In this post, I am going to cover the complete deployment of Checkpoint Endpoint from scratch. On the upcoming post, I will cover all Blade wise Usecases.
NOTE: I am going to demonstrate on R80.20 GAIA OS but you can use R80.30 or R80.40 for your LAB setup.Also below prerequisites link may me expire so if the link not work then refer the mention SK for download the file.
Prerequisites
GAIA R80.20 ISO for Management Server
Secure Knowledge Details: sk122485
File Name: Check_Point_R80.20_T117_Security_Management.iso
MD5: b2b3abce0d7534eb65a4bd079d6bd8d9
Download Link: https://supportcenter.checkpoint.com/supportcenter/portal?action=portlets.DCFileAction&eventSubmit_doGetdcdetails=&fileid=91745
sk122485 Link: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk122485
R80.20 SmartConsole SecureKnowledge Details: sk122485 File Name: Check_Point_SmartConsole_R80_20_jumbo_HF_B055_Win.exe MD5: 207340a2160aa0b49d292d6b7a0532d9 Download Link: https://supportcenter.checkpoint.com/supportcenter/portal?action=portlets.DCFileAction&eventSubmit_doGetdcdetails=&fileid=94524 sk122485 Link:https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk122485
CPUSE Gaia Deployment Agent SecureKnowledge Details: sk92449 Download Link: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk92449&partition=General&product=All%22
Jumbo Hotfix Accumulator for R80.20 SecureKnowledge Details: sk137592 Download Link: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk137592
Endpoint Security Client SecureKnowledge Details: sk117536 Download Link:https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk117536
Anti–Malware HotFix (Anti-Malware signature updates (E1 engine) for Endpoint Management Server) SecureKnowledge Details: sk127074 File Name: Check_Point_EP_AM_updater_T16_sk127074_FULL.tgz MD5: 342c5d8f1c24cf27f52ea7e3216bfea6 Download Link: https://supportcenter.checkpoint.com/supportcenter/portal/role/supportcenterUser/page/default.psml/media-type/html?action=portlets.DCFileAction&eventSubmit_doGetdcdetails=&fileid=66684 sk127074 Link:https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk127074
GAIA R80.20 ISO for Security Gateway NOTE: R80.20 Gateway use for give internet access to the internal LAN and Smart Endpoint Server NOTE: You can also use any third-party firewall or router for this lab SecureKnowledge Details: sk122485 File Name: Check_Point_R80.20_T101_Security_Gateway.iso MD5: d0f1a973dd30fd4f4d58c36bd18e0b59 Download Link: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk122485
Windows 7 and Windows Server 2008 R2 Service Pack 1 KnowledgBase Details: KB976932 Download Link: https://www.microsoft.com/en-in/download/details.aspx?id=5842
Microsoft .NET Framework 4.6.2 for Windows 7 SP1 Download Link: https://www.microsoft.com/en-us/download/details.aspx?id=53344
Security Update for Windows 7 for x64-based Systems KnowledgeBase Details: KB3033929 Download Link: https://www.microsoft.com/en-us/download/details.aspx?id=46148
LAB Topology
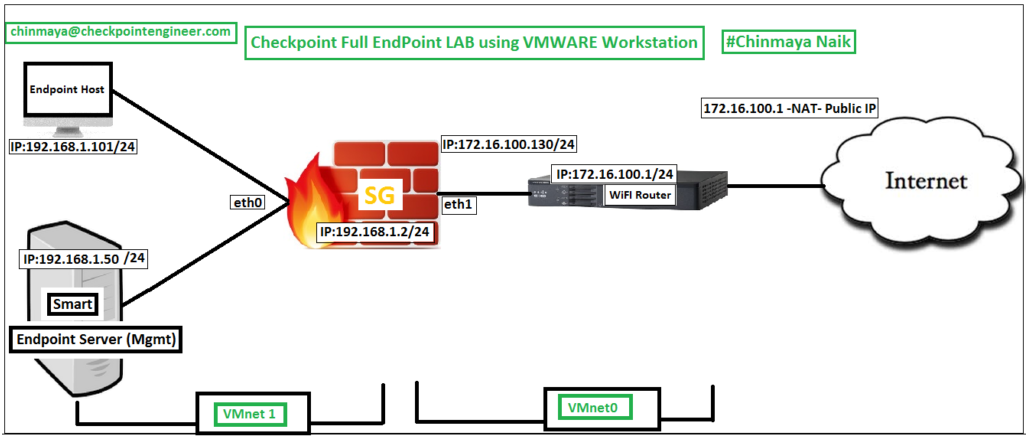
VMNET Details
VMnet1: Host-Only : 192.168.1.0/24 VMnet0: Auto-Bridging : 172.16.100.0/24
IP Address Details
Physical HOST Machine(Where VMware is running)> 172.16.100.120/24 SmartEndpoint Server > 192.168.1.50/24 Test Host Machine > 192.168.1.101/24 Security Gateway > Internal (eth0) > 192.168.1.2/24 | External (eth1) --> 172.16.100.130/24
Route
Internal LAN (192.168.1.0/24) ---> Default Gateway (IP:192.168.1.2/24) Test Host Machine (192.168.1.101/24) ---> Default Gateway (IP: 192.168.1.2/24) Smart Endpoint Server (192.168.1.50/24) ---> Default Gateway (IP: 192.168.1.2/24) Gateway (172.16.100.130/24) ---> Default Gateway (IP:172.16.100.1/24)
STEP: Create a New Virtual Machine –> Next
STEP2 : Select browse for select the ISO image.
STEP3: Click “Next”.

STEP4 : Select the Guest operating system : Other and version : Other 64-bit.
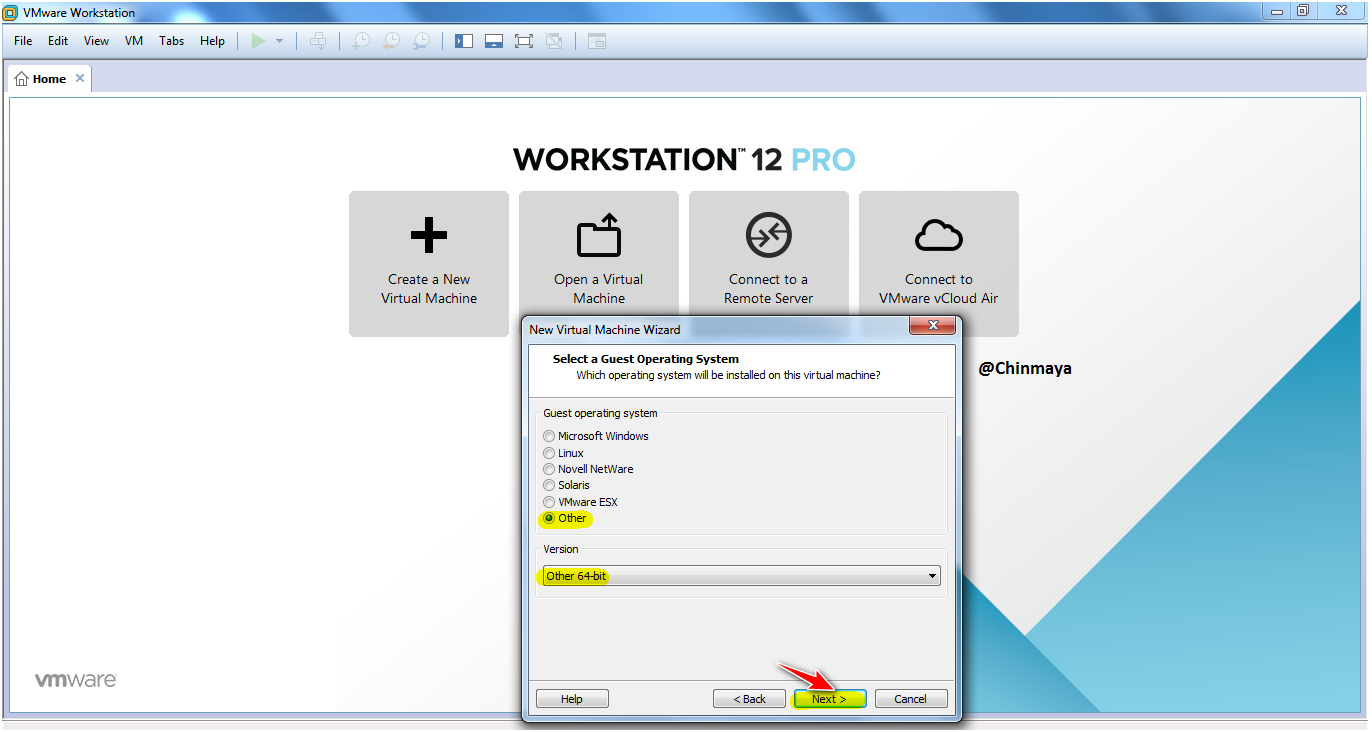
STEP5 : Click “Next”.
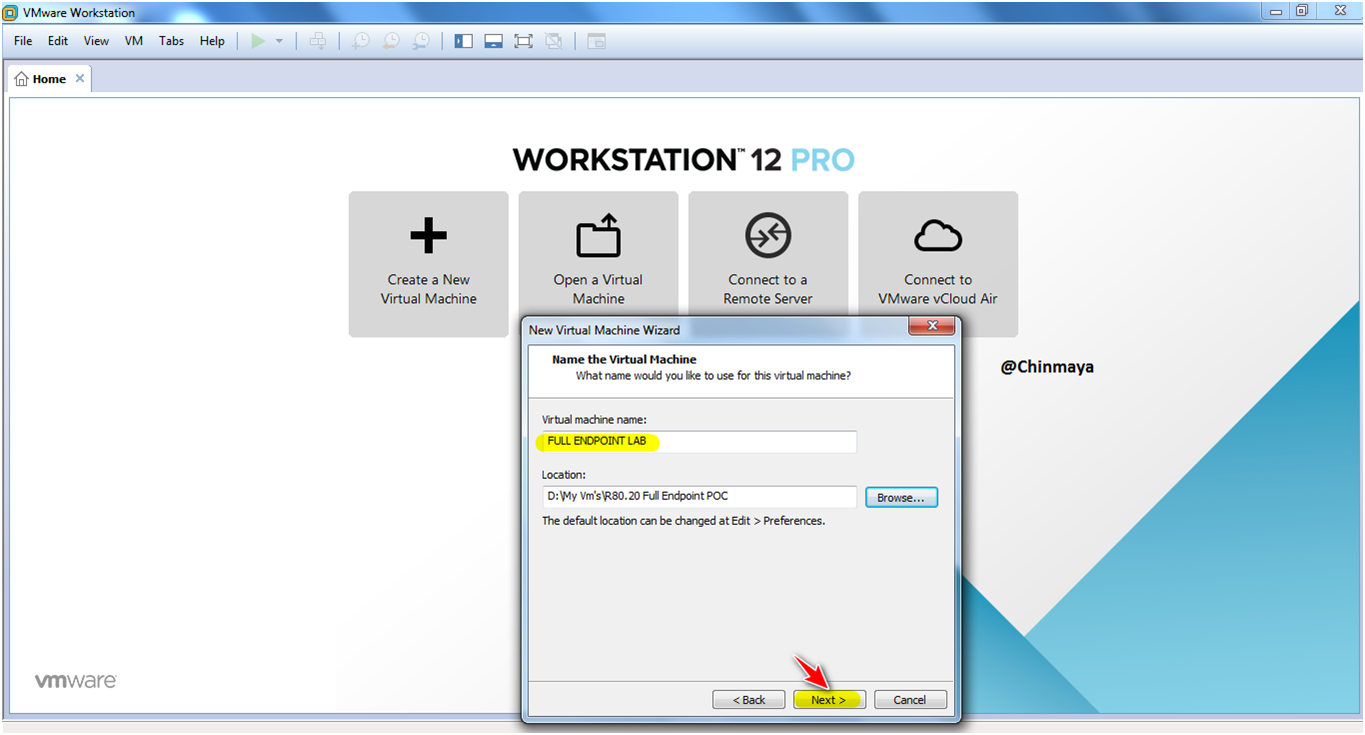
STEP6: Select Disk Size :100 GB , and select “store virtual disk as a single file”.
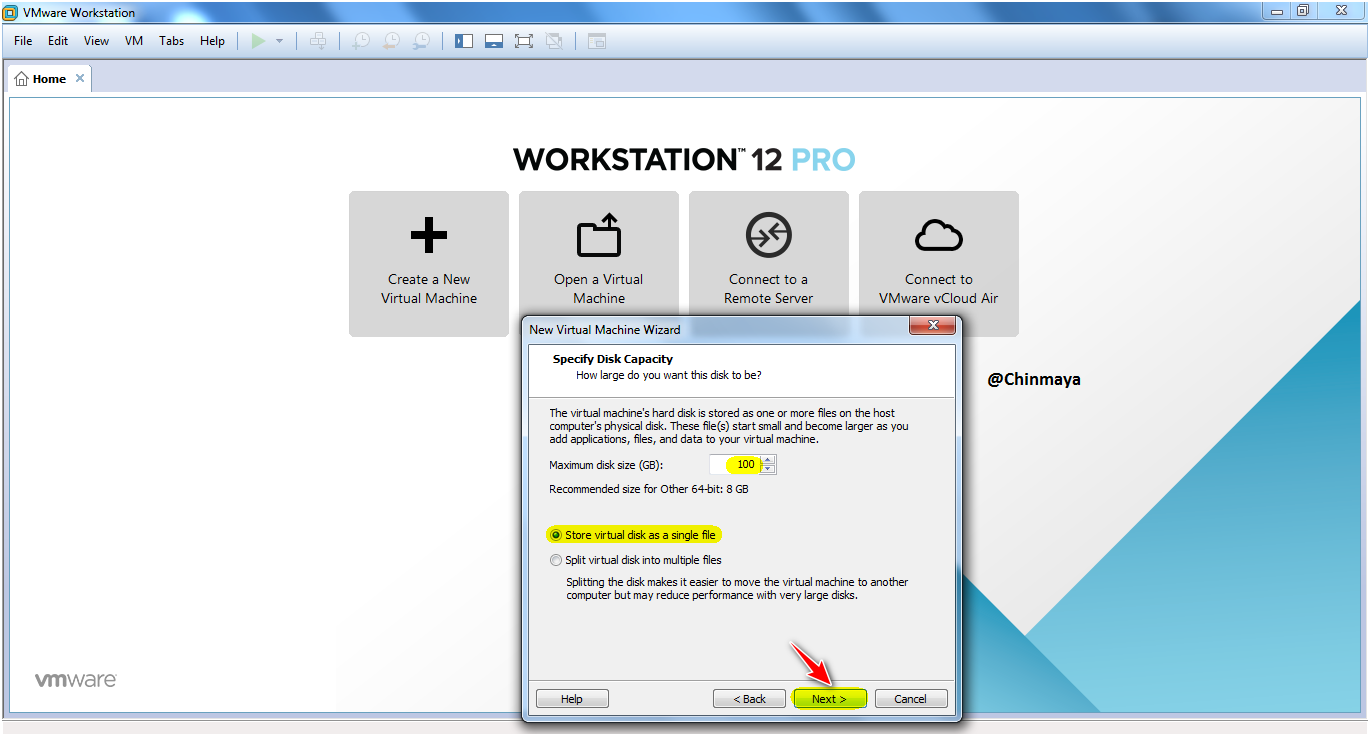
STEP : Click “Finish”.

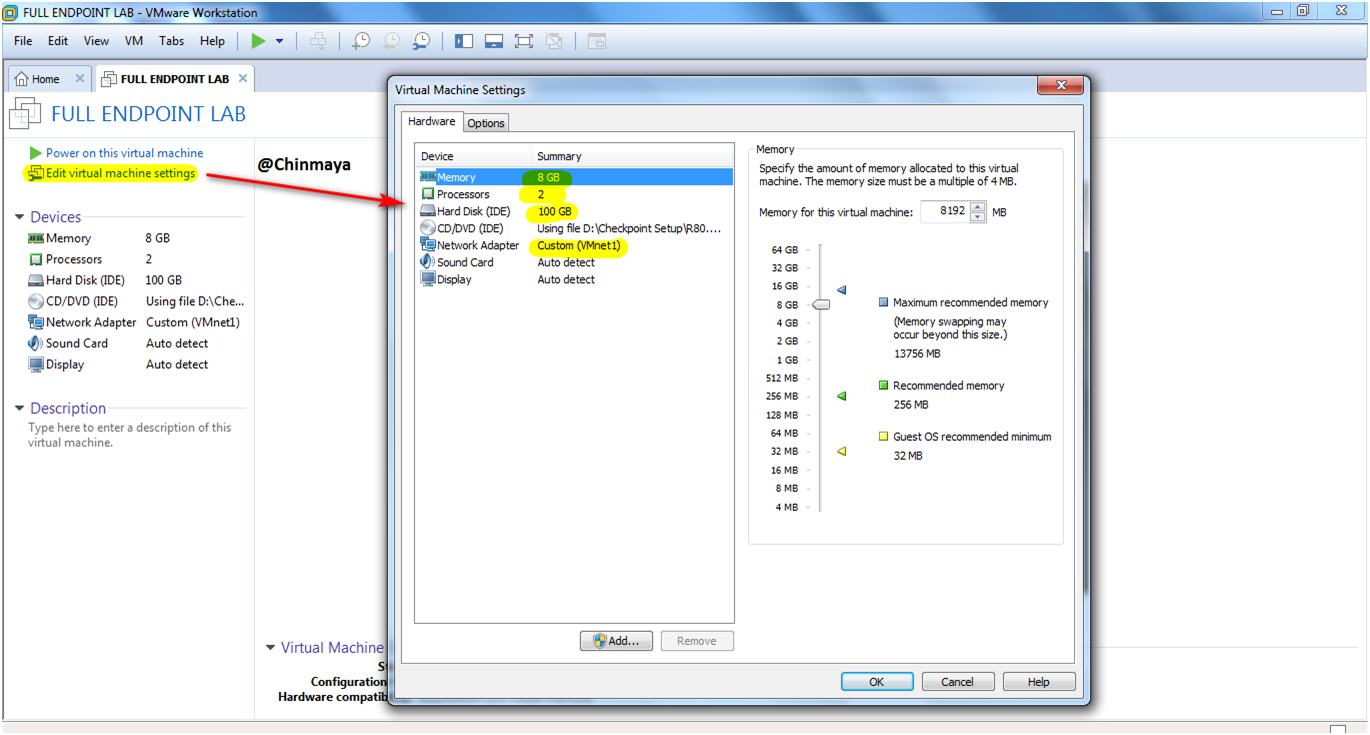
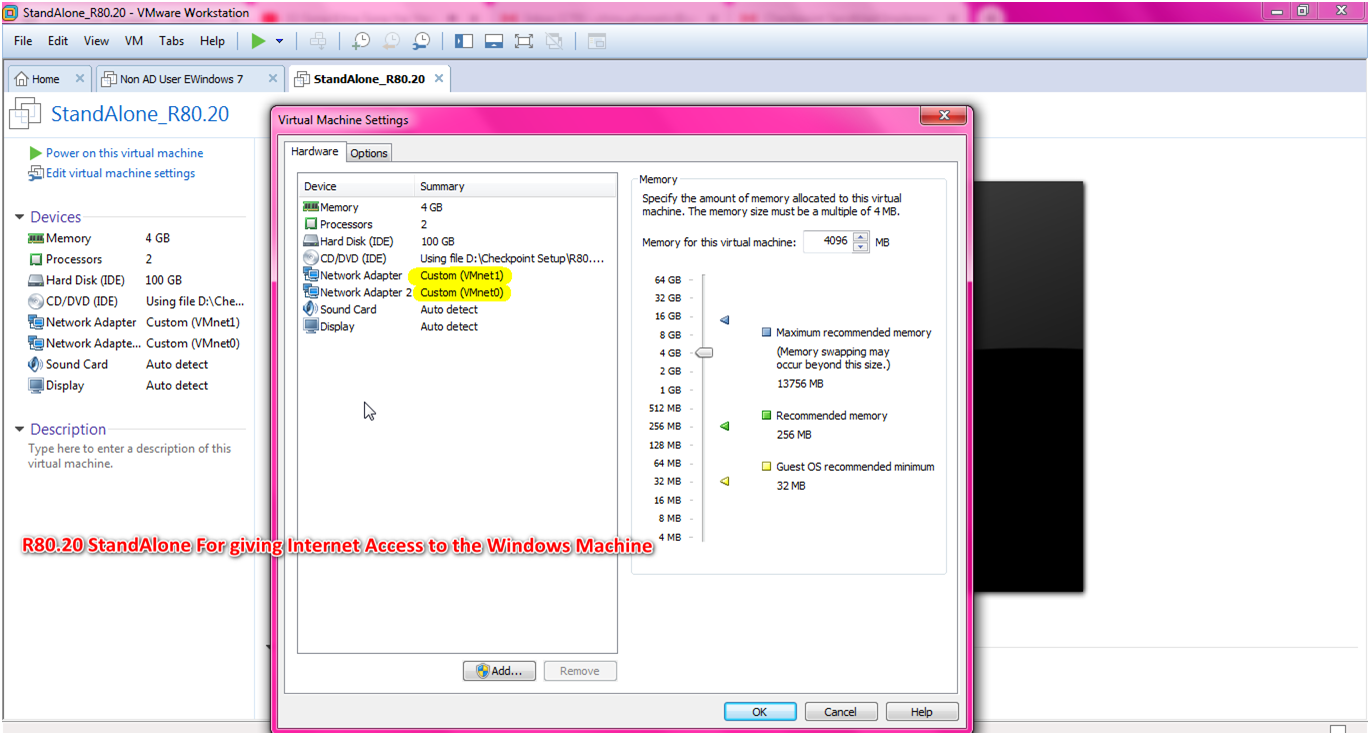
STEP : Select Network Adapter : VMnet (192.168.1.0/24), Memory :8 GB ,Processor:2.
NOTE: Configuration is vary depends upon the requirement but if you are using VMWARE for LAB setup then you can also use minimum memory : 4GB.
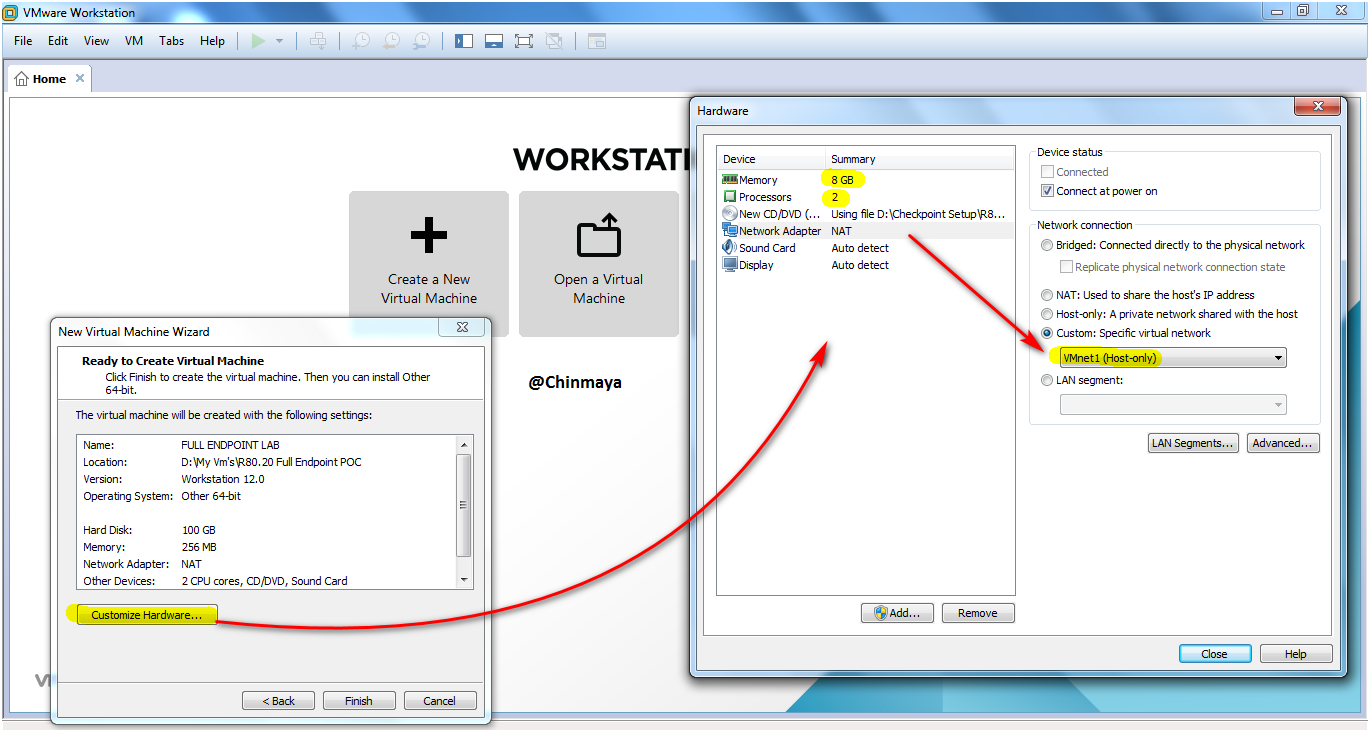
STEP : Edit the virtual machine setting for verification.
STEP : Power on the virtual machine.

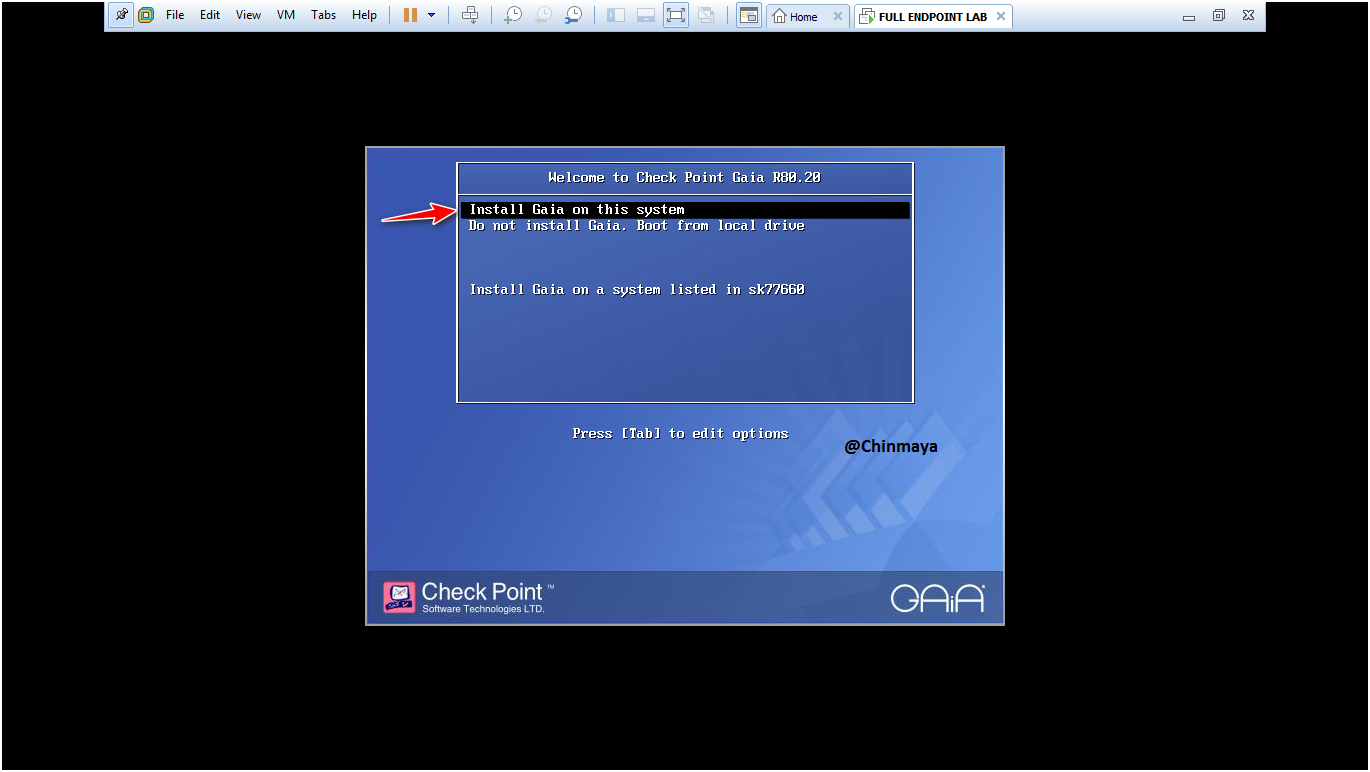
STEP : Select “Install Gaia on this system”
STEP : Click “OK”.

STEP : Select “US” and Click “OK”.
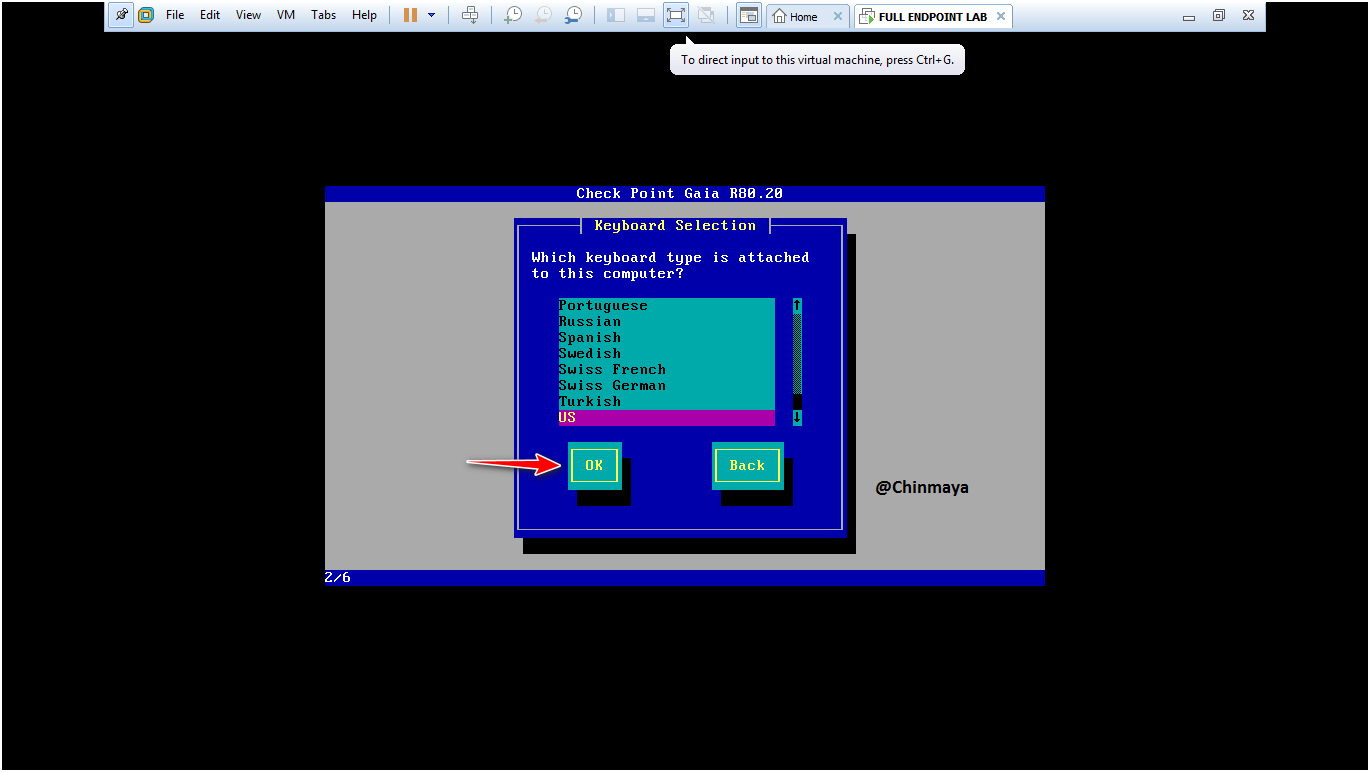
STEP: Change the Disk Size or you can leave as is it and Click “OK”.
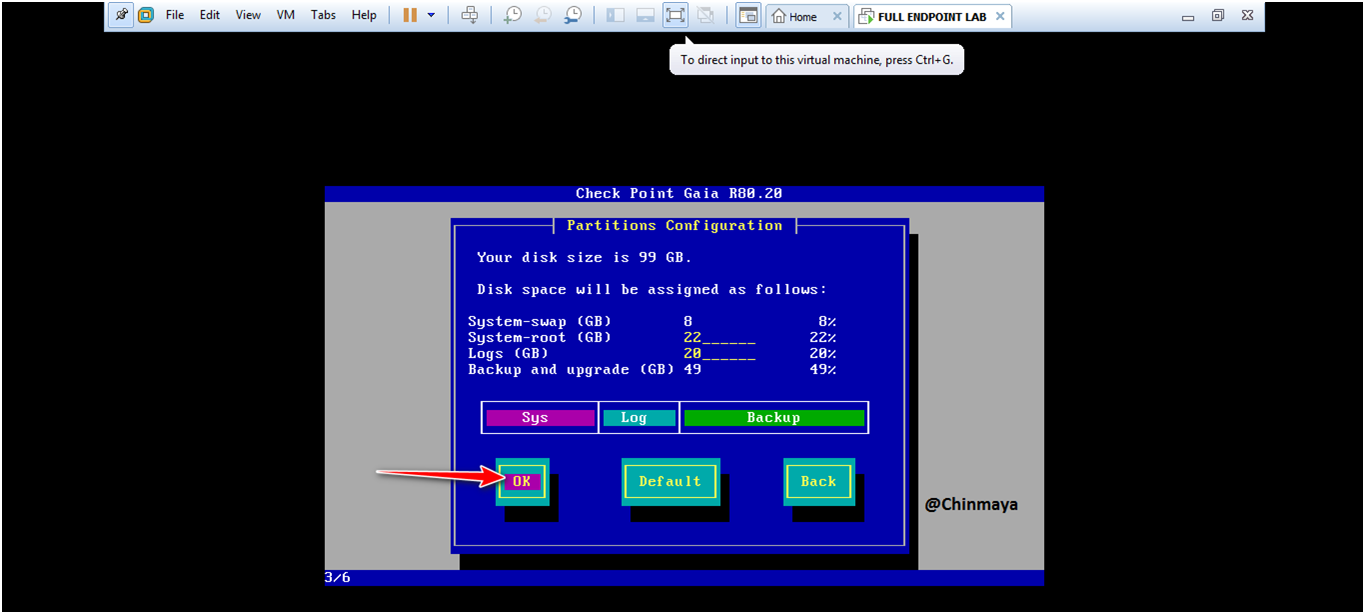
STEP: Assign password and click “OK” .
NOTE: CapsLk must be enable when you assign the password.

STEP: Assign IP address to the Management Server with netmask and click “OK”.
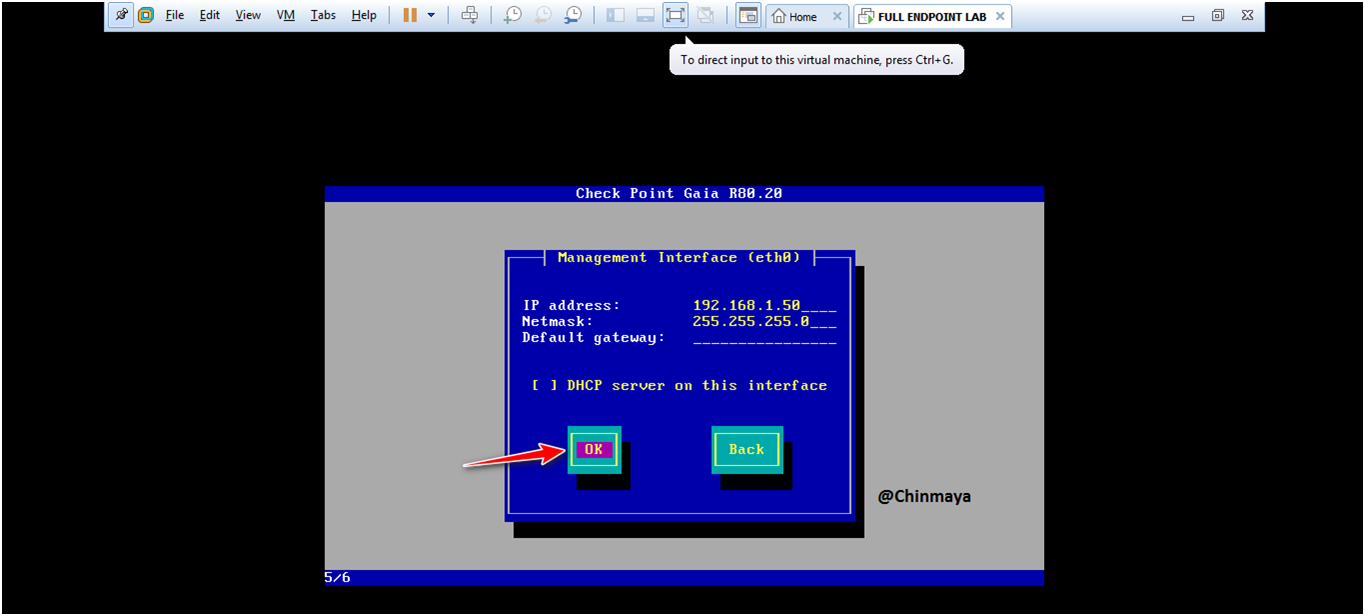
STEP :Click “OK”.
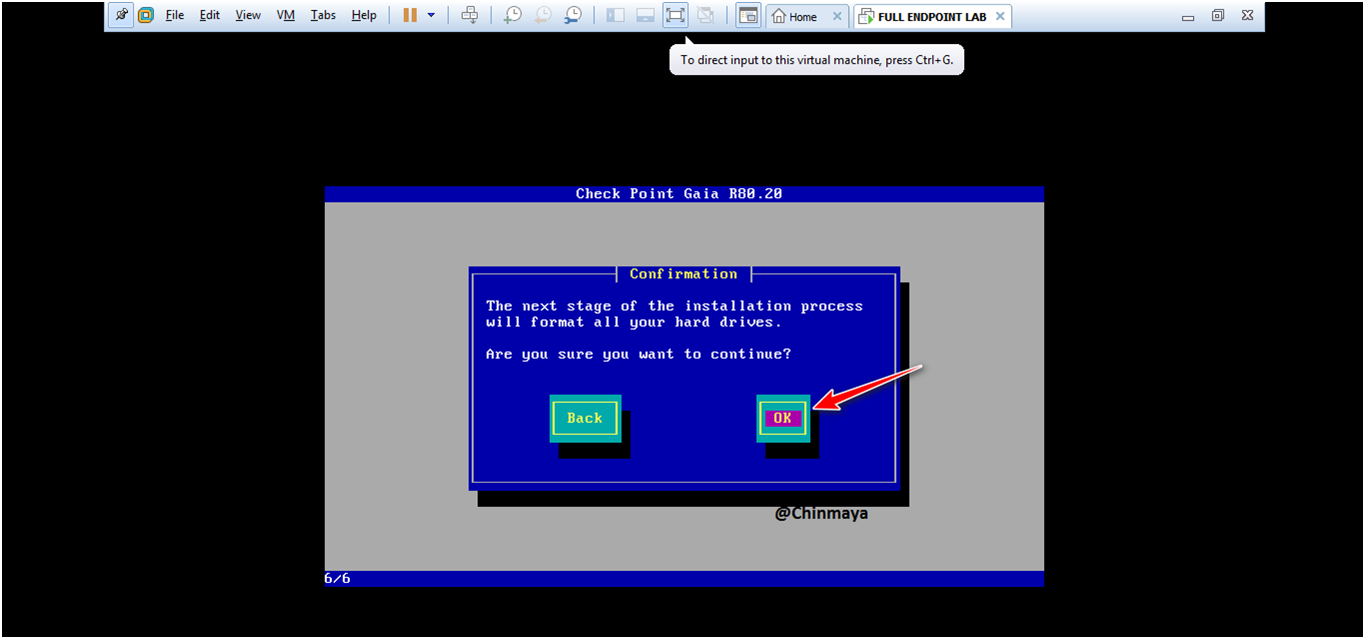
STEP: Select “Reboot”.

STEP : Check the IP address via CLI to run the First Time Configuration Wizard.
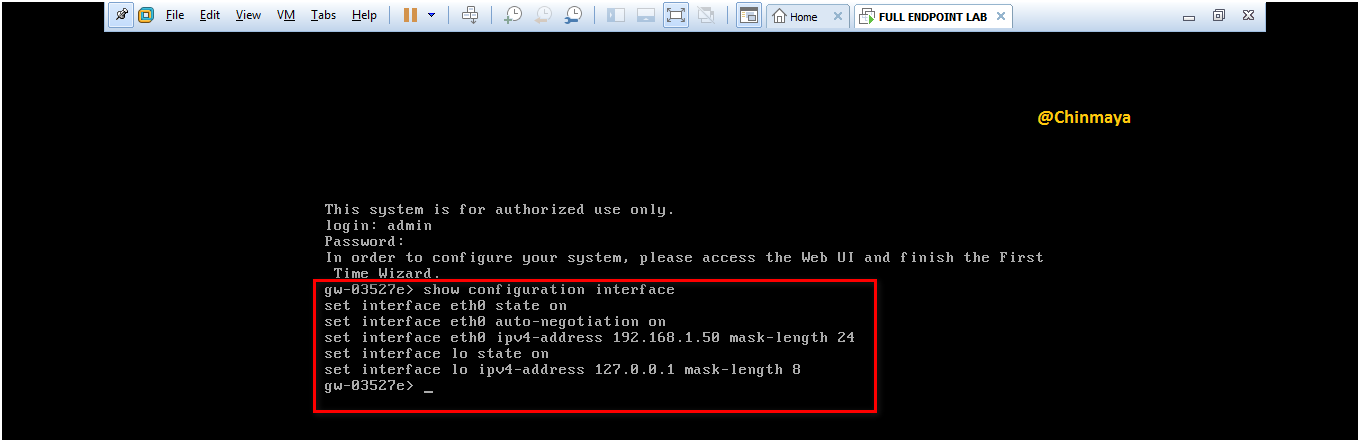
STEP : Give the credentials (Refer STEP 🙂 and click Login.
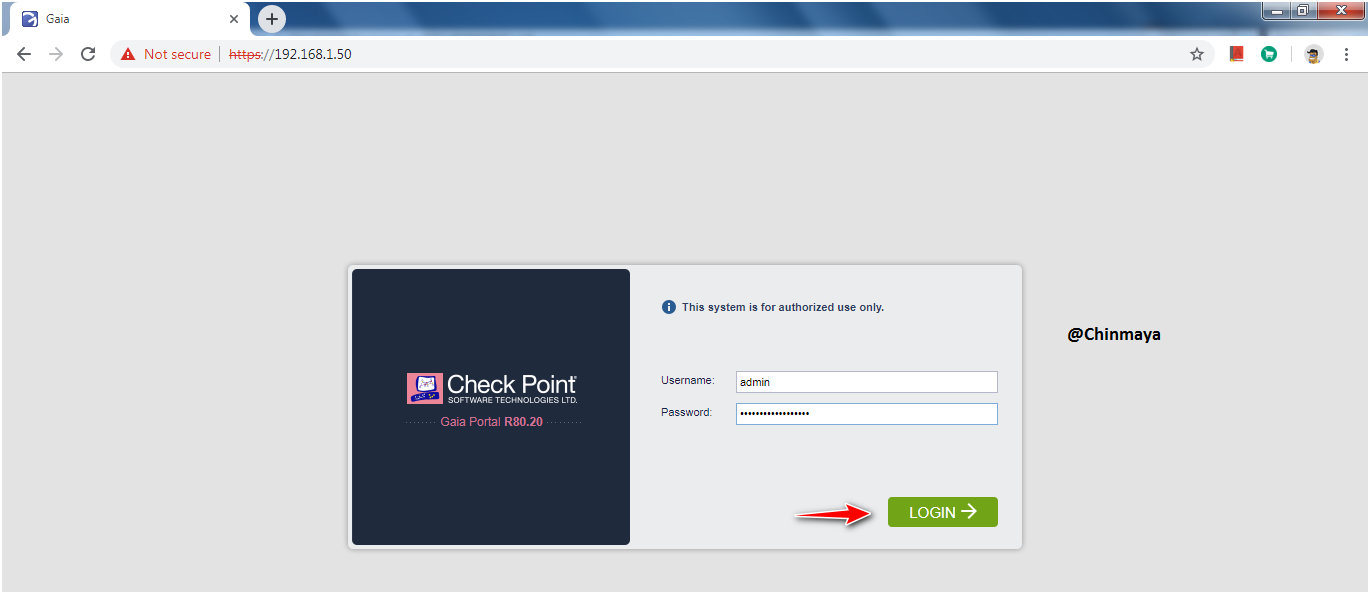
STEP :Click “Next”.

