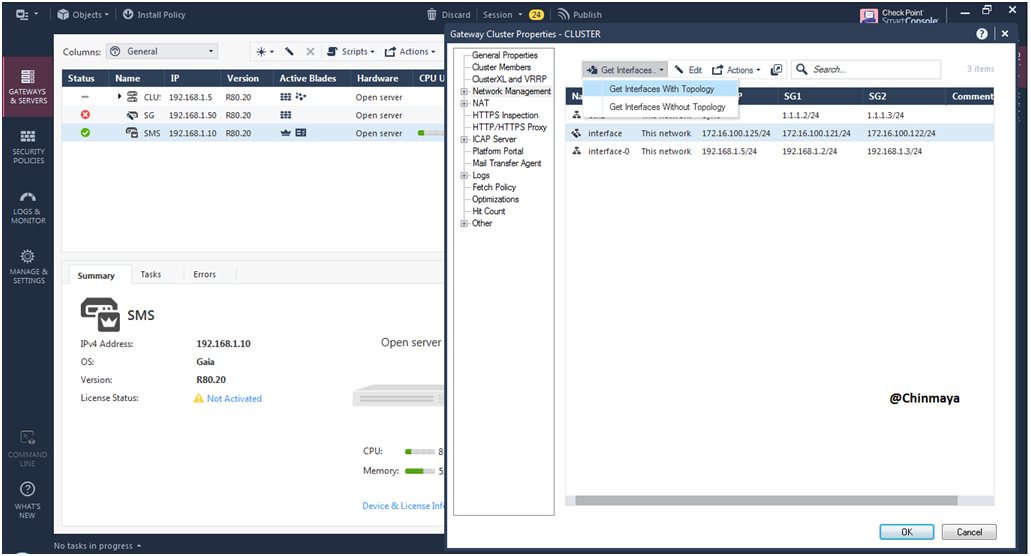
STEP 48: When select “Get interface with Topology” then pop up will select “Yes”.
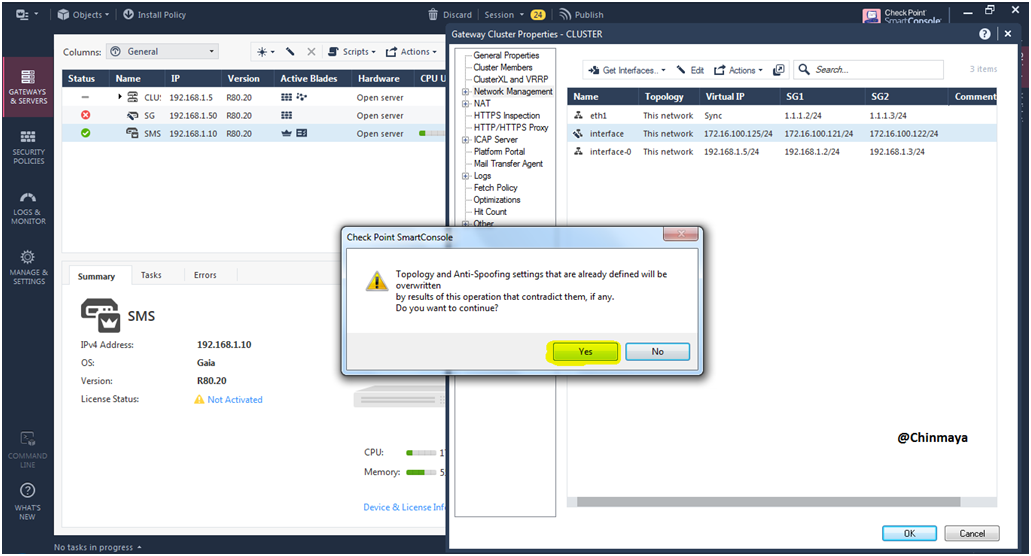
STEP 49: Policy is fetch successfully.
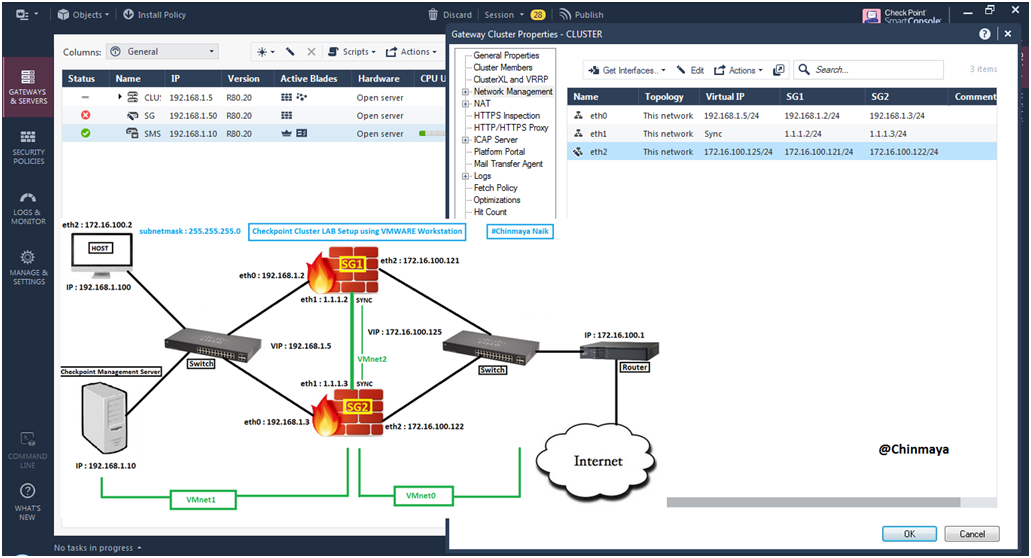
STEP 50: Click the eth0 interface and check the Anti-Spoofing setting. It should be Prevent & Log.
Showing Network Type : Cluster with Cluster member’s IP address.