STEP : Select “Continue with R80.20 configuration” and click “Next”.
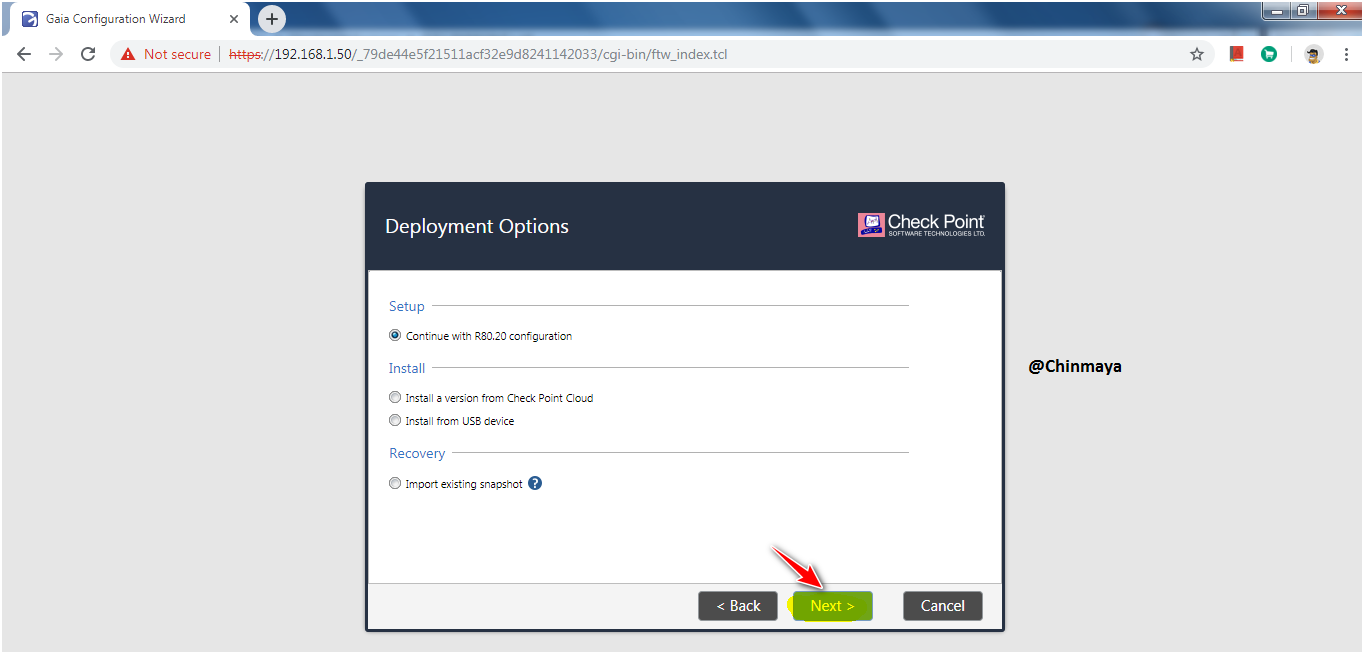
STEP : You can also change the IP address if you want.
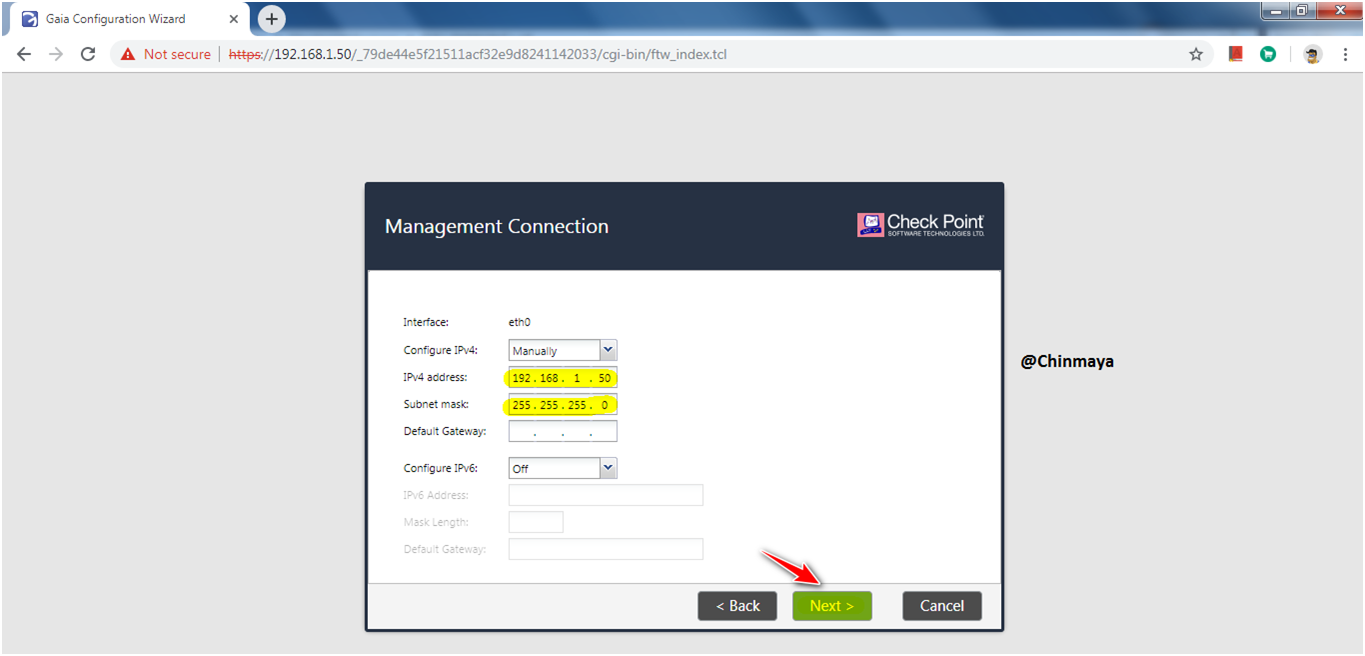
STEP : Login with GAIA WebUI by giving credentials and then start run the First Time Configuration wizard.
STEP: Assign hostname.
Name: FULL-END-LAB
Refer my previous link to installing Security Managemnt Server
STEP: Select Time manually and verify the time & Date and click “Next”.
STEP : Select “Security Management” and Click “Next”.
STEP : Select Default Security Management as “Primary” and click “Next”.
STEP : Select “Use Gaia administrator admin” and click “Next”. (For accessing GUI Client like Smart Console)
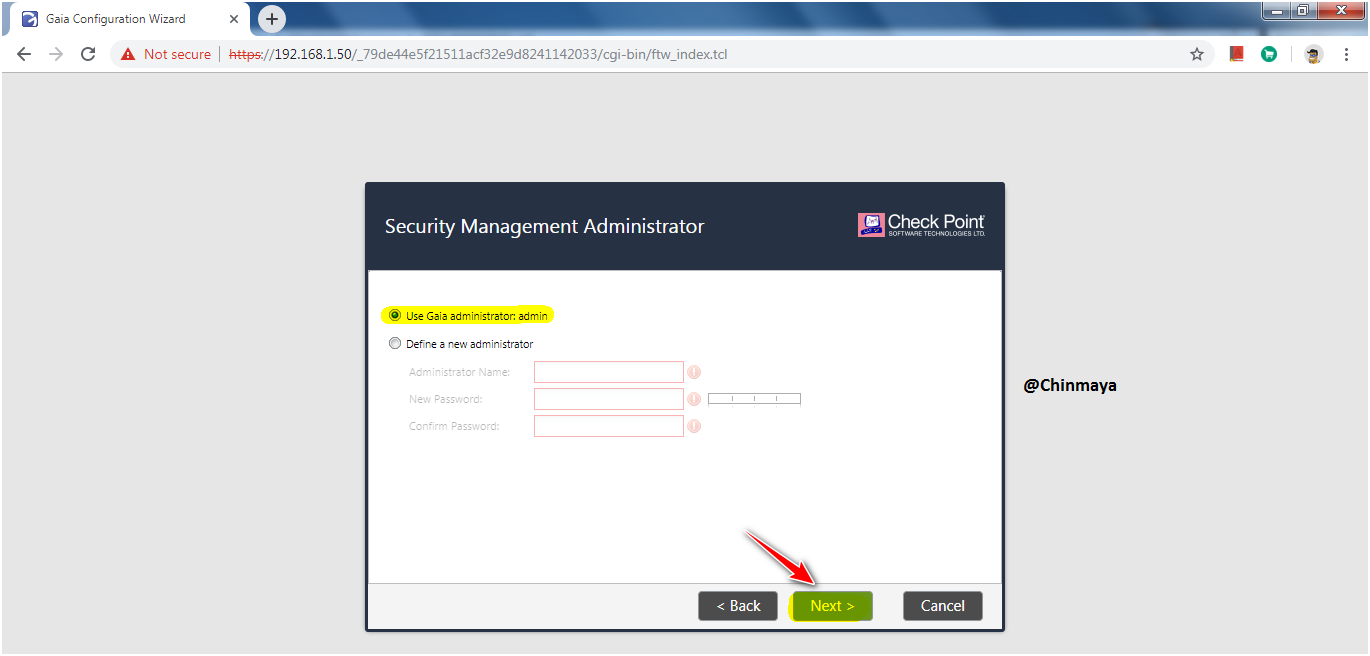
STEP: Select “Any IP address” or you can also define as Network, Machine or range of IP address to access GUI client SmartConsole.
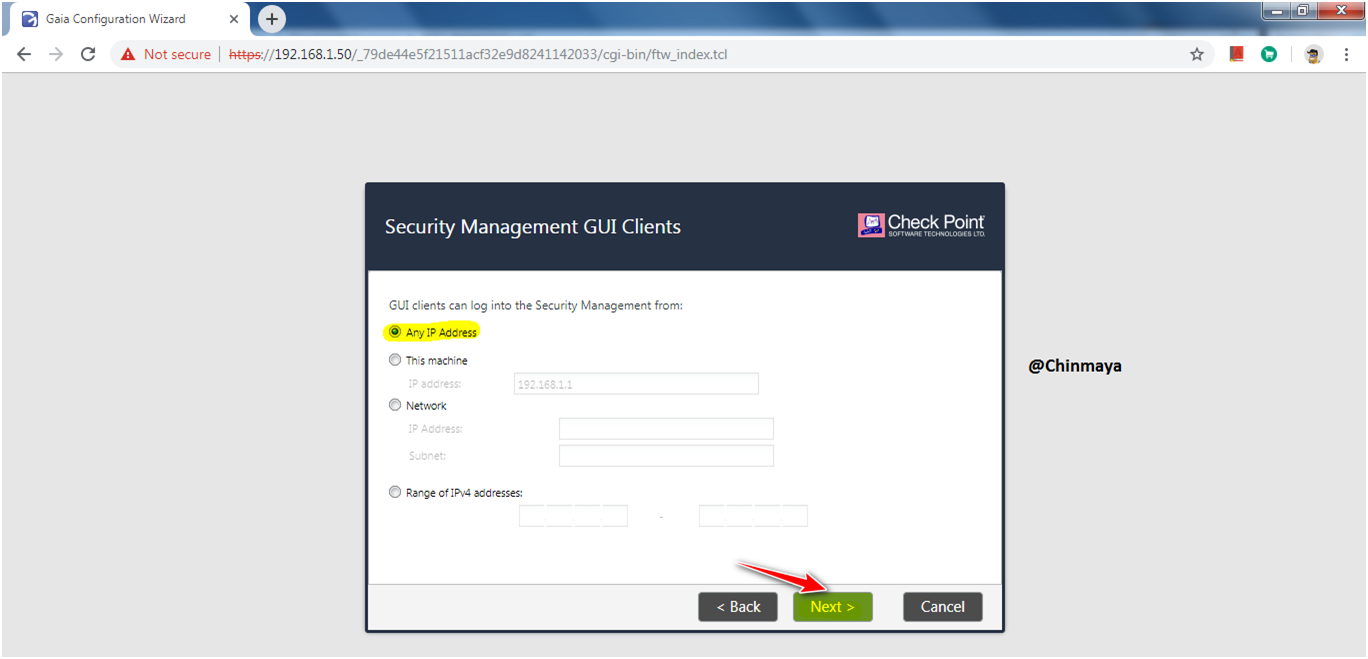
STEP: Select “Finish” to complete the First Time Configuration Wizard.
STEP : Click “Yes”.

STEP : Click “OK”.

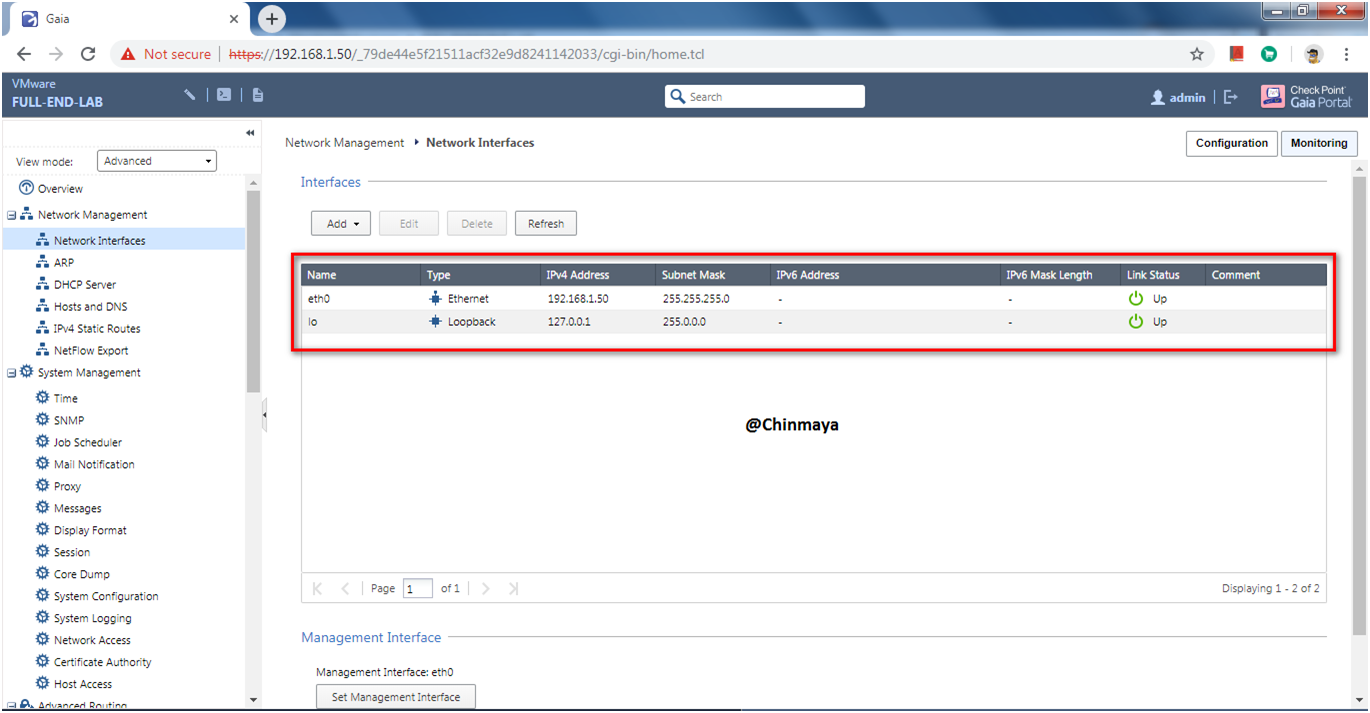
STEP : Check the Network Interface status.
STEP : Open the putty and give the IP address of the Management Server for CLI access.
STEP : Click “Yes”.
STEP : Verify the interface configuration by below command.
command : CLISH>show configuration interface
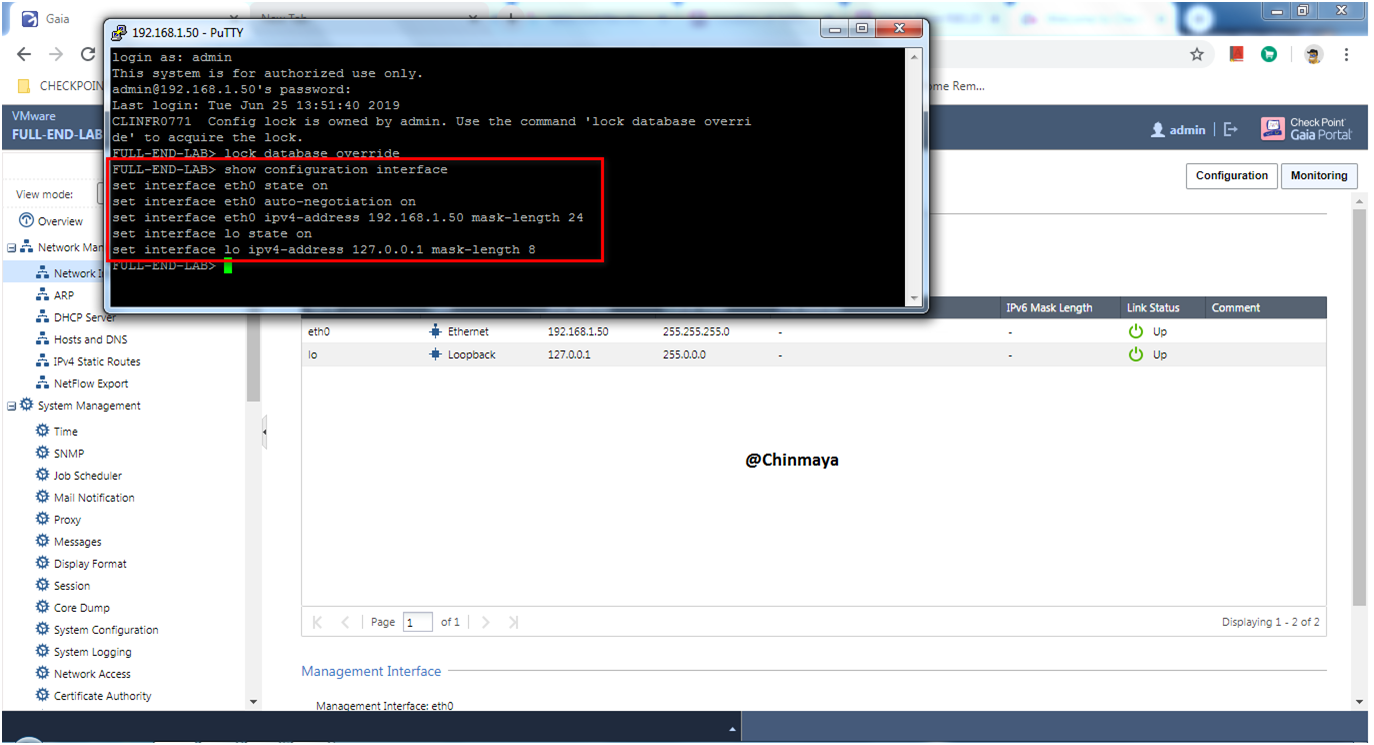
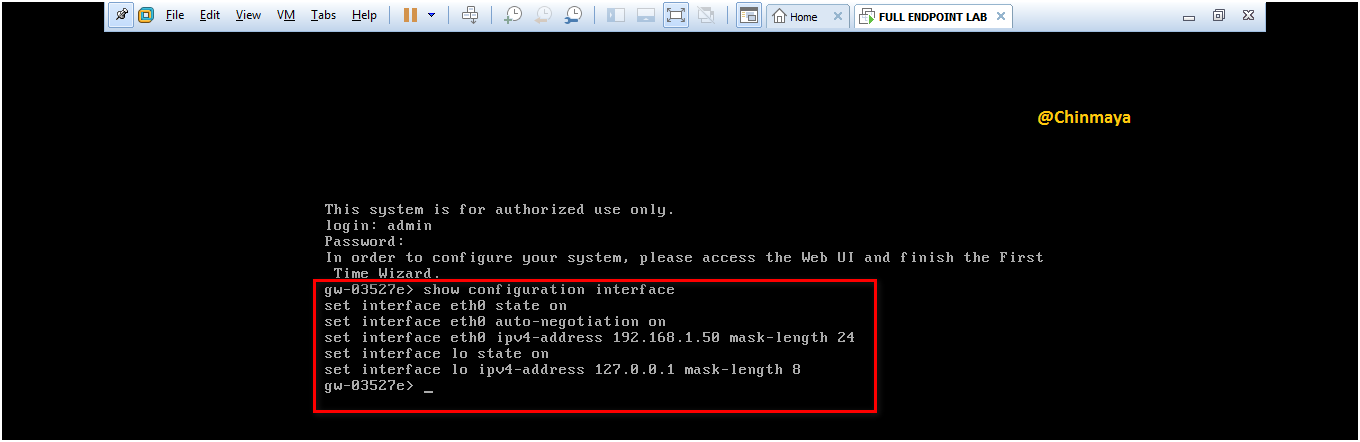
STEP :Next to install the CPUSE Gaia Deployment Agent.
Refer SK92449.
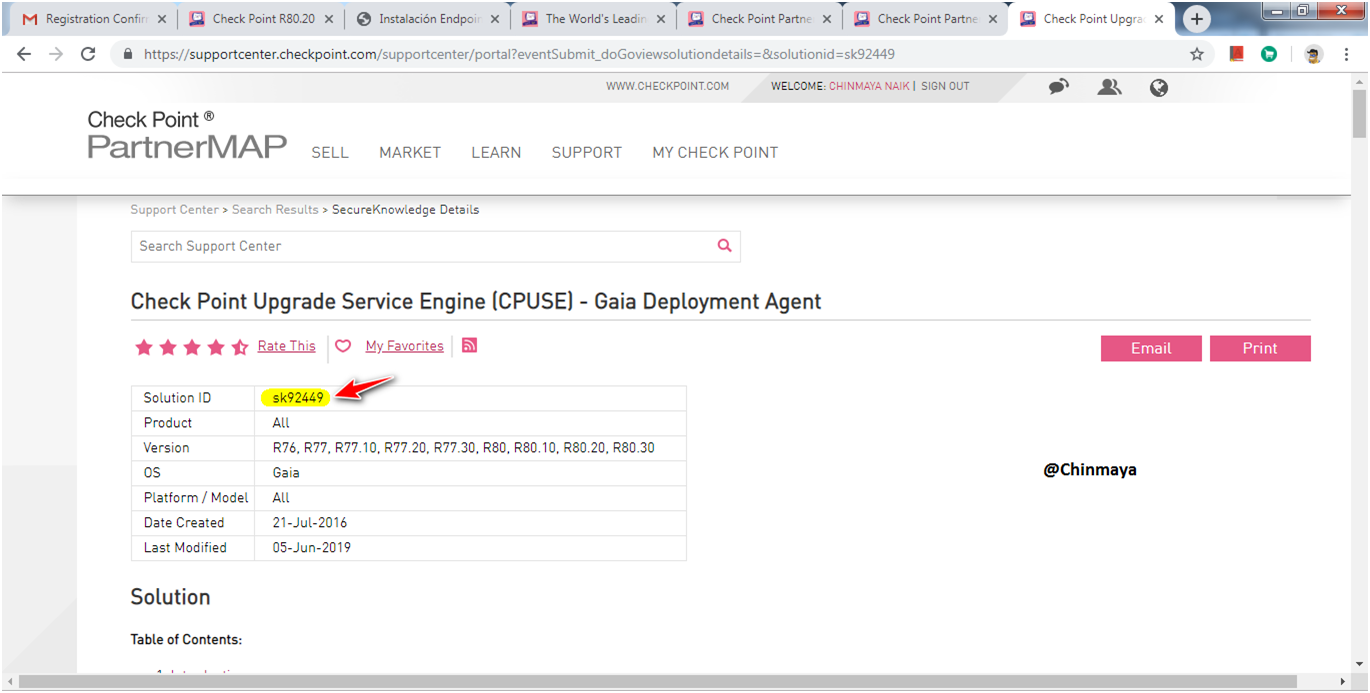
STEP : Download the latest CPUSE Deployment Agent Build.
NOTE : Always download the latest build.

STEP : Note the MD5 value for verification.
Click “Download”.
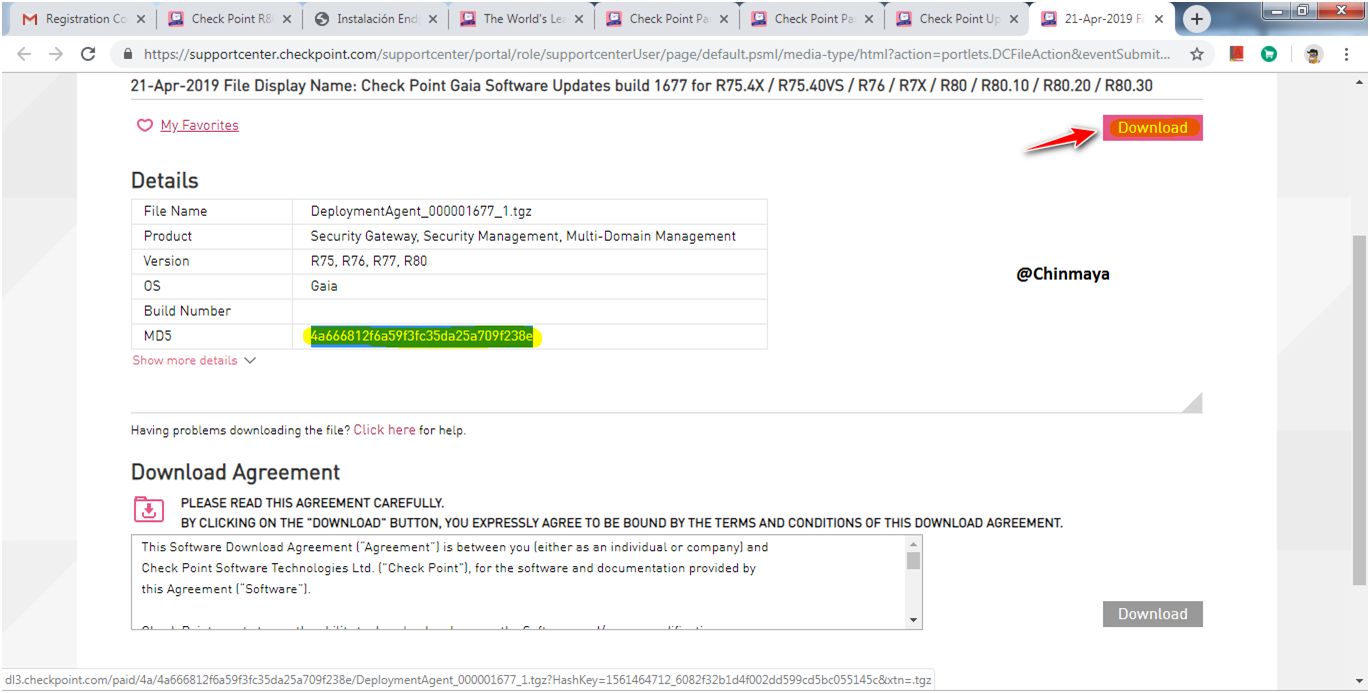
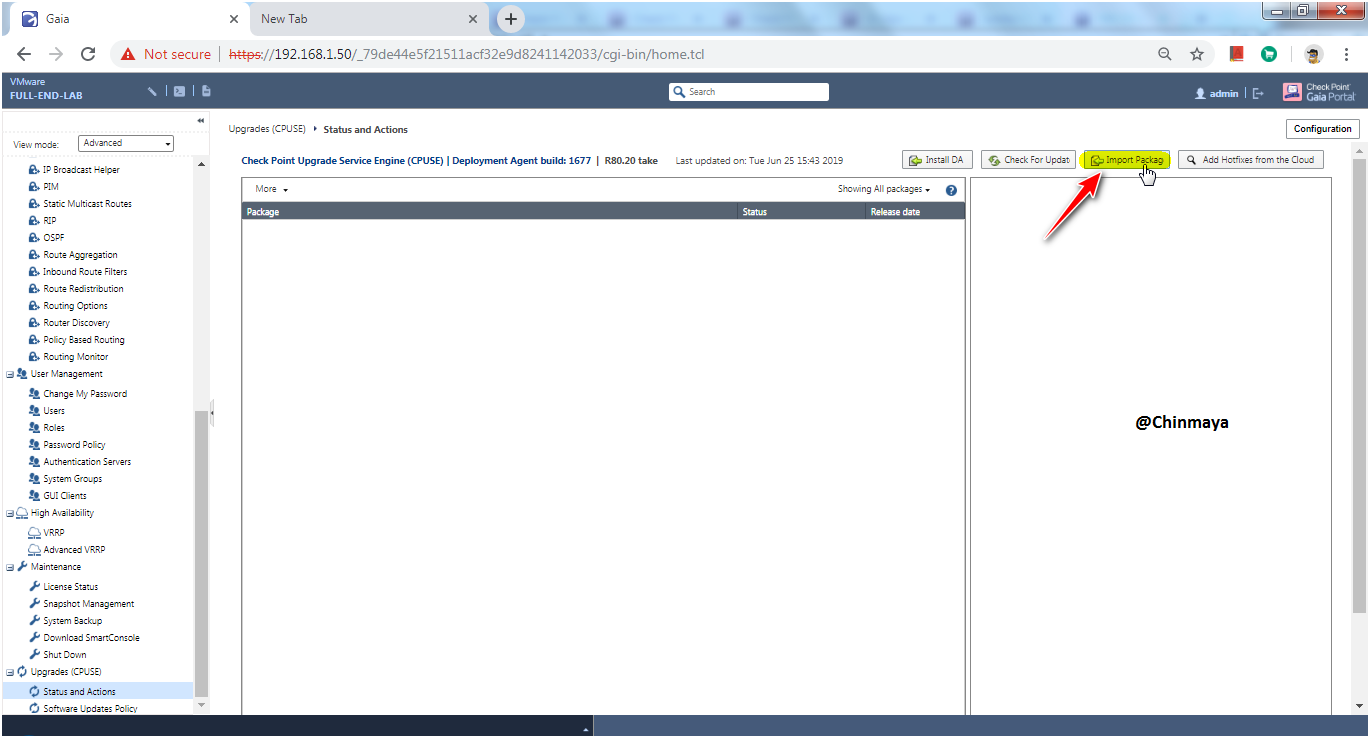
STEP : Import the CUSE Package.
Go to ---> GAIA WebUI ---> Install DA ---> Click "Browse" ---> After Browse ---> click "Install"



STEP : Deployment Agent update successfully.

Jumbo HotFix Installation
STEP :Install the latest Jumbo HotFix.
Refer sk137592 for download the Jumbo HotFix Take.
NOTE: Always install the latest Jumbo Take.
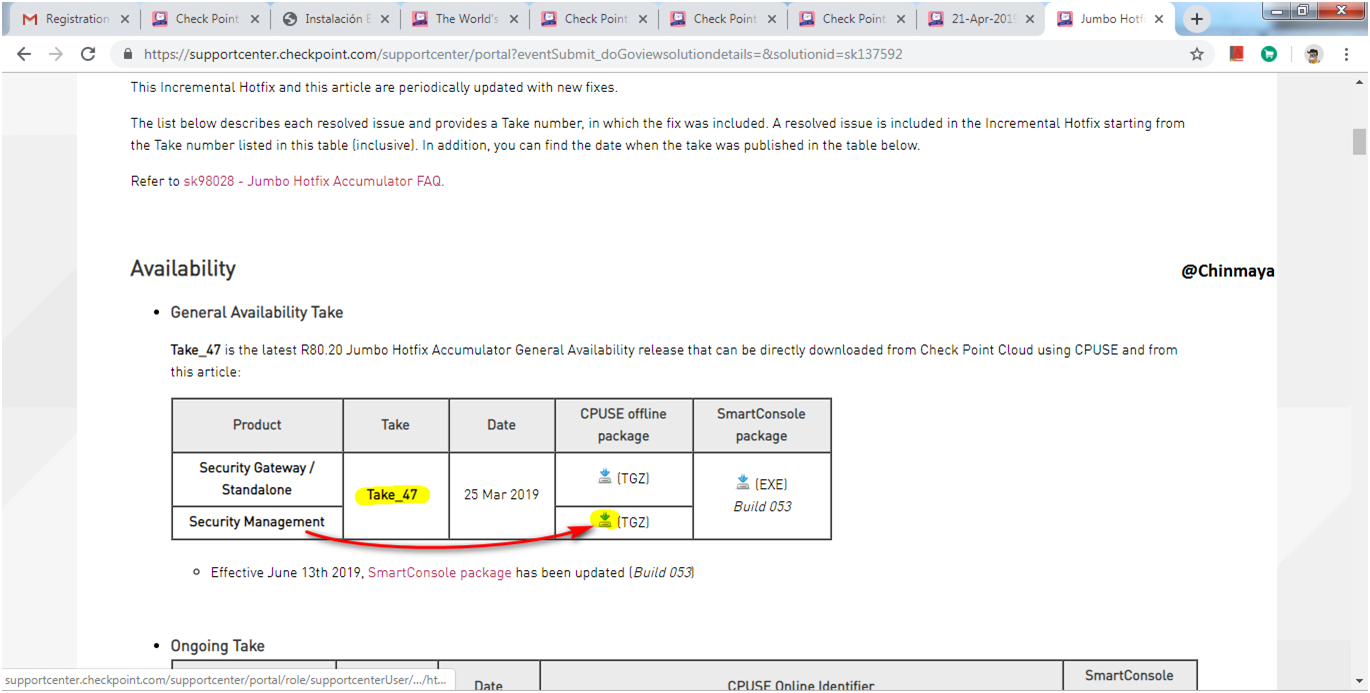
NOTE : Check the MD5 value for verification.
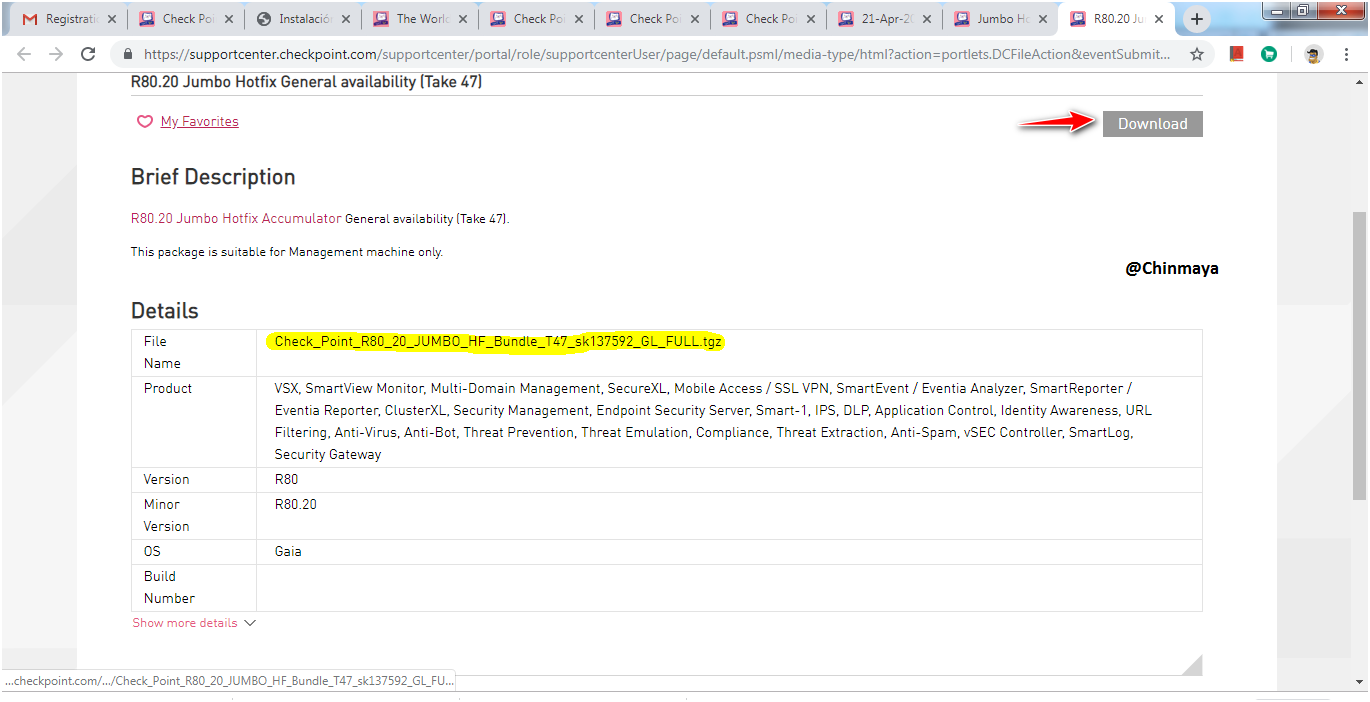
STEP : For installation the Jumbo HotFix.
Go to -- -> GAIA WebUI ---> Status and Action ---> Import Package ---> Select the Jumbo HotFix ---> Import the Package ---> Browse the package

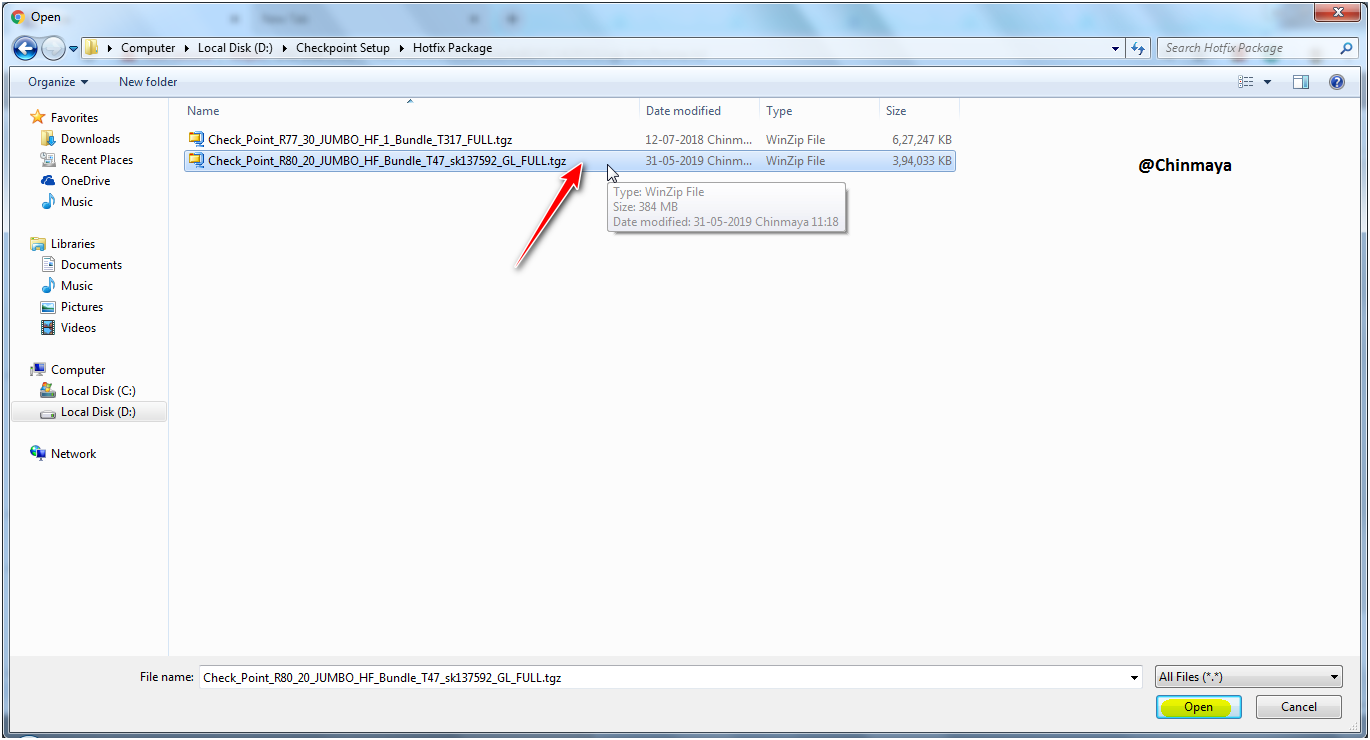
STEP : Click “Import” to importing the package.
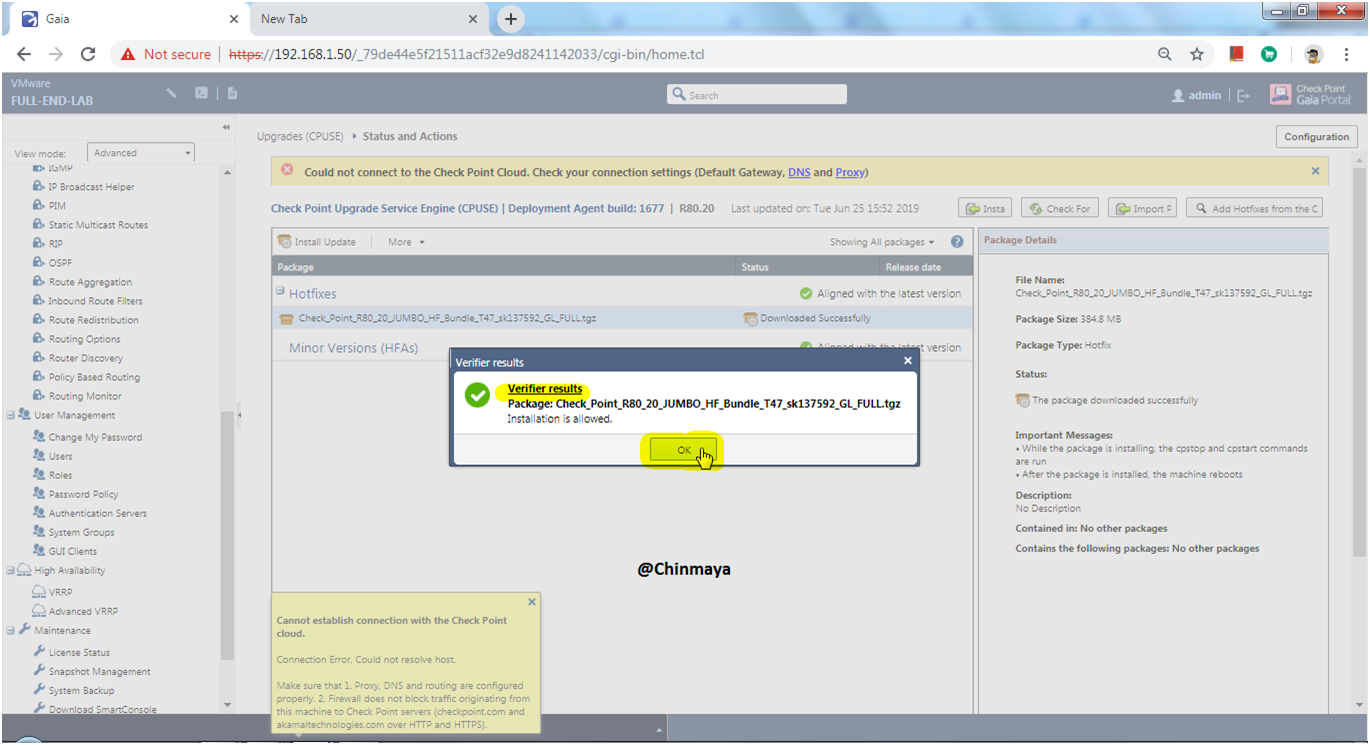
STEP: Click “Verify” to verify the package that I import.

STEP: Click “Ok” after successfully import.
NOTE: In case if you face any issue then check the MD5 of the package and also verify the package compatibility. Also its going to reboot once installed completed.
STEP: Click on “Install Update” and click “OK”.
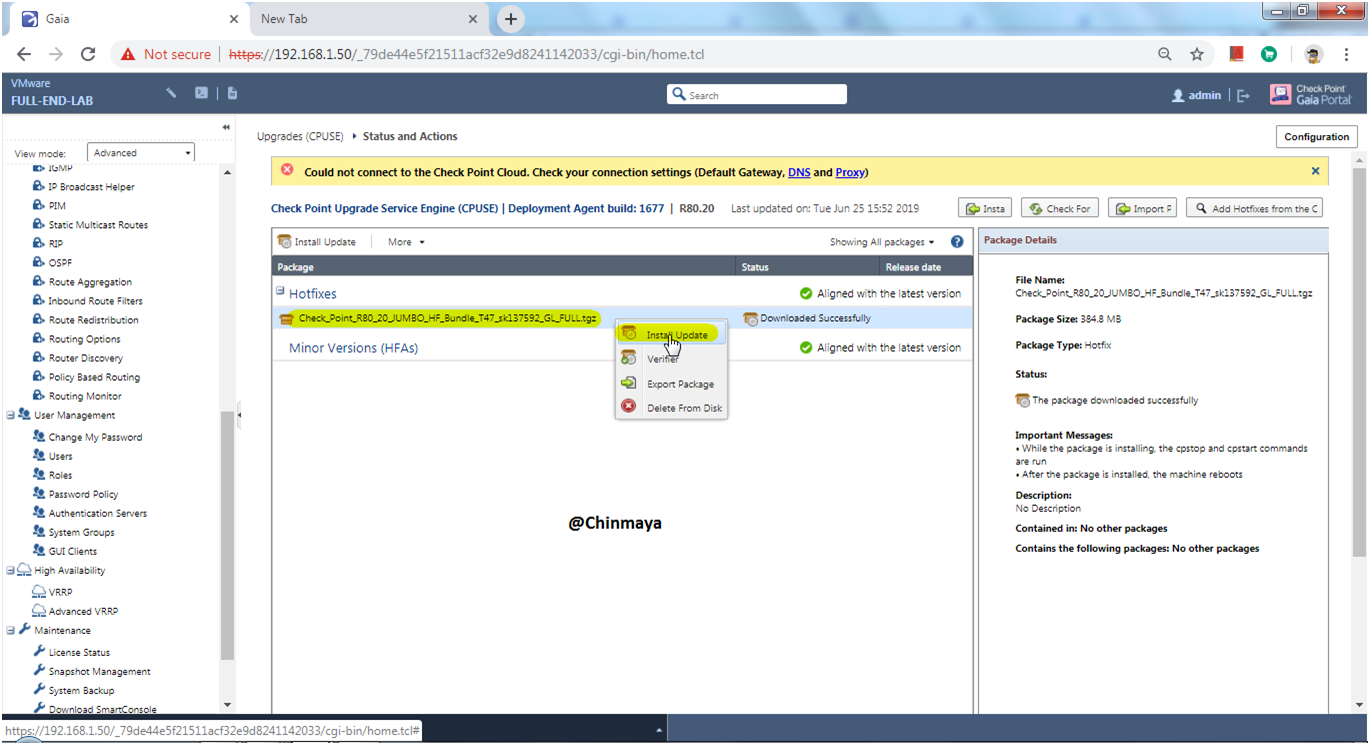
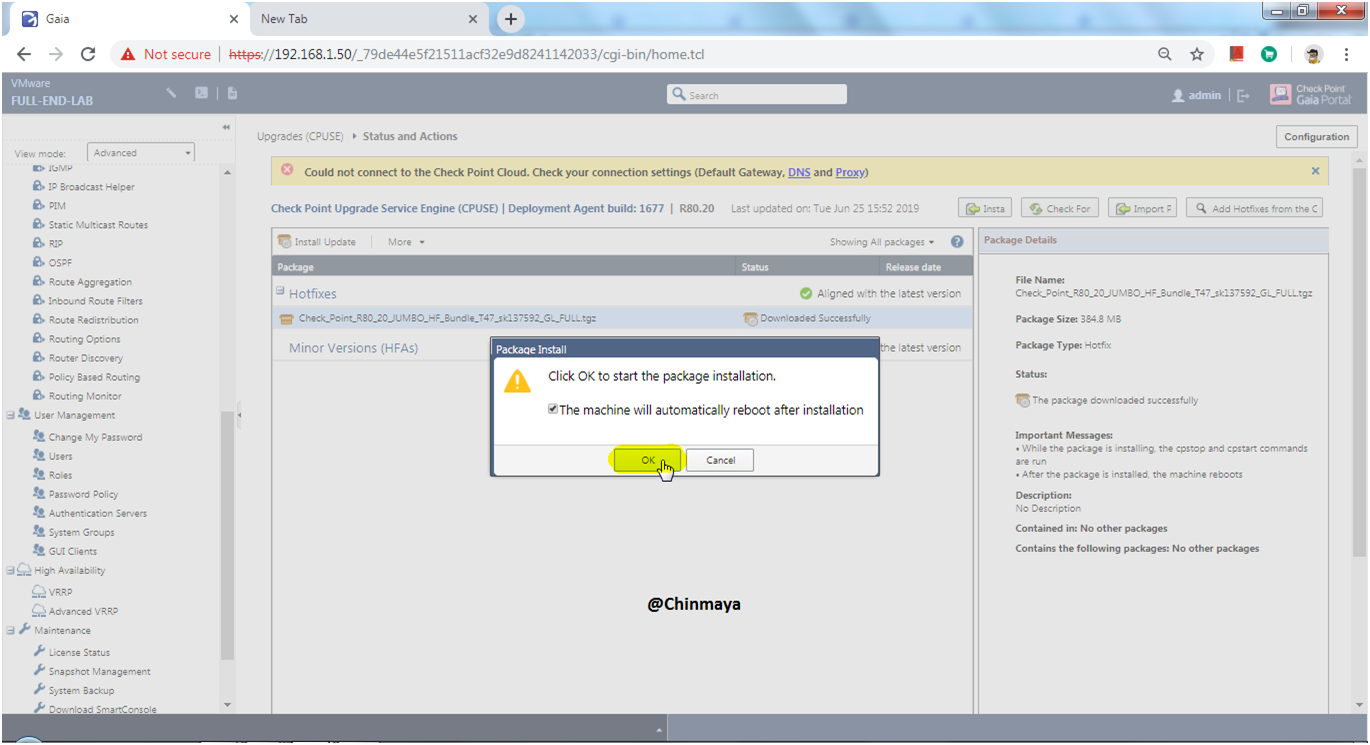

STEP: Login to GAIA portal.
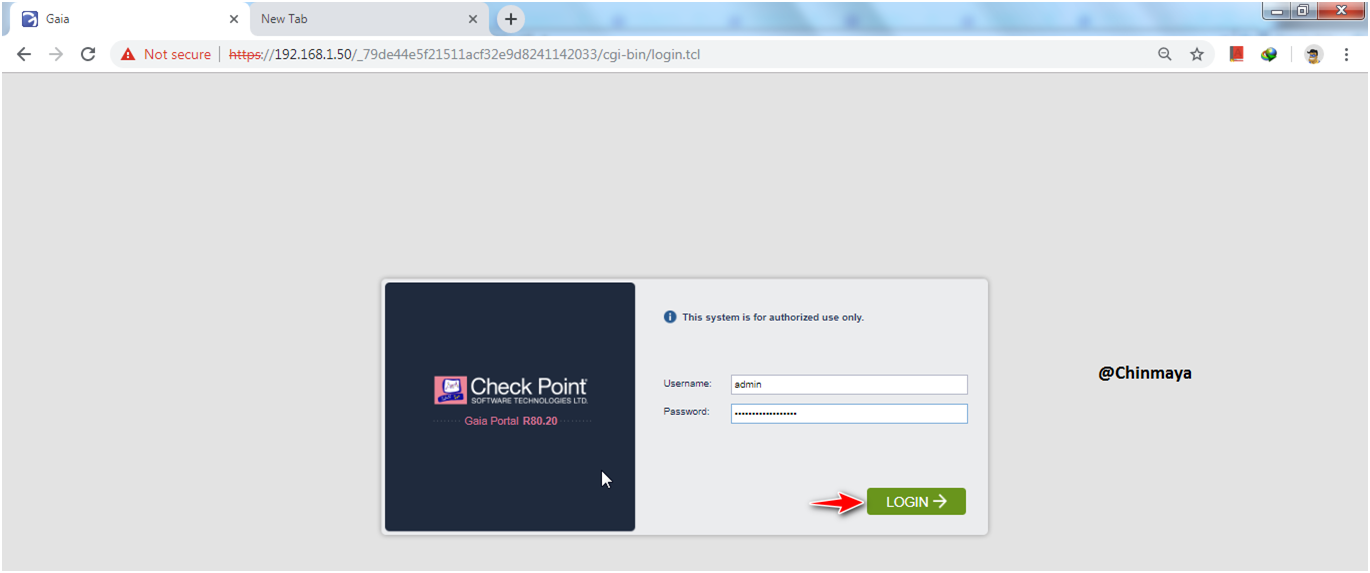
STEP: Click “All” to verify that HotFix is install successfully.

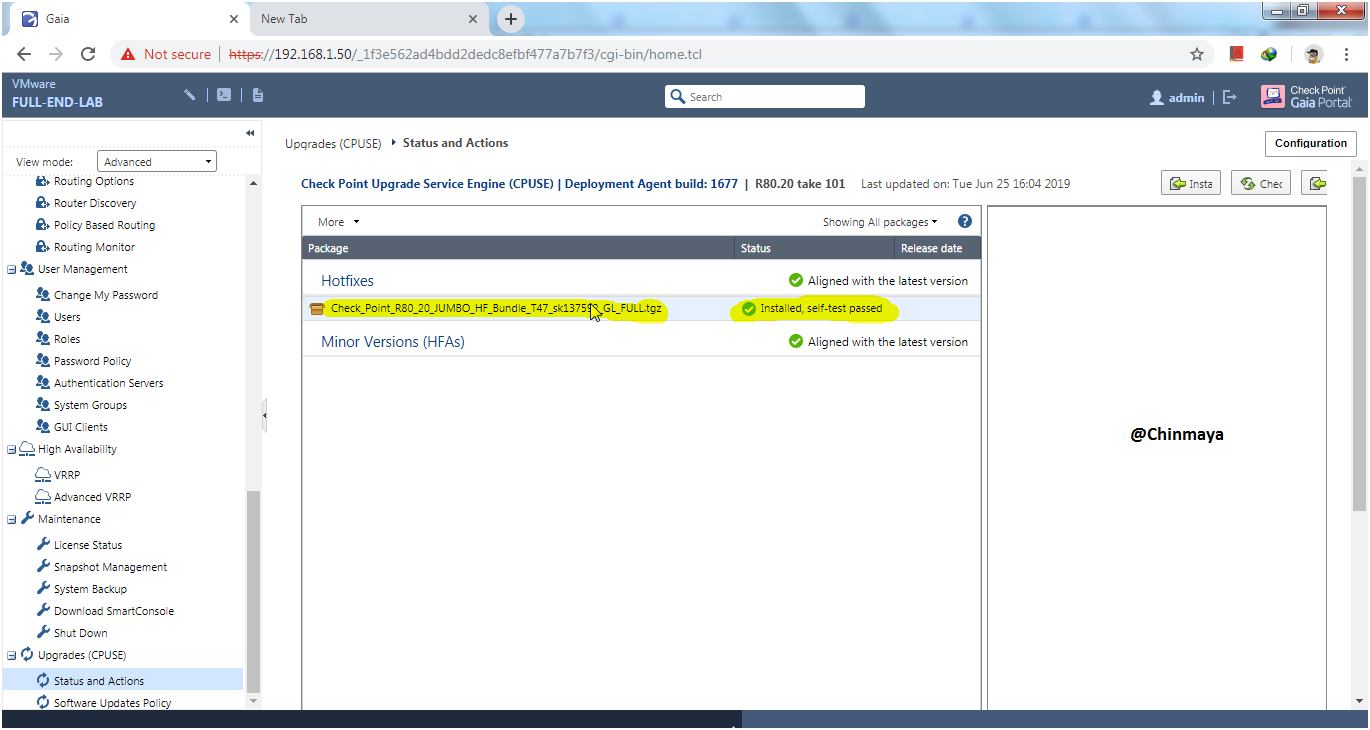
STEP: Verify via CLI.

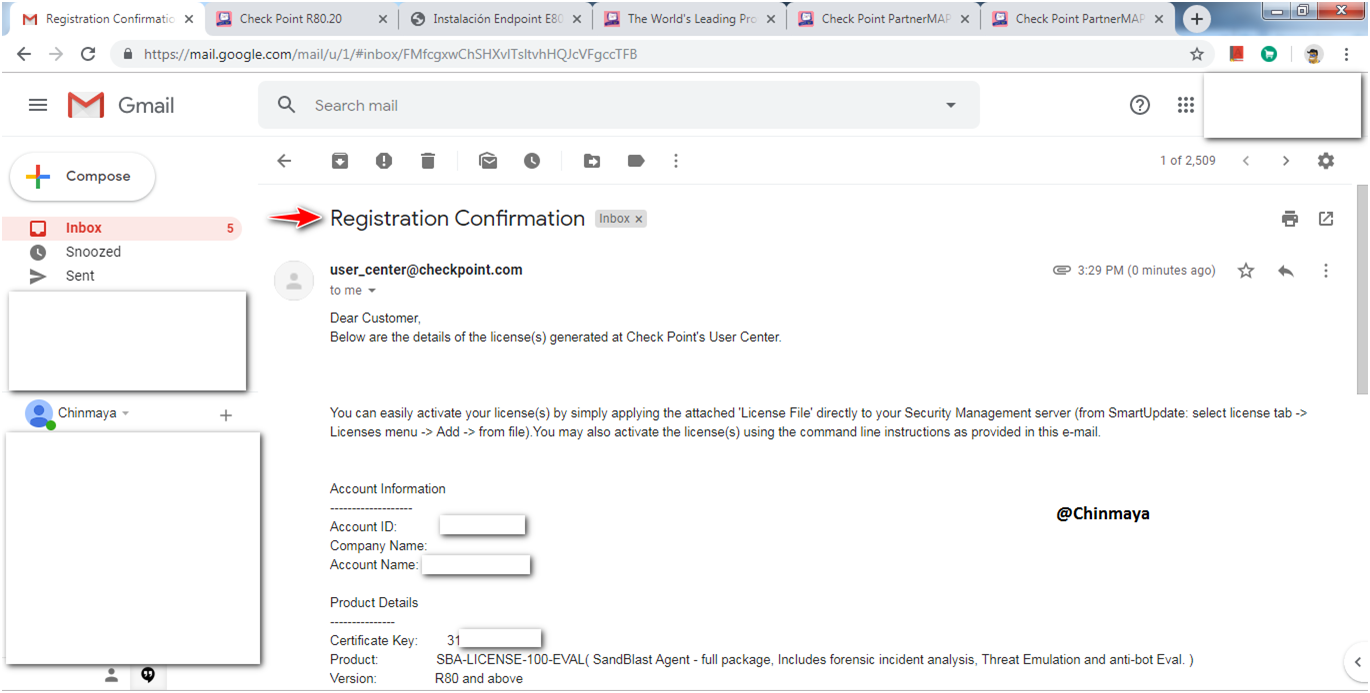
LICENSE
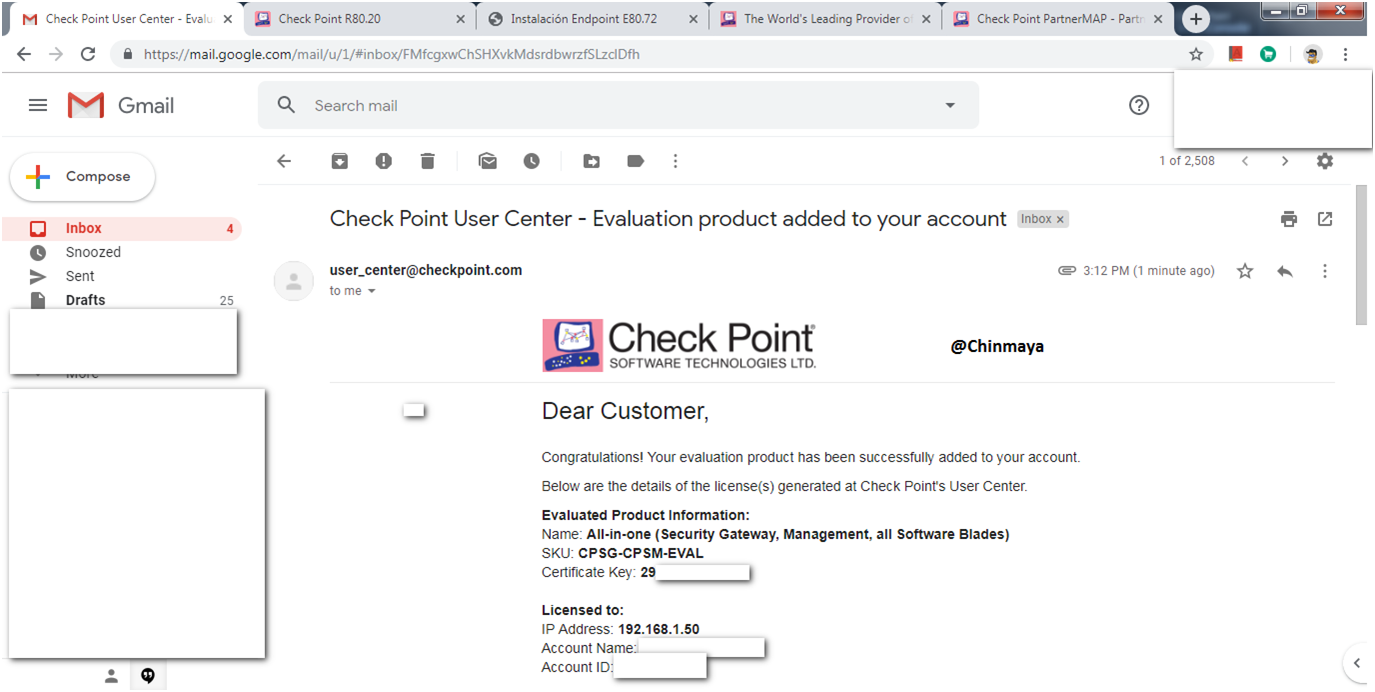
STEP : Generate the Evaluation License.
Go to usercenter.checkpoint.com ---> Login ---> After Login go to Product Center ---> Select the specific account ---> Go to Evaluation ---> Product Evaluation.
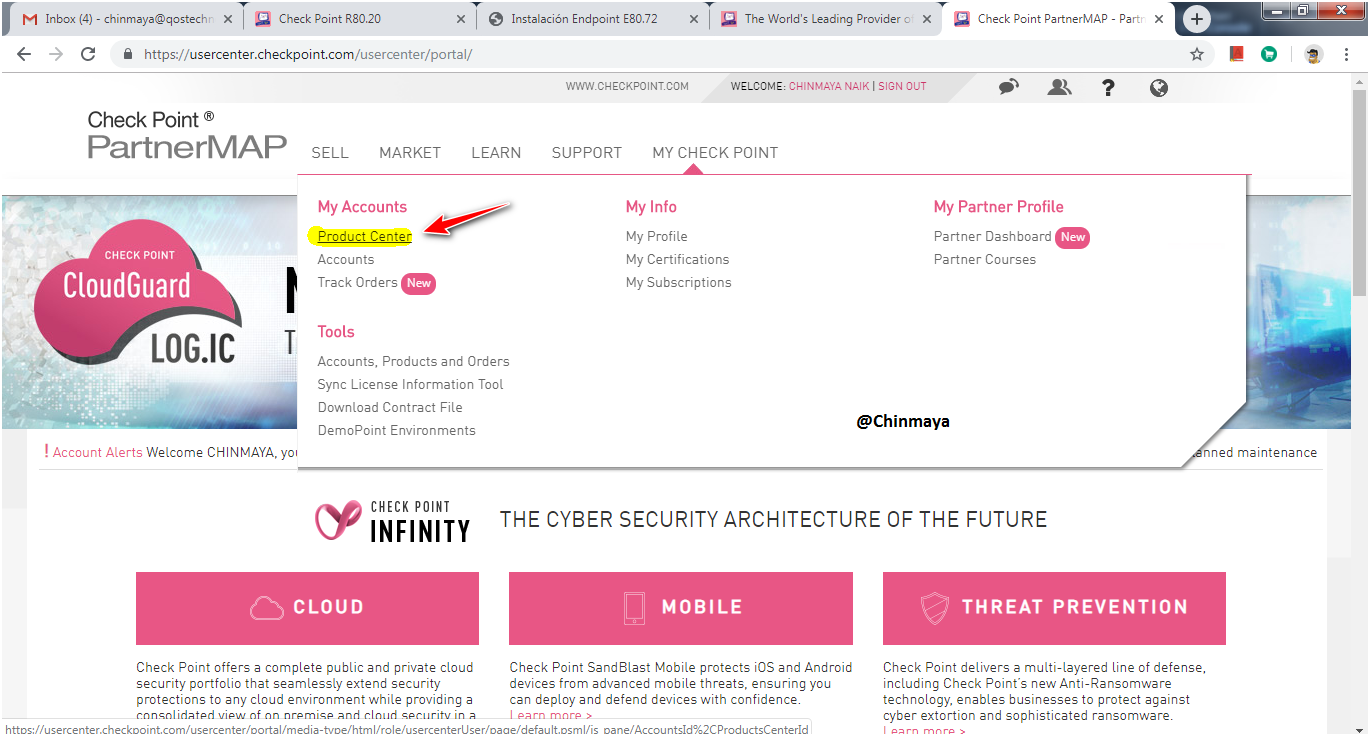
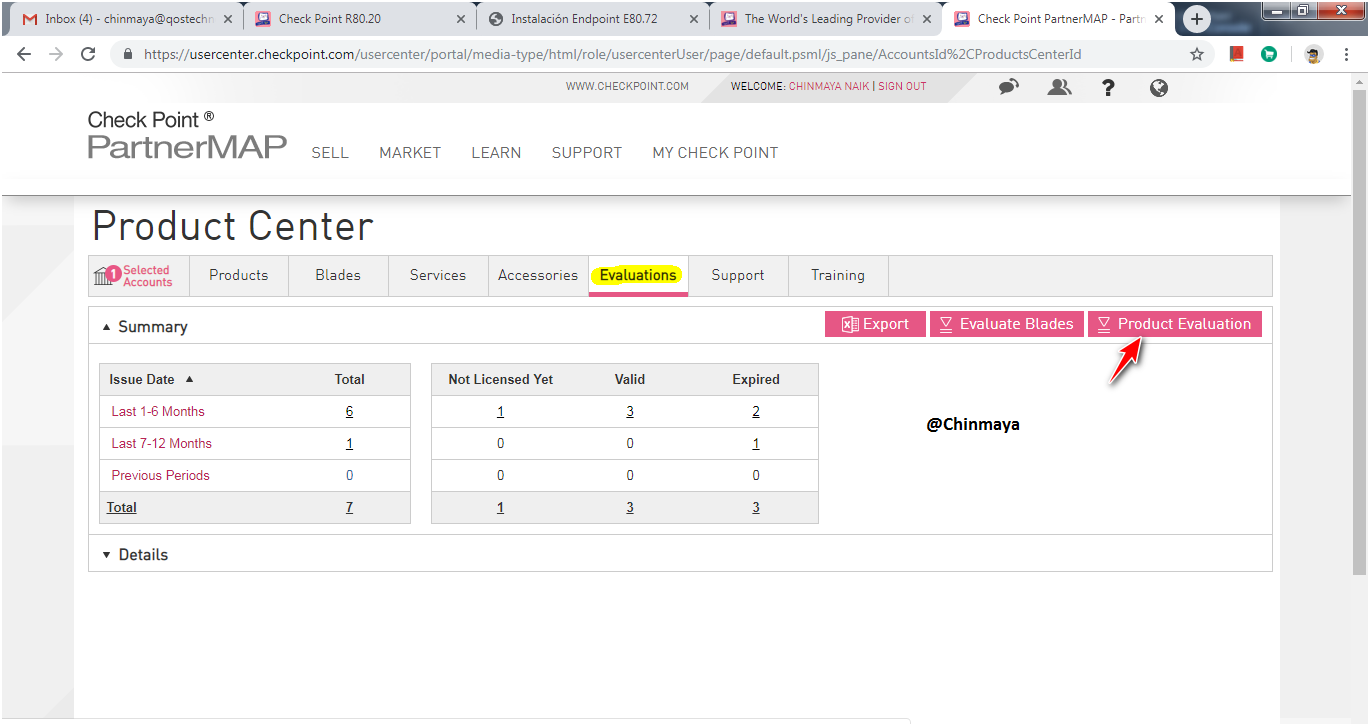
STEP : Select “ALL-IN-ONE EVALUATION” and click “Next”.

STEP: Assign the IP address of MGMT server and fill the all relevant details and Click “Get Evaluation”.

Evaluation License is generated successfully.
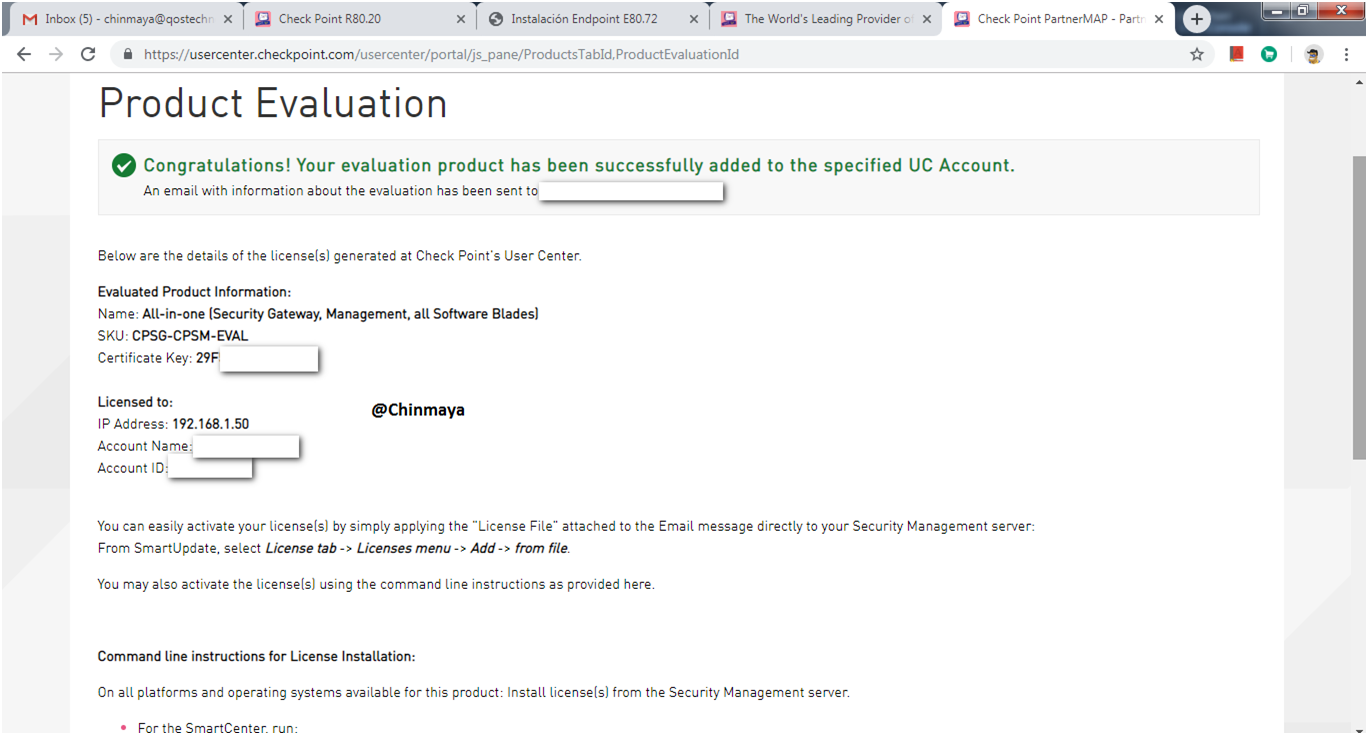
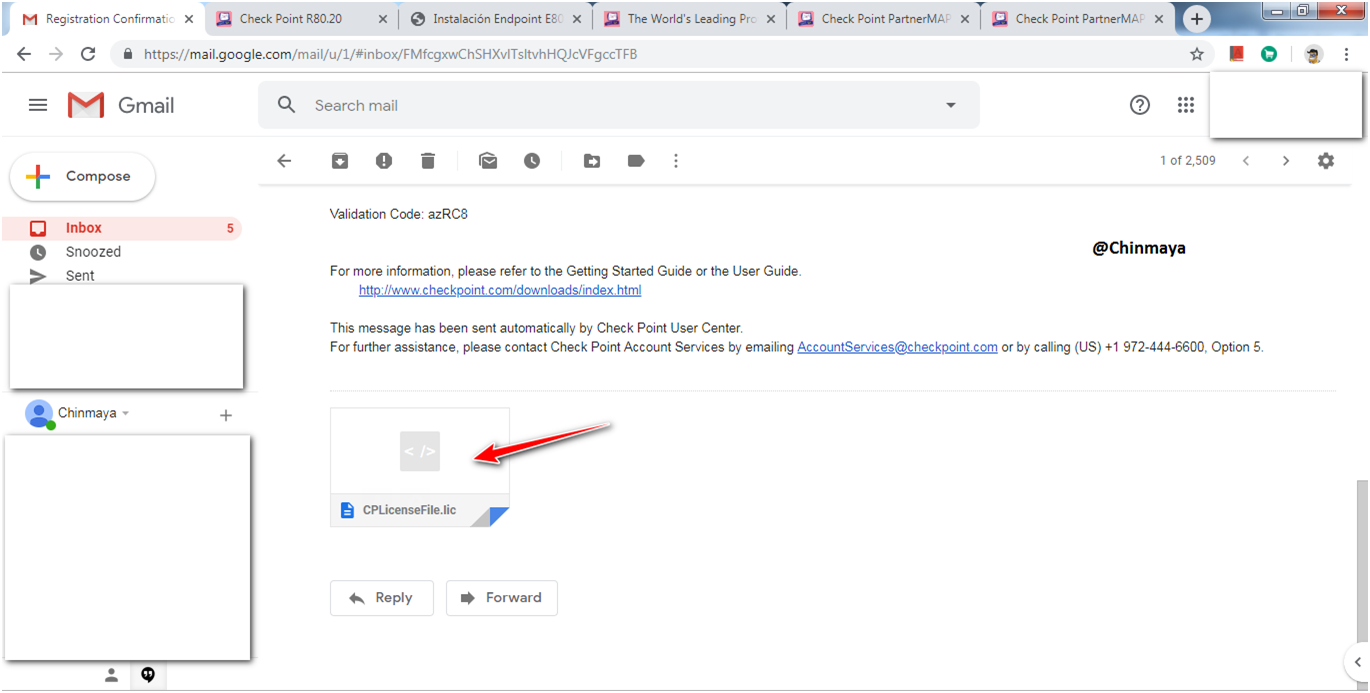
Parameter to add license via CLI you also got this via Email.
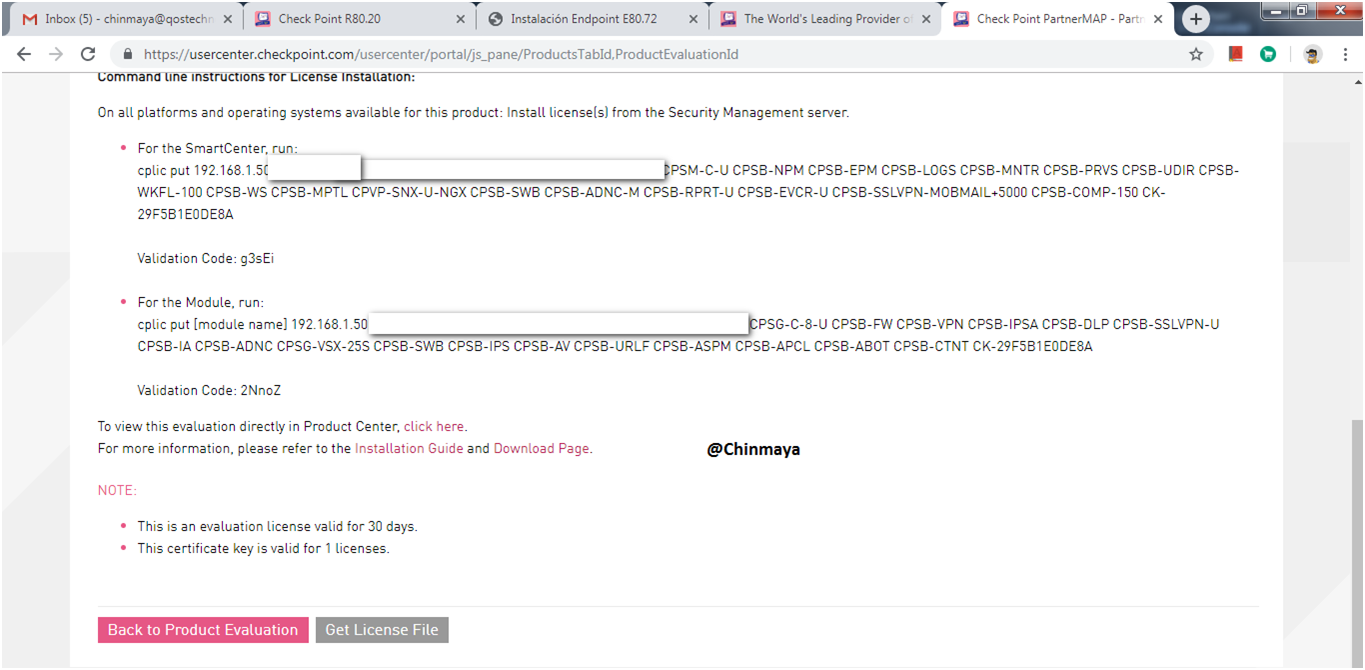
STEP : Now we are going to generate the EVAL License for Sandblast Agent Package. So login to https://usercenter.checkpoint.com
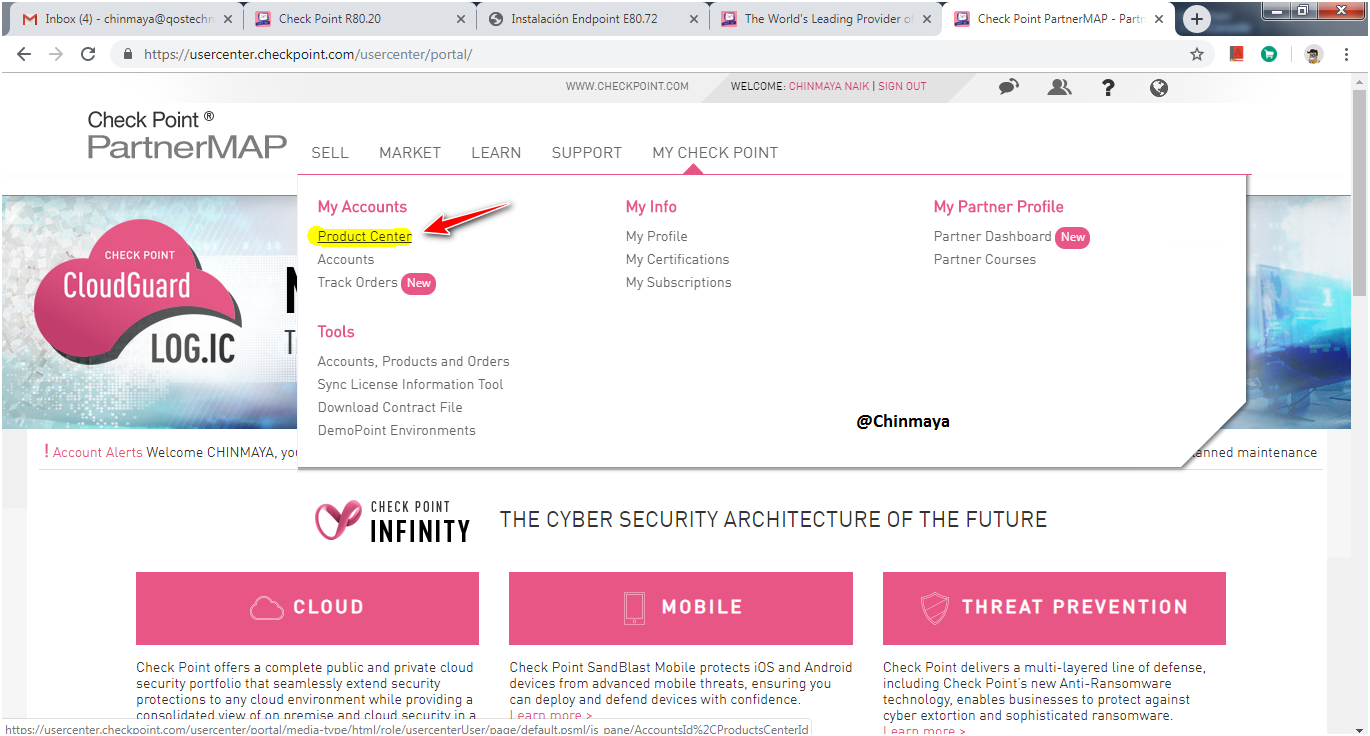
STEP: Go to “Evaluation” section and select “Product Evaluation”.
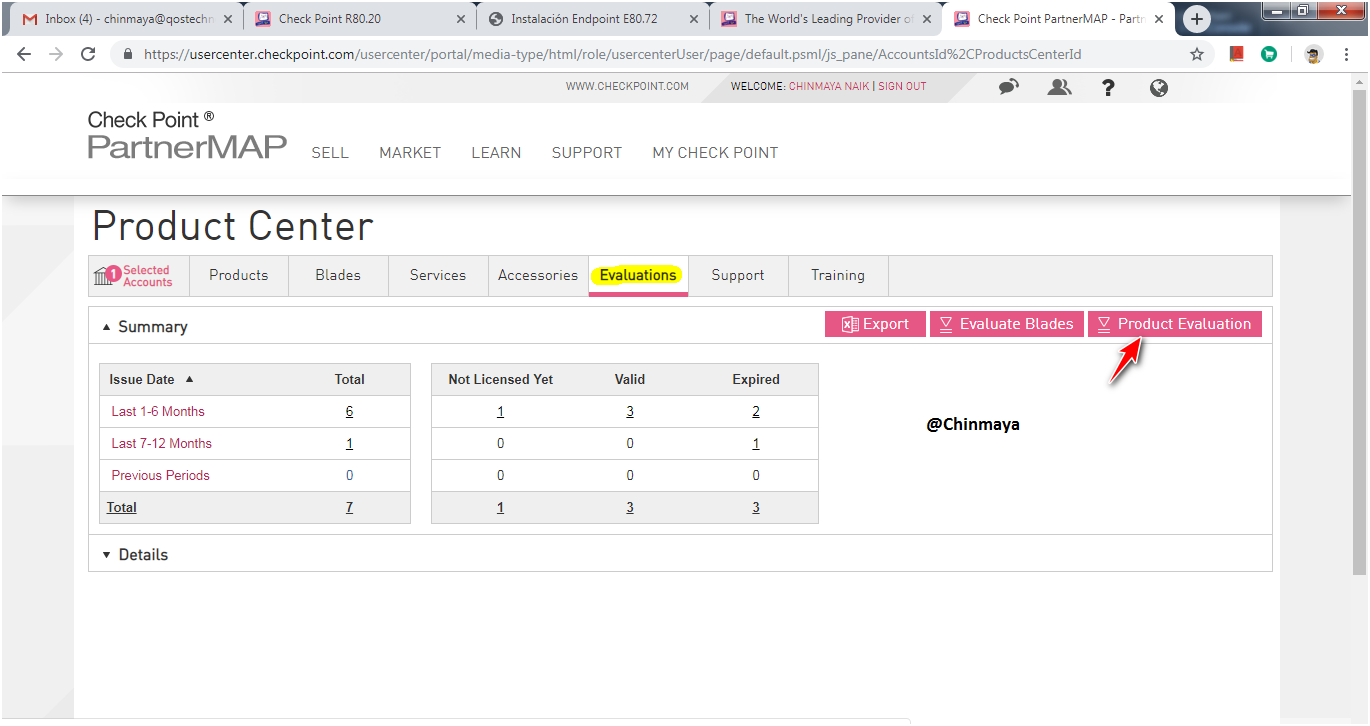
STEP: Select the “Other Evaluation Option” and click on “select a product”
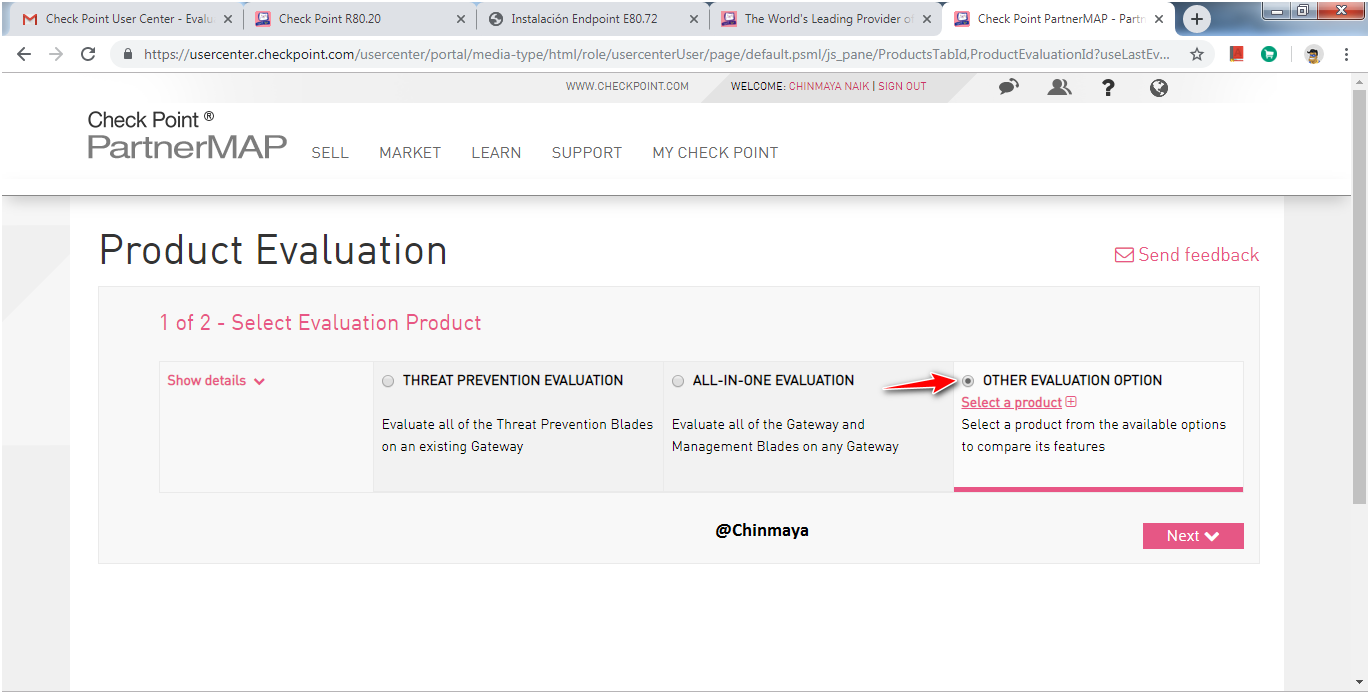
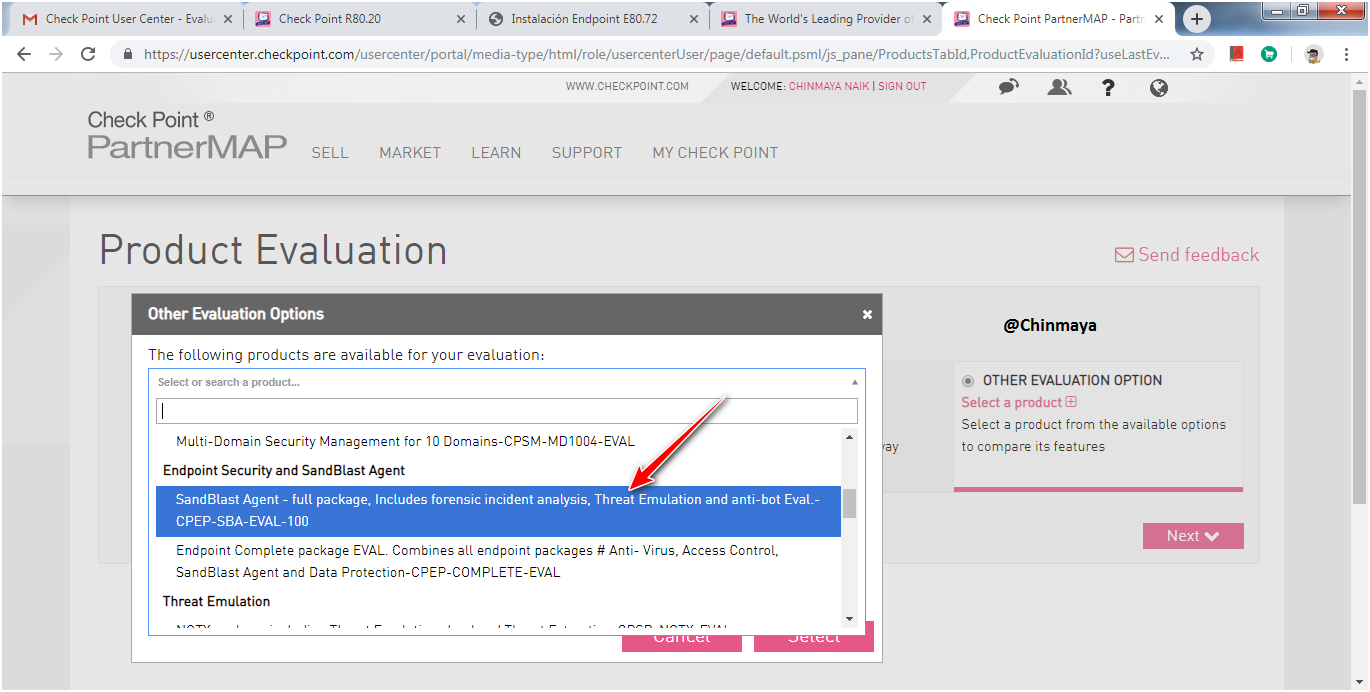
STEP : Select “SandBlast Agent-Full ackage***”
NOTE : Endpoint Complete package is for all the relevant blade for Checkpoint Endpoint also the Sandblast packages.

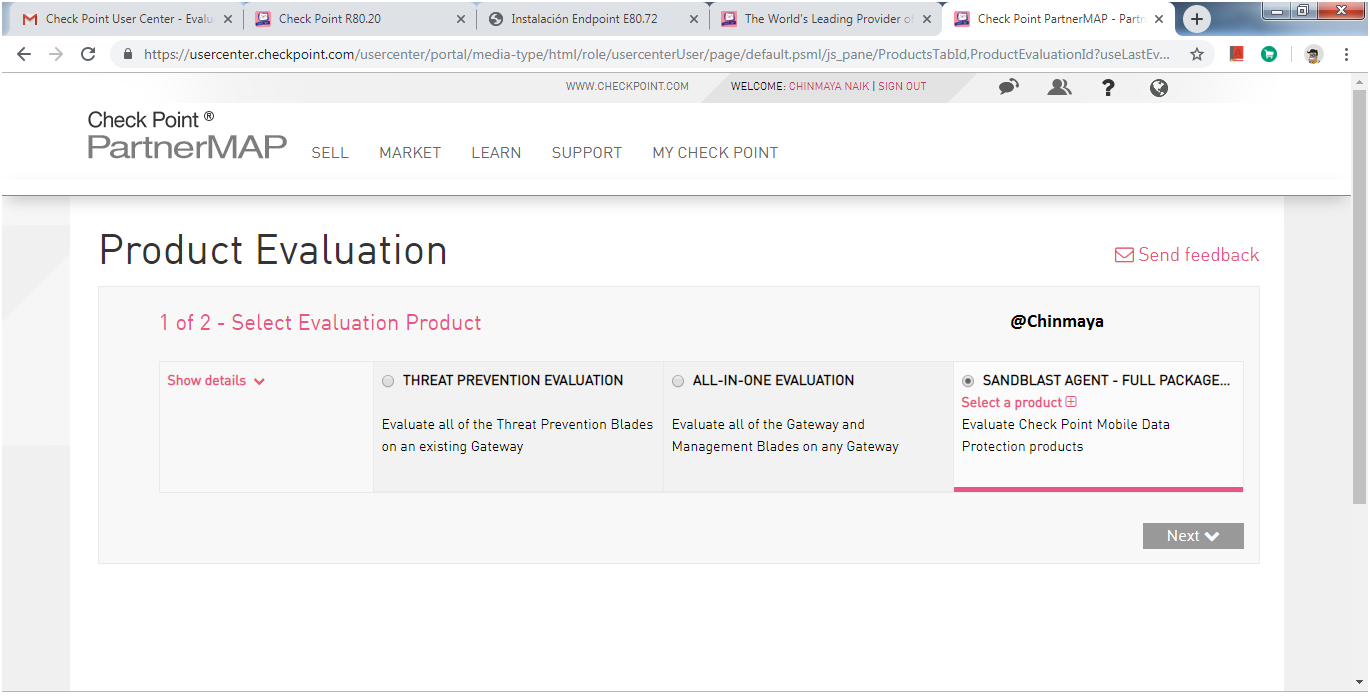
STEP : Give the details below and click on “Get Evaluation”.