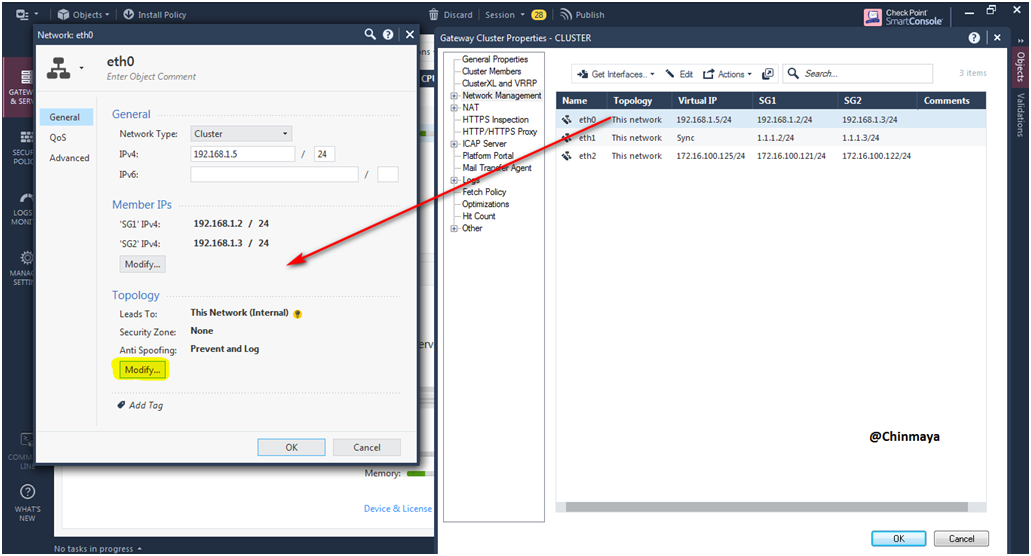
STEP 51: Click “Modify” for more details.

STEP 52: Click the “eth1” interface check the Anti-Spoofing configuration.
Showing Network Type:Sync with Member’s IP address.
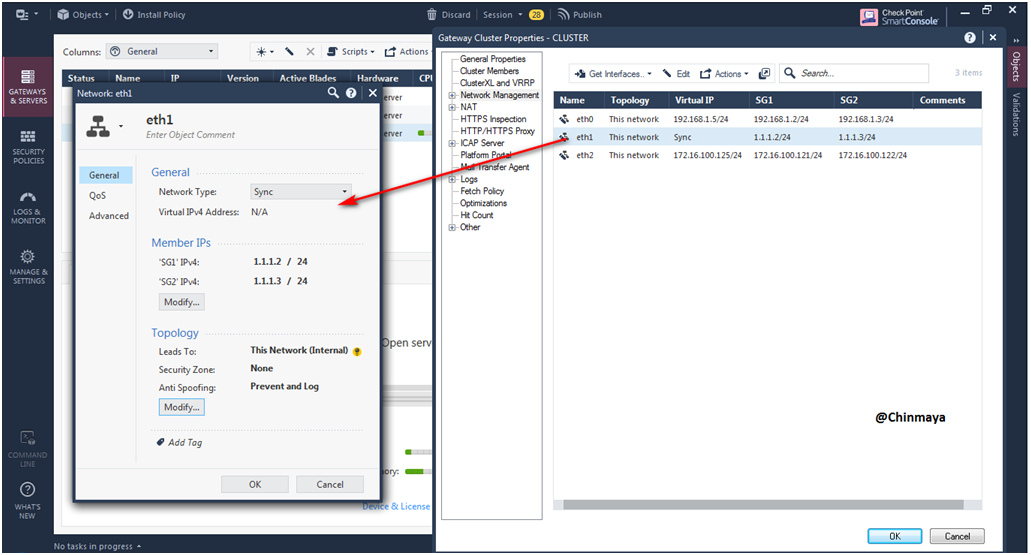
STEP 53: Click the interface “eth2” which should my external IP address and its could be public IP address which leads to internet.
Showing Network Type : Cluster with Member’s IP address.
Click “Modify”.

STEP 54: Define as External and click “OK”.
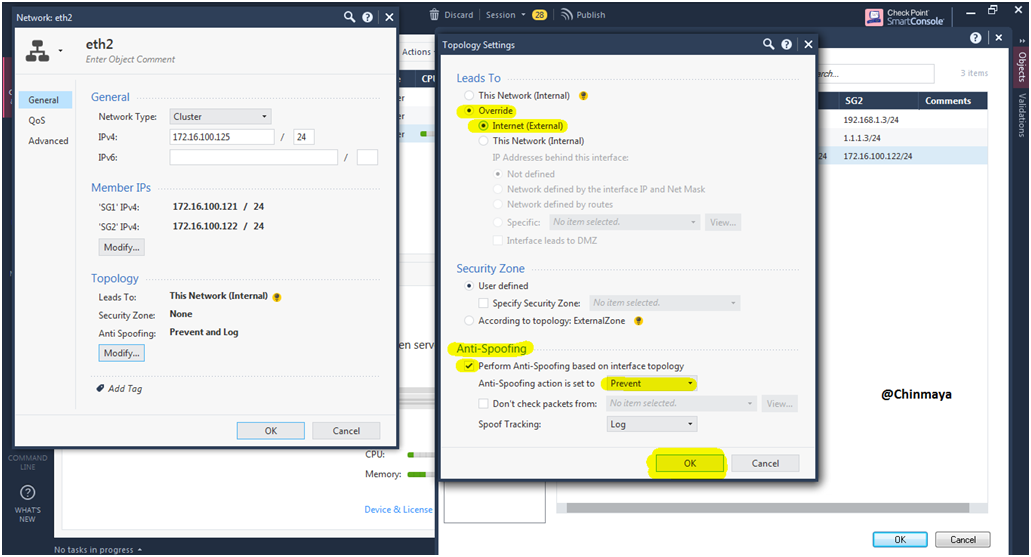
STEP 55: Click “Ok”.