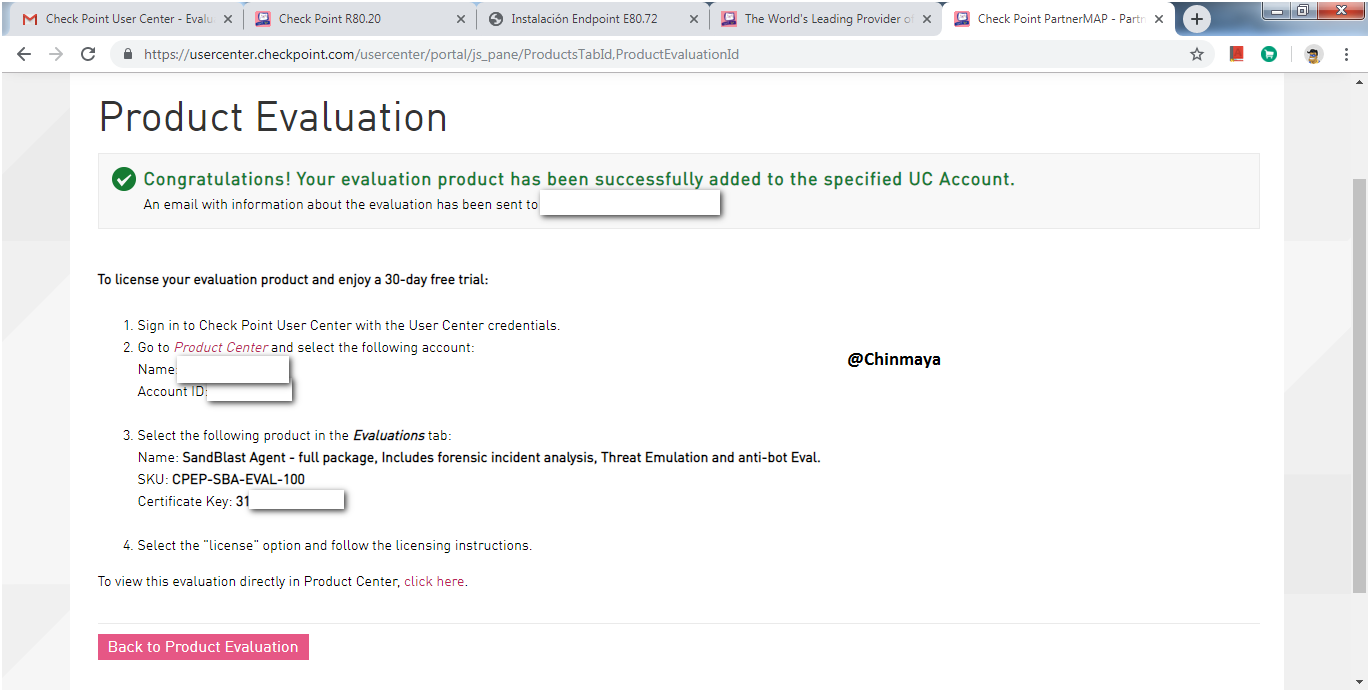
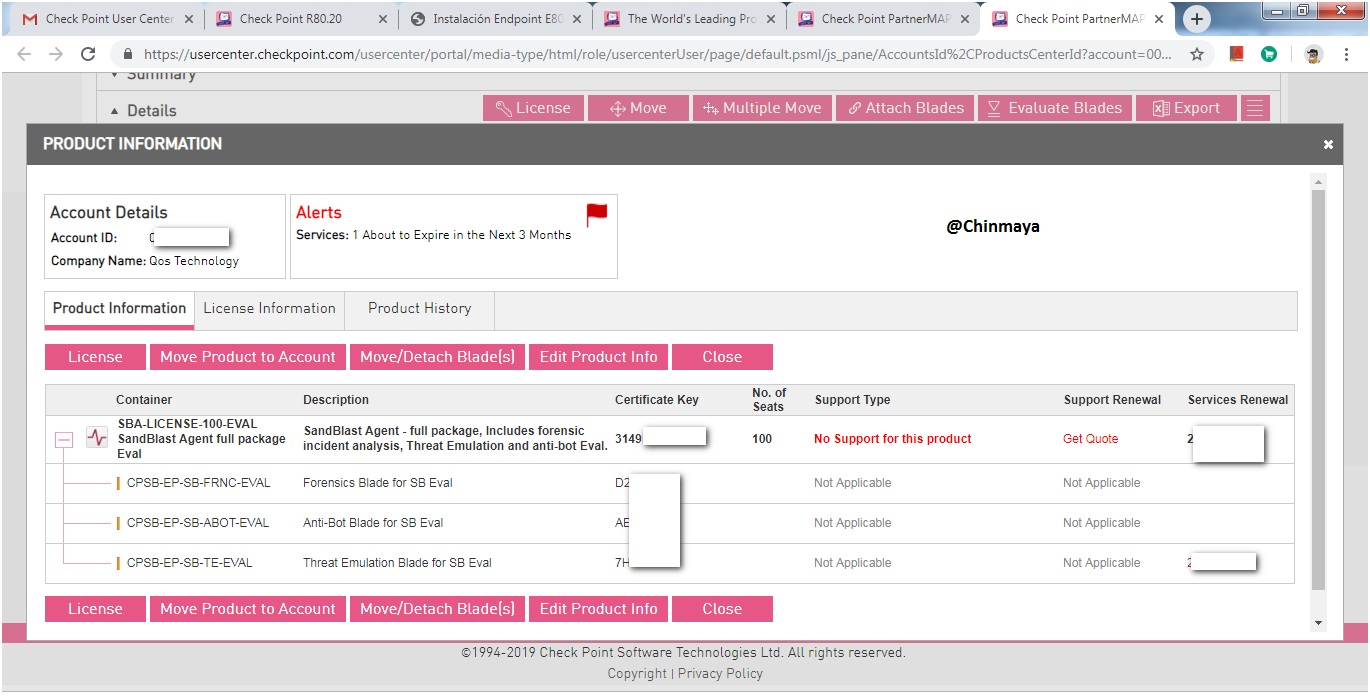

STEP : Select the “License”.
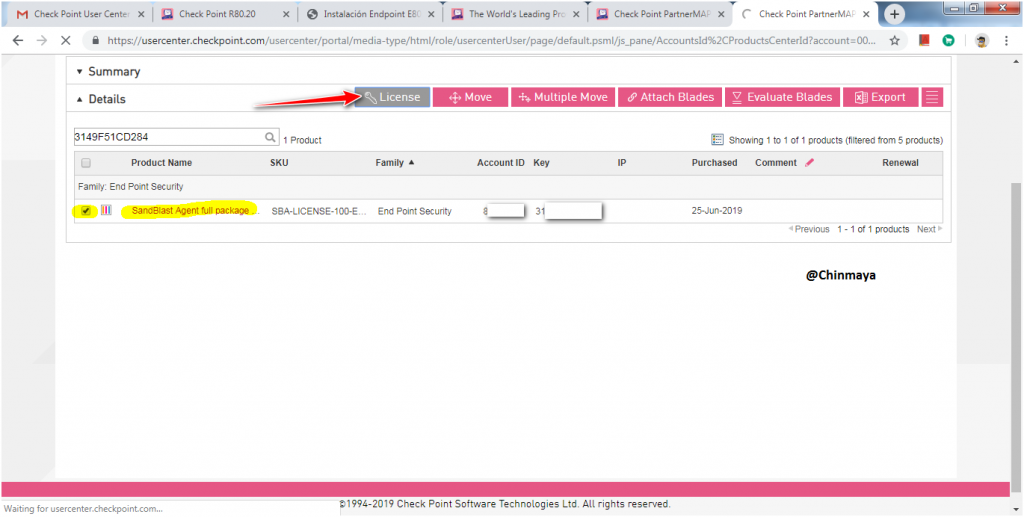
STEP: Assign the IP address of Management Server.
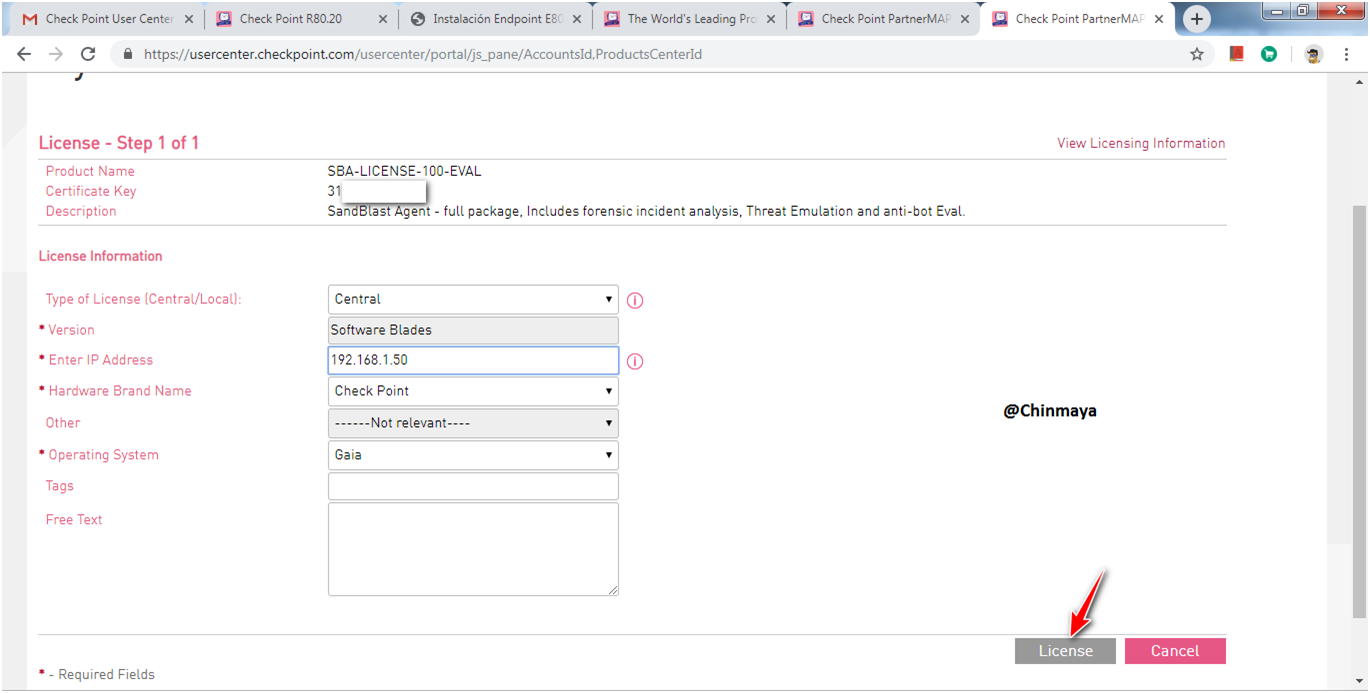
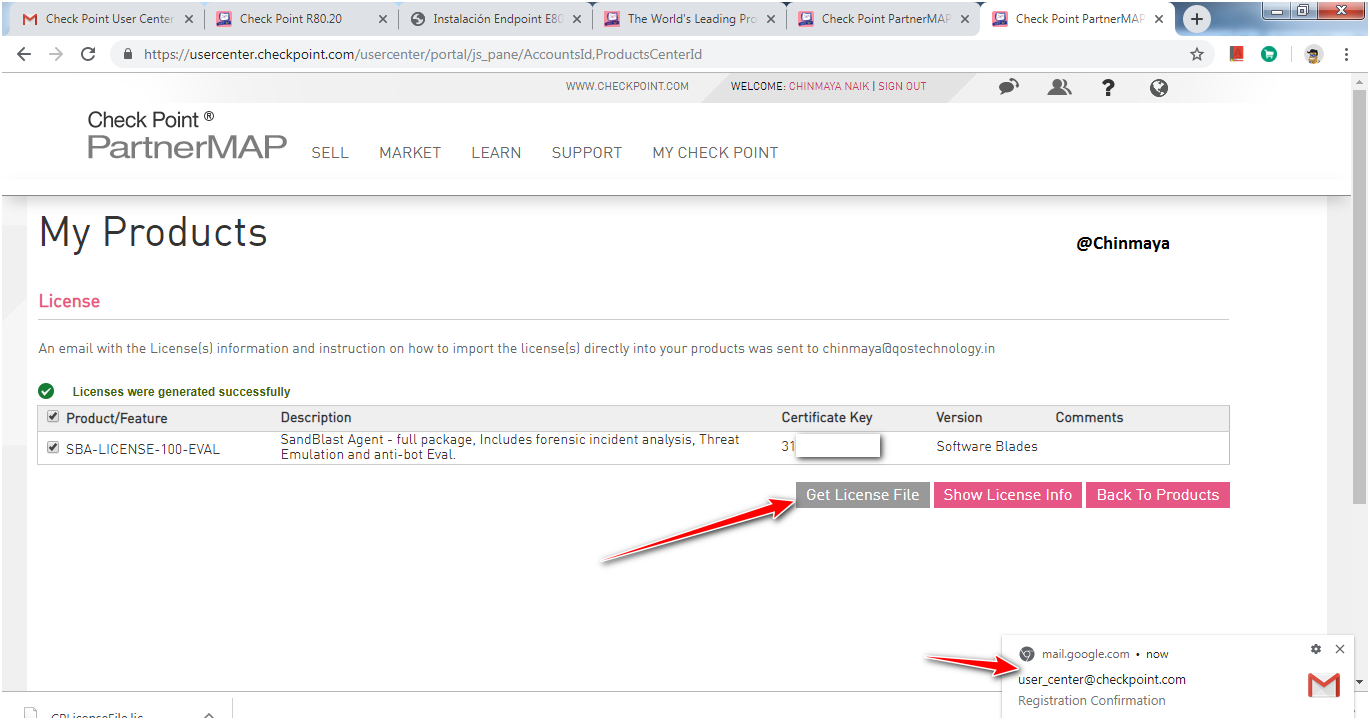
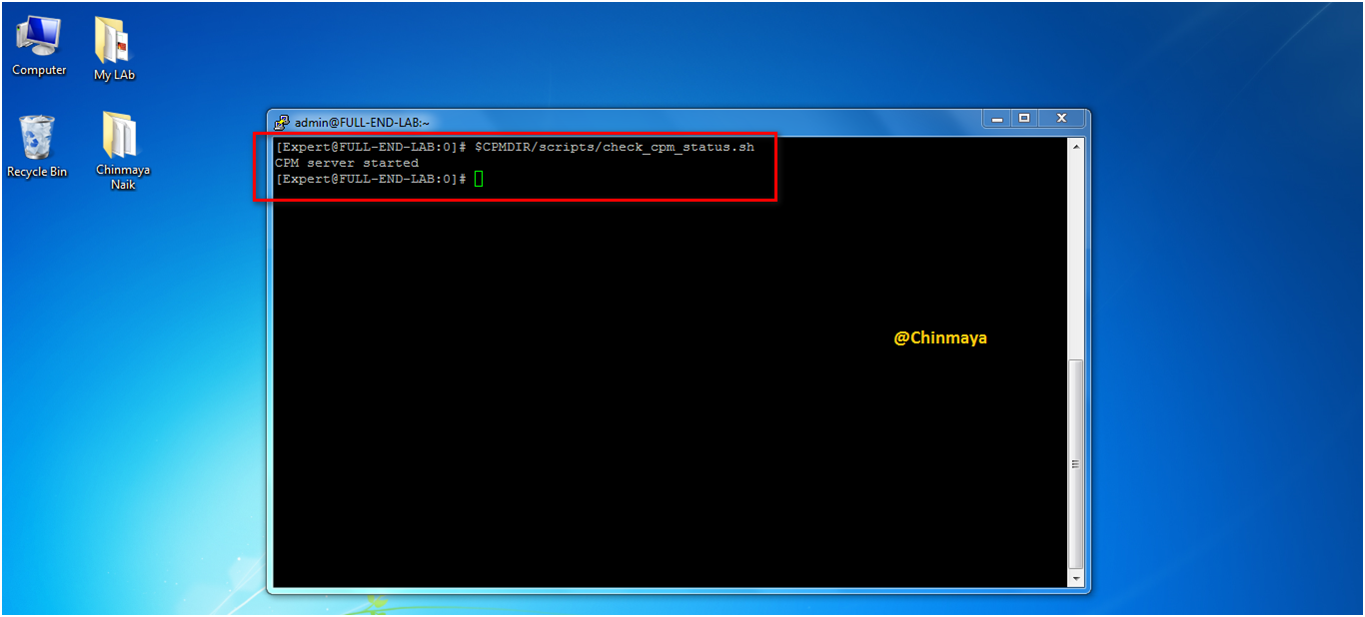
STEP : Run the below command to start the CPM server to access Smart Console R80.20. Sometime we unable to access Smart Console because sometime CPM services is not yet started.
Command:
EXPERT#$CPMDIR/scripts/check_cpm_status.sh
EXPERT#api status (CPM should showing as started)
STEP : Give the credentials and login to the SmartConsole.
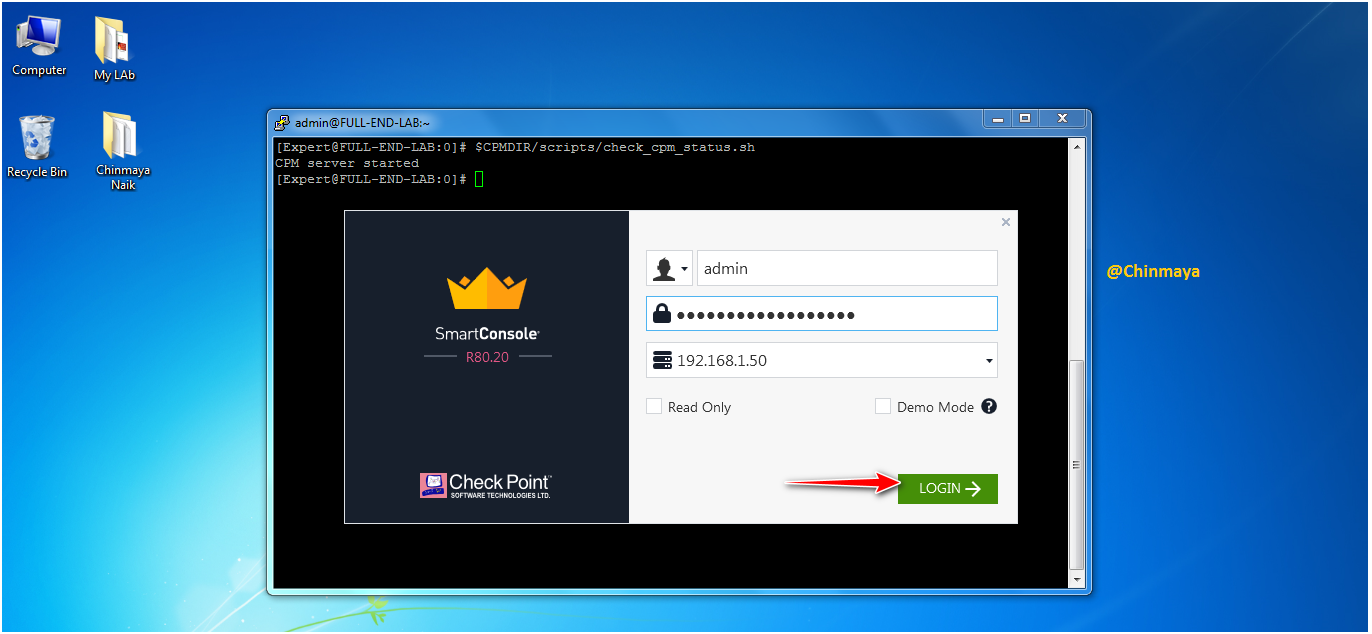
SmartConsole is open.
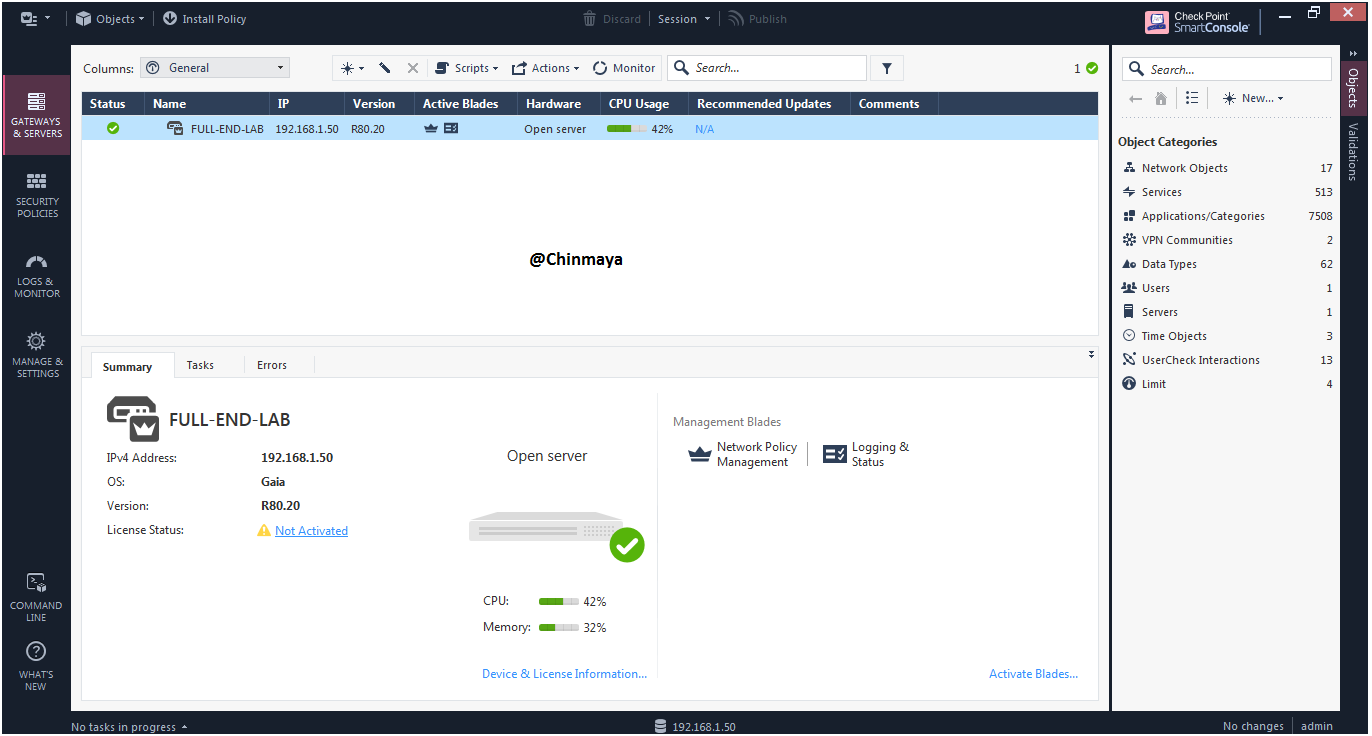
STEP: Go to the general properties for verify the configuration like IP,hostname ,Hardware,etc.

STEP: Install the two license that I download already.
SmartConsole ---> Menu ---> Manage license and packages.
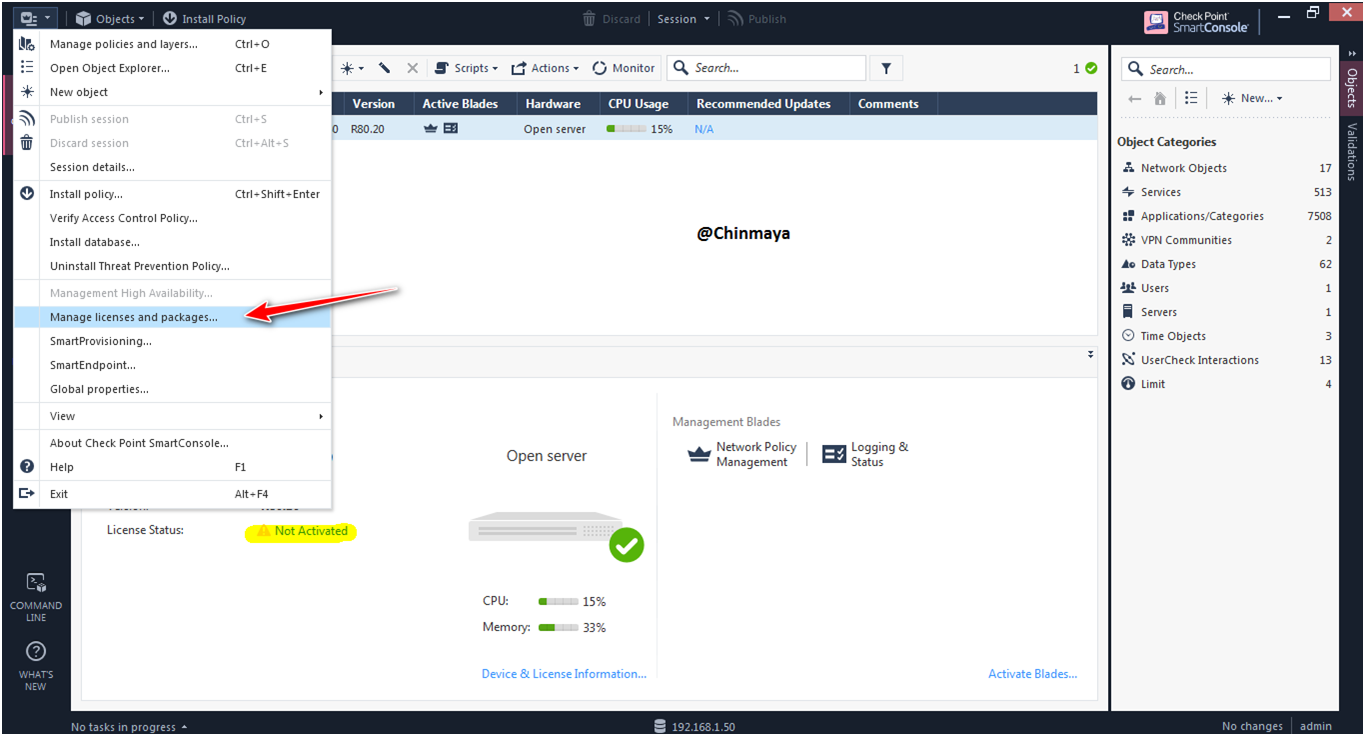
STEP: Go to the License & Contracts option.

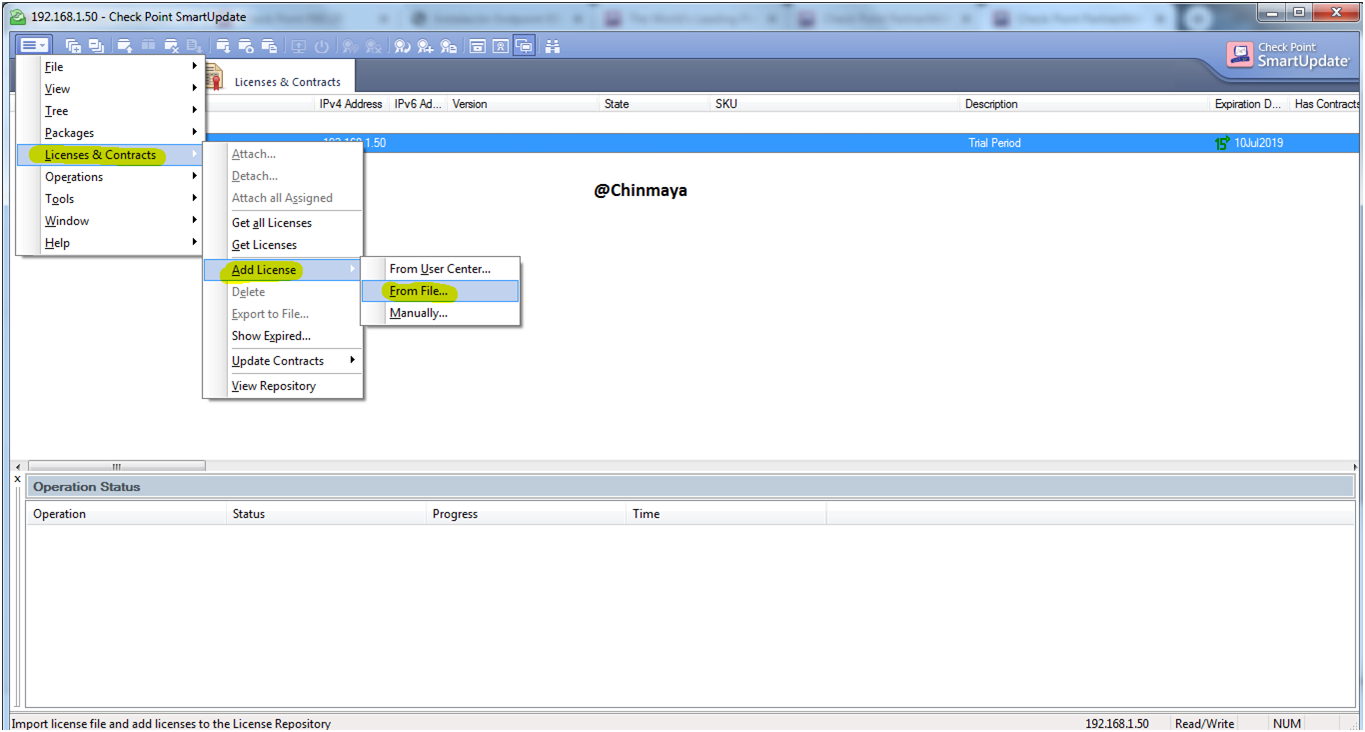
STEP: Add the All in one License first that we download already.
NOTE : Here we using offline method to install the license.
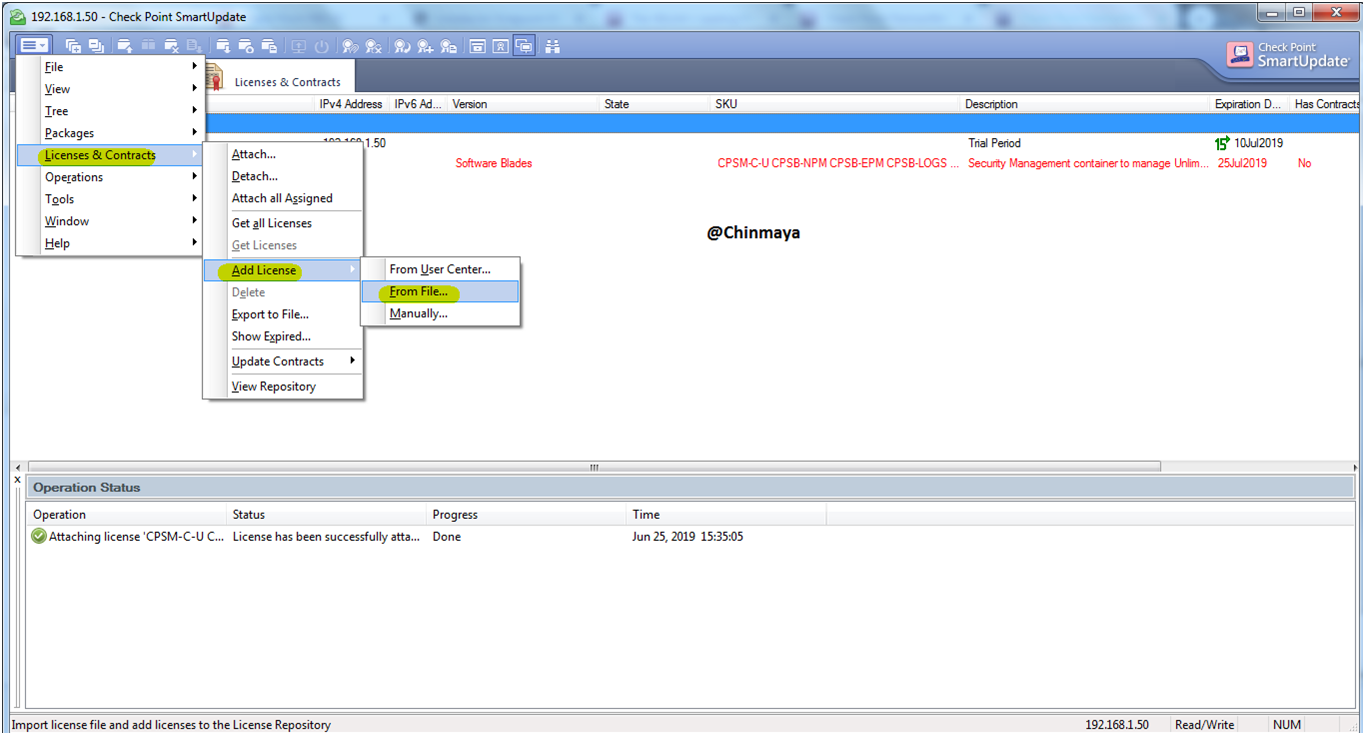
SmartUpdate ---> License & Contract ---> Add License ---> From File--> {Select the License File}
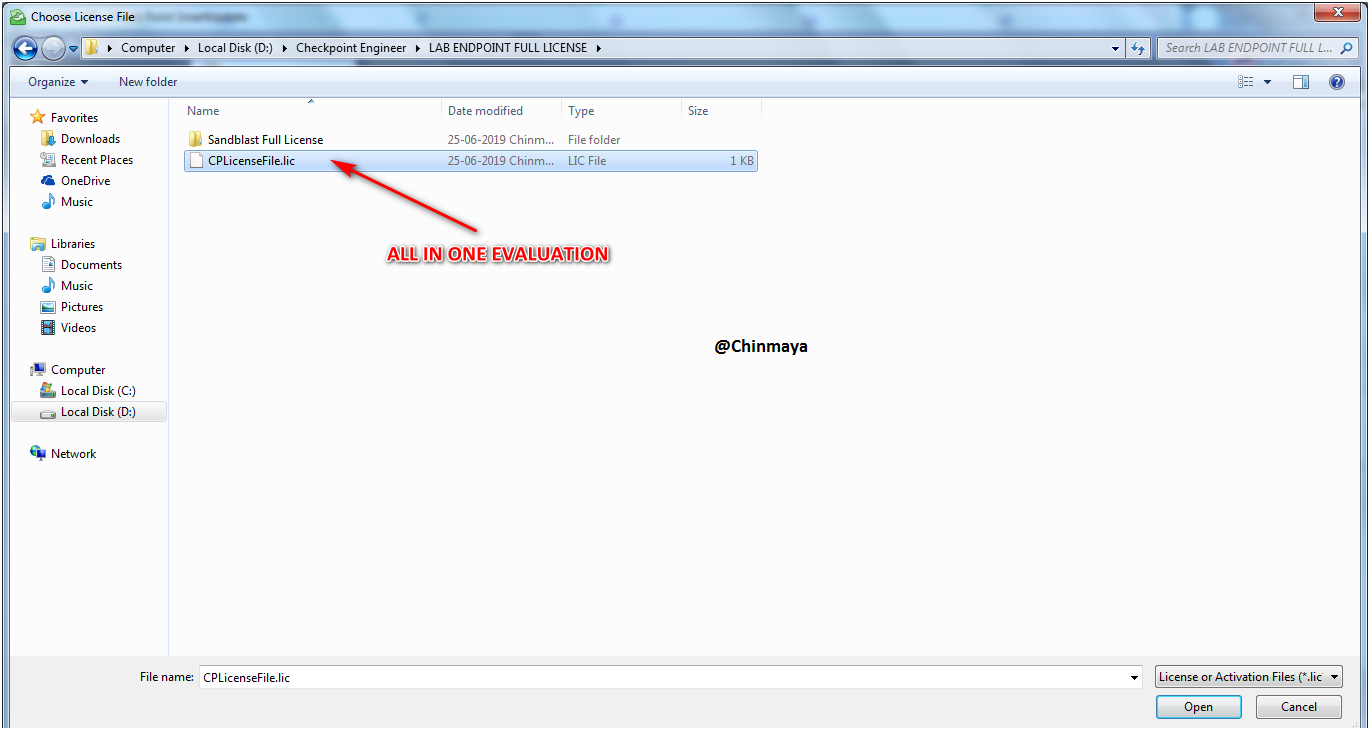
STEP: All in One Management License added successfully.
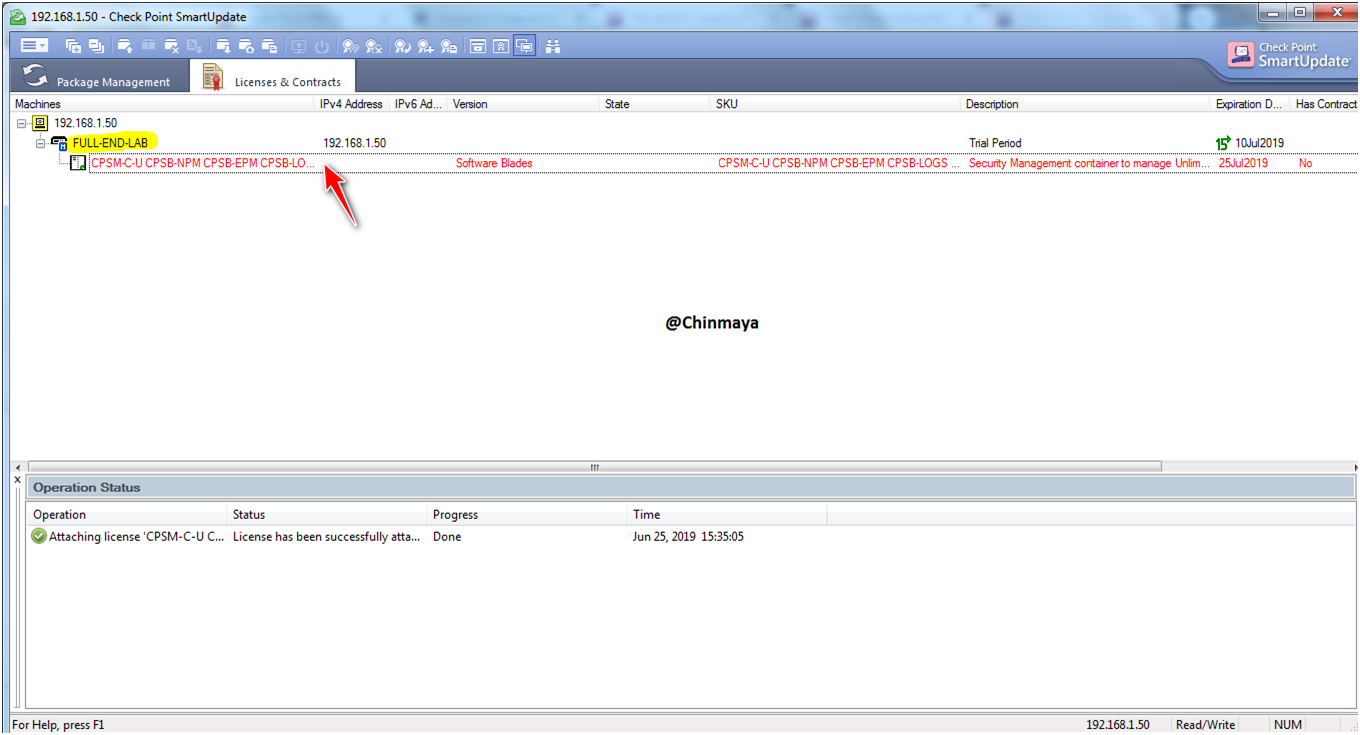
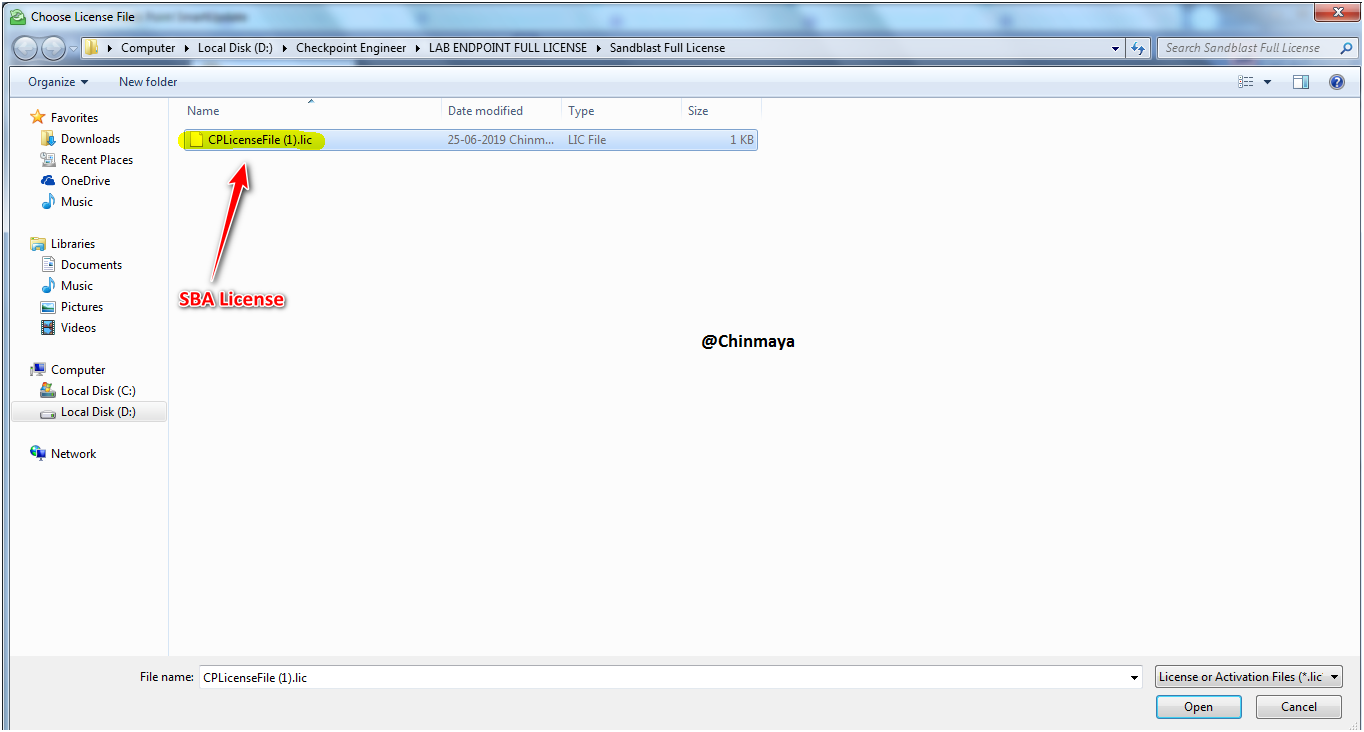
STEP : Added the second license (Sandblast Package) using offline method only because we already download the license file.
SmartUpdate ---> License & Contract ---> Add License ---> From File--> {Select the License File}
STEP: Click to “Get License”.
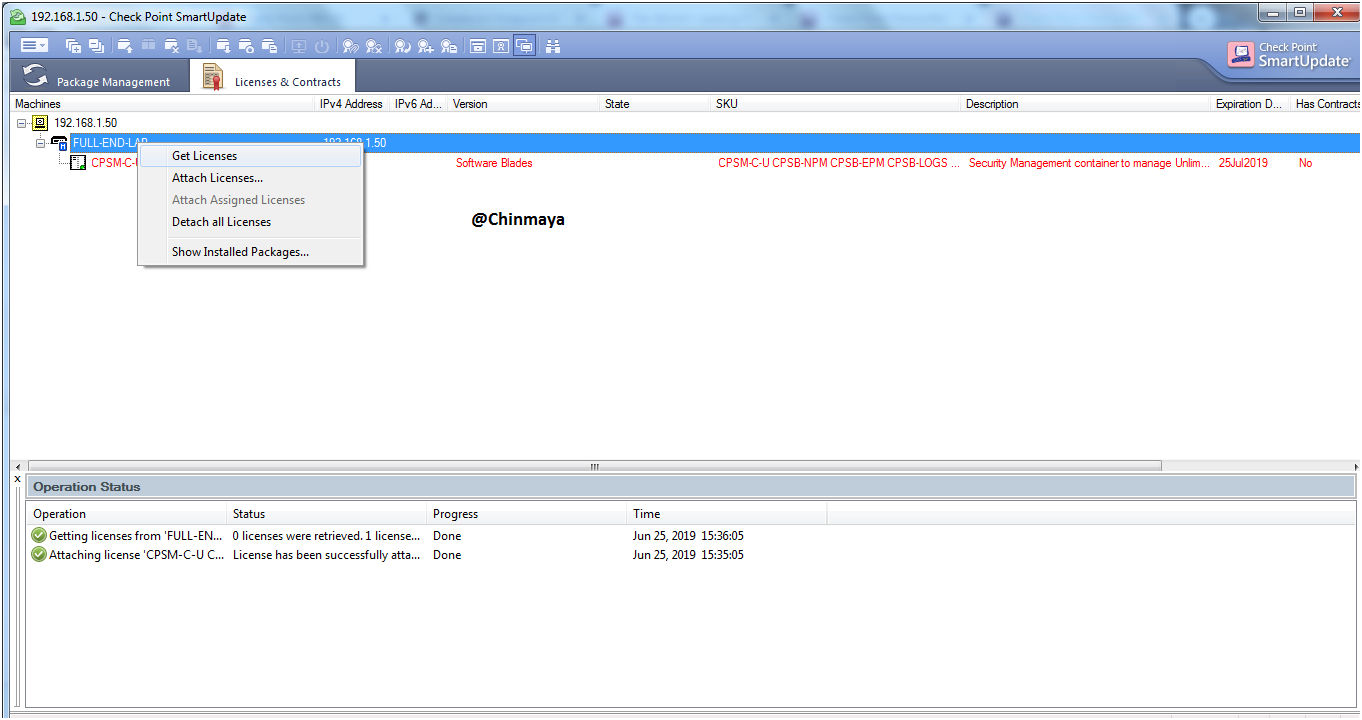
STEP: Attach the license.
Click on “Attach License”

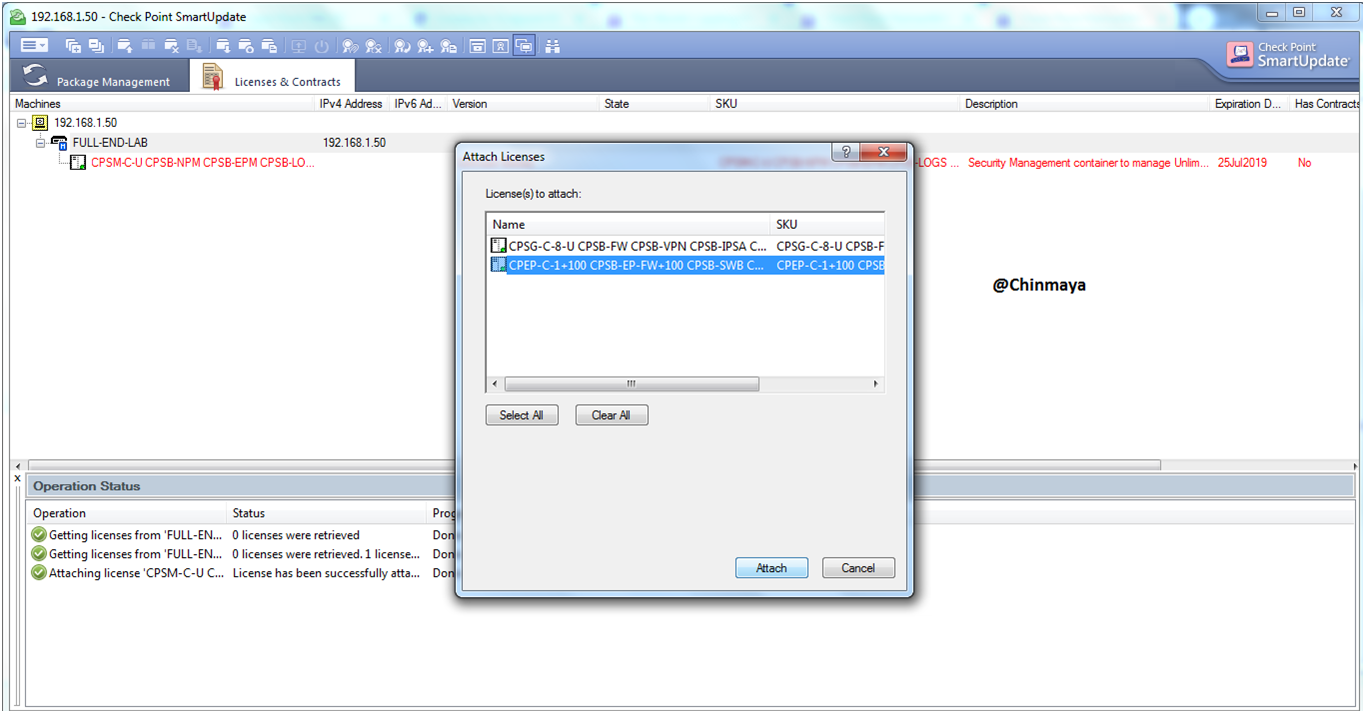
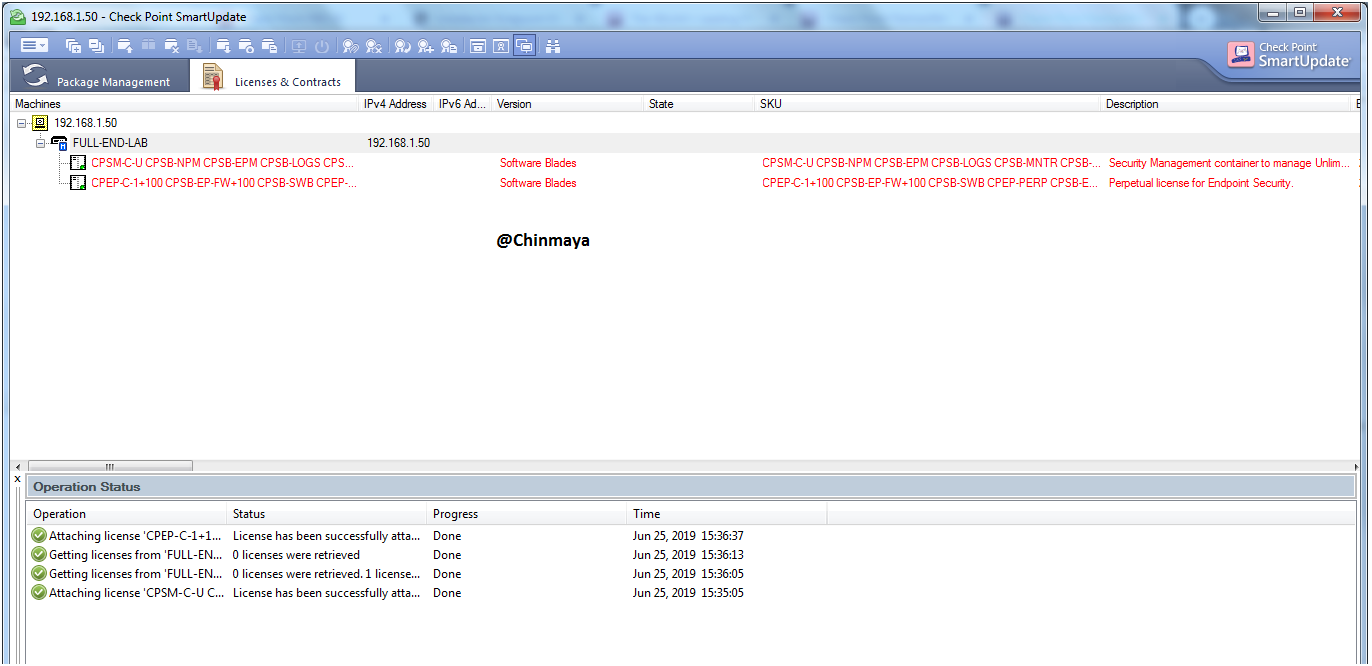
Showing both License.
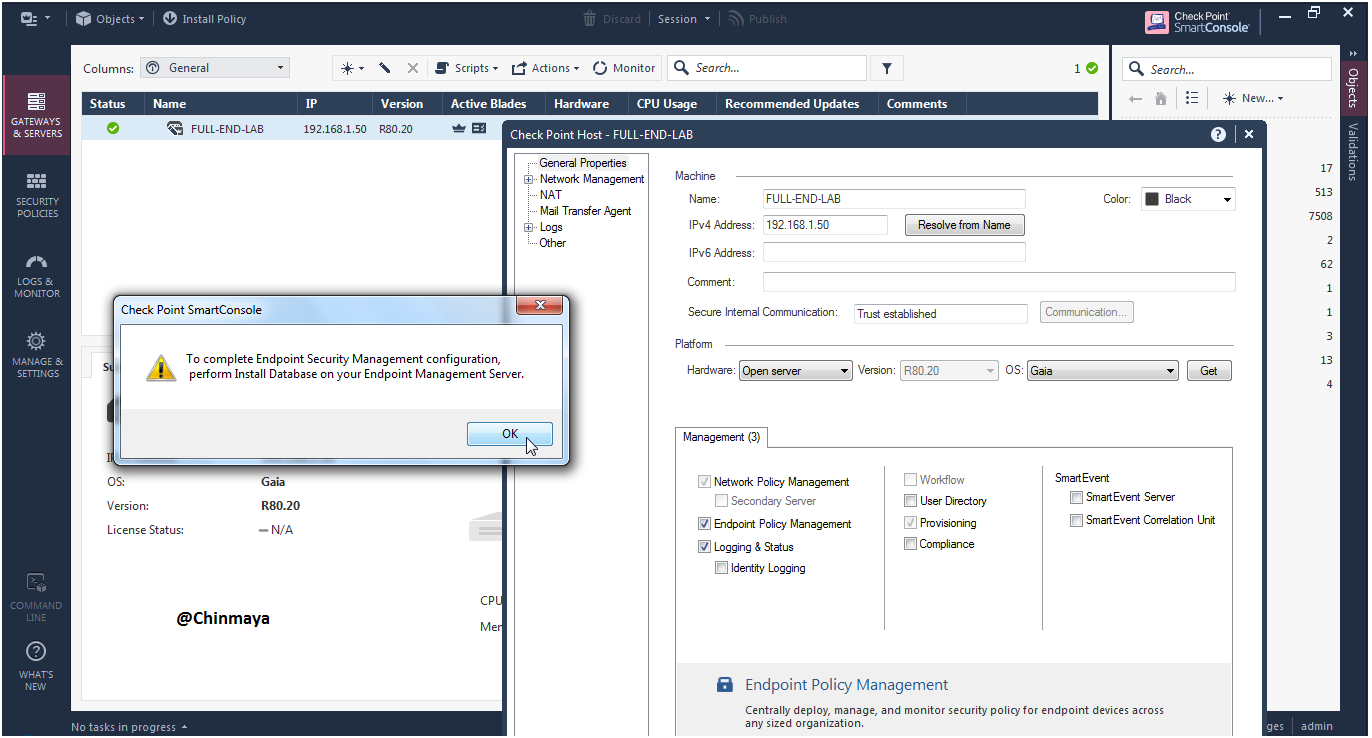
STEP: Before enable the Database enable the Log Indexing First to index the logs.
Location : Management Server Object ---> General Properties ---> Logs ---> Enable Log Indexing
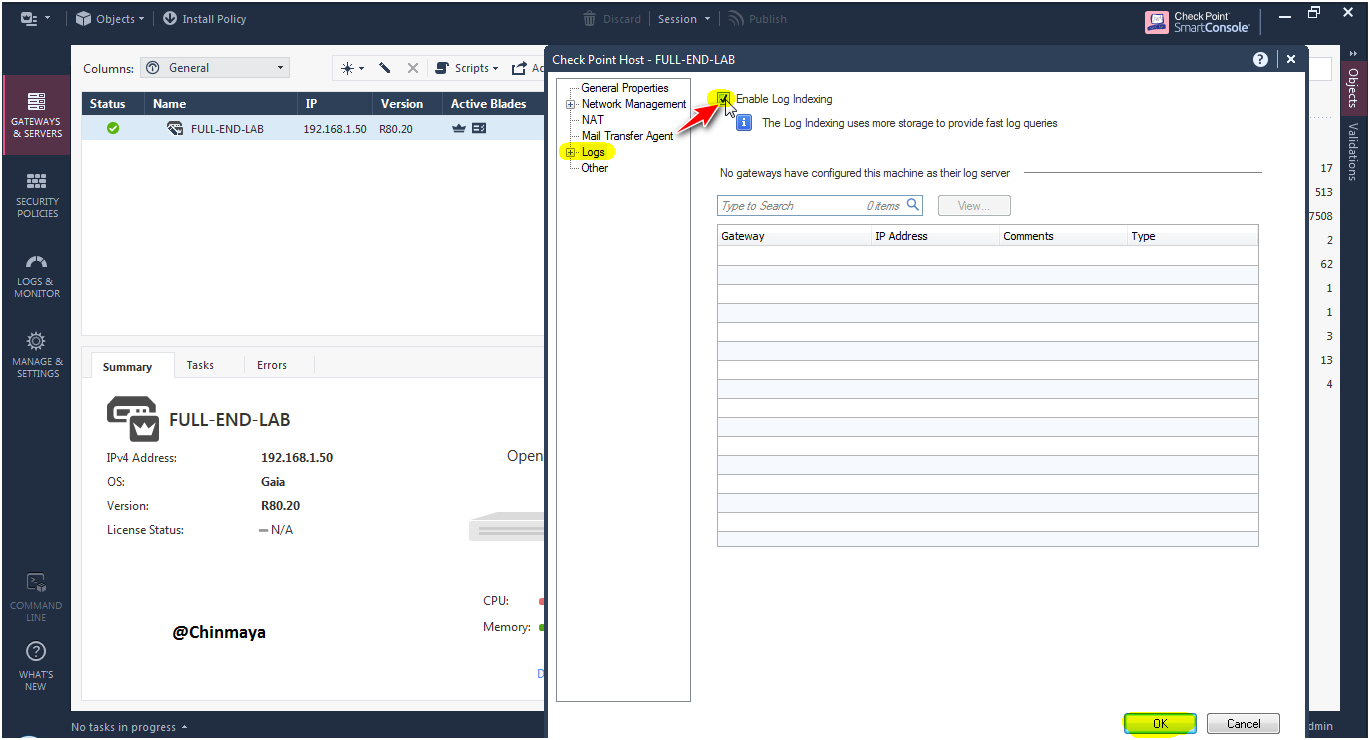
STEP : Install the Database.
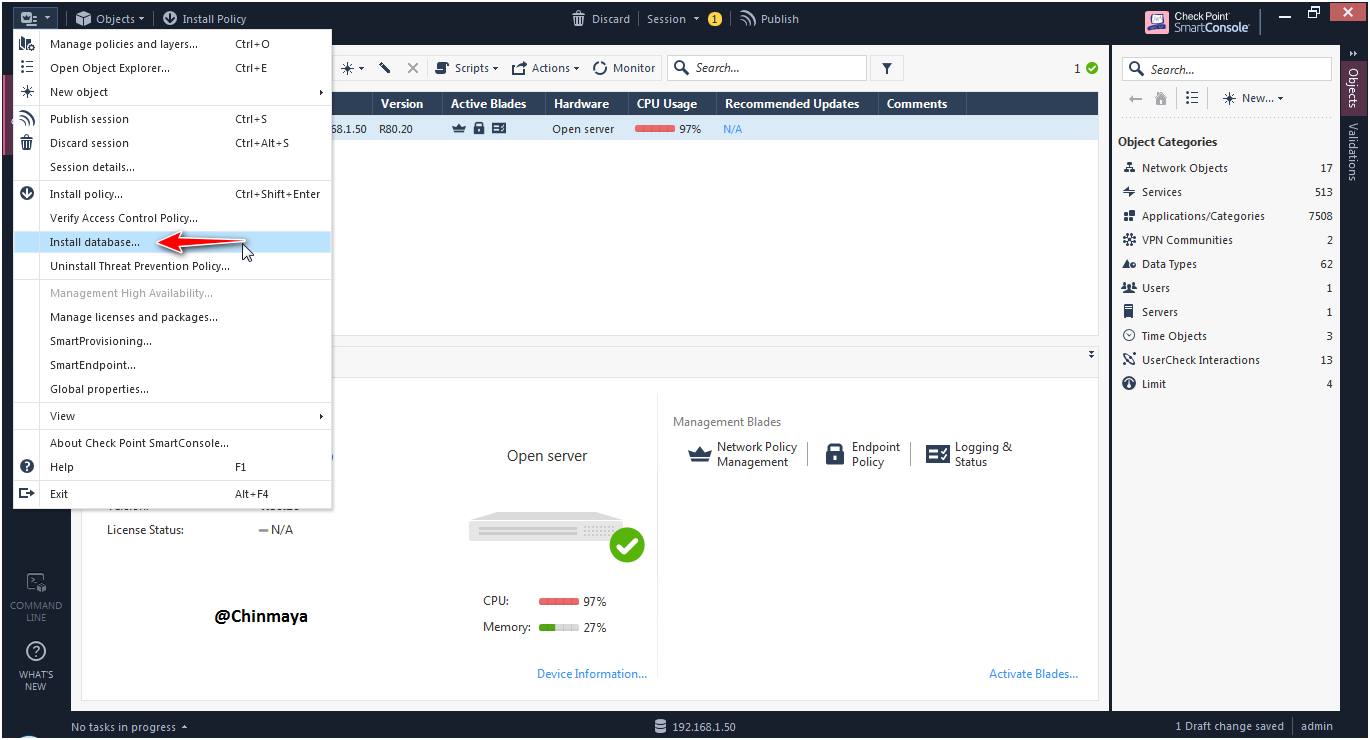
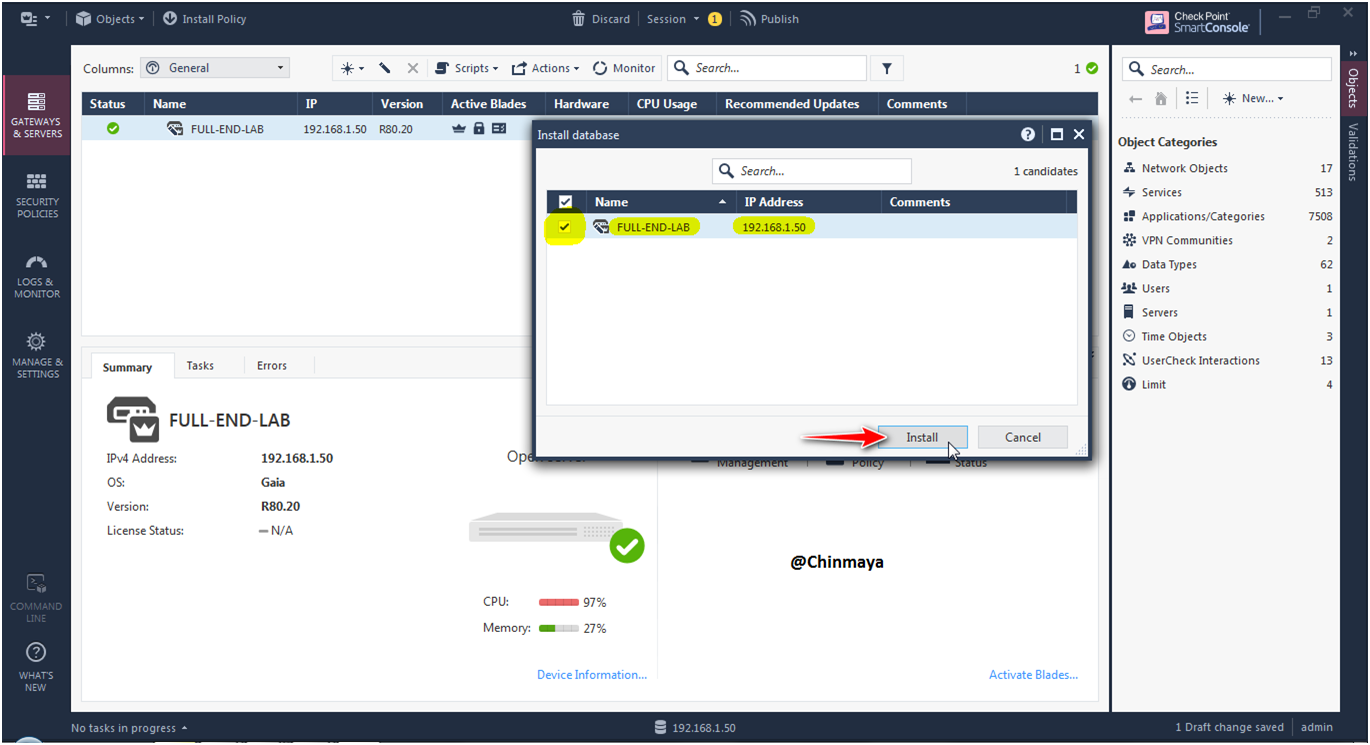
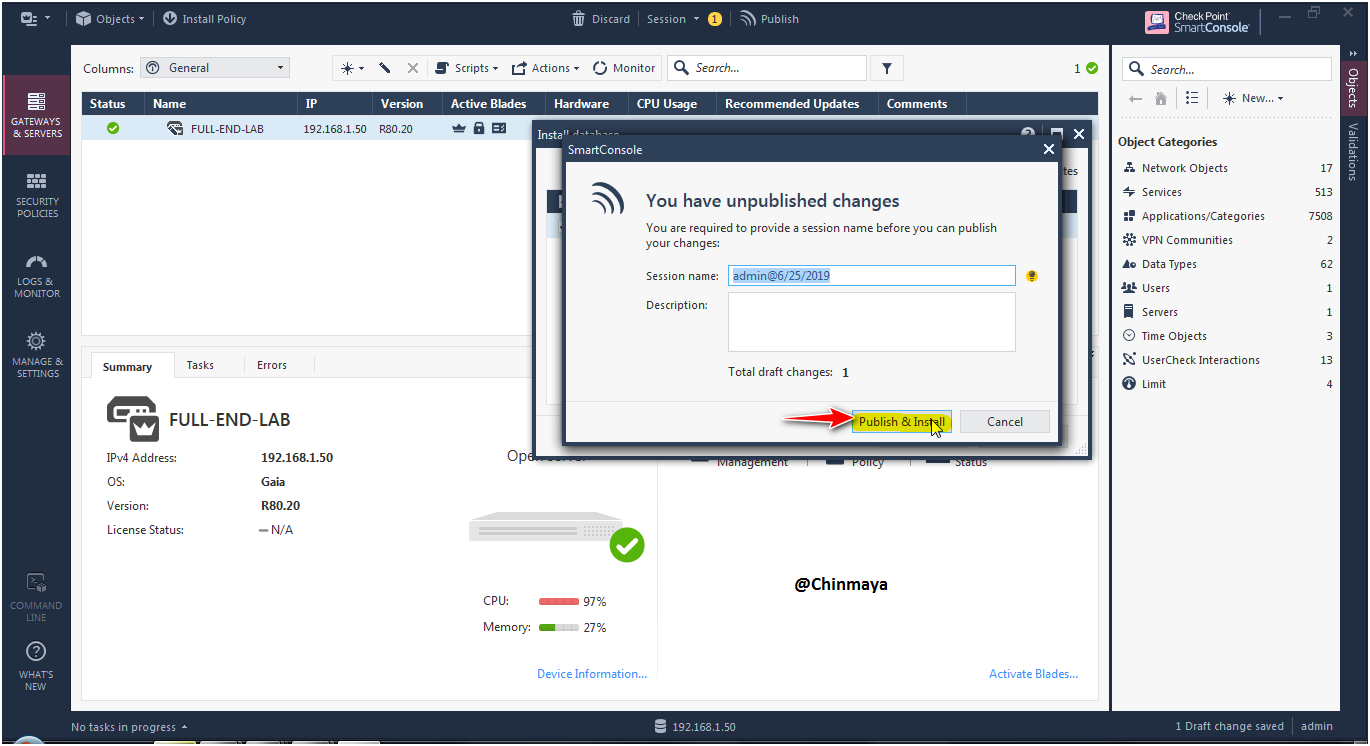

Now after installed the database License status is showing “OK”
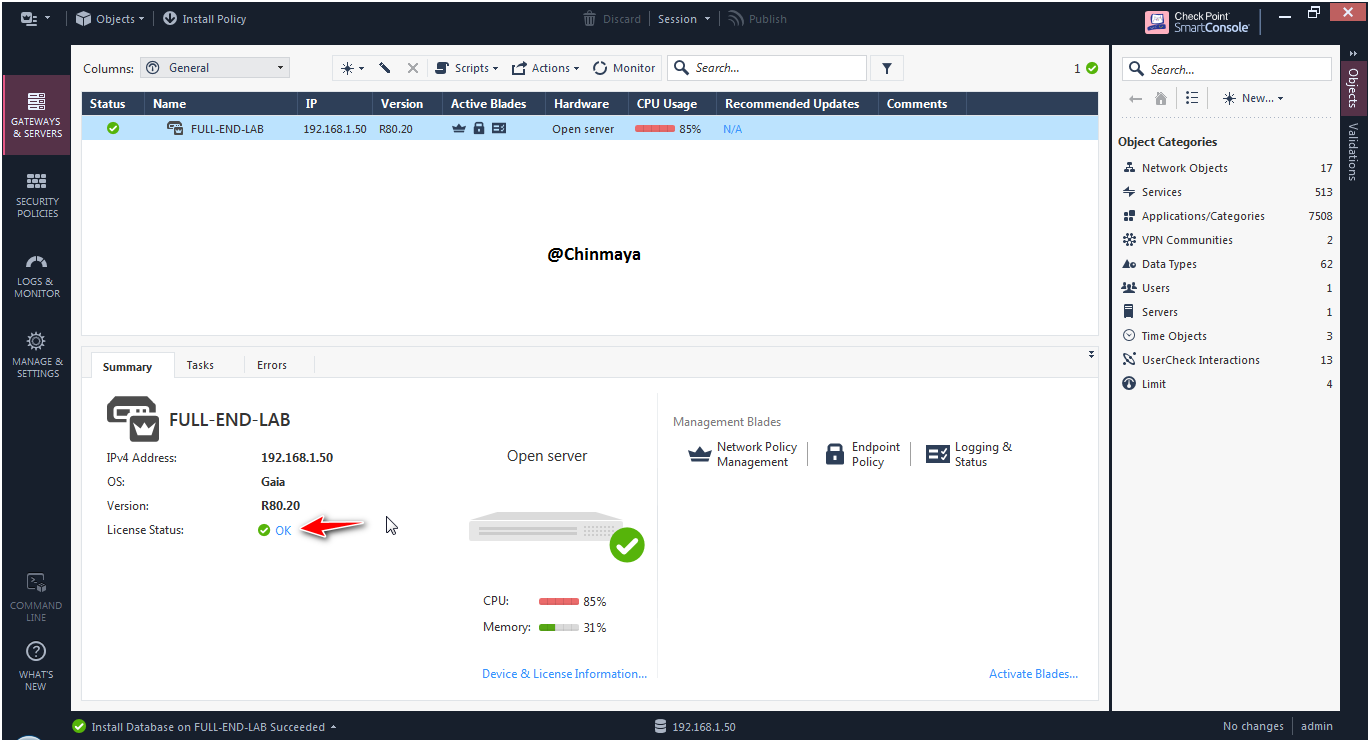
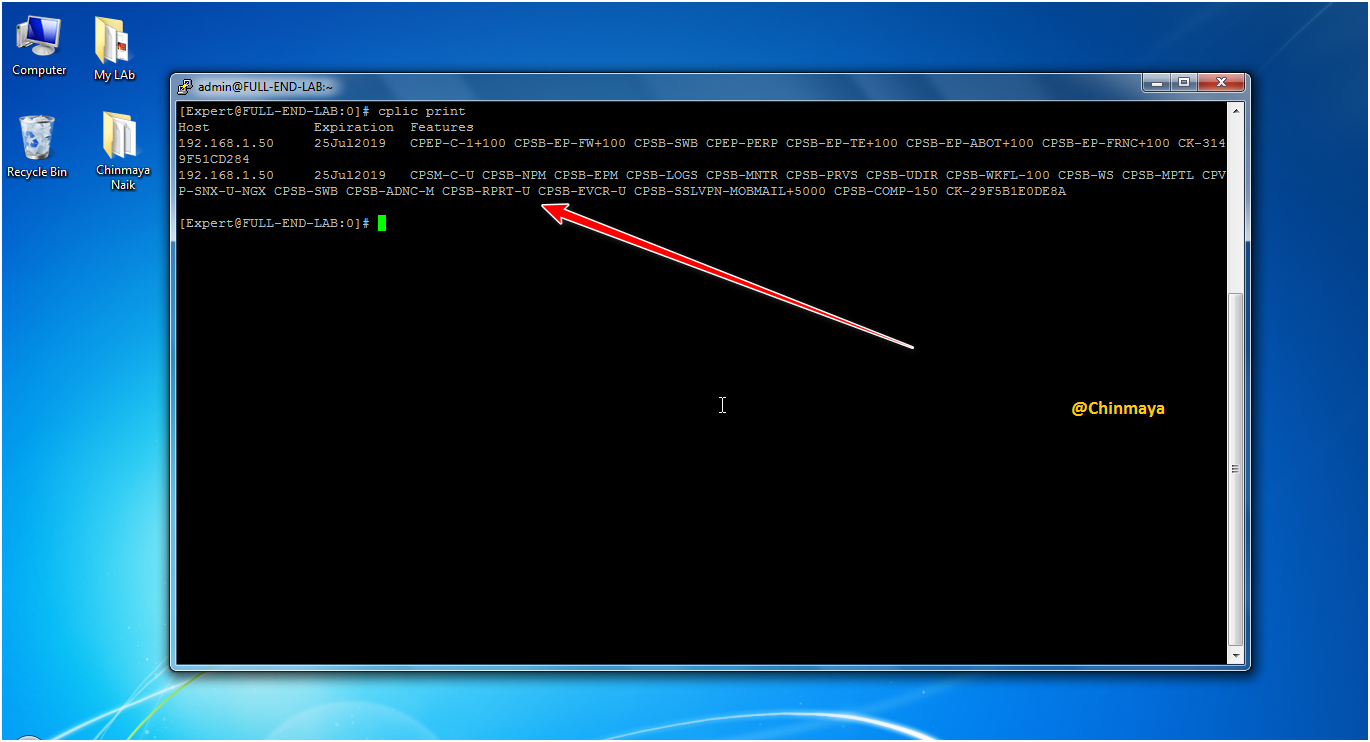
STEP: Check the license status via CLI
Command : [Clich or Expert]#cplic print
STEP : Open the “SmartEndpoint”.

STEP : Click “NO” because I am going to download the offline packages.

Go to Deployment section.
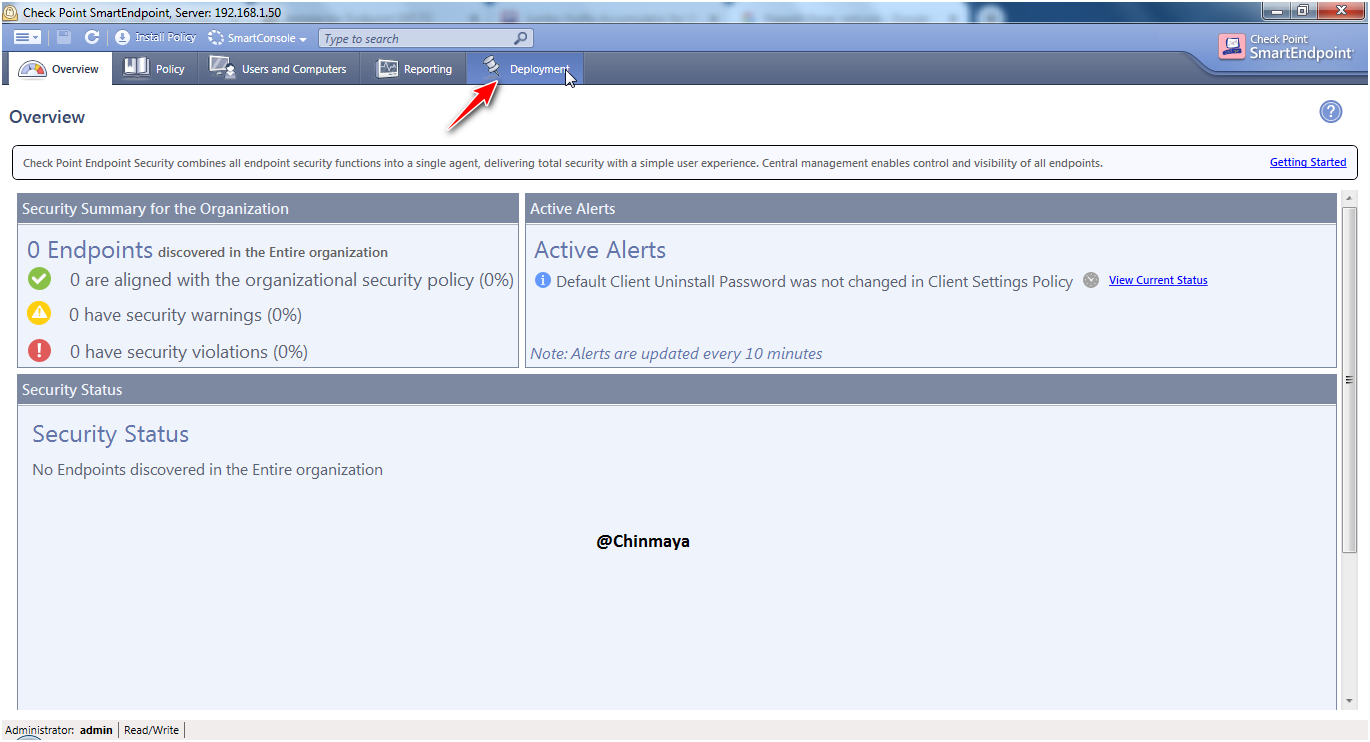
Default rule is for Entire organization and on action still we did not select any package but on next we need to import the package and create a deployment rule.

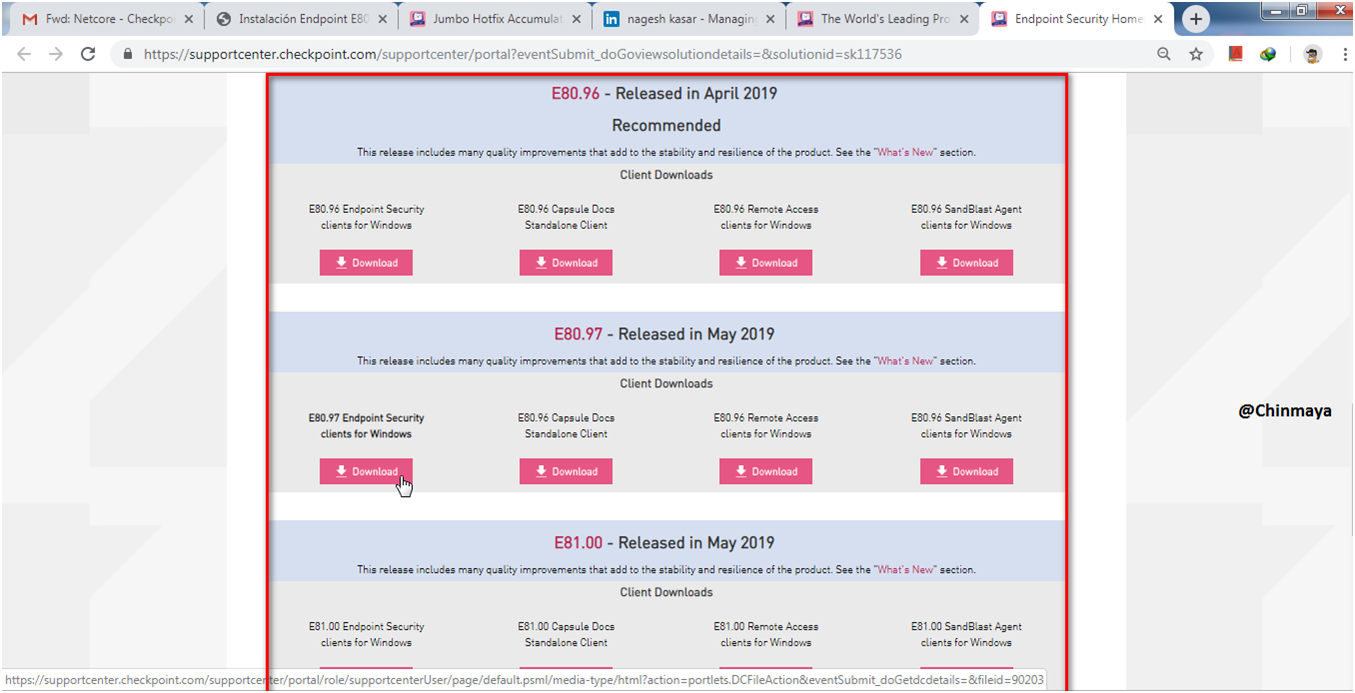
STEP: Refer sk117536 for download the latest Endpoint security client package.

STEP: I am going to download E80.97 and note down the MD5 value.
NOTE : Always download the latest client Packages.
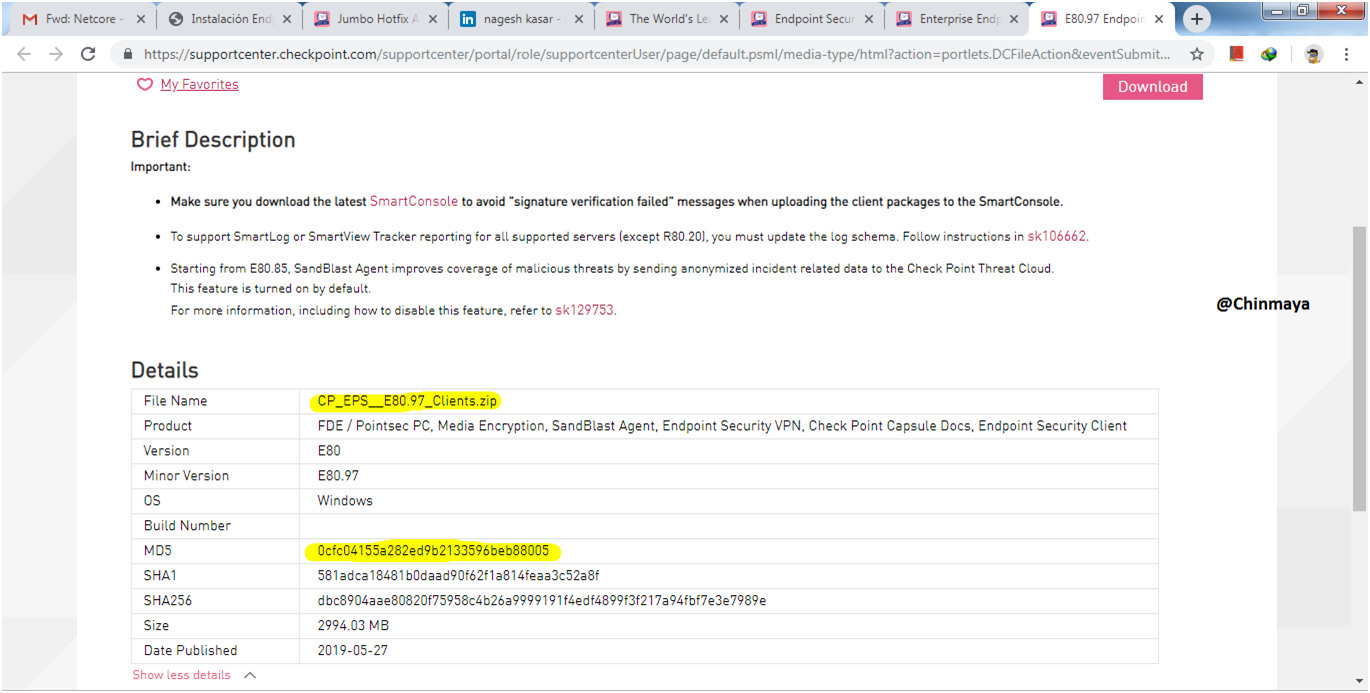
STEP: Click on “E80.97” to open the E80.97 homepage where we going to download the client package.
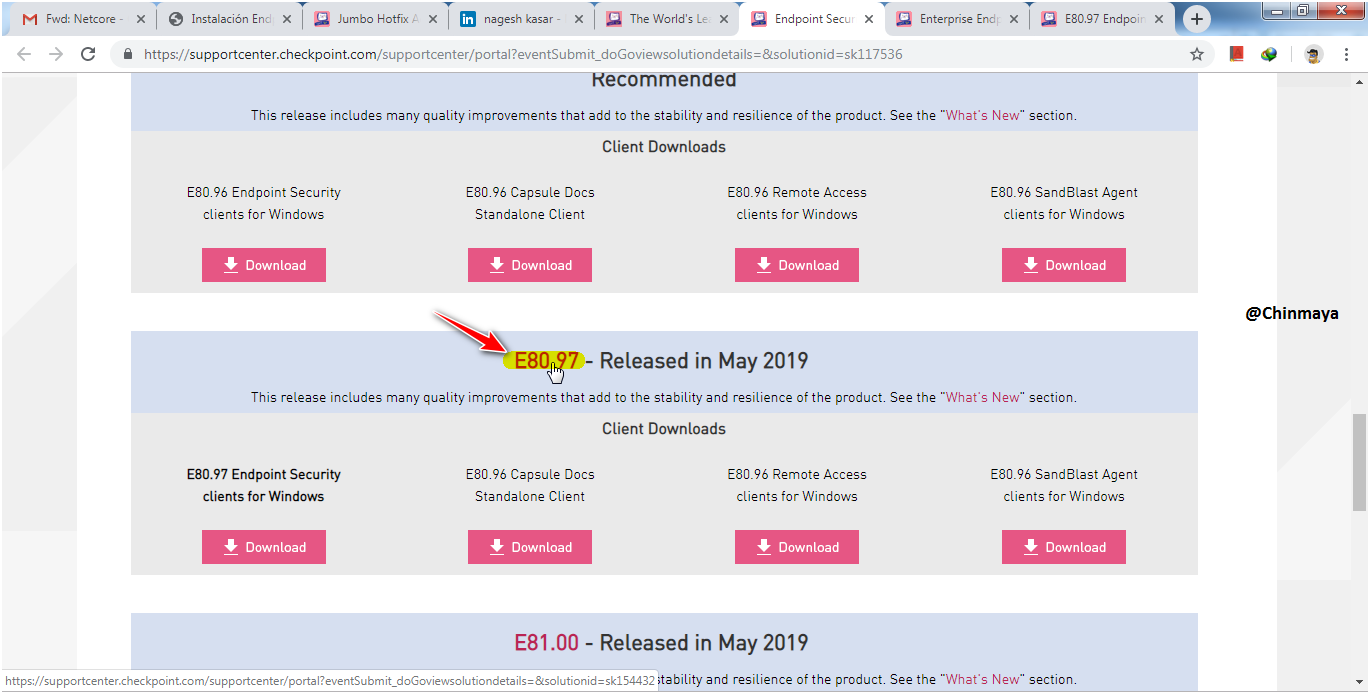
sk154432
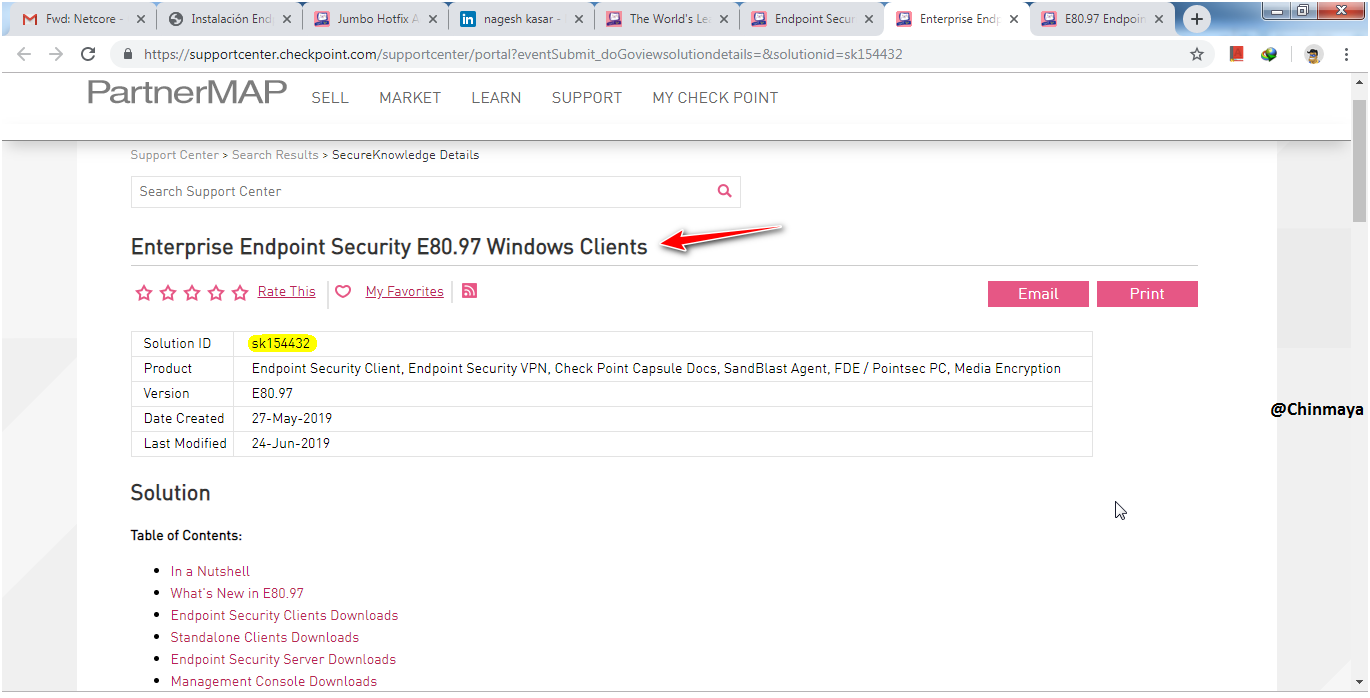
Here we see multiple package option to download but base on your requirement and base on the license you need to download those package. But we also download the Complete package (All packages) and later base on our requirement we enable those blade.
NOTE: The best practise is to download those package base on your requirement , Let’s suppose you only want SBA without Antimalware or like only required Full Disk encryption , media encryption and port protection then base on that you can download the specific package to reduce the Size of the Package.
Here I am going to download the complete package for 64 bit OS so basically I am going to install the client package on 64 bit Host Machine.
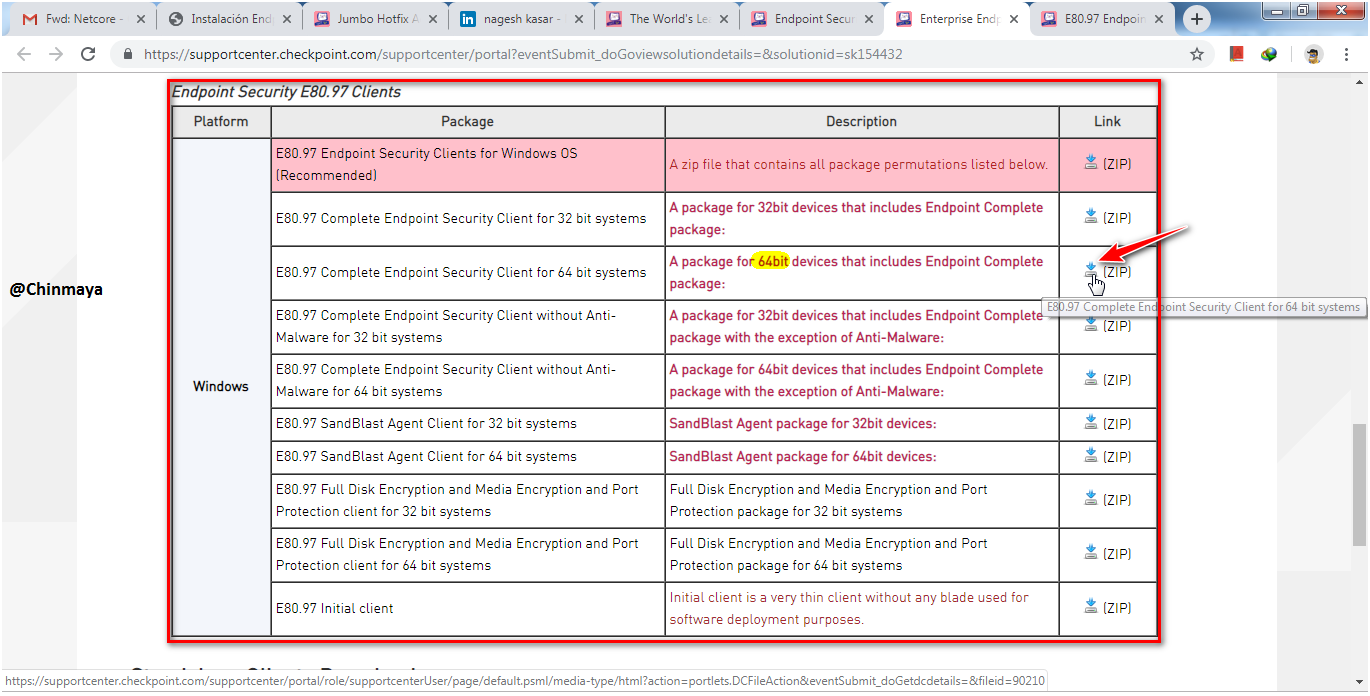
STEP : Note down the MD5 value and using MD verify tool verify the value.
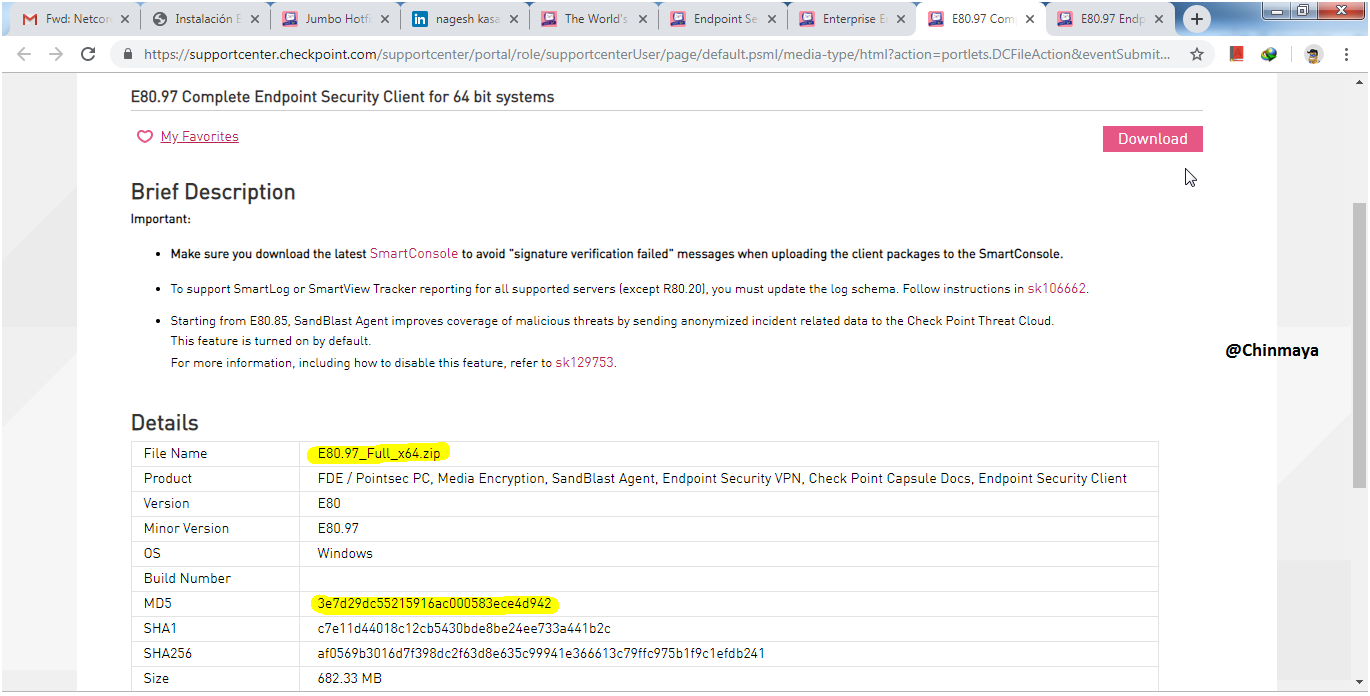
Now I have Endpoint complete package , so I am going to import the package.
Endpoint Console ---> Deployment ---> Action ---> Load a folder containing client installer..
We can also select the
1. Load latest supported client version from internet , where it require endpoint server must have internet access 2. Load client installer file , where instated of selecting the folder we select the .msi package which there on that folder (example :E80.97_Fullx64)
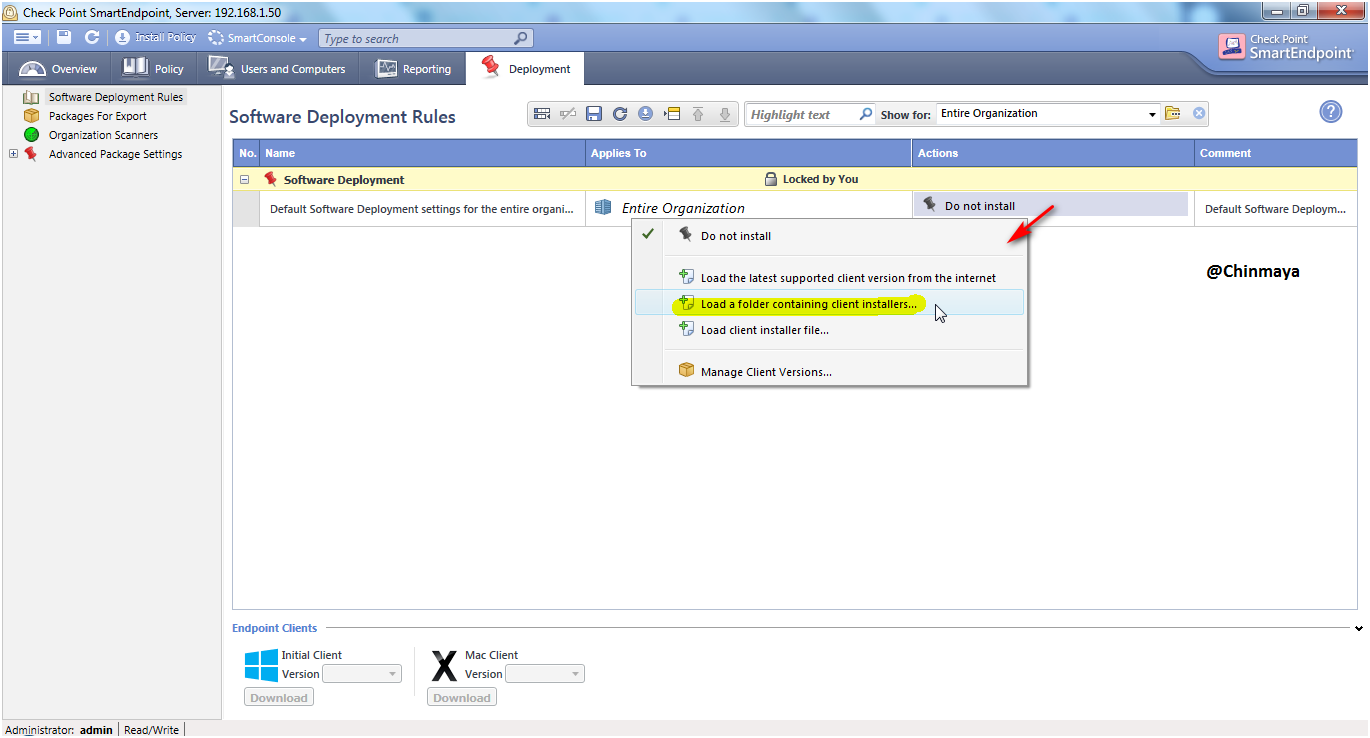
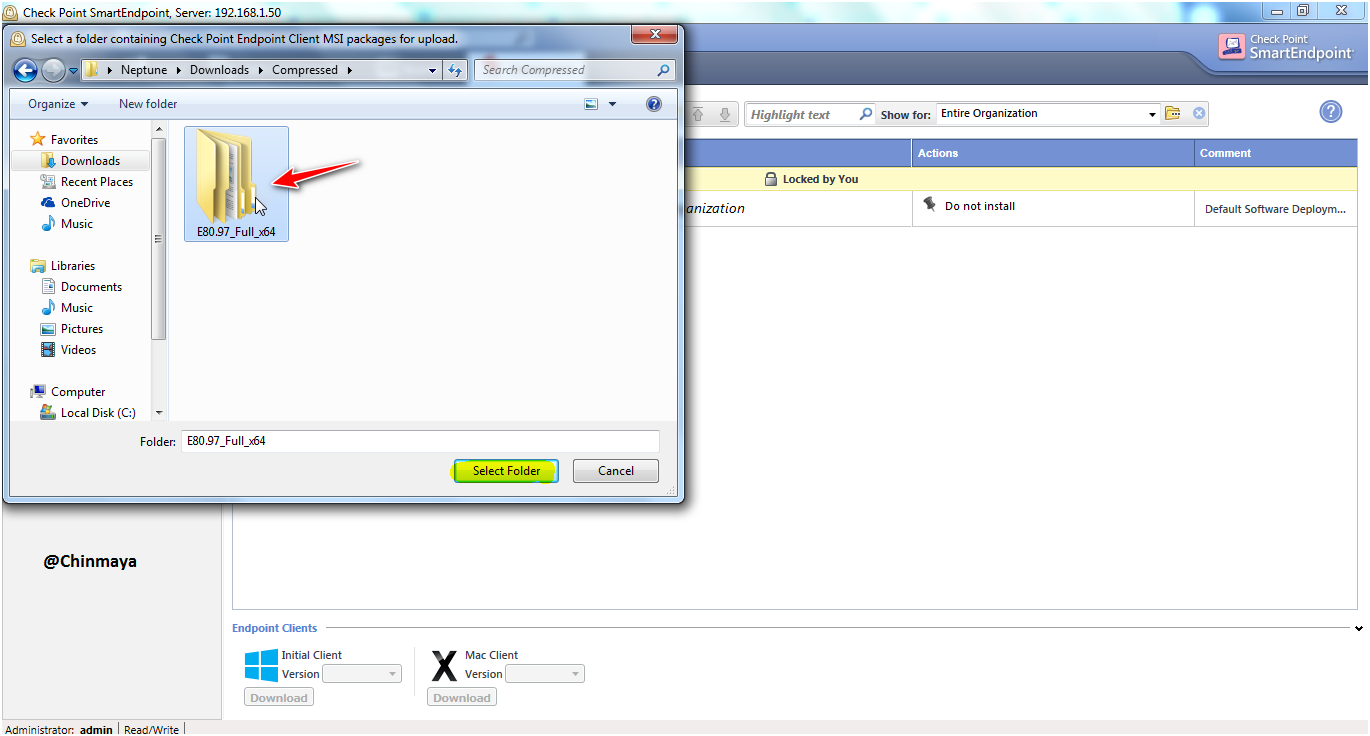
STEP: Select the Complete Package Folder (Name:E80.97_Full_x64)
NOTE : Before select the package we need to extract the Client Package (Complete package) that we download previously.
STEP: Mark “Validate packages signature” and then click “OK”.