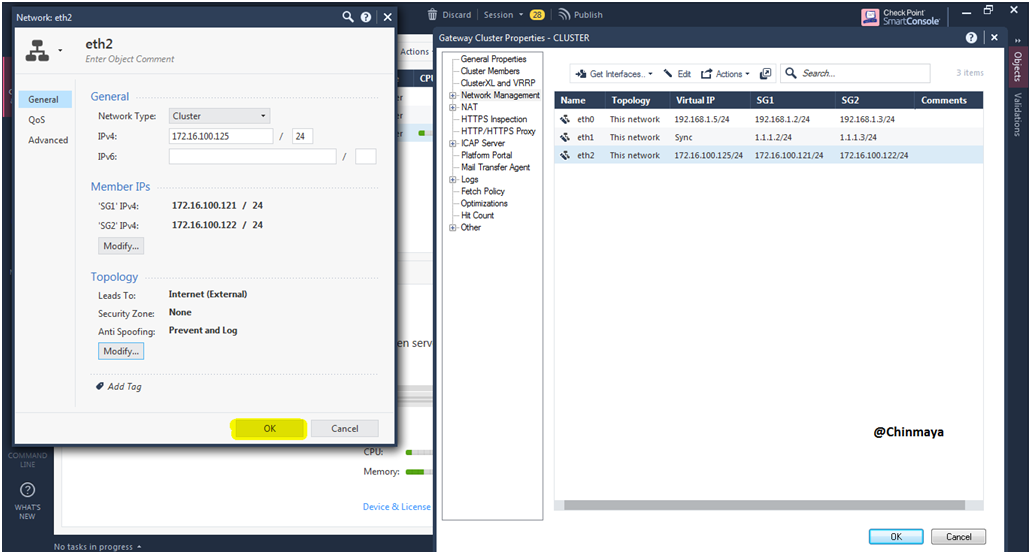
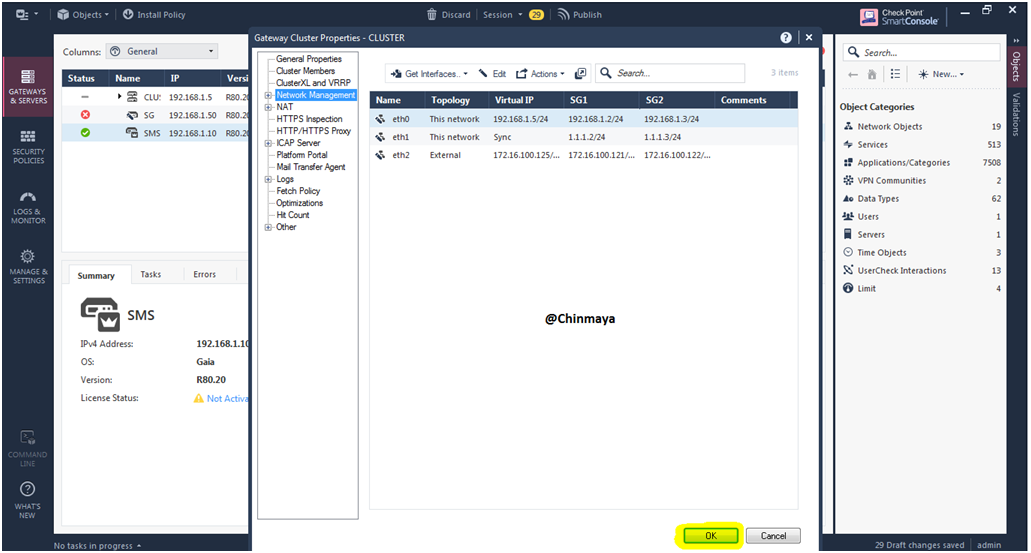
STEP 56: Verify the topology.

STEP 57: Click “OK”
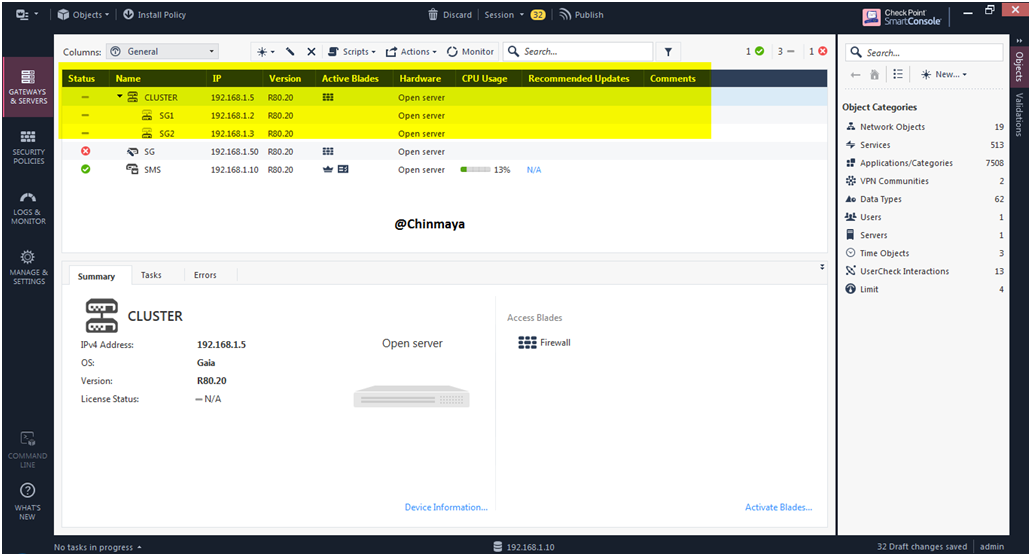
Dashboard of SmartConsole
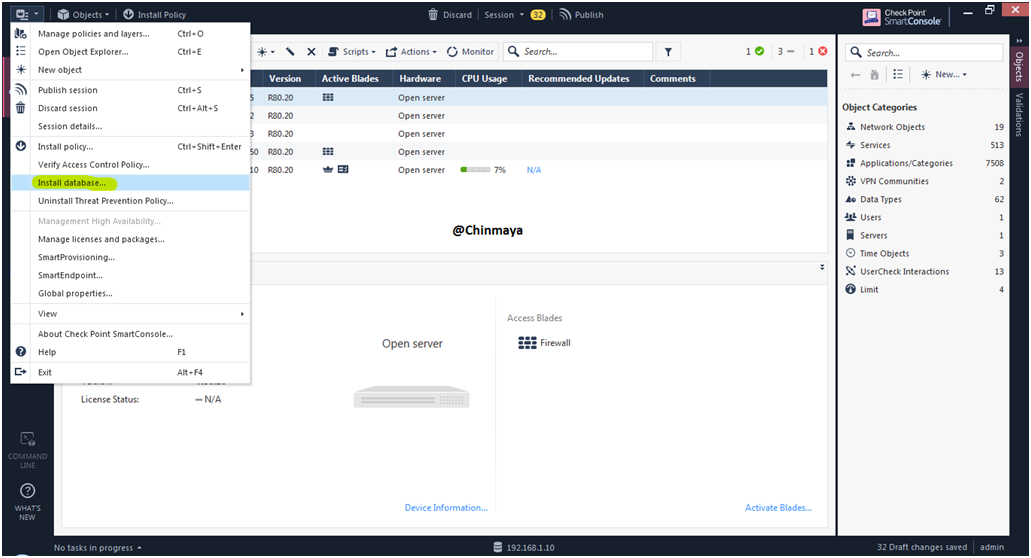
STEP 58: Install the Database.