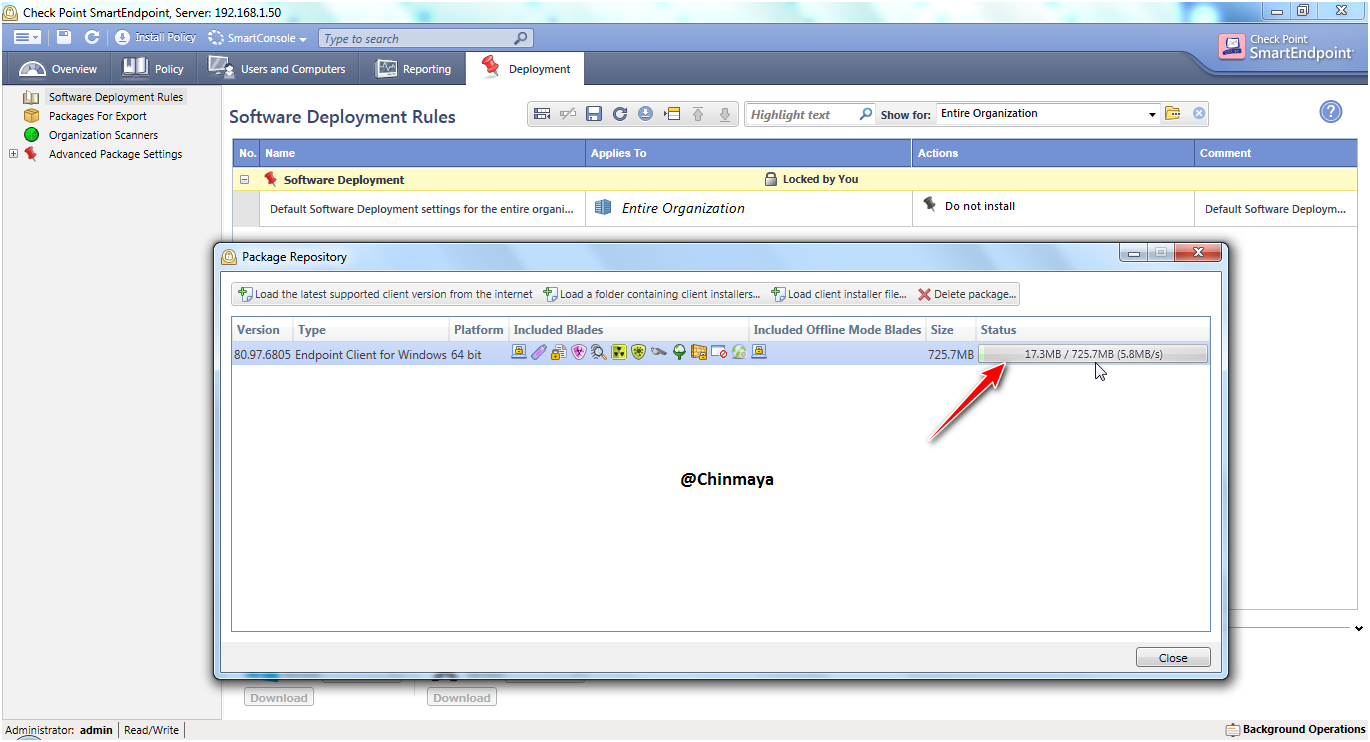
Now we able to see the imported package E80.97.

STEP : Create a Deployment rule on basic of host machine like some of the machine you want to enable some specific blade. For example like to create a policy for Higher management members and you don’t want any media encryption and port protection policy for Higher management members so you need create a Group add all higher management members machine host machine in to a one group and then create a deployment rule for those member group and accordingly we can disable or enable blade base on the requirement.
Deployment Rule also be use when you want to upgrade so like from E80.97 to E81.0 client package.
For testing you can create a deployment rule for specific machine (test machine) or you can also upgrade on the existing deployment rule where already E80.97 is exist so basically you can check the behaviour of the new client like E81.0 so base on that you can upgrade the all available Endpoint client.
Before I am going to create a deployment rule for a particular group , first I need to create a Group.
STEP: Open User and Computers tab.

STEP: Create a new Virtual Group.
STEP: Click “OK”.
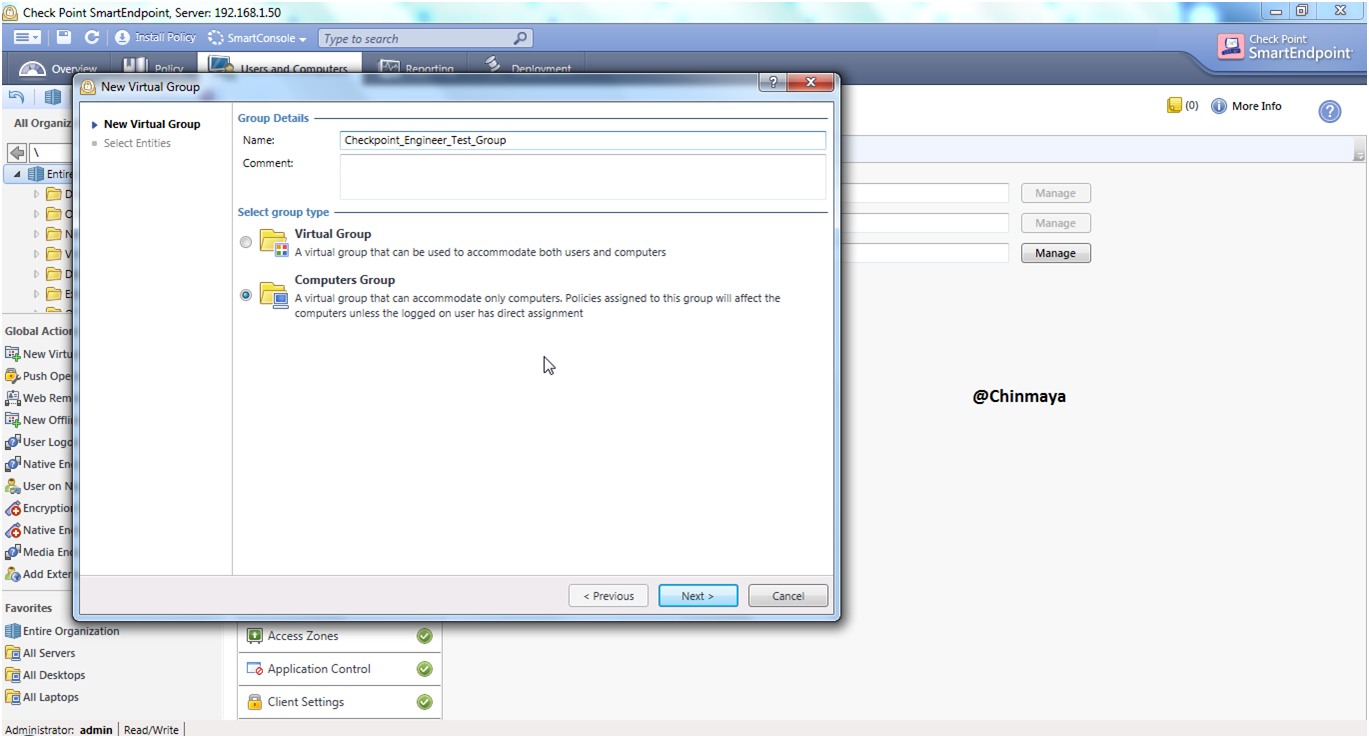
STEP: Give a name to the Virtual Group and Select Group type as “Computer Group” then click “Next”.
Name: Checkpoint_Engineer_Test_Group
NOTE : We can also select Virtual Group as well , Virtual Group is for both User and Computer but Computer is base on the machine base only.
STEP: Select Virtual Group.
STEP: Click “Yes” then click “Finish”.
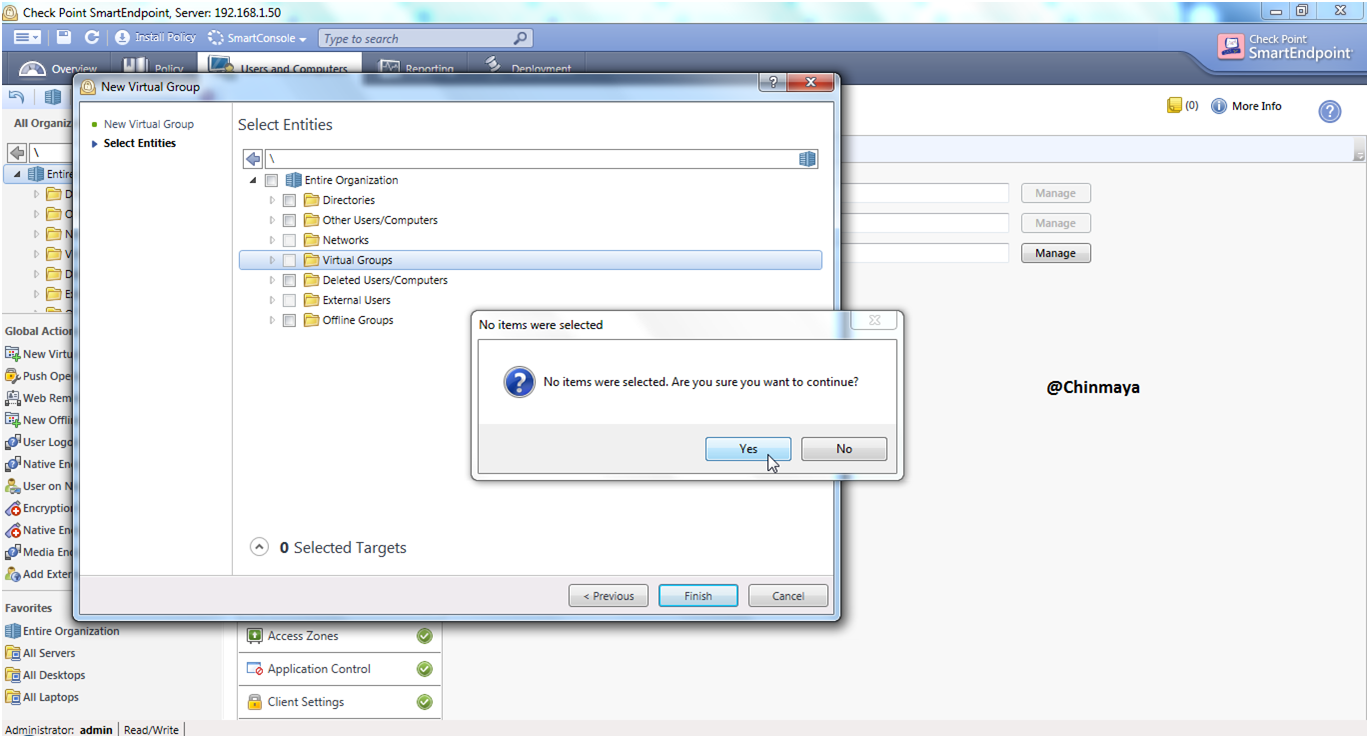
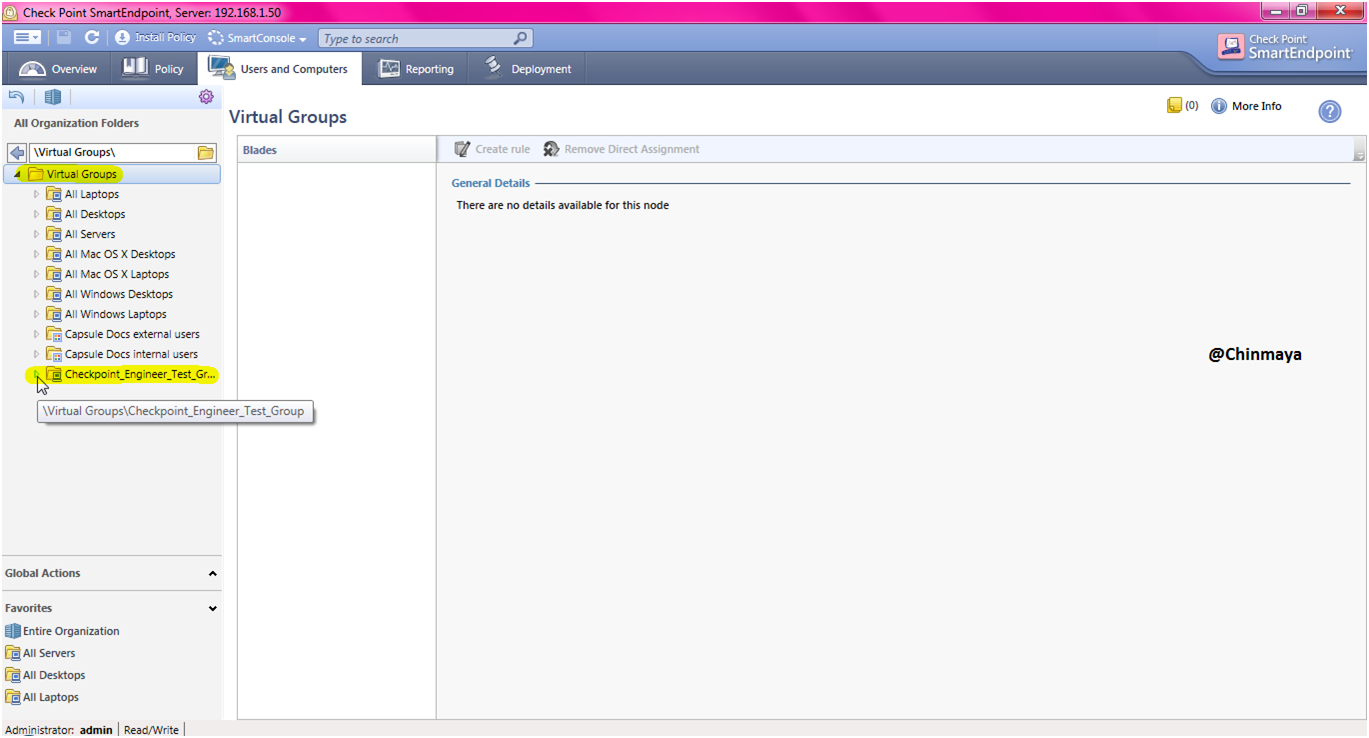
STEP: Verify the Group is created or not. (Name: Checkpoint_Engineer_Test_Group)
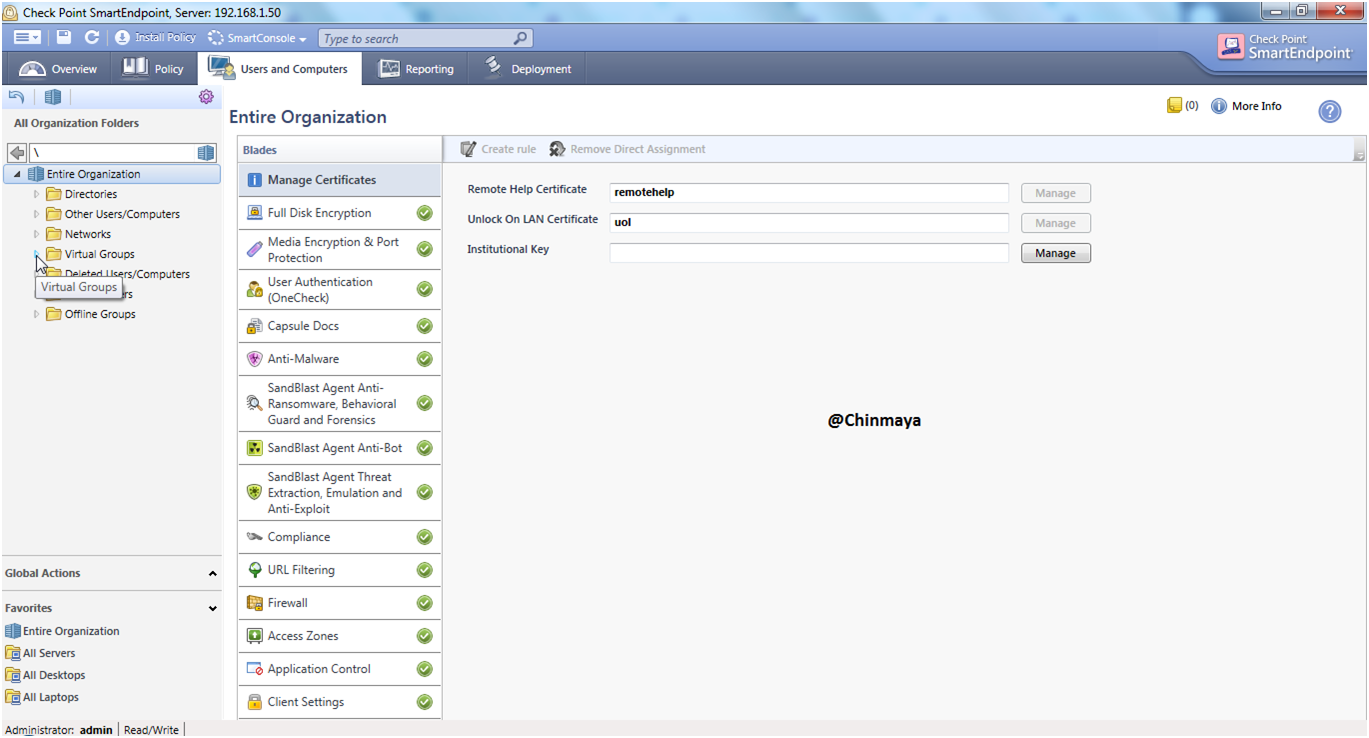
Group is showing inside the Virtual Groups
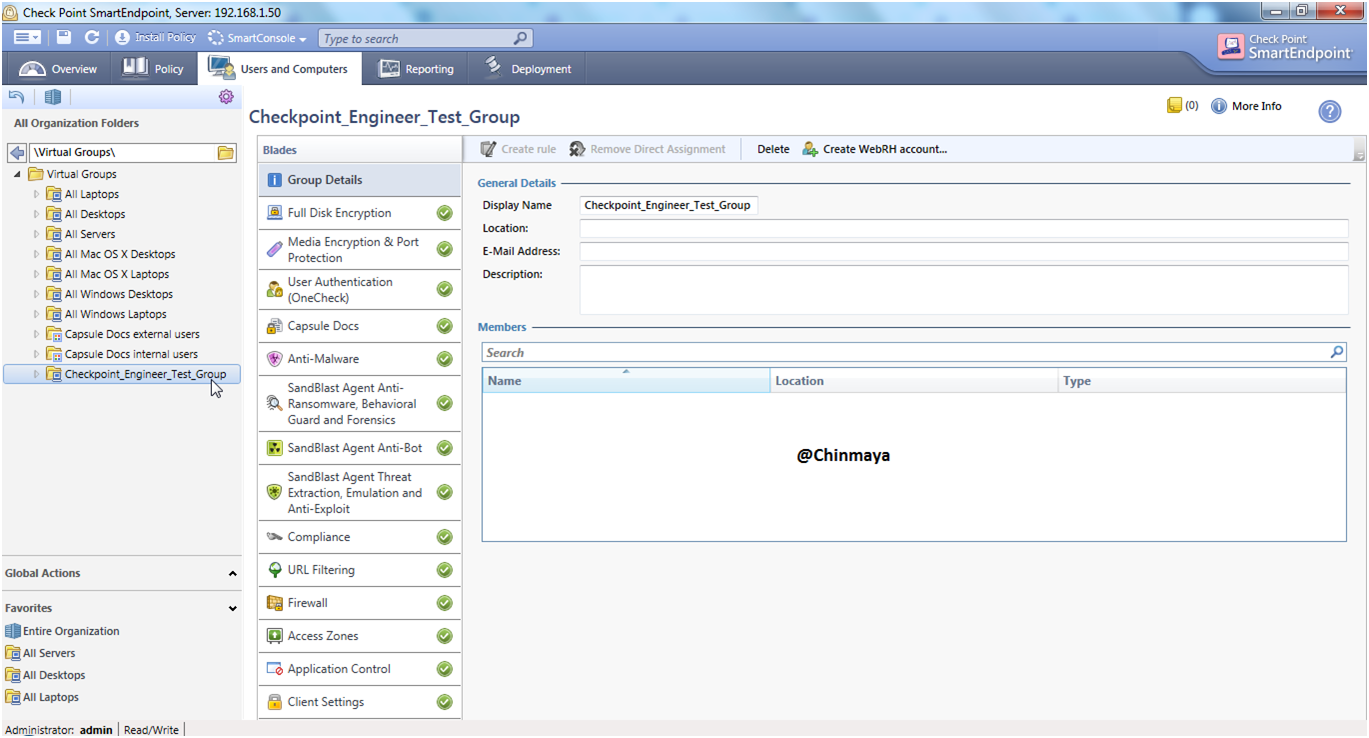
STEP: Create a deployment rule for a particular group.
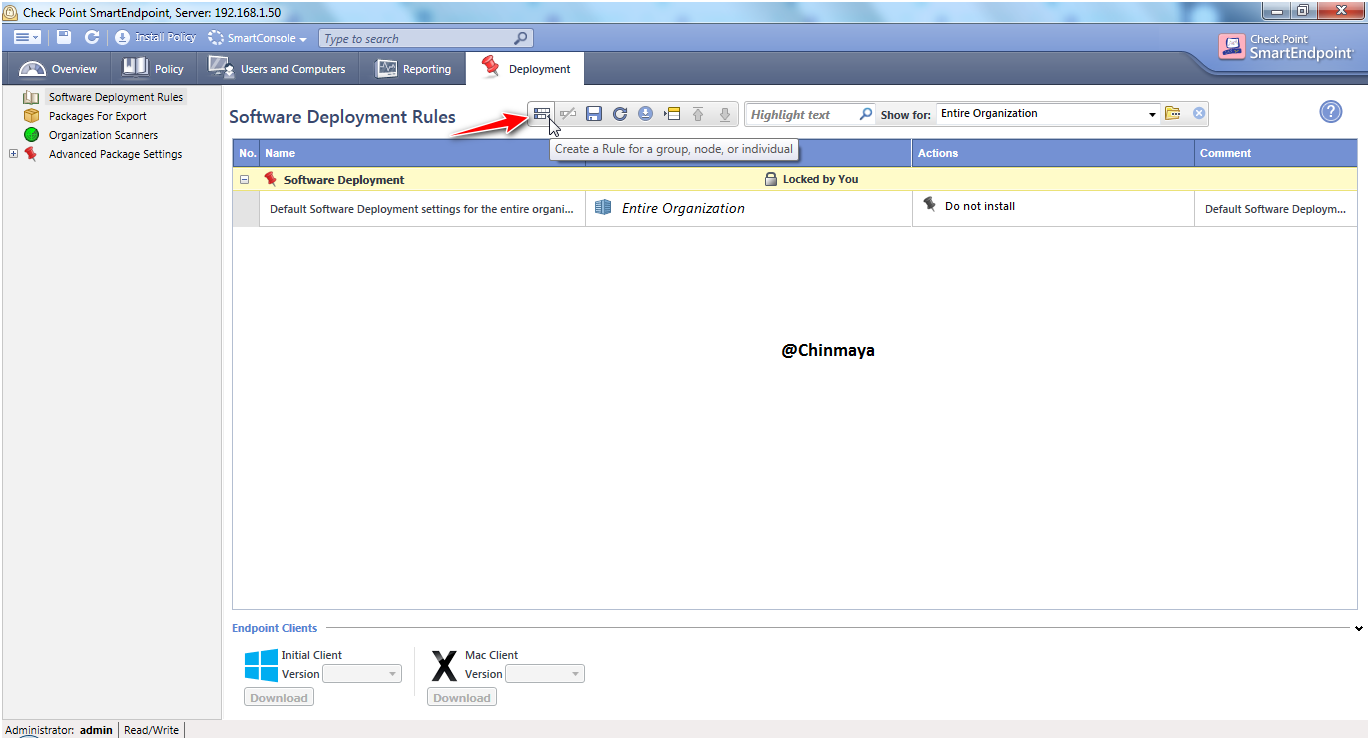
STEP: Select the virtual group.
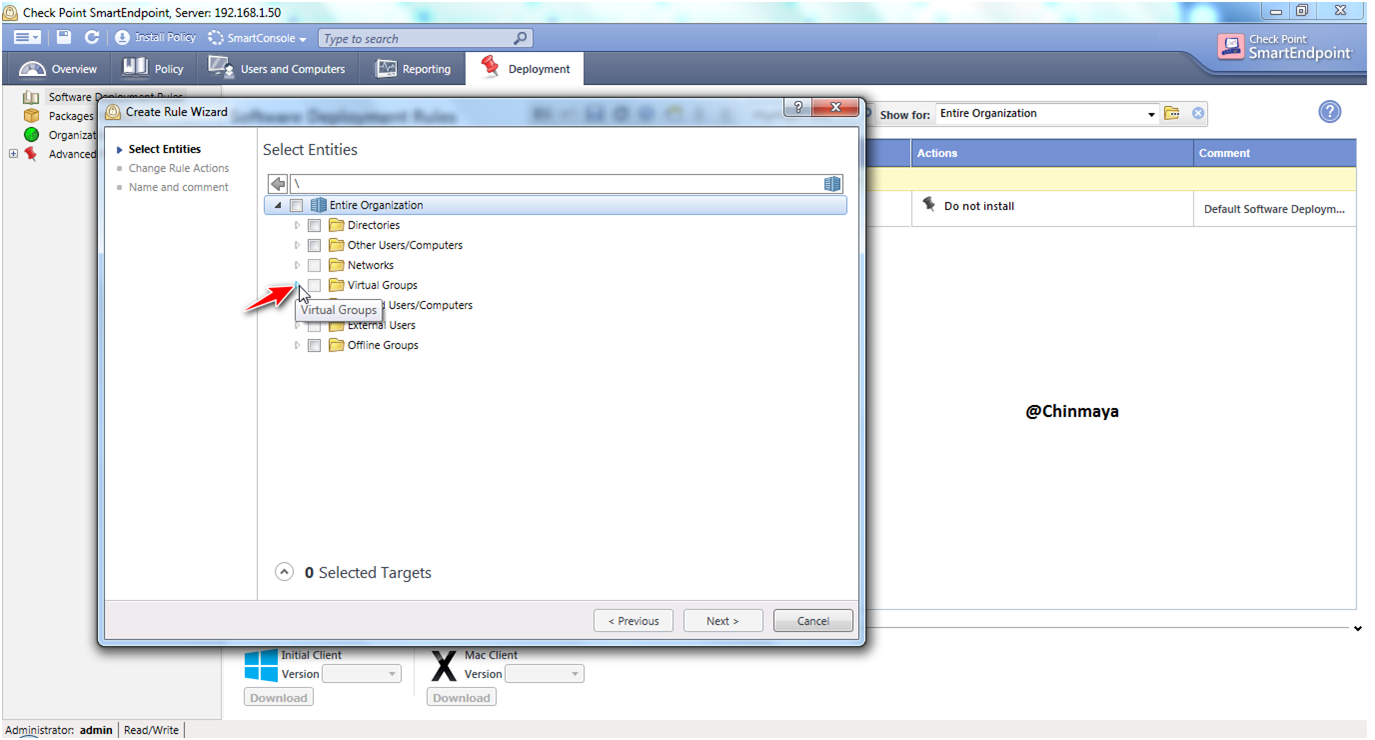
STEP: Inside the virtual group select the Group that we already created (Group name: Checkpoint Engineer Test Group) then click “Next”.
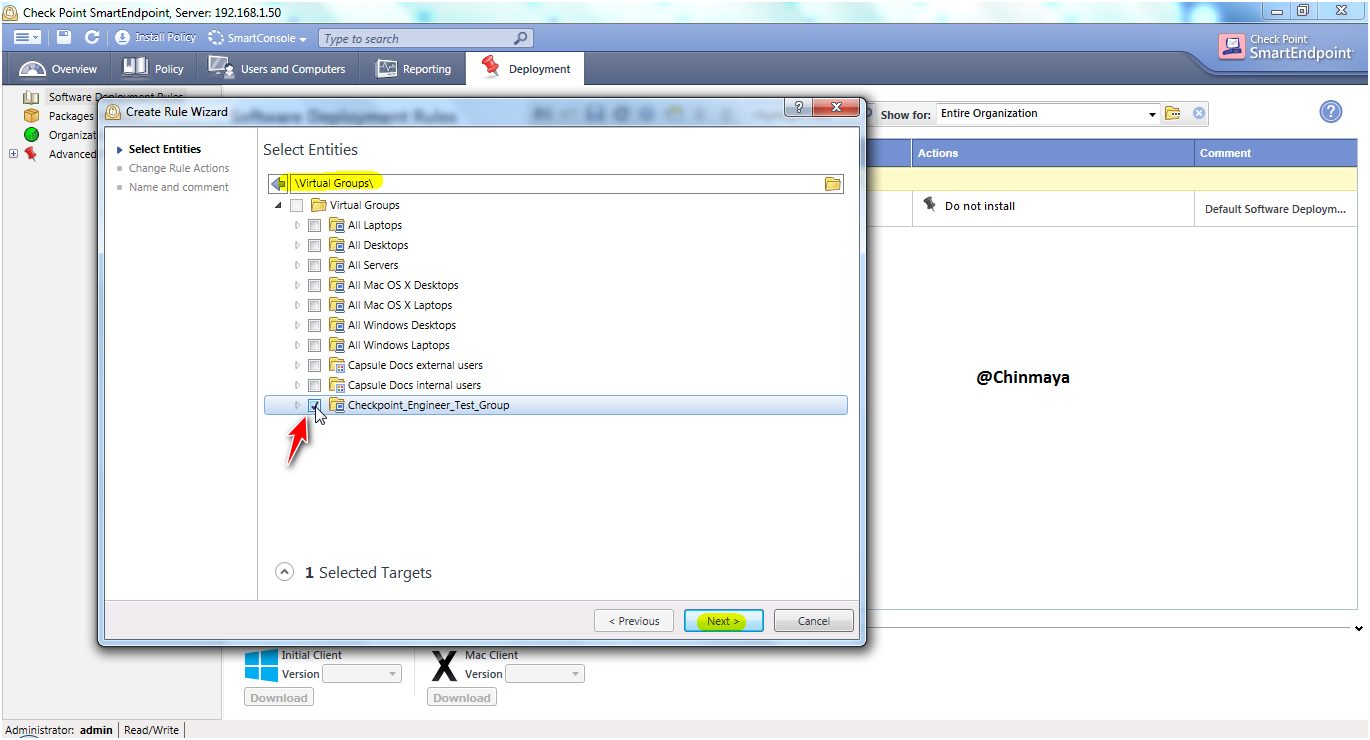
STEP: Select the Endpoint client package then click “Next”.
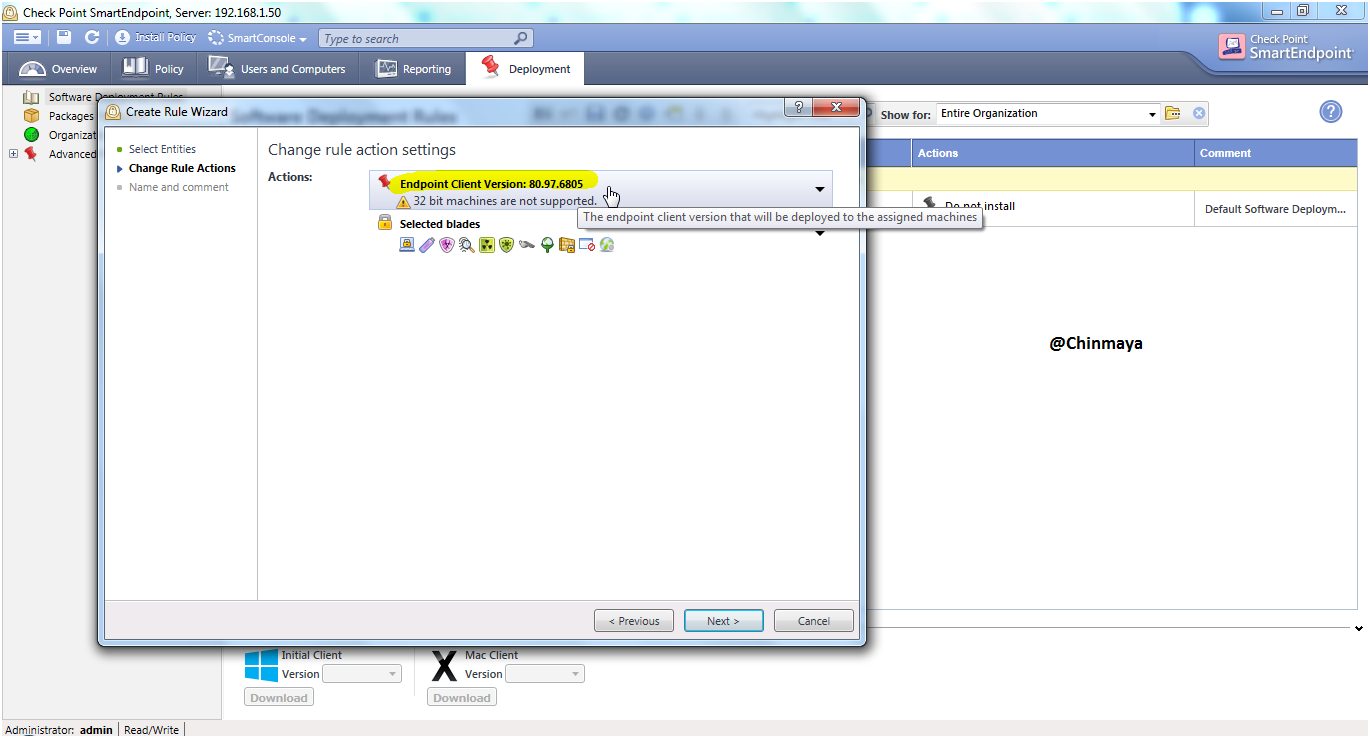
STEP: Check the enable blade , we can disable the blade which not required for your organization.
Note : For testing I am going to keep Endpoint Connect VPN blade enable and later on we remove this blade.
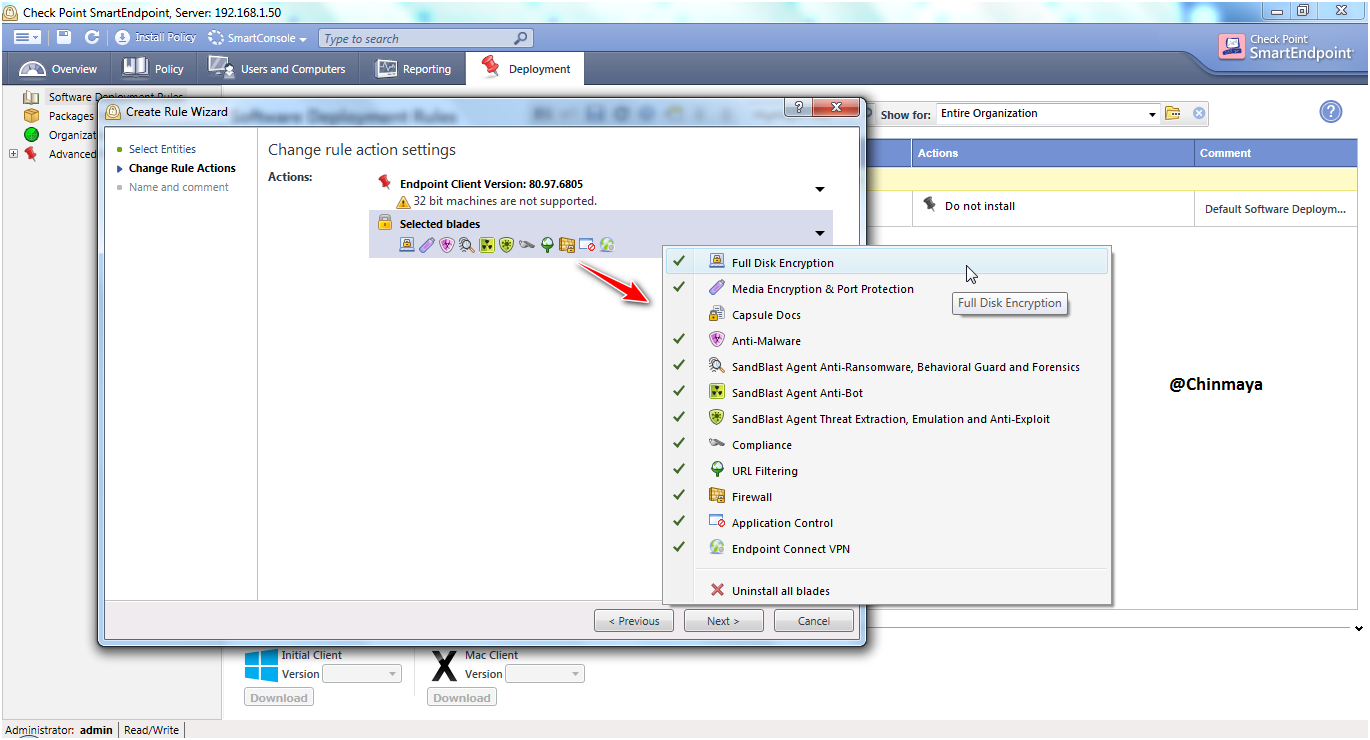
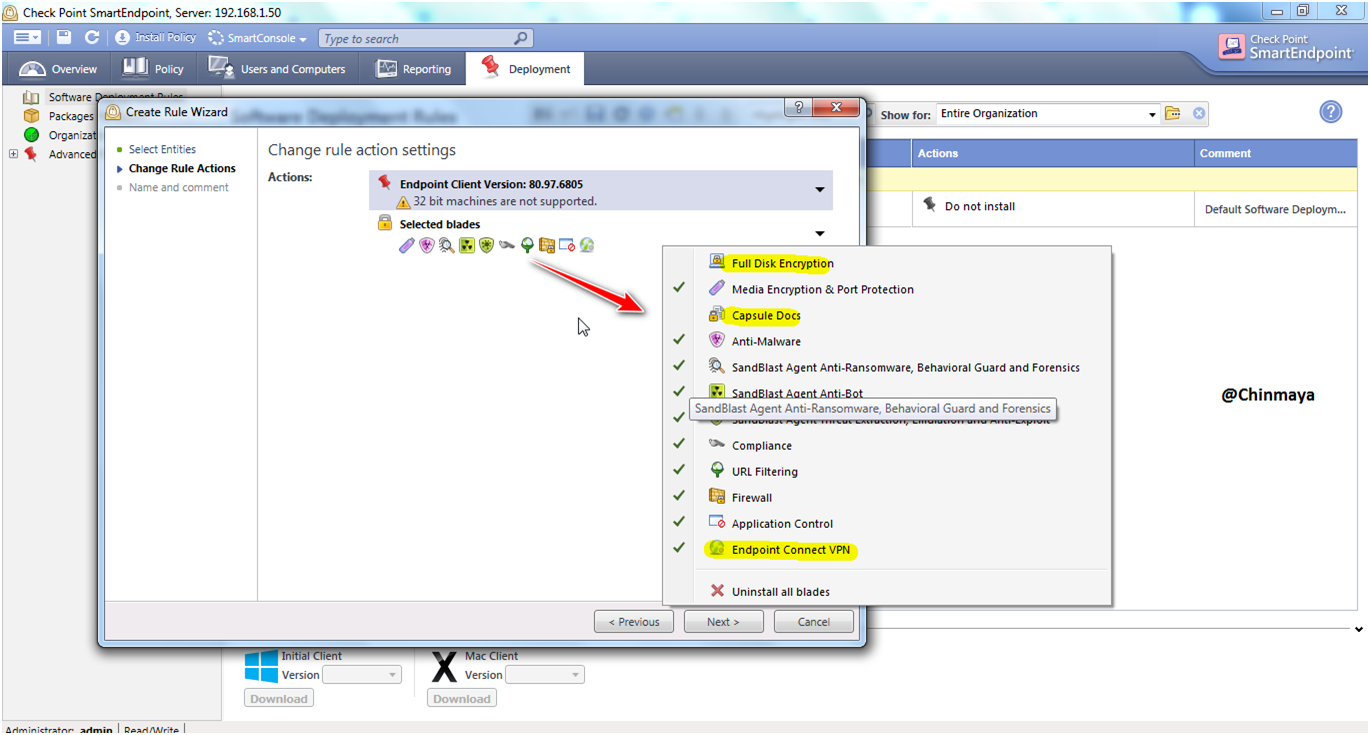
STEP: Select the “Next”.
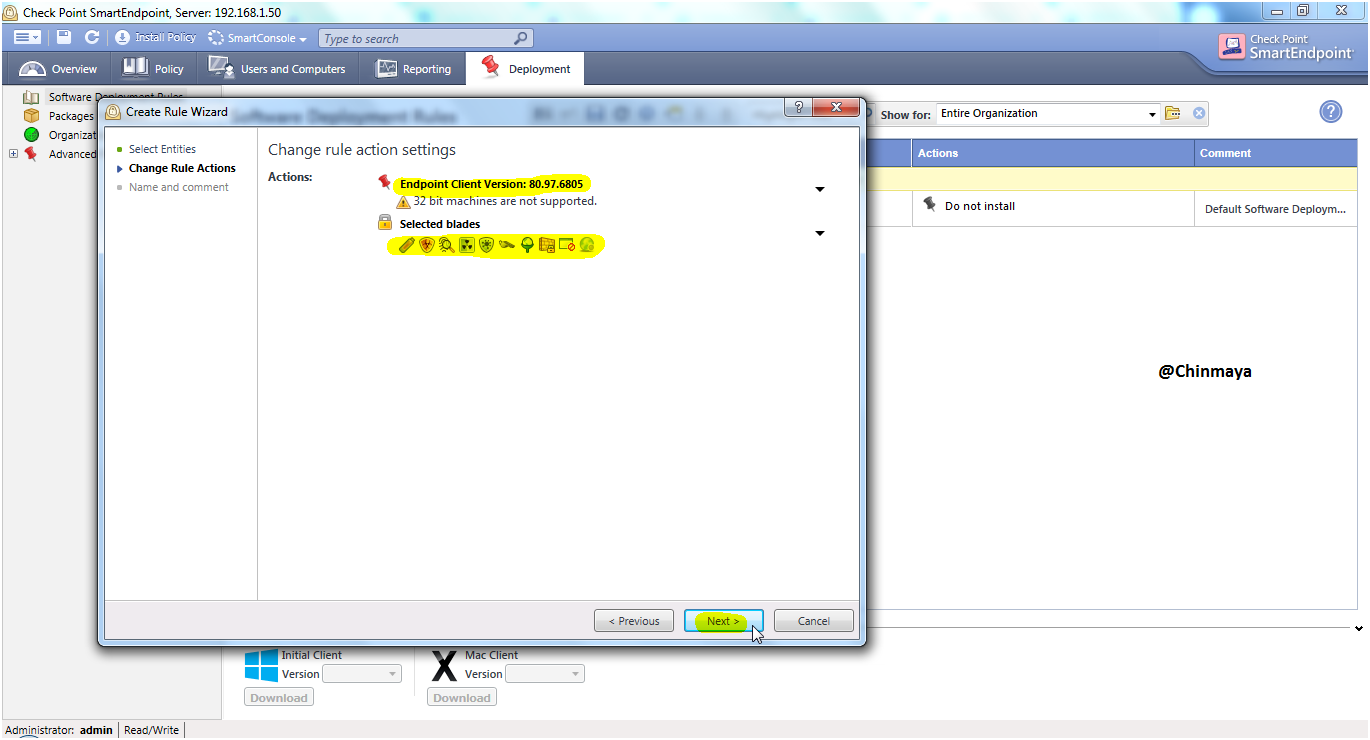
STEP: Give the Rule name (Checkpointengineer_test_Deployment_Rule) and click “Finish”.
STEP: Re verify the rule is created or not .Also check the enabled the blade.
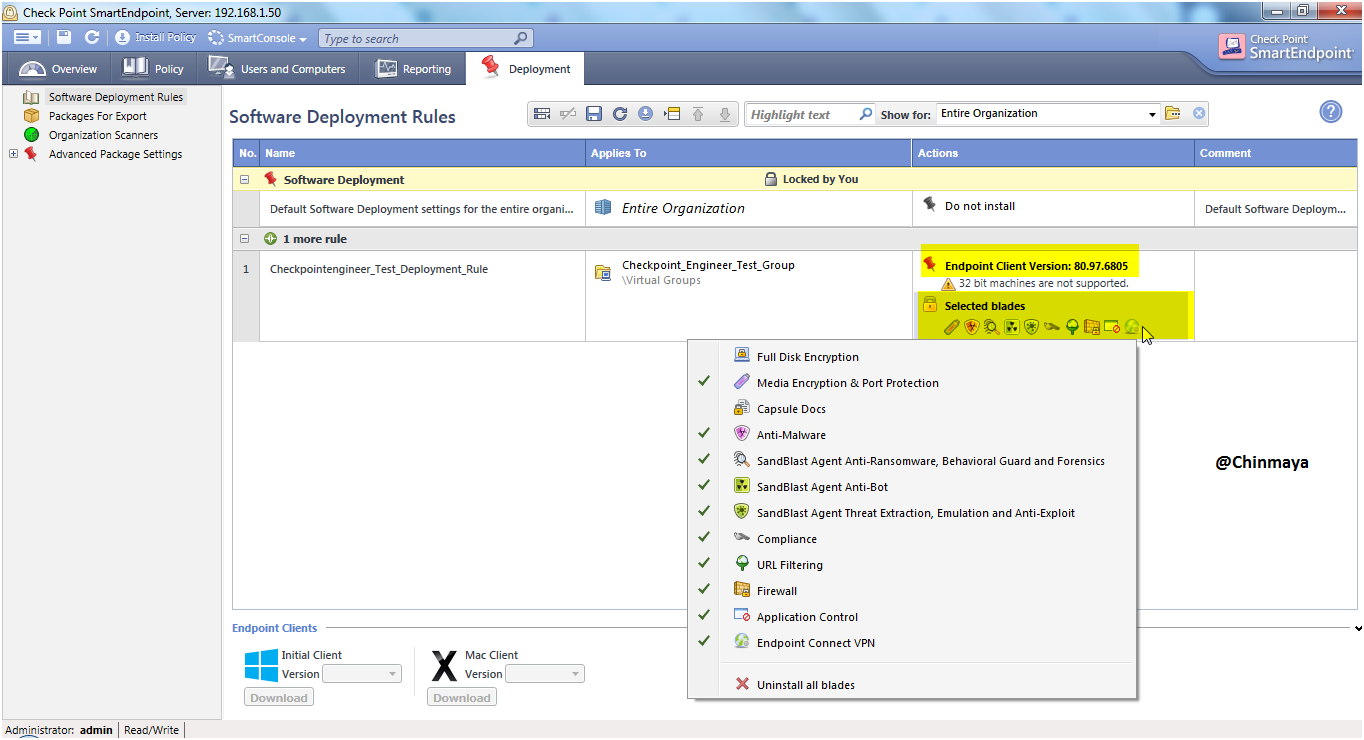
STEP: Go to “Package For Export” for exporting the client package and later we install in the windows machine.
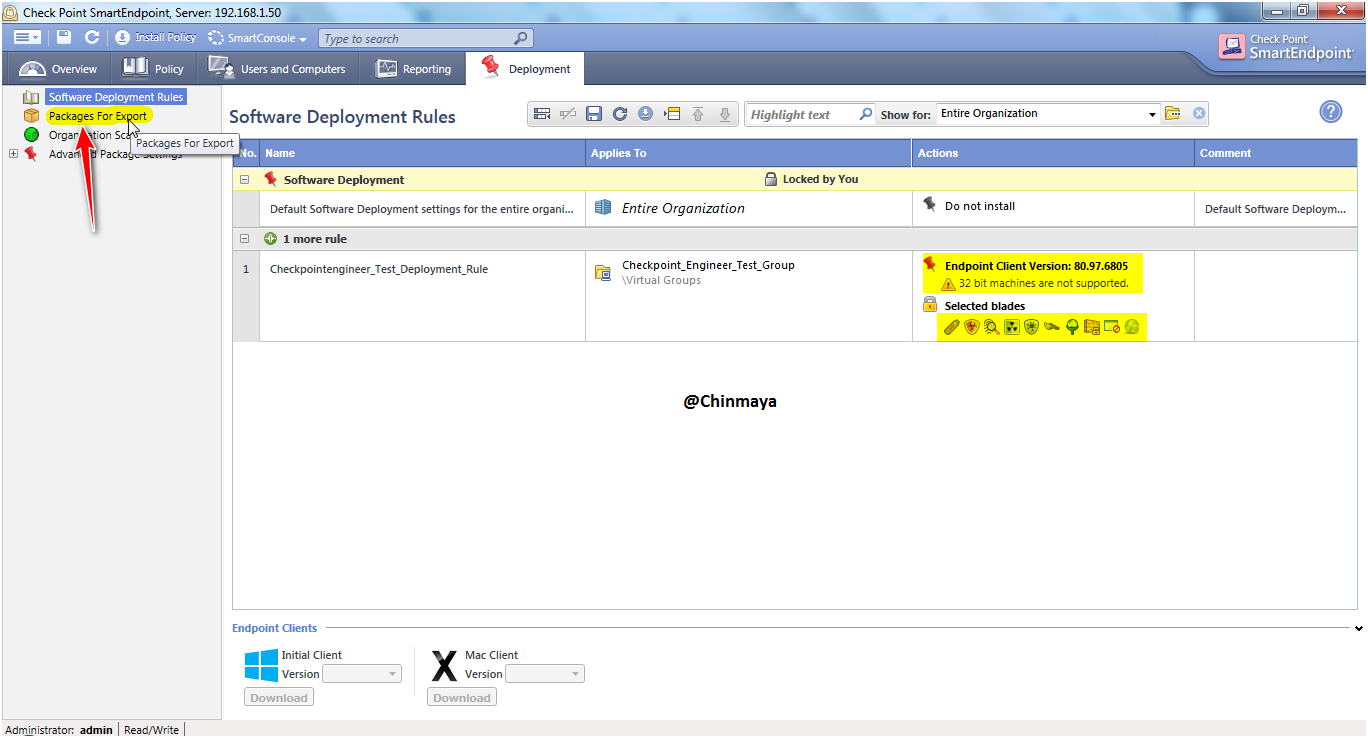
STEP: Click on “Add Package”.

STEP: We able to see the Package information but make sure that the correct version is selected or else you can click on the “Client version” to change the version.
NOTE: Now this is most important part you need to select the correct blade before you download the package for Laptop or Desktop.
So basically Checkpoint segregate into two different part like Laptop and Desktop , so base on your Machine you need to export the client package and install it on Host machine either on Laptop or Desktop.
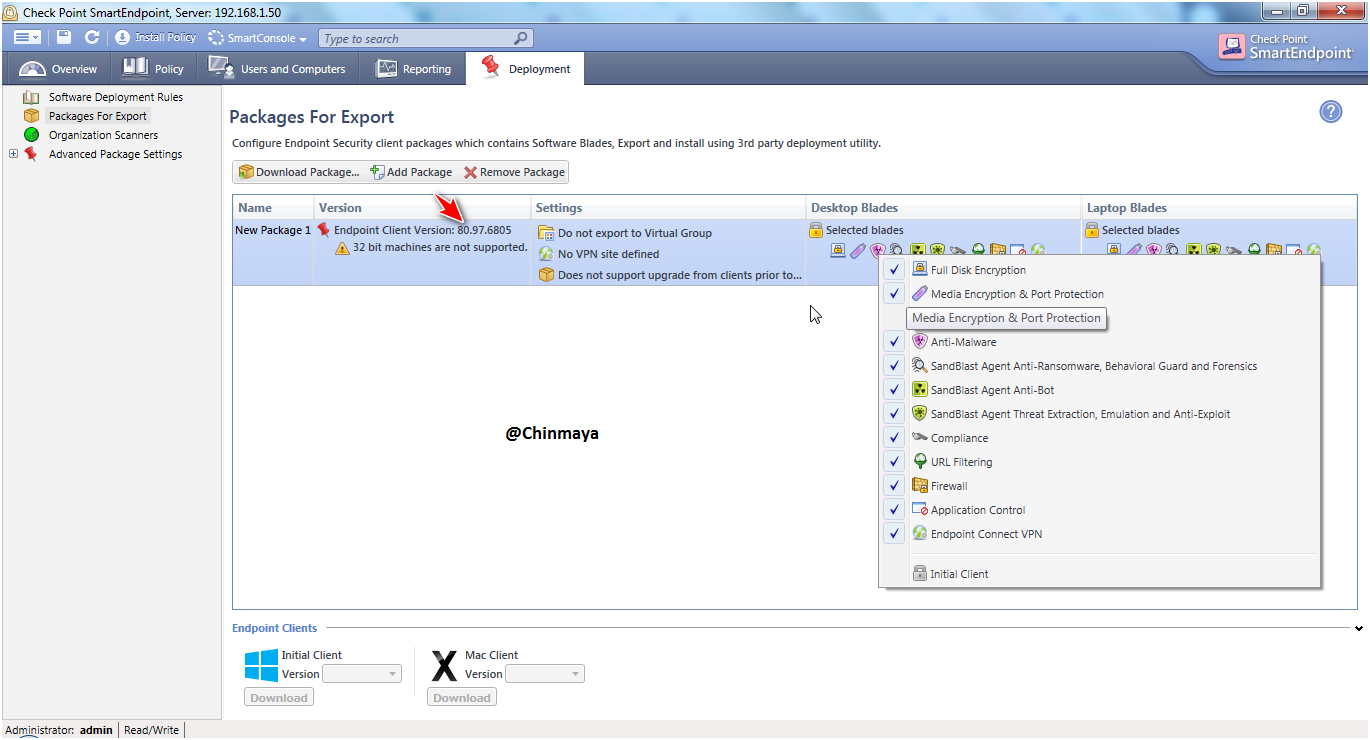
For Desktop enable or Disable the blade base on your need.
NOTE : I Always recommended all to disable the Full Disk Encryption blade for first time when you download the client package even your requirement is also Full Disk Encryption, For Full Disk Encryption Its always be good to test for few machine with different flavour like windows8 or windows 10 or windows server in your environment. So basically during the download the client package first disable the Full Disk Encryption balde and after deploy then enable the Full disk Encryption blade using Software Deployment Rule and reinstall the policy.

For Laptop select the blade.

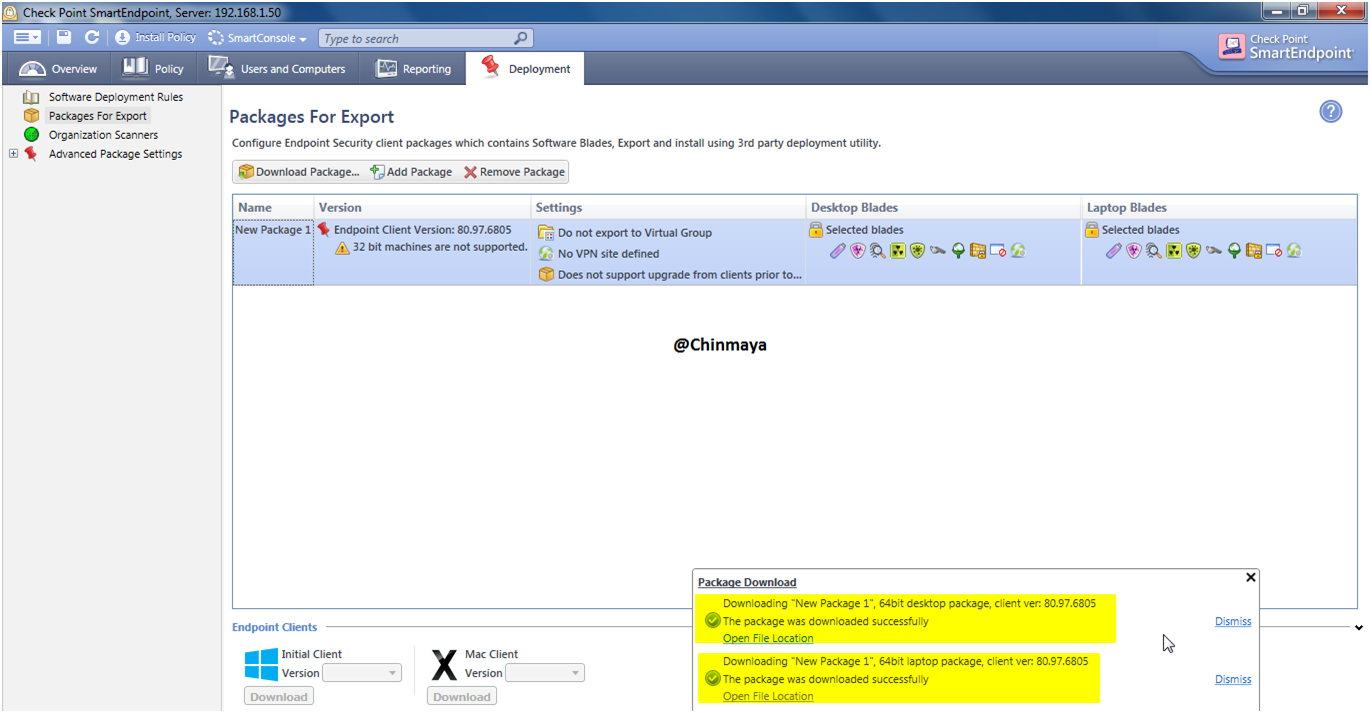
STEP : Right click on New Package 1 to download the client package.
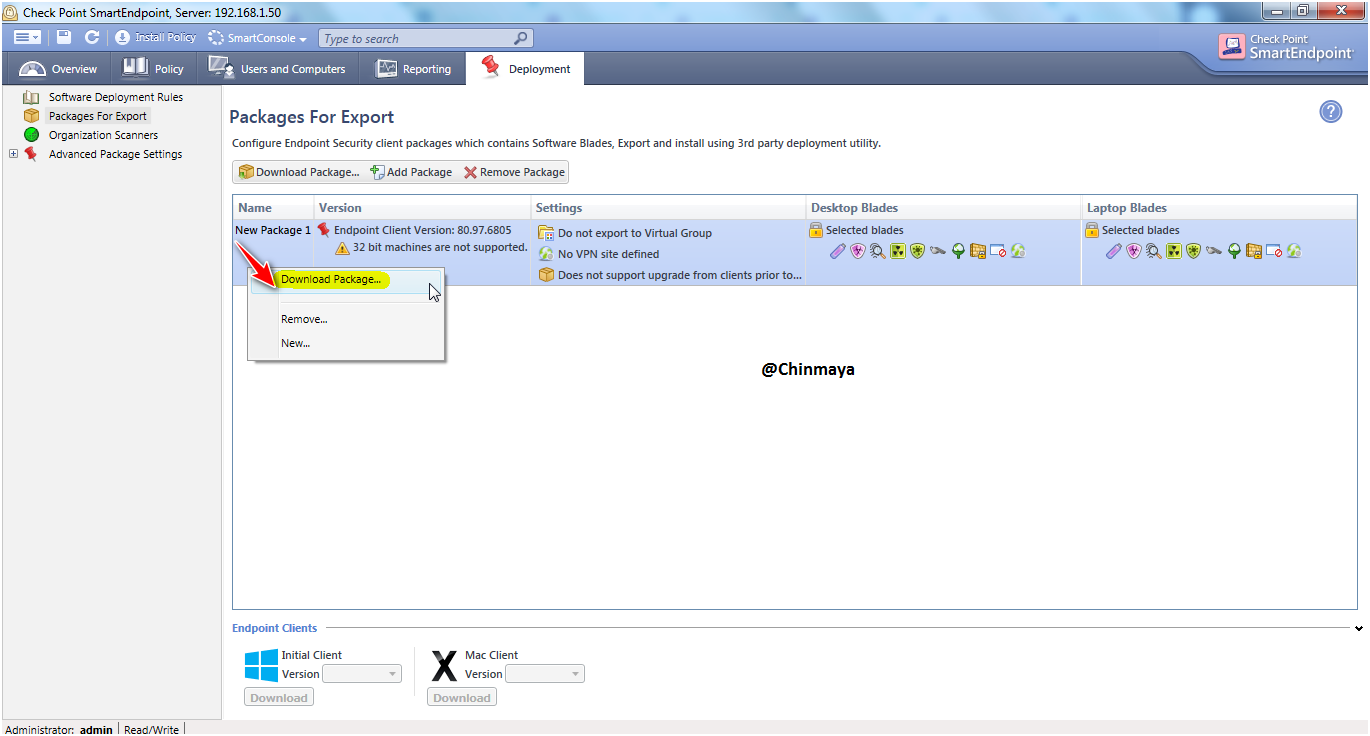
STEP: Click the “Download” to download the Endpoint client for client machine.
Note: The 32-Bit grade out because we not import the 32-bit . Checkpoint provide both flavor like 32 bit and 64 bit . We need to import the package base on our requirement.