Location : Menu –> Install Database
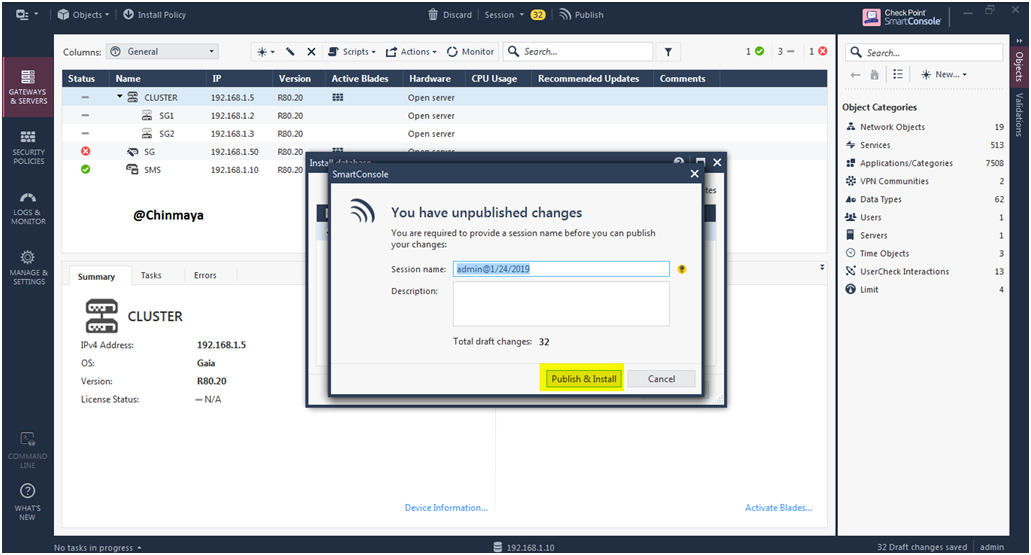
STEP 59: Click “Install” to install the database.

STEP 60: Click “Publish and Install”
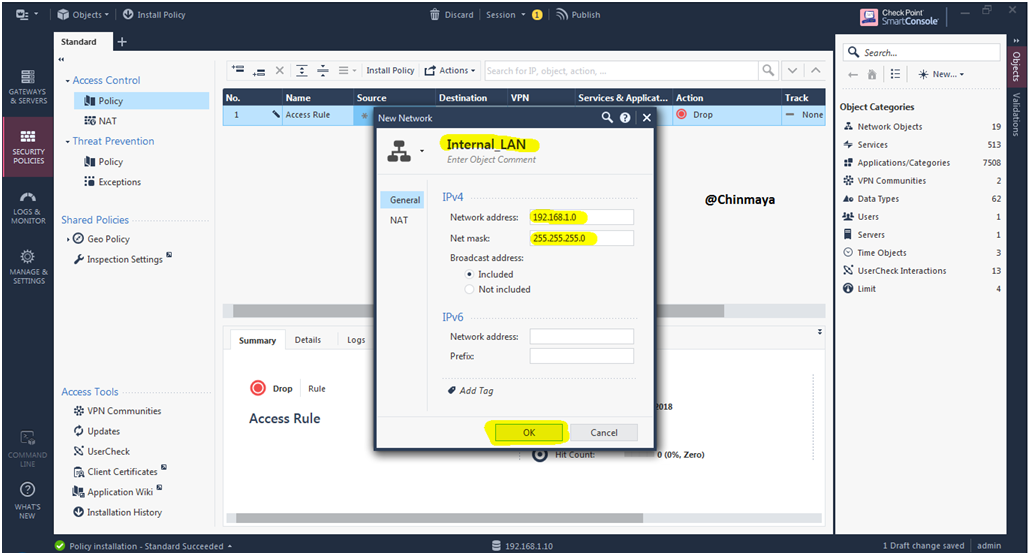
STEP 61: Create a Network Object for creating a security policy.
Name : Internal_LAN
Network : 19.168.1.0
Net Mask :255.255.255.0
Location :- SmartConsole —> *New —> More —> Network Object —> Network
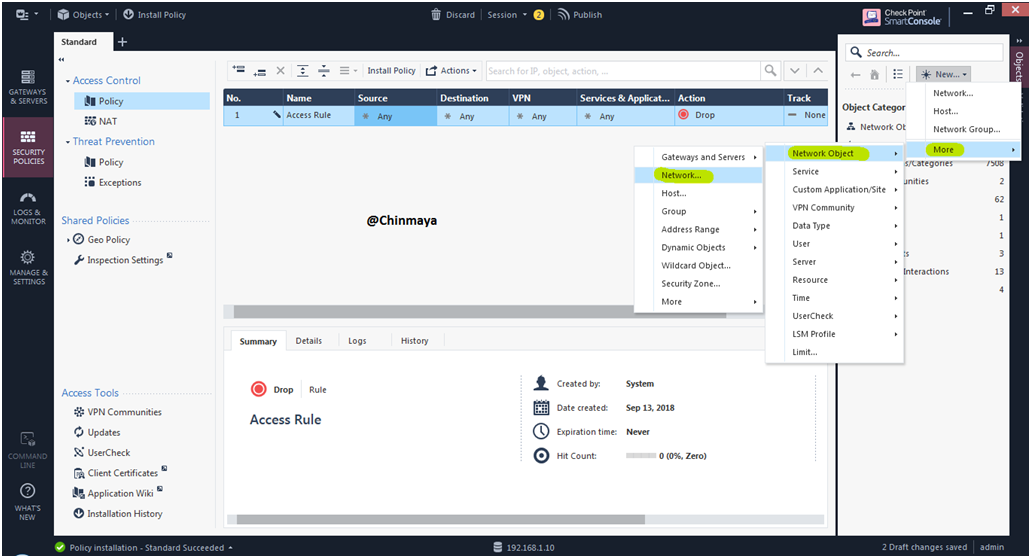
STEP 62: Click ”OK”
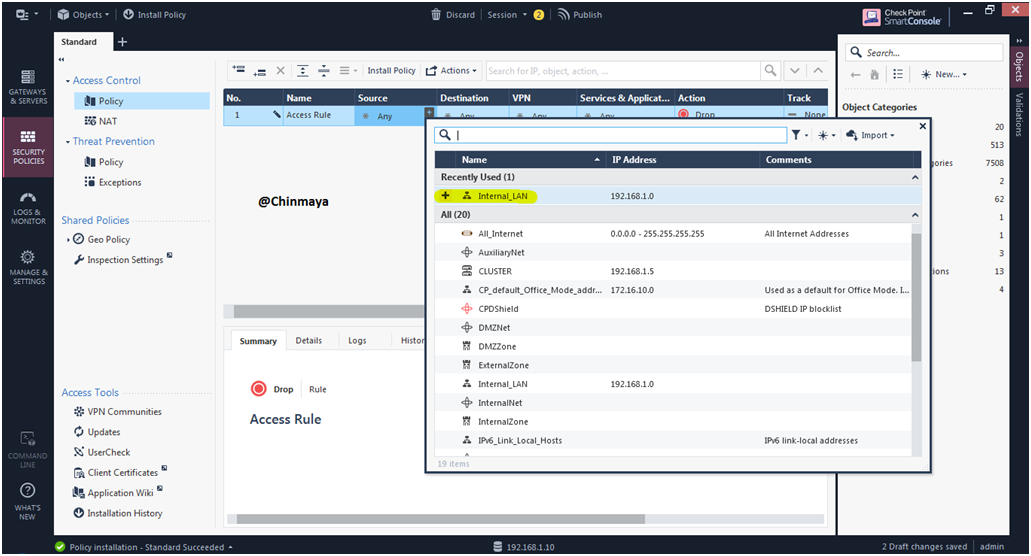
STEP 63: Create a Security policy.
Policy Package : Standard (Default ) (NOTE : You can also rename the existing policy package and also you can create new policy package for other cluster)
Click “+” in Source. Adding Source : Network “Internal_LAN” (192.168.1.0/24) that we already created
Policy :- Source : Internal_LAN , Destination: Any , VPN: Any , Services & Application: Any , Action: Accept ,Track: Log.
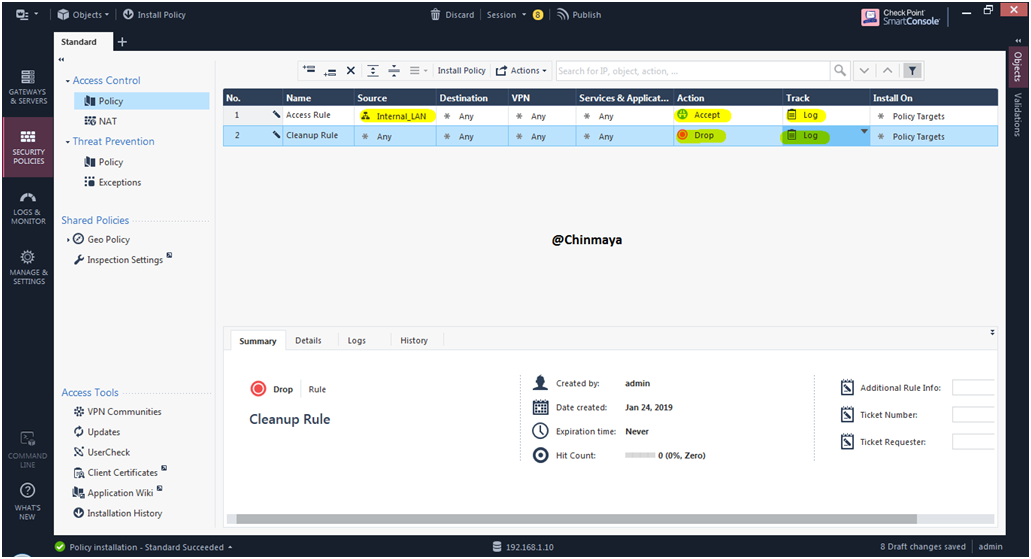
STEP 64: Add Cleanup Rule .
Right click on the “Missing cleanup rule” and Select “Add Cleanup Rule”
Policy :- Source: Any, Destination: Any , VPN: Any , Services & Application: Any , Action: Drop , Track: Log.

STEP 65: Install the Database.
Location : SmartConsole —> Menu —> Install Database
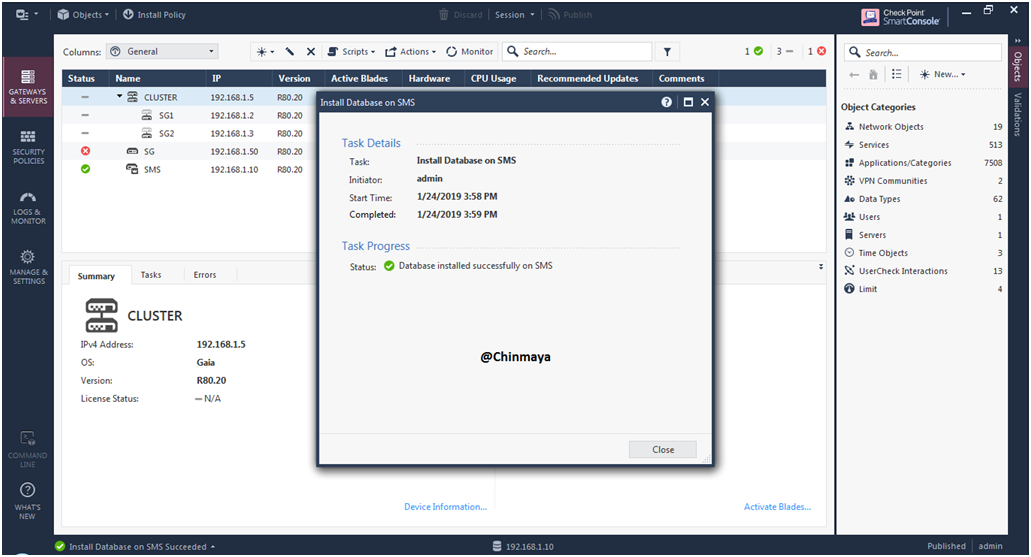
STEP 66: Install the Security Policy .
Select “Access Control” Policy.
Select the “CLUSTER Object”
Select “Install on each selected gateway independently”
Check Mark “For gateway cluster, if installation on a cluster member fails, do not install on that cluster”.
Click “Install”
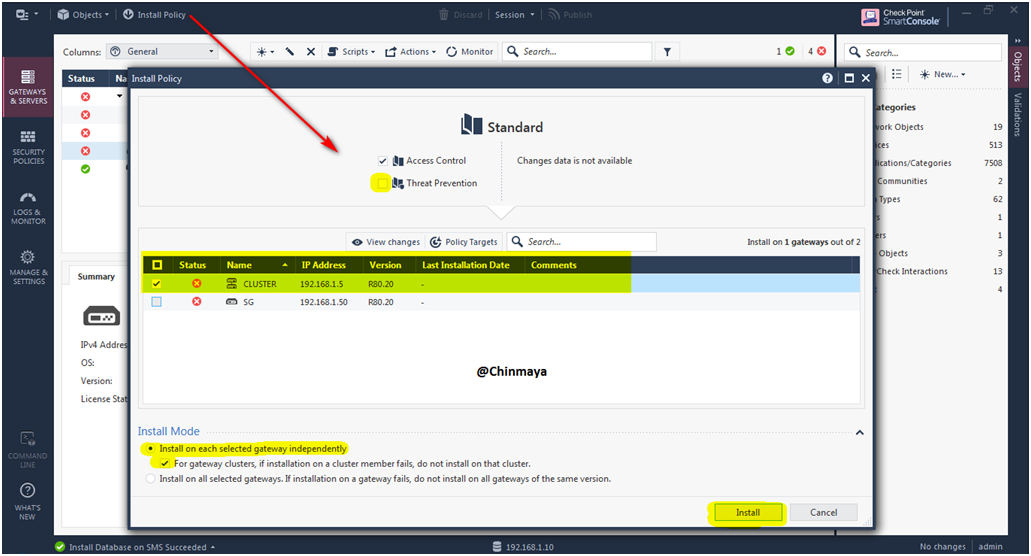
Policy Installation in process

STEP 67: Policy Installed successfully.
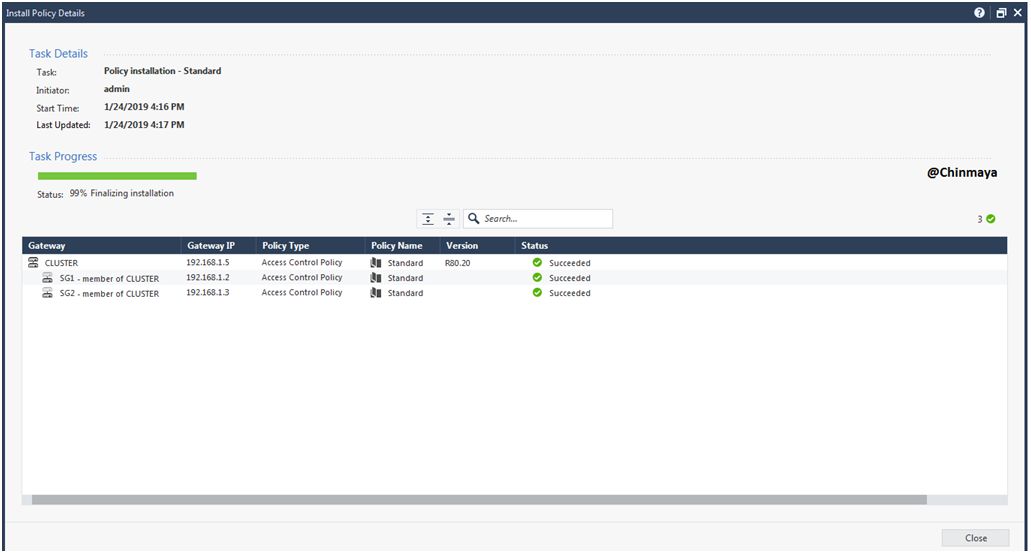
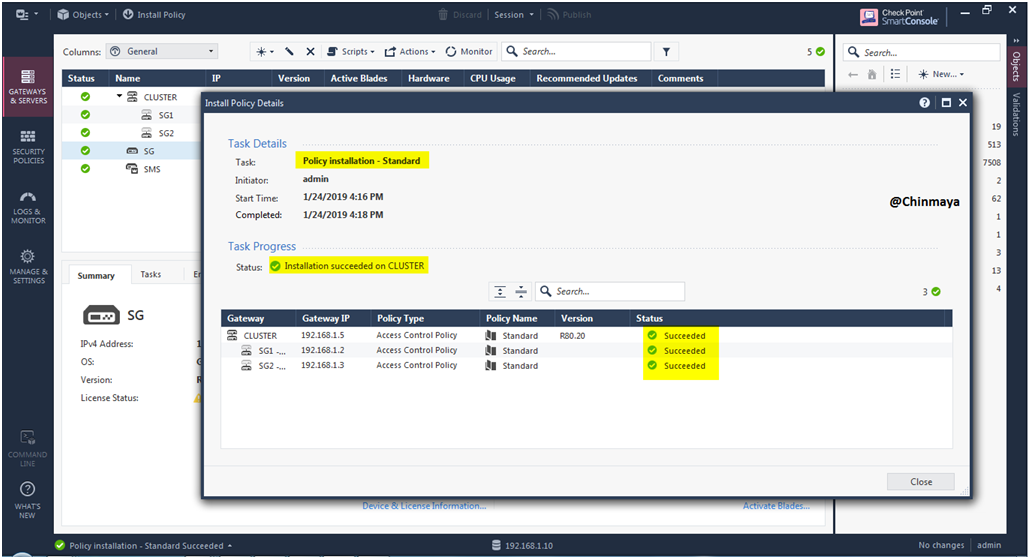
STEP 68: Status is showing “OK”
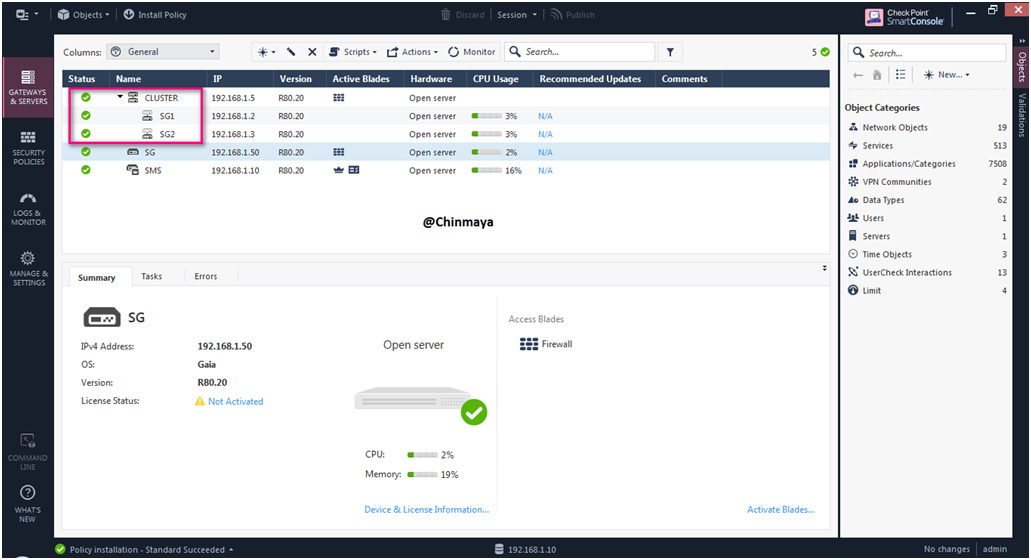
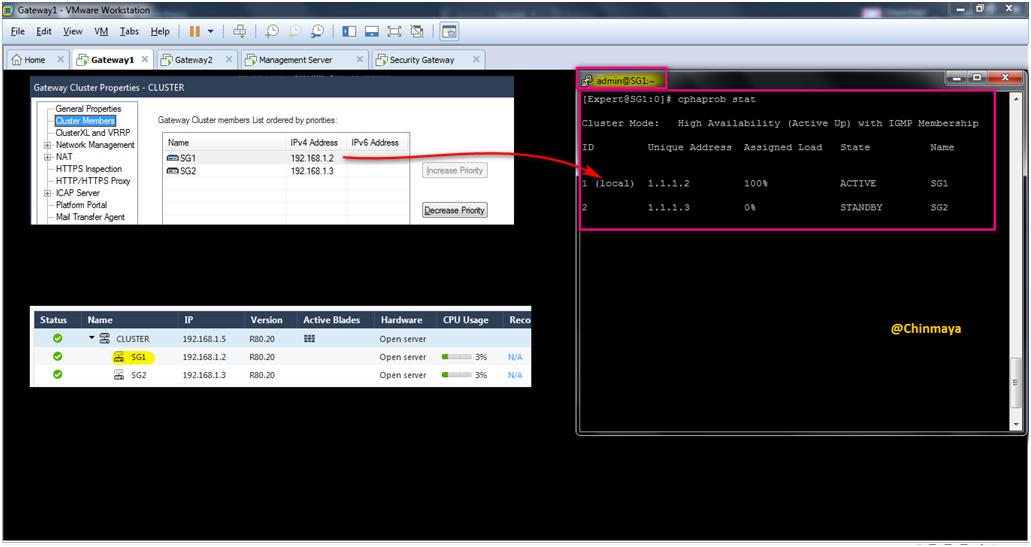
ClusterXL COMMAND
Check the cluster status.
Command : Clish> or [Expert mode]#cphaprob stat or cphaprob state
Now SG1 is become “Active” because 1.1.1.2 is belongs to the Gateway1 (SG1).
We can also see the IP address 1.1.1.2 as “local” and state become “Active” means current SSH session of Gateway1 is Active so If you take SSH of Gateway2 and check the status in Gateway2 then it will be showing 1.1.1.3 as “local” and state become “Standby”
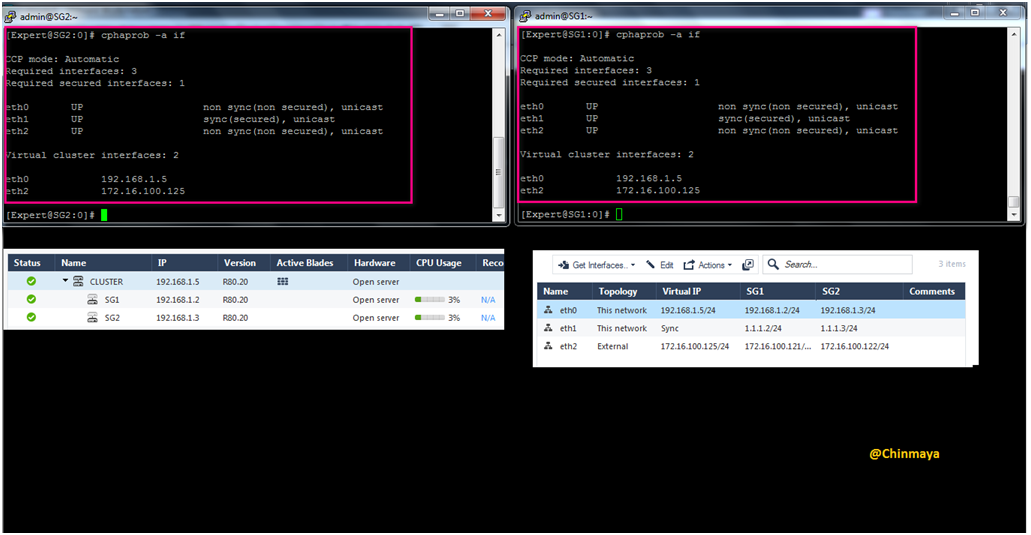
Check cluster interface status with virtual IP address
Command : [Expert]#cphaprob -a if
Check the concurrent connection
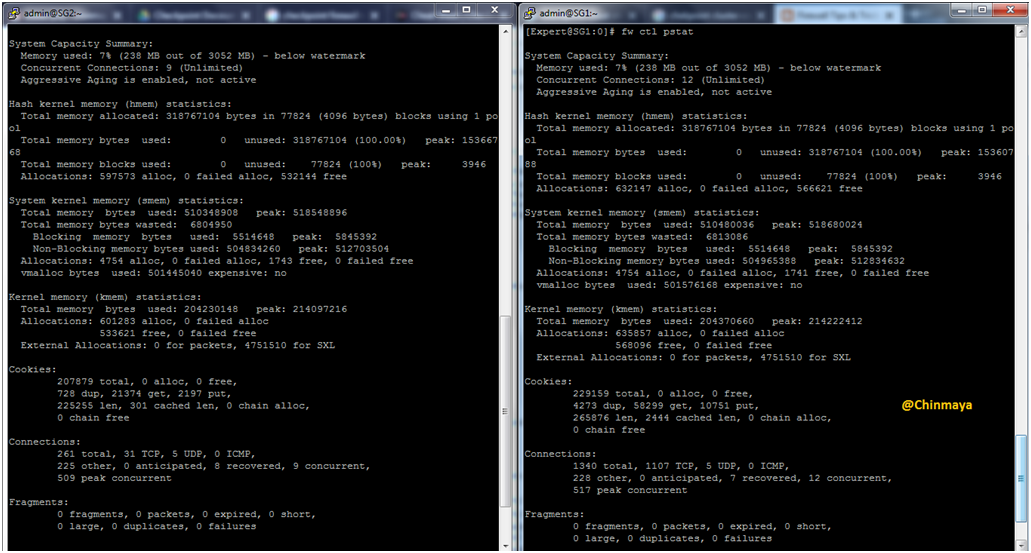
Check any “pnotes” in problem state or not
Command : [Expert]#cphaprob -ia list
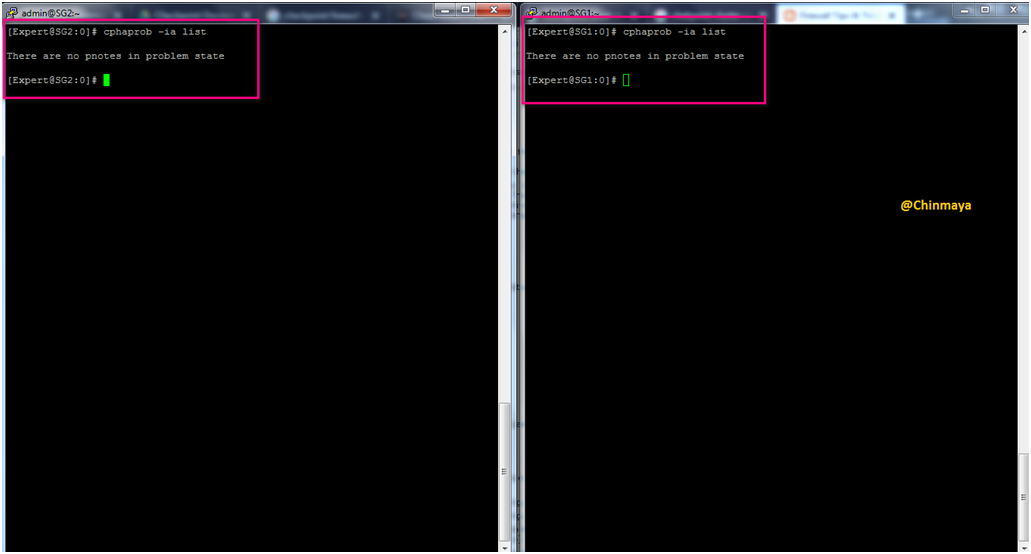
Cluster Failover Test.
Note: You can also restart the services or reboot the gateway or unplugged the connected interface or like shut down the interface , multiple way for testing purpose but it always good to use below command for testing.
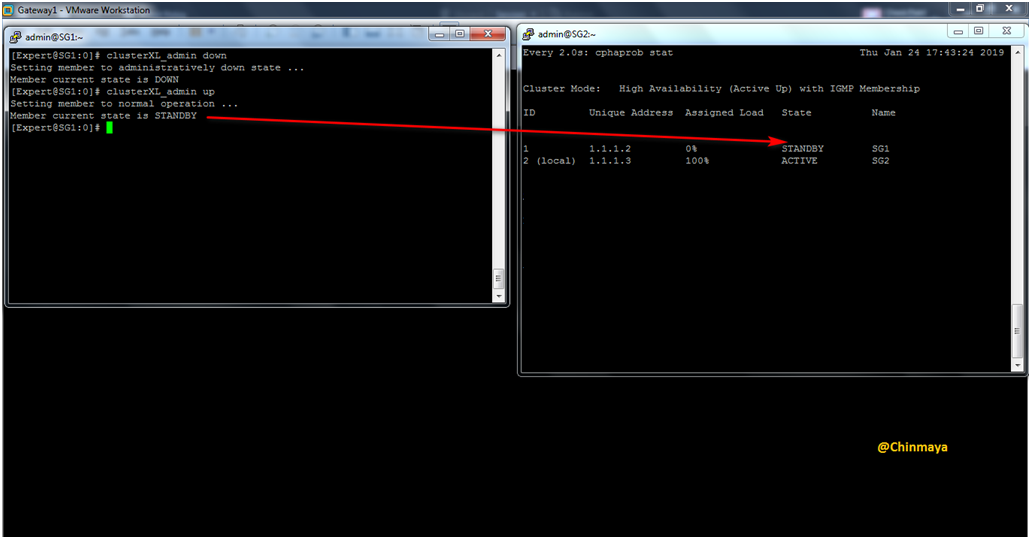
Command : [Expert]#clusterXL_admin down

Showing Gateway1 (SG1) is down. Run below command on Gateway2 (SG2) to check the cluster status.
command : cphaprob stat
Now Gateway2 (SG2) is become Active.

To up the Cluster member Gateway1 (SG1)
Command : [Expert]#clusterXL_admin up
Now showing SG2 (Security Gateway 2) become Standby
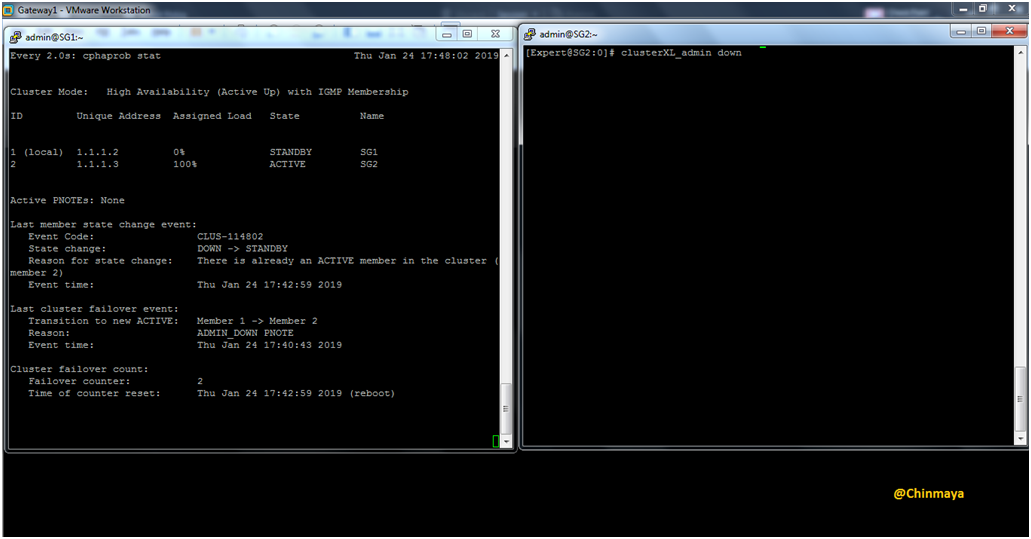
Check the Last failover Time with all details.
Command : Clish> and [Expert]#cphaprob stat

Down the SG2 to active the SG1.
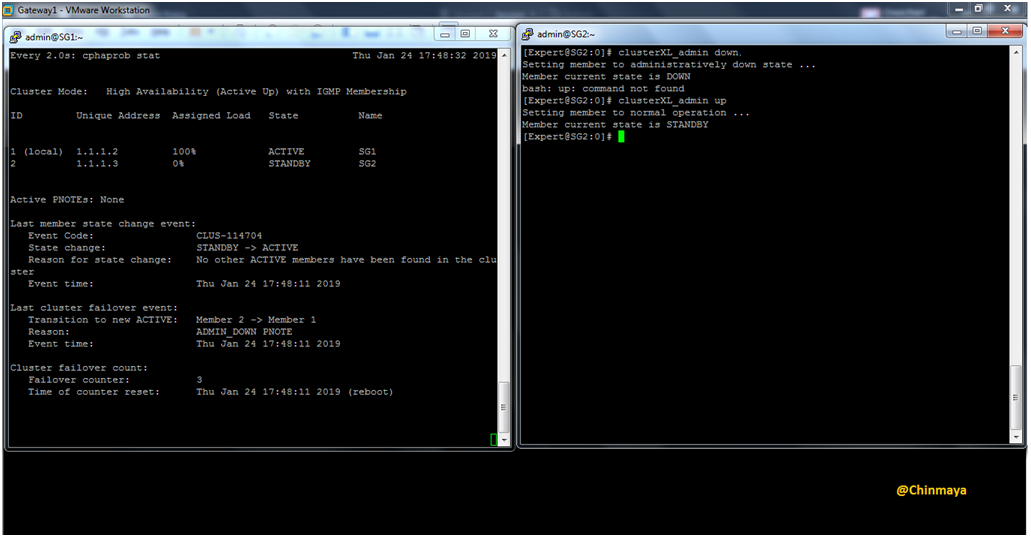
Down the Cluster Member SG2 and UP again
Command : SG2 : [Expert]#clusterXL_admin down
[Expert]#clusterXL_admin up






Leave a Reply