Processing
Click on Open File Location to check the package is successfully export to a folder and inside that Folder you see Laptop and Desktop Folder.
STEP: Click on “Save” icon to save.
STEP: Open the Windows 7 VM to install the client on windows 7 machine.
I am only demonstrate for windows 7 but windows 7 required additional package. Also windows 7 is out of support now so recommended version is Windows 10.
Before install the client package we required a next hop like route , L3 switch or a firewall where I need to give the internet access to the Endpoint Server and the windows machine.
So basically I am going to create a new VM with R80.20 Standalone.
Network Setup
VMnet1 (eth0) : IP address : 192.168.1.0/24 VMnet0 (eth1) : Auto Bridge : 172.16.100.0/24
IP Address
eth0 : 192.168.1.2/24 eth1 : 172.16.100.130/24 Default Gateway : 172.16.100.1/24
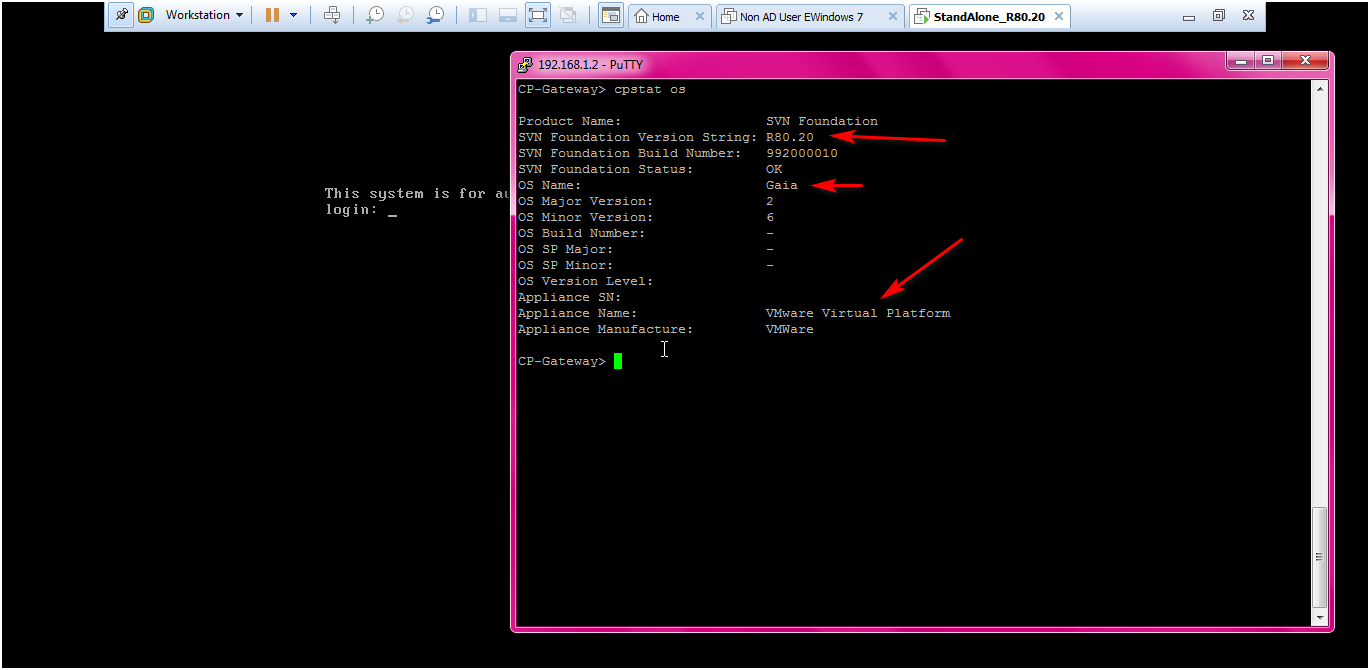
STEP : Open the CP StandAlone VM then the check the below command to verify the setup.
Command : clish > cpstat os
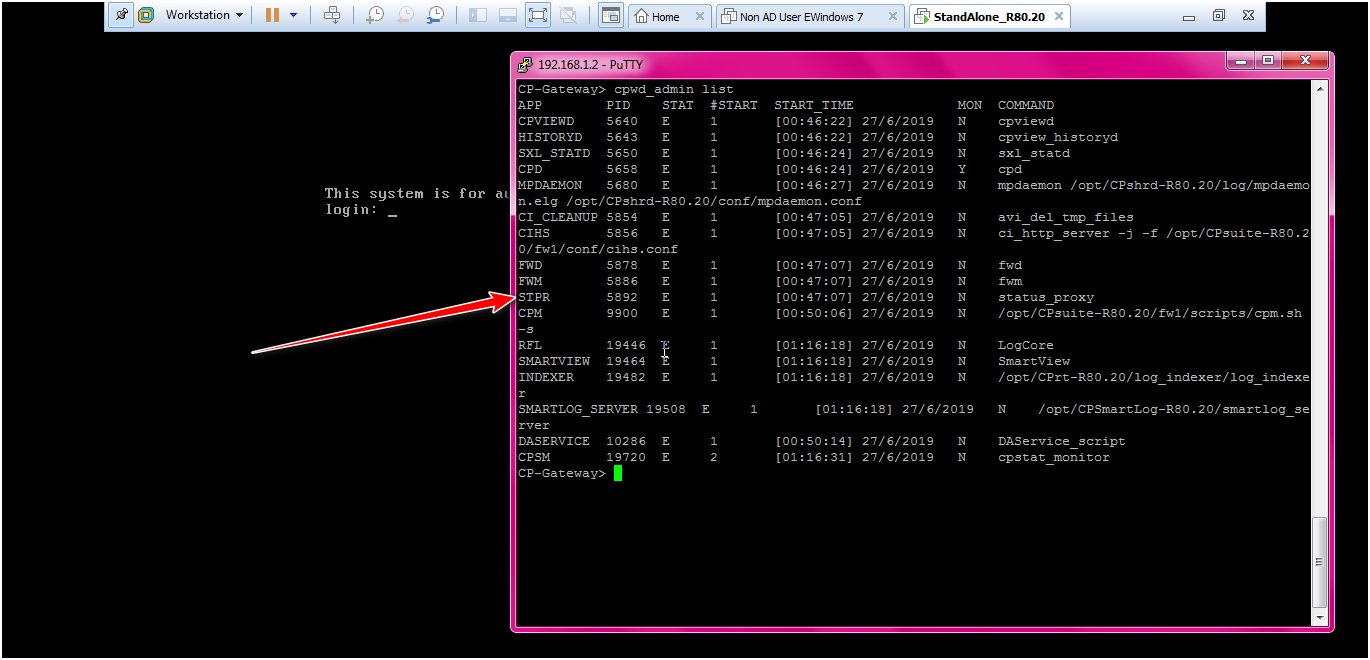
STEP: check the services.
Command : clish or Expert >cpwd_admin list
STEP: Check the System information.
Command : Clish_or_Expert#cpview
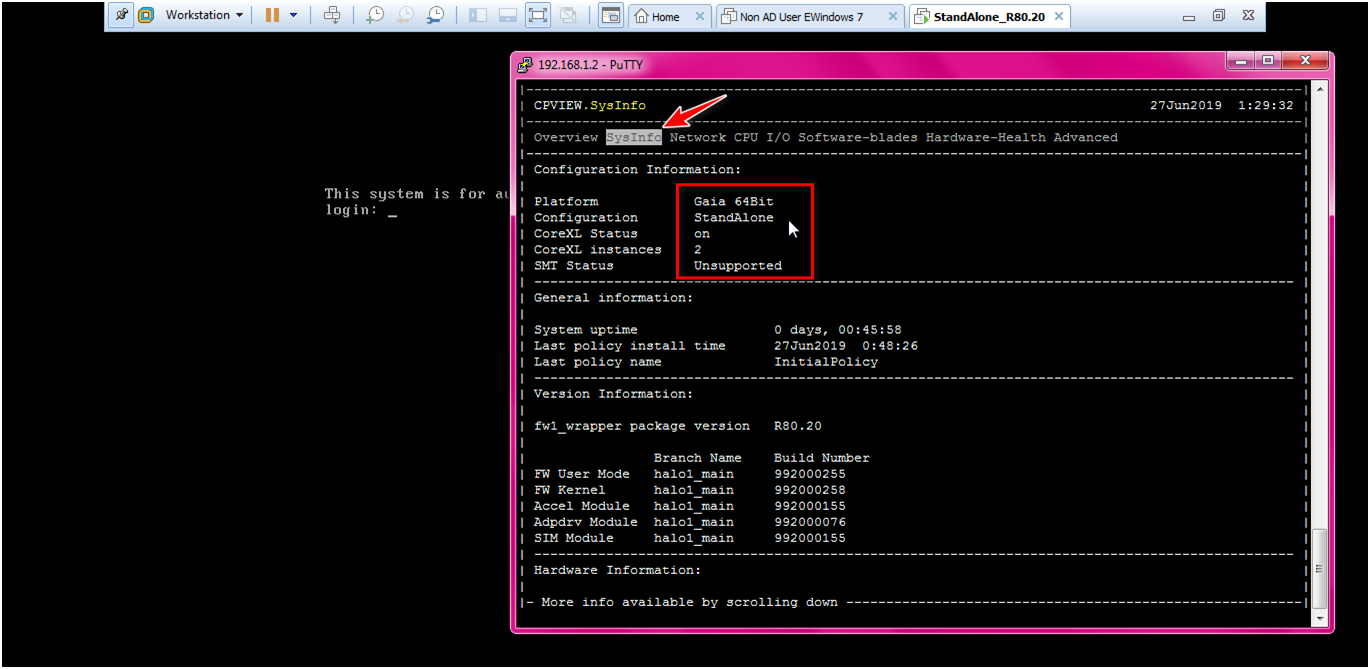
STEP: Check the interface by below command.
Command:
clish>set interface eth0 ipv4-address 192.168.1.2 mask-length 24
clish>set interface eth0 state on
clish>save config
clish>show configuration interface
Only show eth0 interface which is internal interface of CP gateway so we need to assign the IP address on the external interface so we assign the ip address for external interface which is eth1.
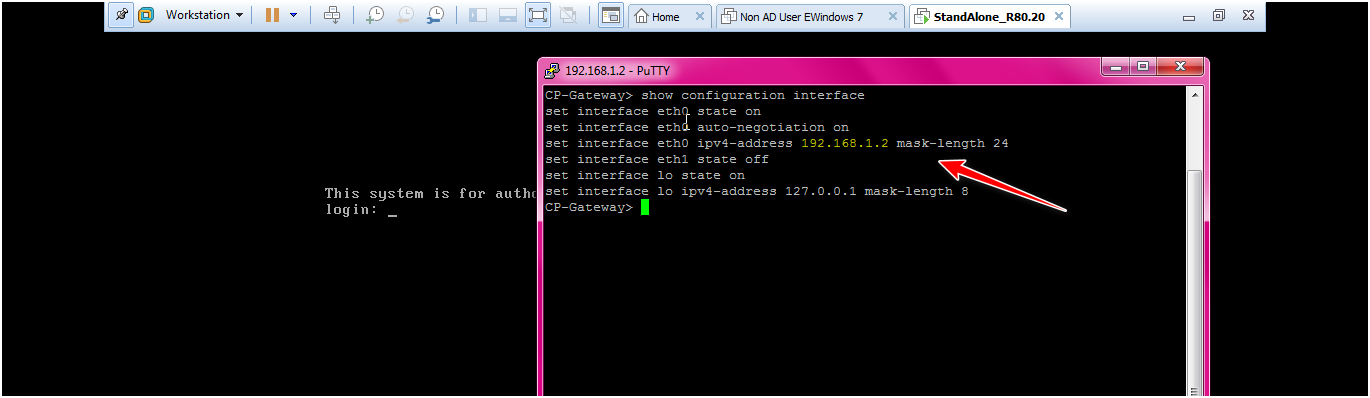
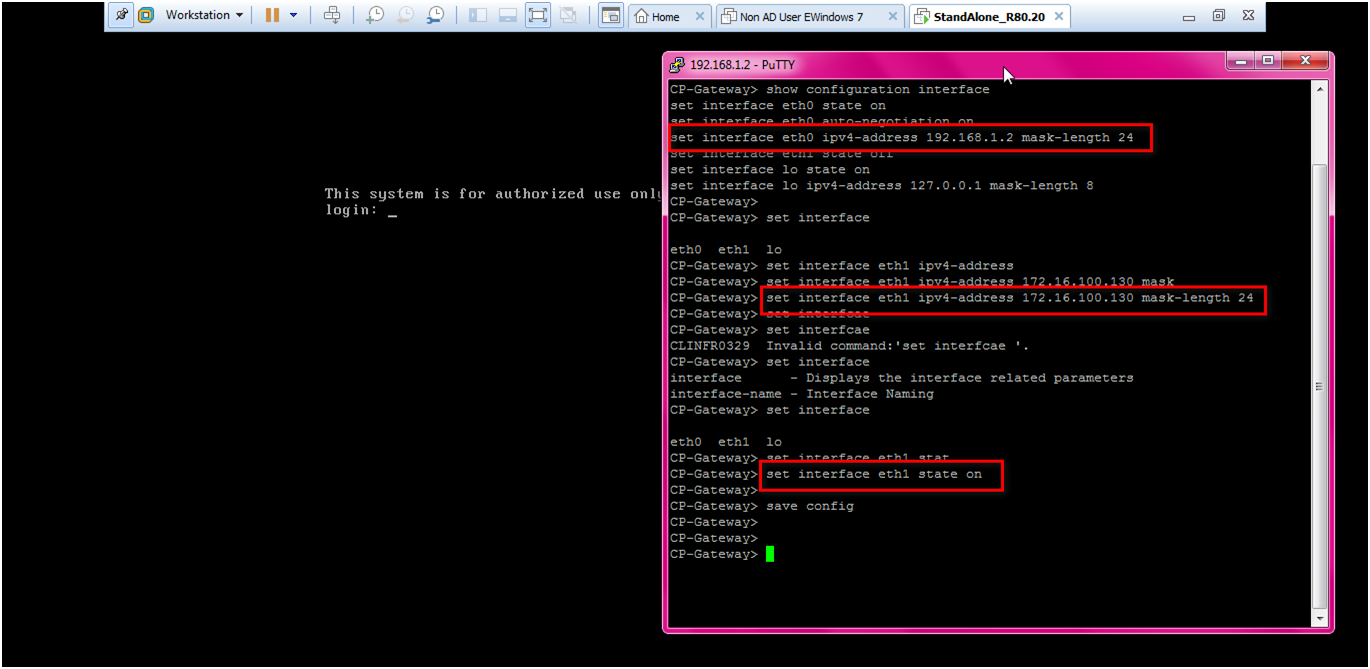
STEP: Add interface for eth1 by below command
Command:
clish>set interface eth1 ipv4-address 172.16.100.130 mask-length 24
command : clish>set interface eth1 state on
command : clish>save config
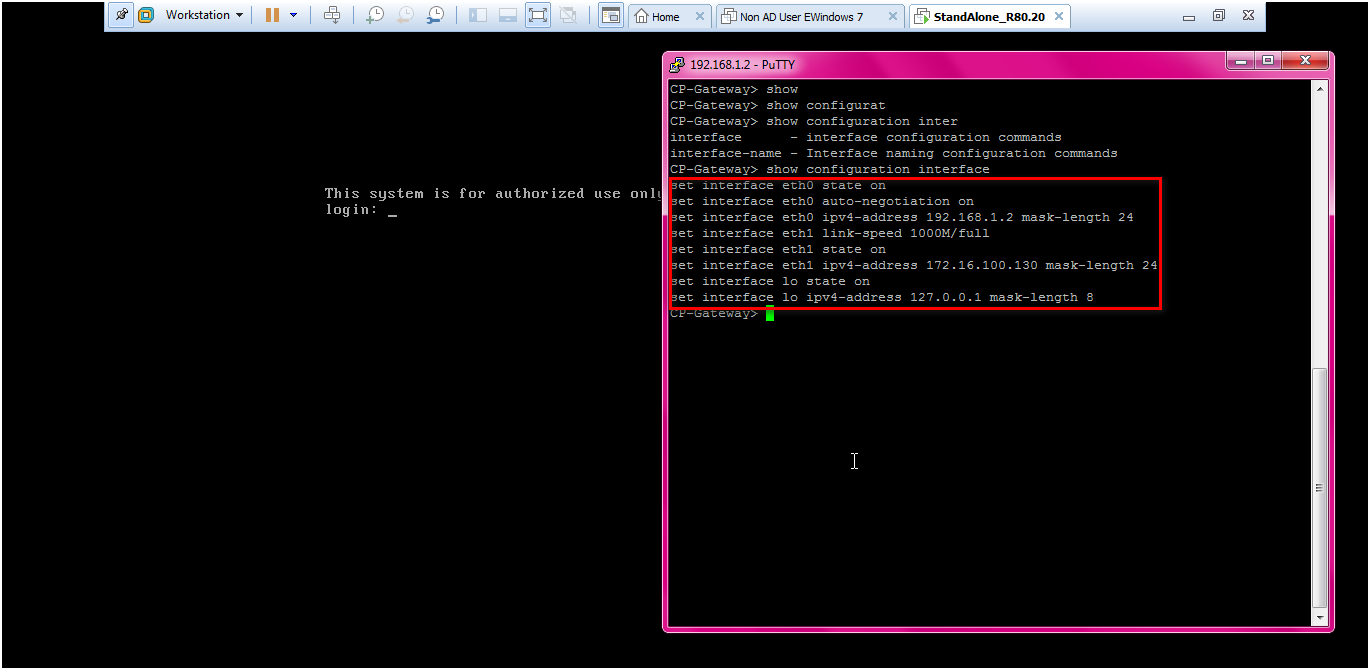
Check the below details via “show configuration interface” to re verify.
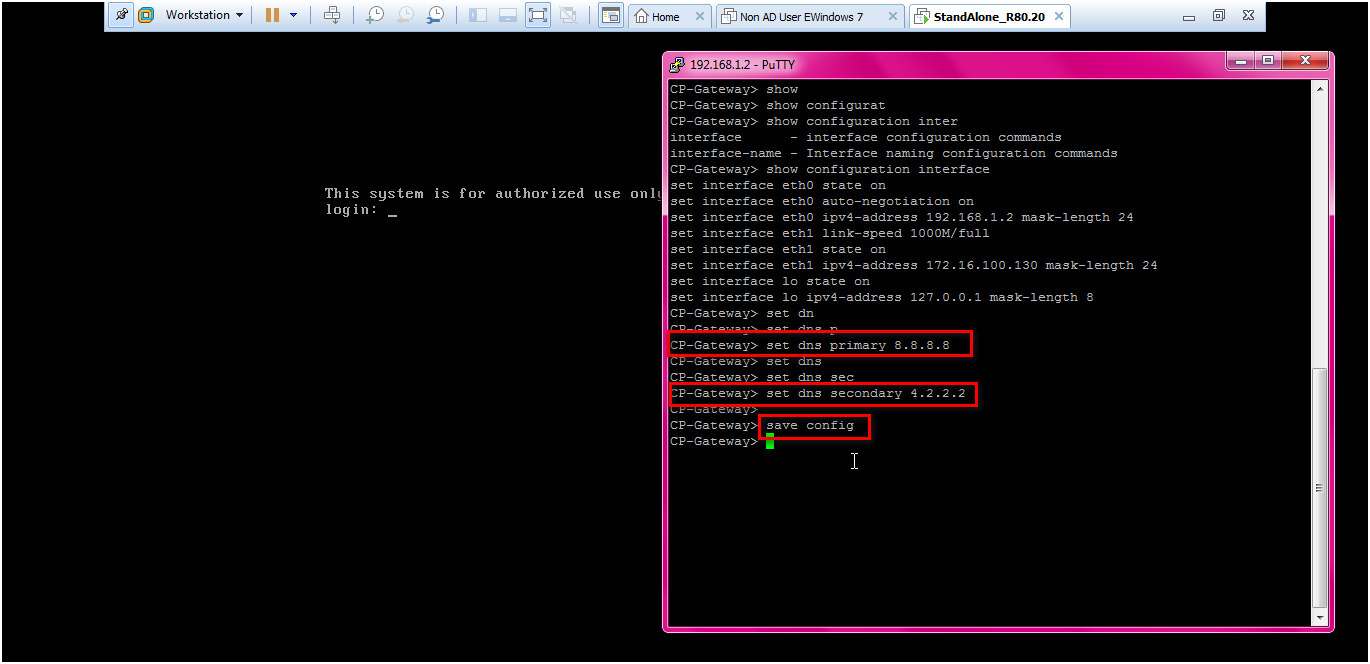
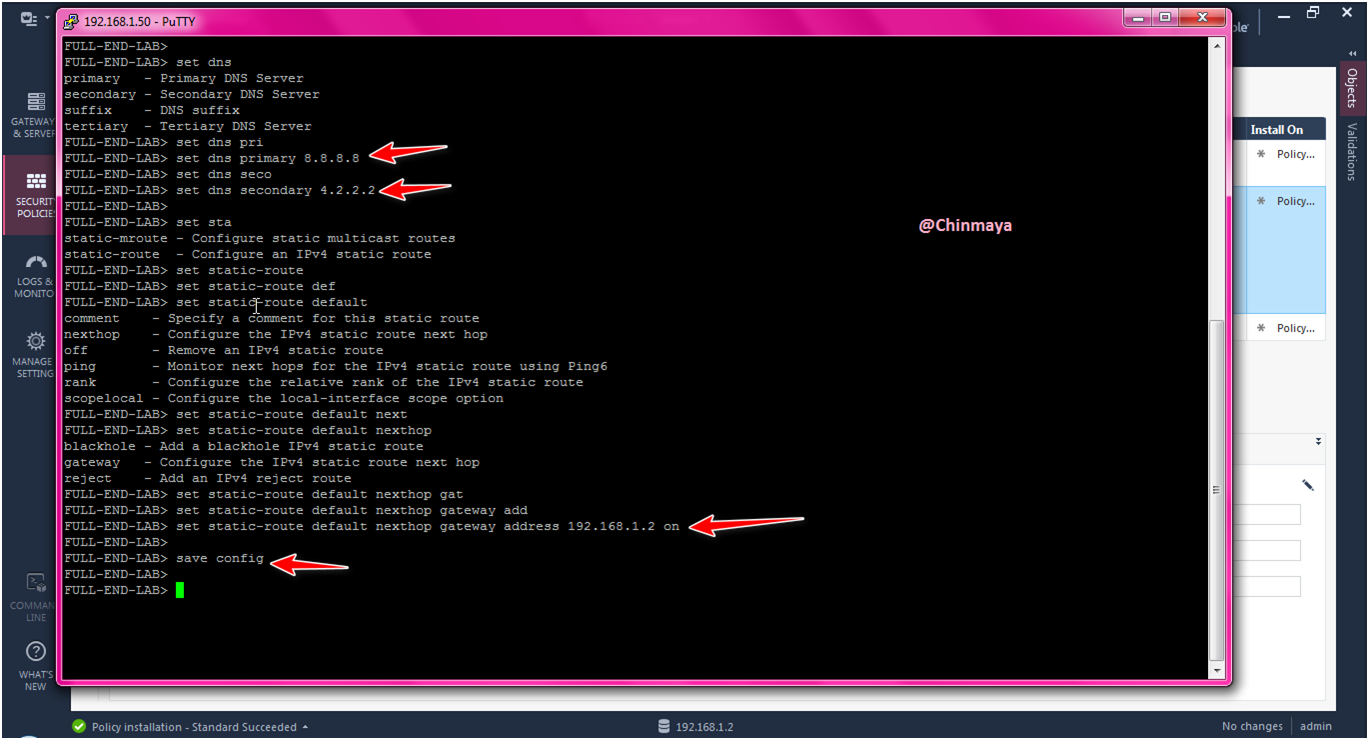
STEP : Set DNS address as 8.8.8.8 and 4.2.2.2
Command:
clish > set dns primary 8.8.8.8
clish > set dns secondary 4.2.2.2
clish > save config
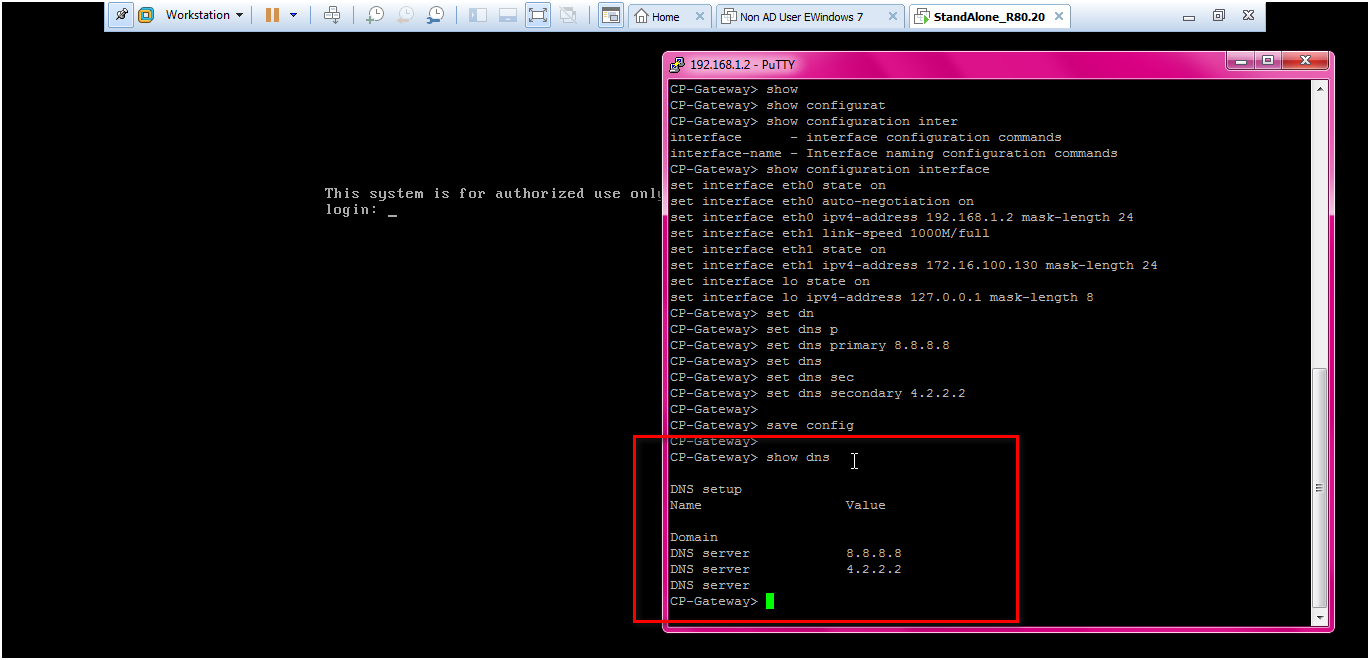
STEP: Check the DNS IP by below command.
command: clish > show dns
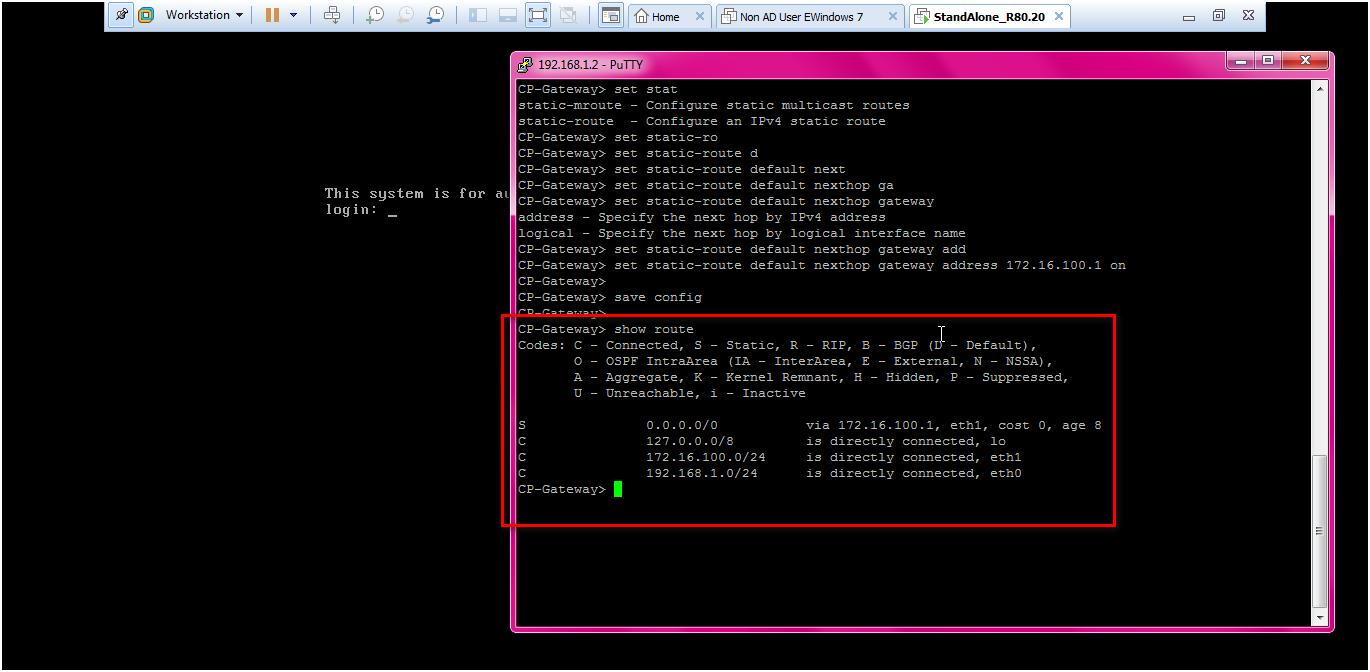
STEP : Add a default gateway for CP Standalone.
Command:
clish > set static-route default nexthop gateway address 172.16.100.1 on
clish >save config
Check the route by below command.
command : clish > show route
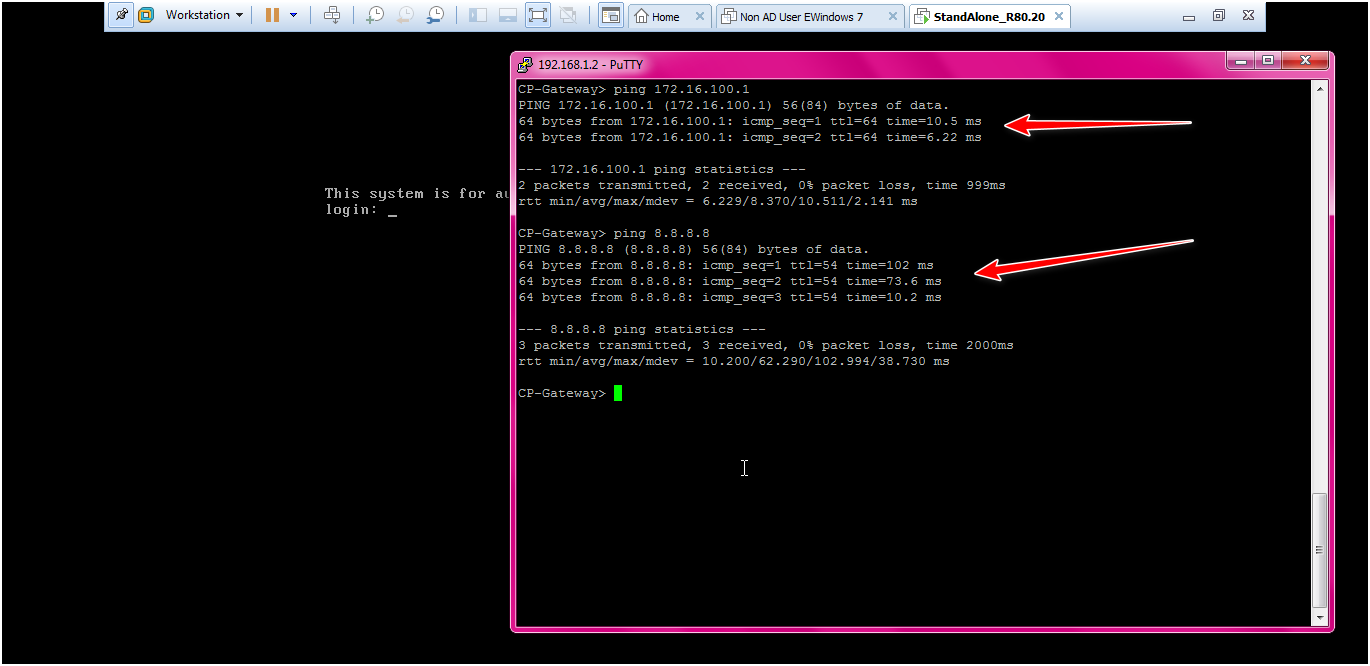
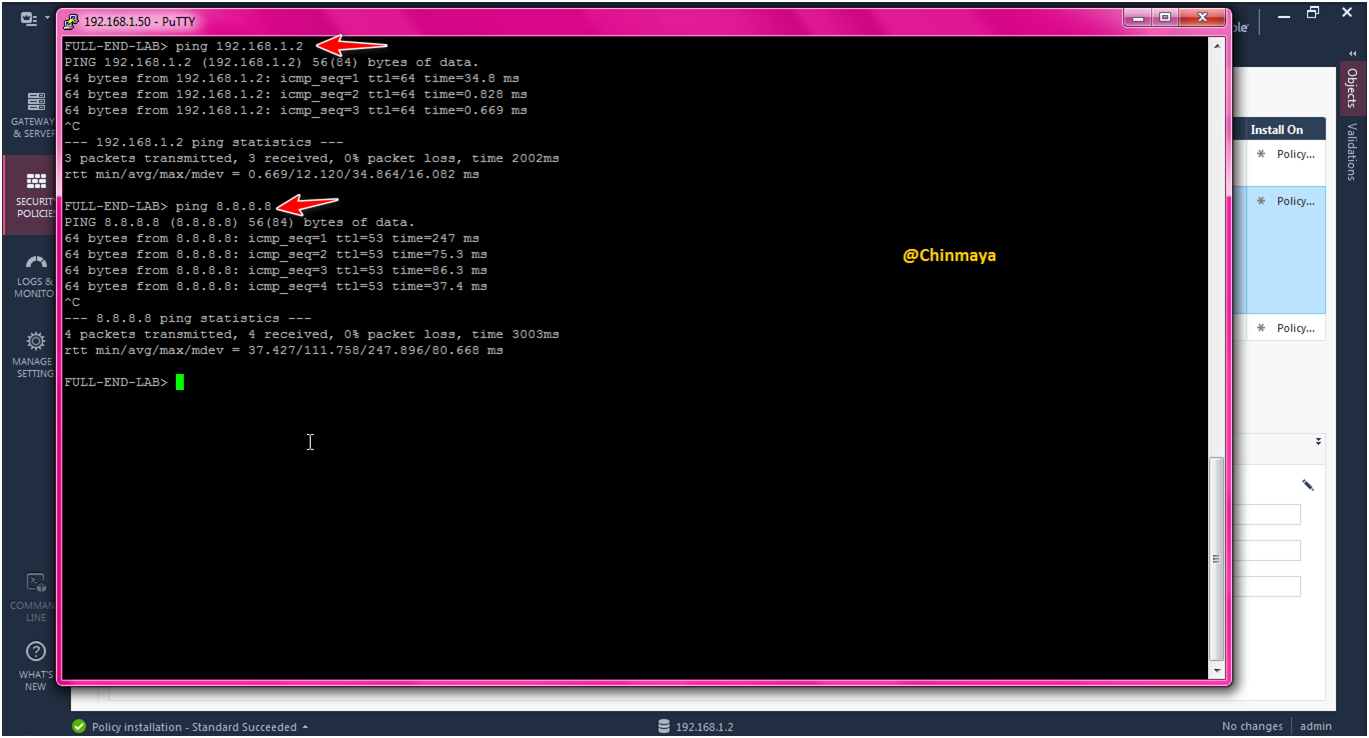
STEP: Check the connectivity from gateway able to access gateway and internet or not.
Command:
clish> ping 172.16.100.1
clish> ping 8.8.8.8
STEP: Set expert password.
command : clish > set expert-password
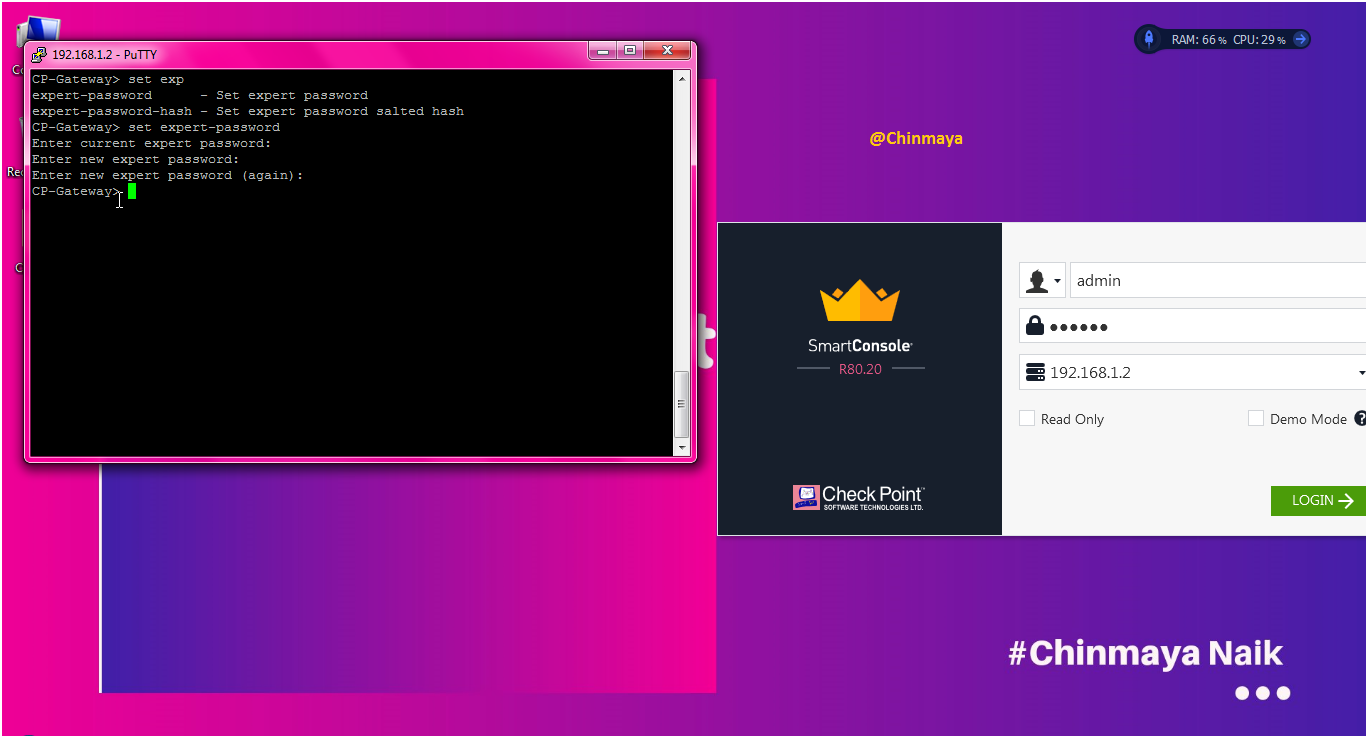
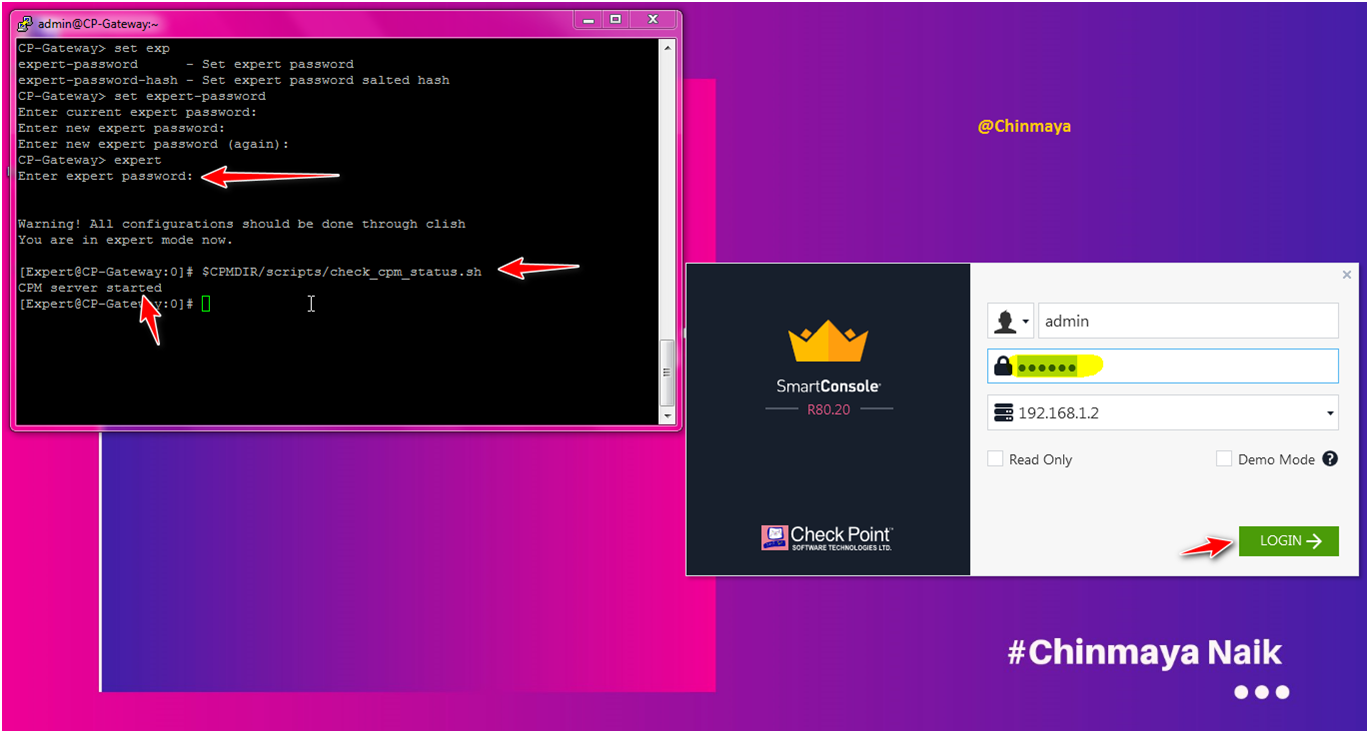
STEP: Run the below command to start the CPM services if you unable to open the smartconsle.
Command:
[expert]#$FWDIR/scripts/check_cpm_status.sh (message show : CPM server started)
command : [Expert]#api status (wait until CPM is not started)
Then login the Smart Console with give the credentials.
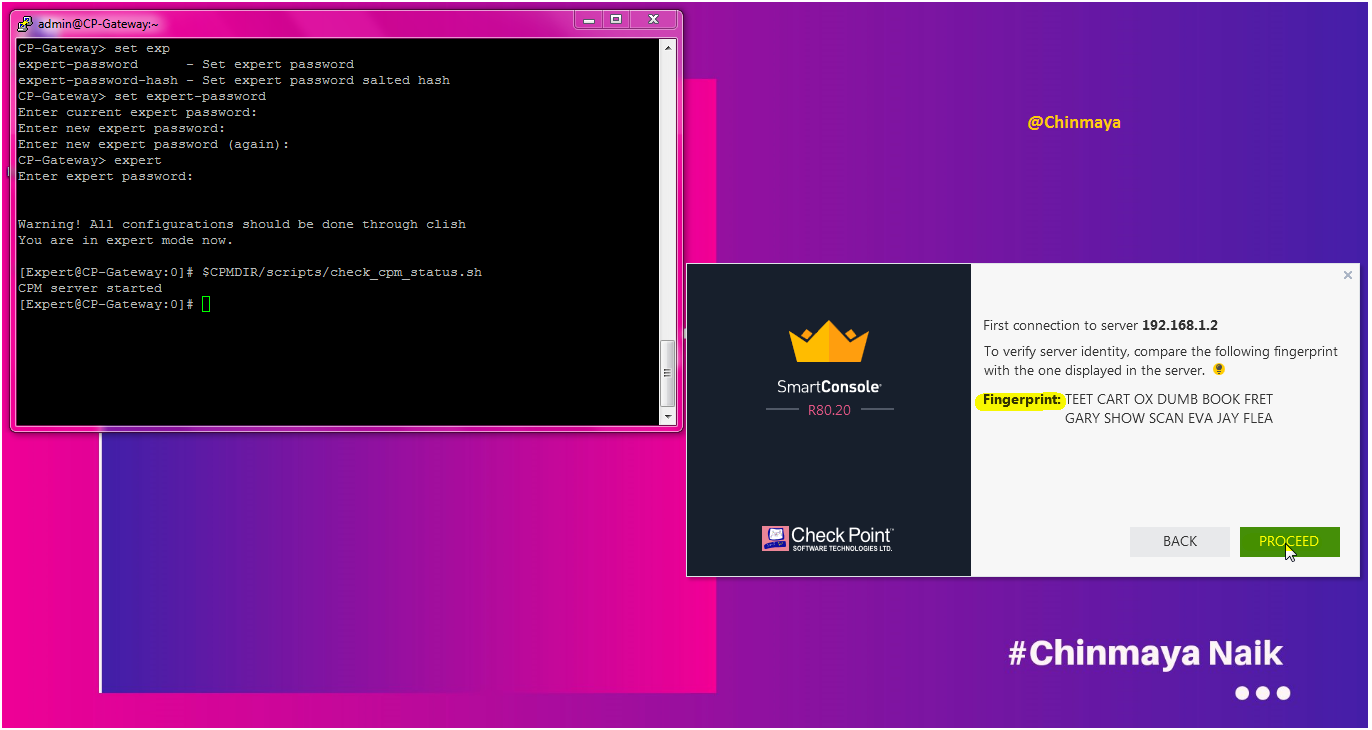
STEP: Check the General properties for configuration like IP, Host , Hardware details.
NOTE : Our requirement is to access the internet to the internal host so “Firewall” blade is enough.
STEP: Fetch the topology.
Location : SmartConsole --> Gateway ---> General Properties ---> Network Management ---> Get interface with Topology
STEP : Click “Yes”.
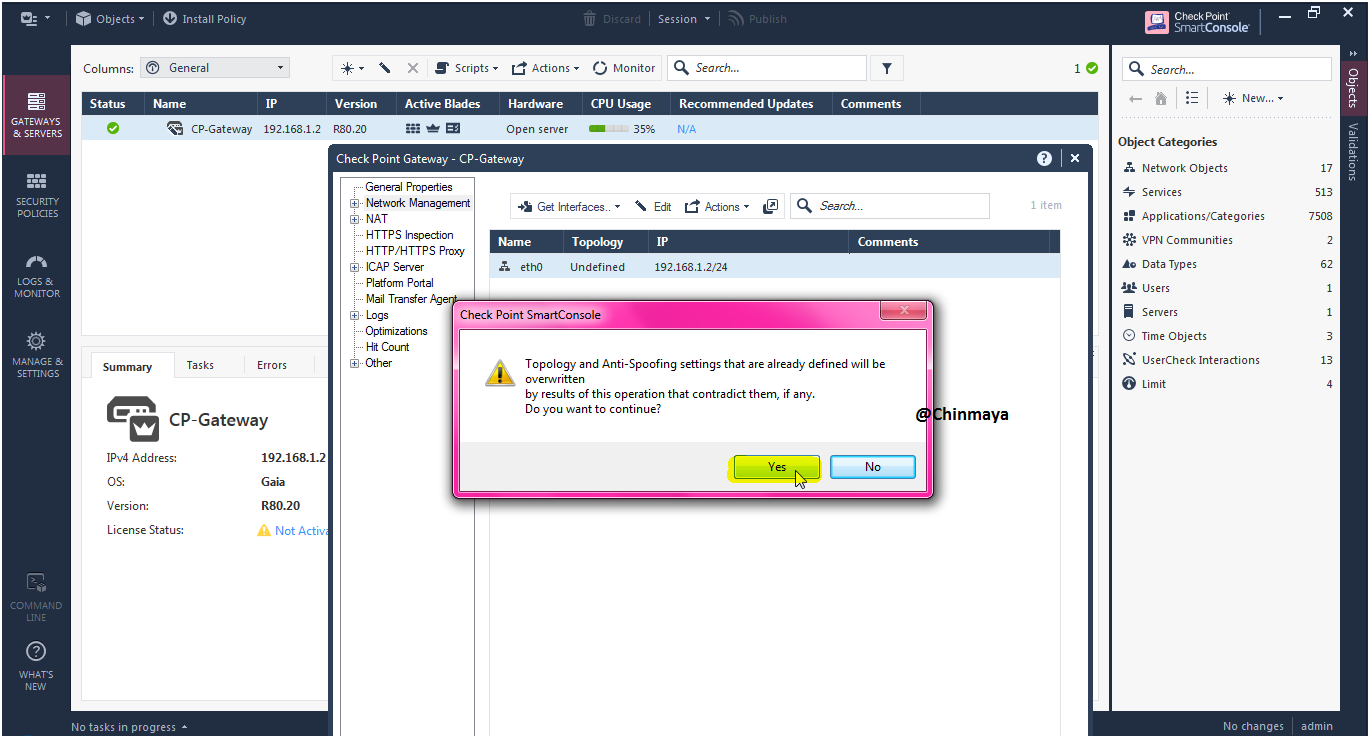
STEP : Click the “Accept” so basically its fetch the all connected interface.
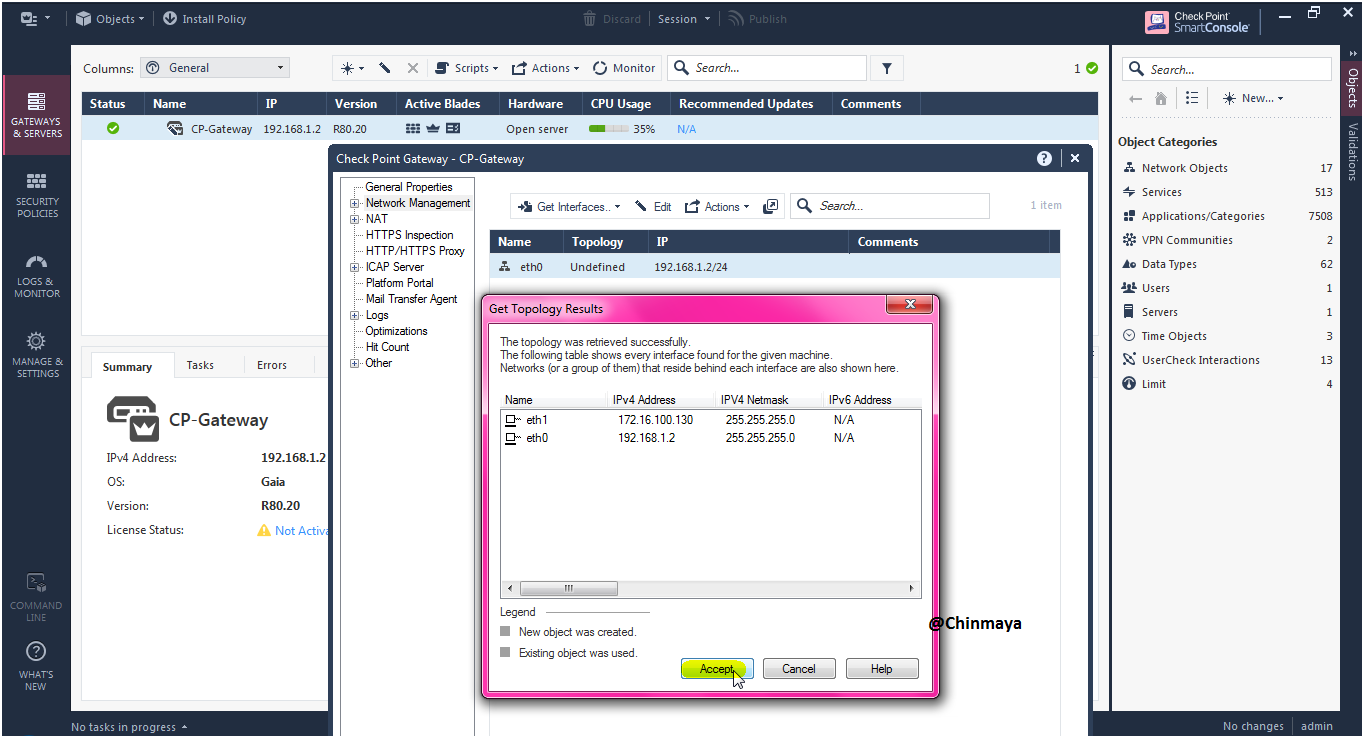
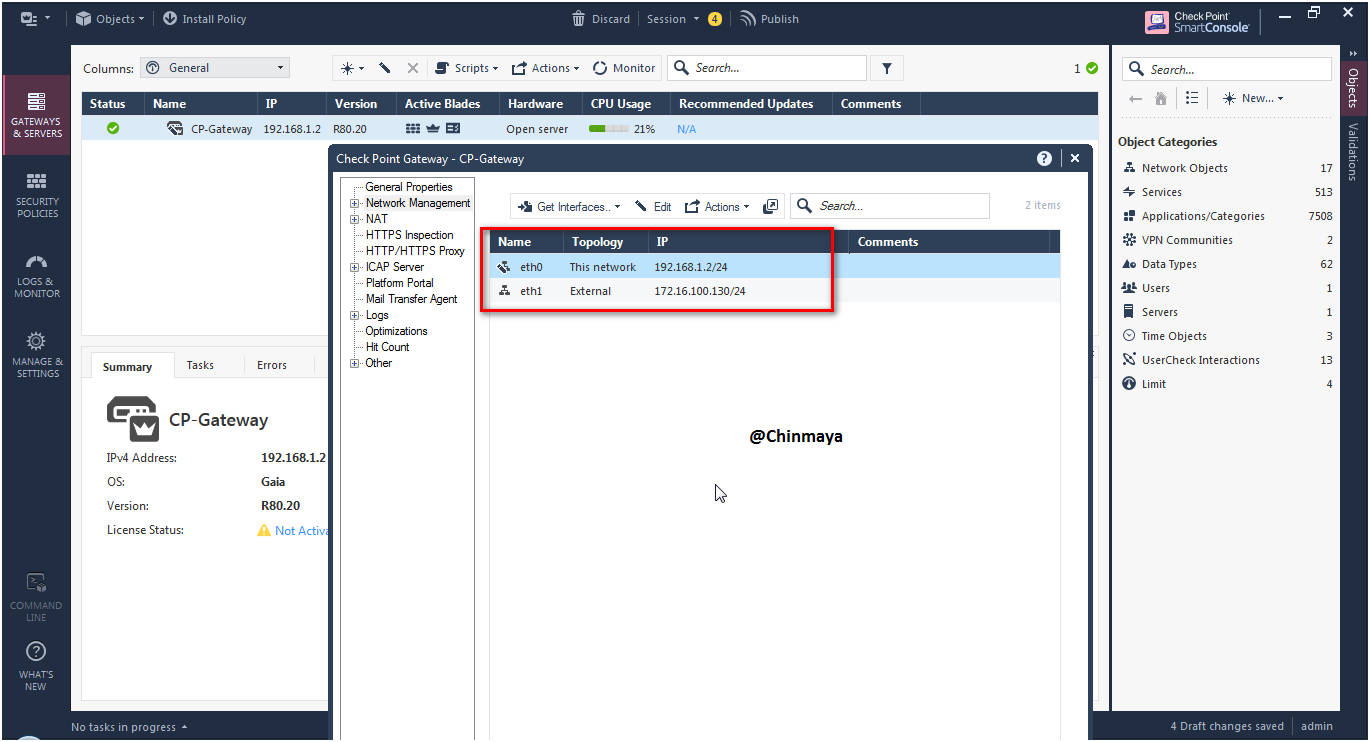
STEP: Verify the interface like both internal or external , if not then double click the interface and define as internal or external.
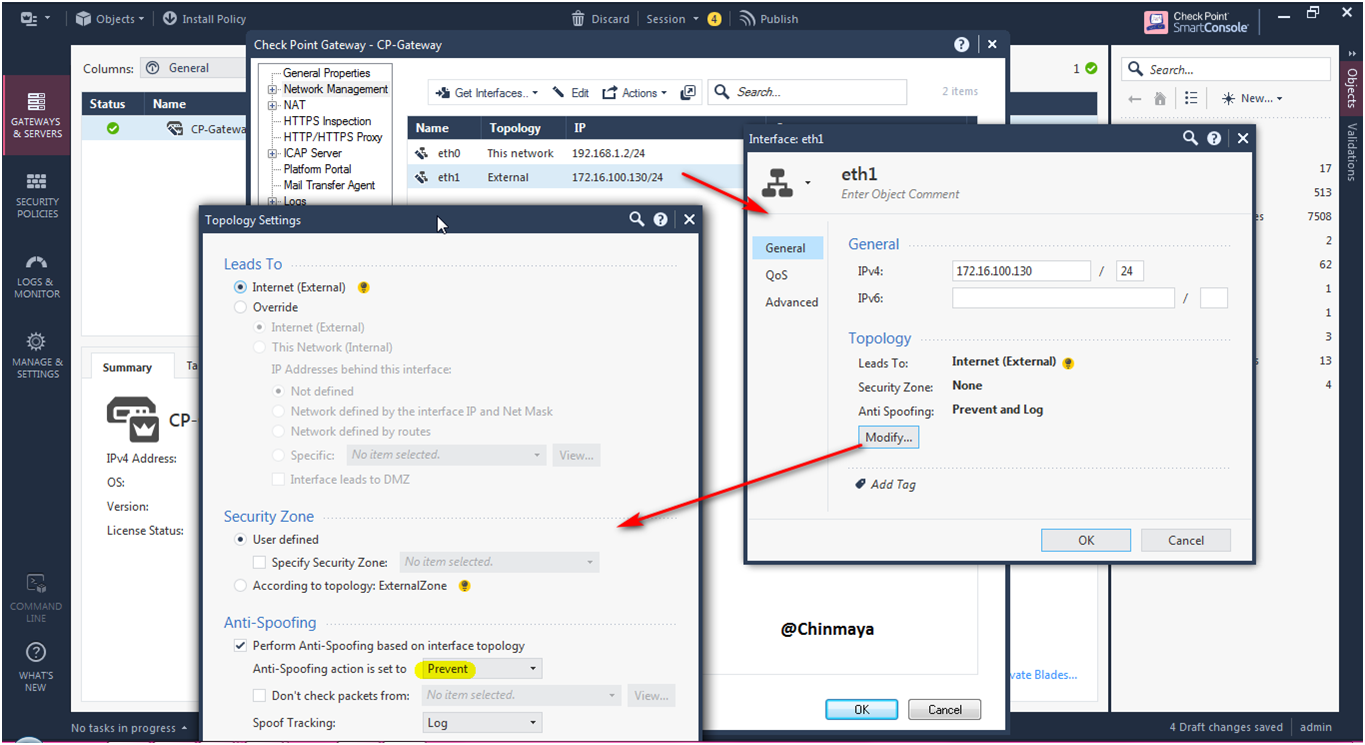
STEP: Check the Anti-Spoofing configuration by double click the interface.
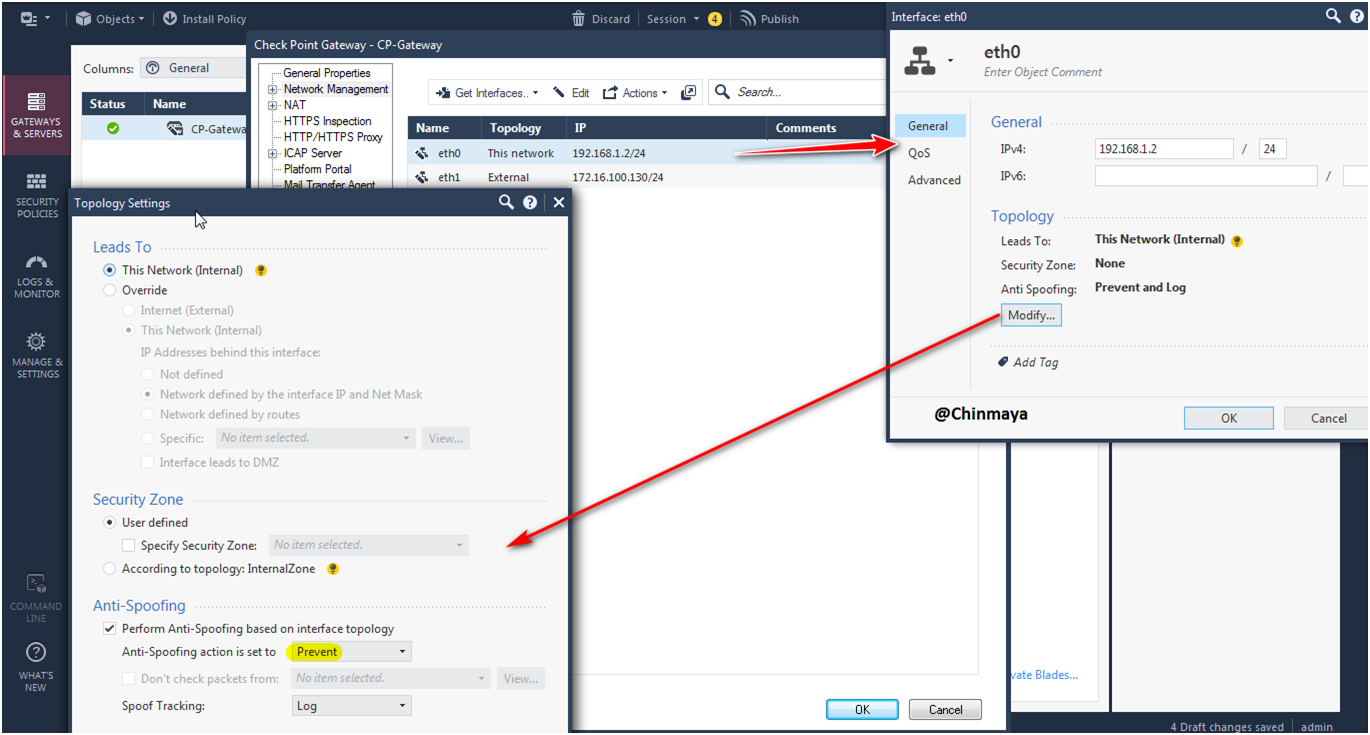
STEP: Click “Ok”.
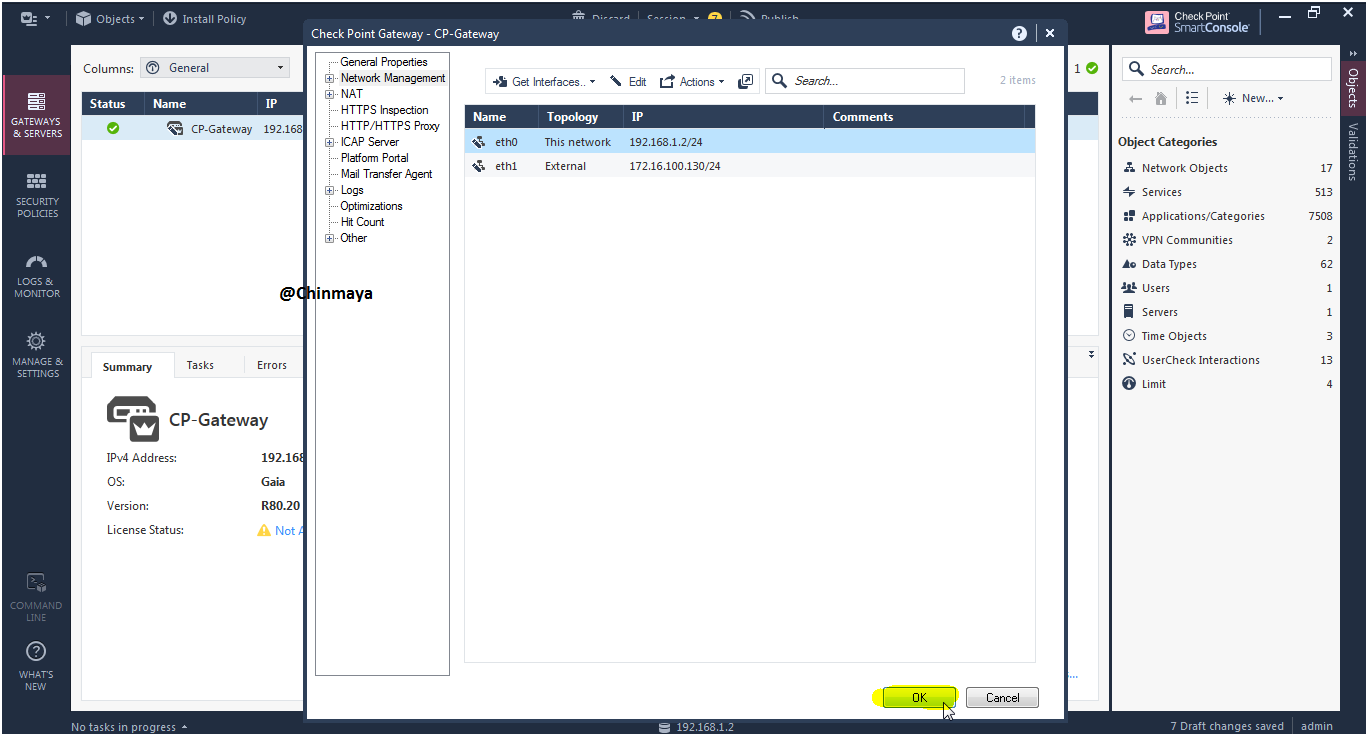
STEP: Create a host object for Windows 7 Host machine to create a rule and give the internet access.
SmartConsole ---> New ---> More ---> Network Object ---> Host

STEP : Assign the name to the Host Object
Name : Test_Host_Machine IP Address: 192.168.1.101 (/24)
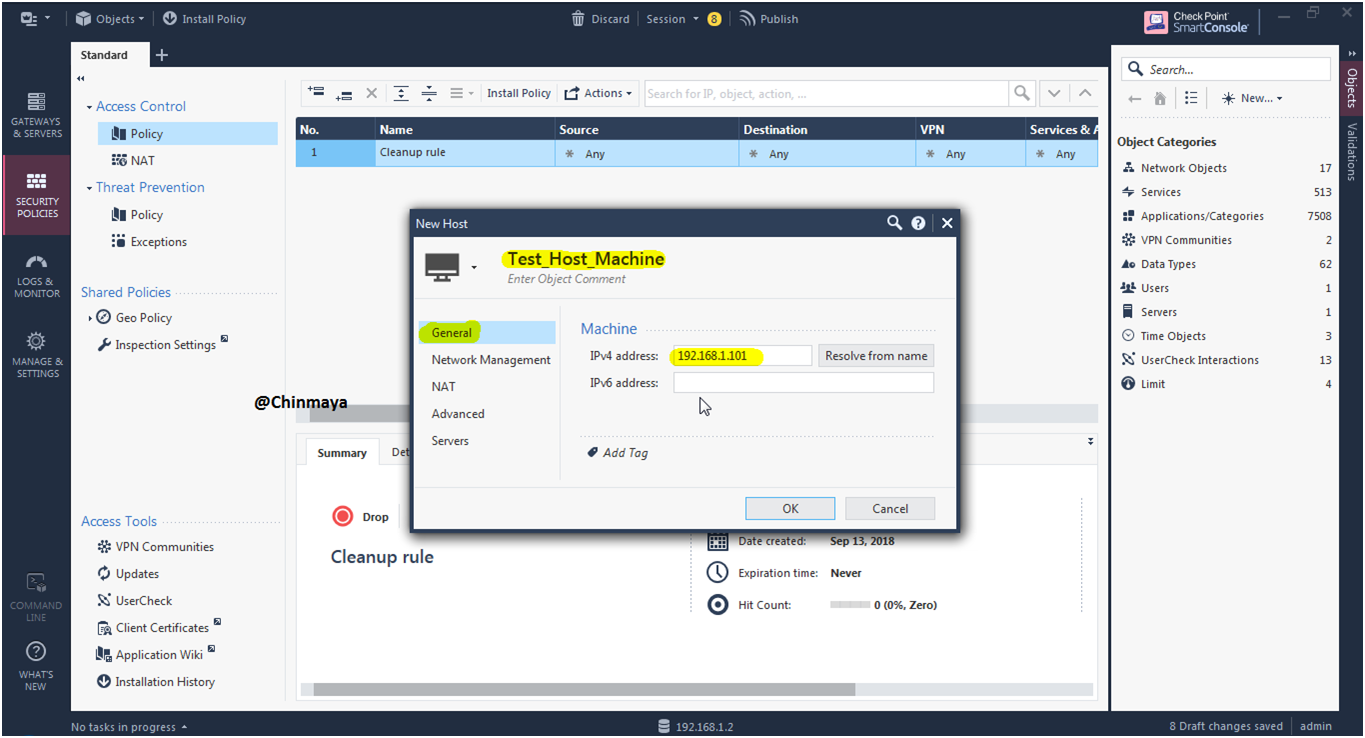
STEP: On NAT section Mark “Add automatic address translation rule” and Click “Next”.

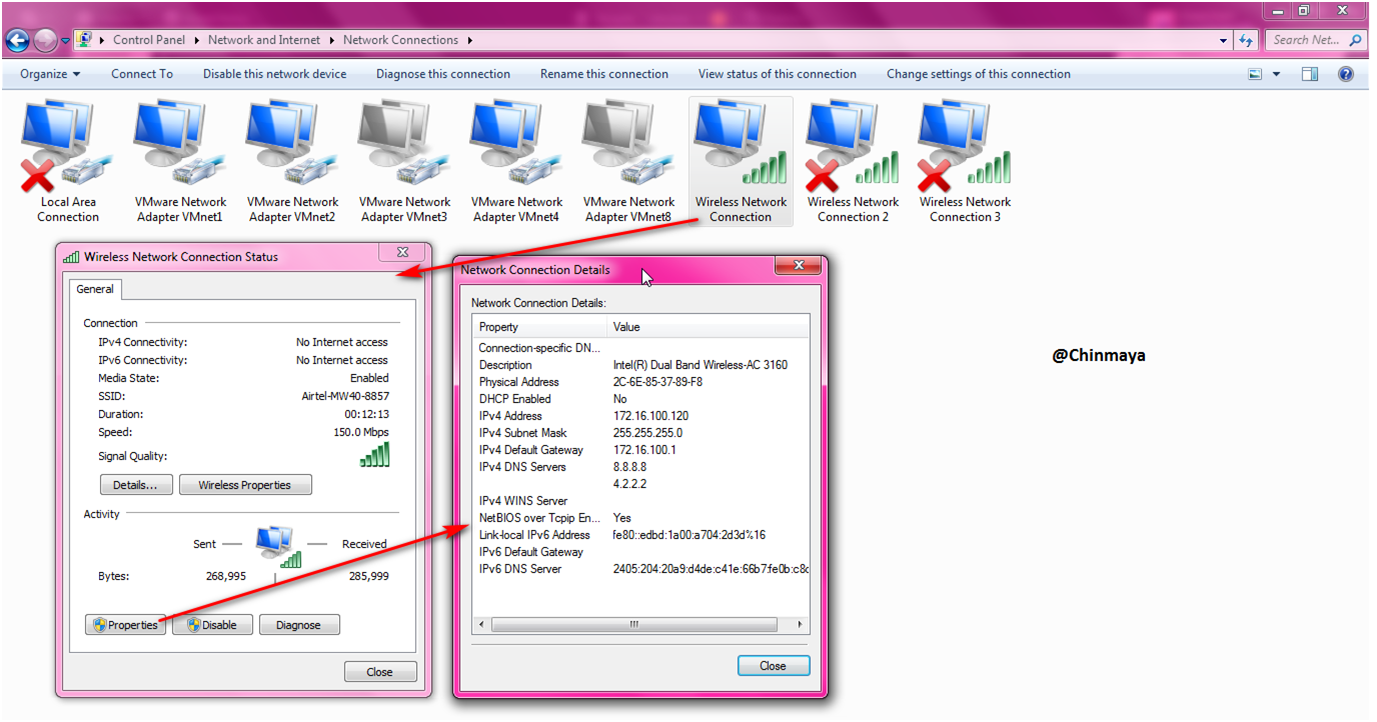
STEP: Check the Host machine where the VM is running like my physical machine IP address.
Location: Control Panel > Network and Internet > Network Conections My IP is "172.16.100.120".
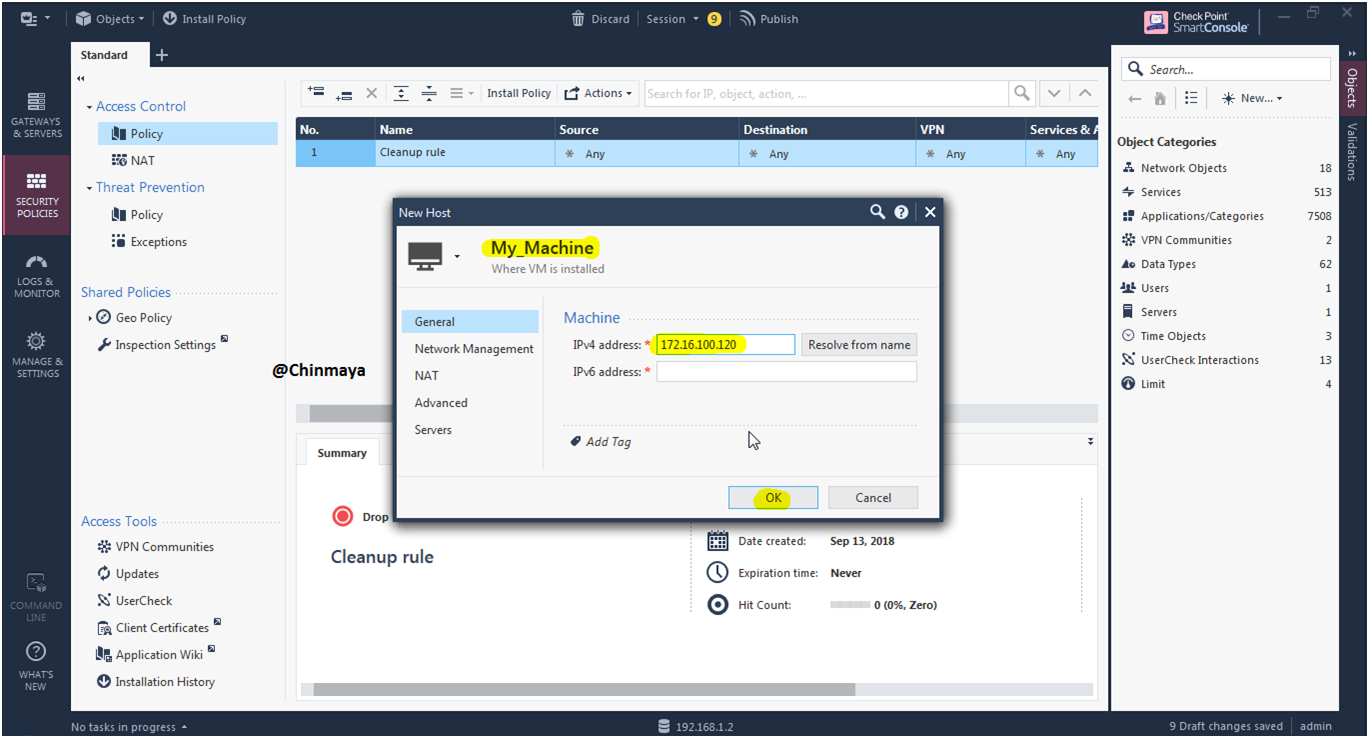
STEP: Create Host for my physical IP address.
Name : My_Machine IP:172.16.100.120 (/24)
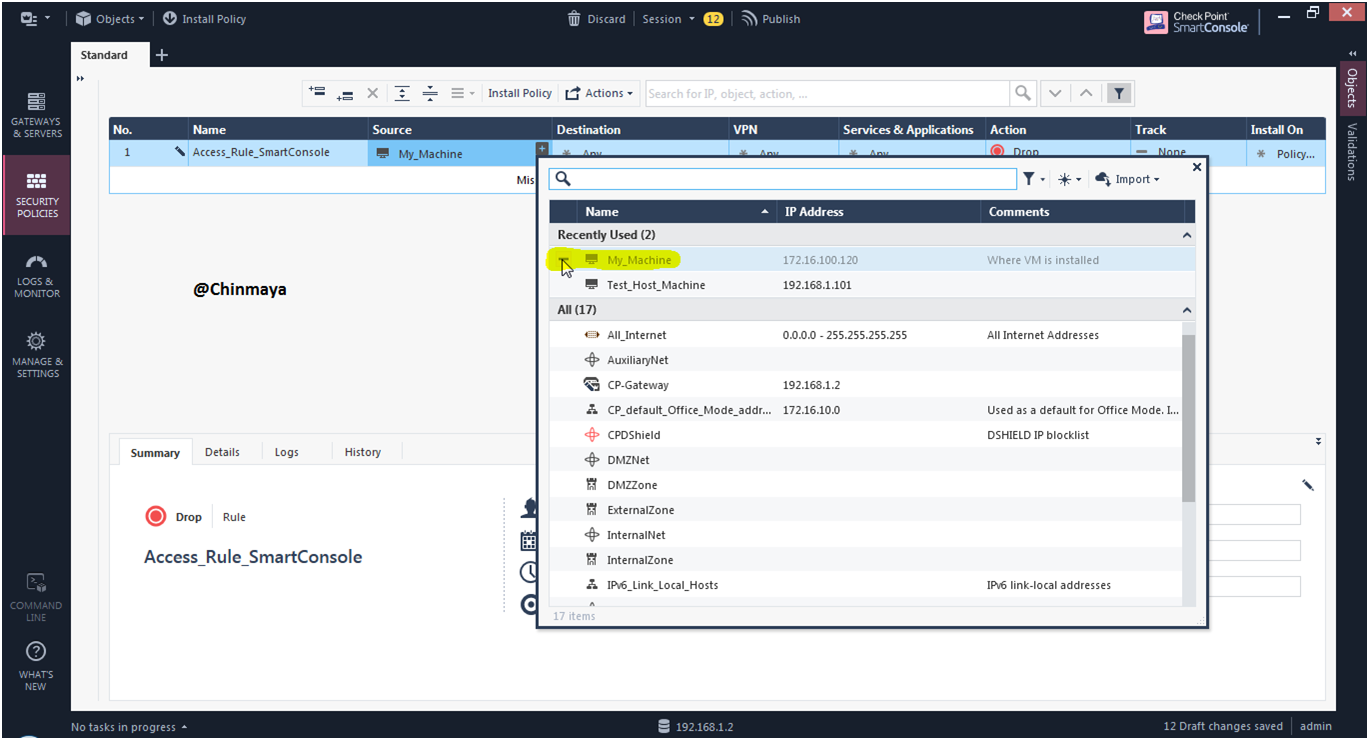
STEP: Refer the below policy. First to access the gateway, SmartConsole and second one give the internet access to the Test Host machine with allow the services http, https.

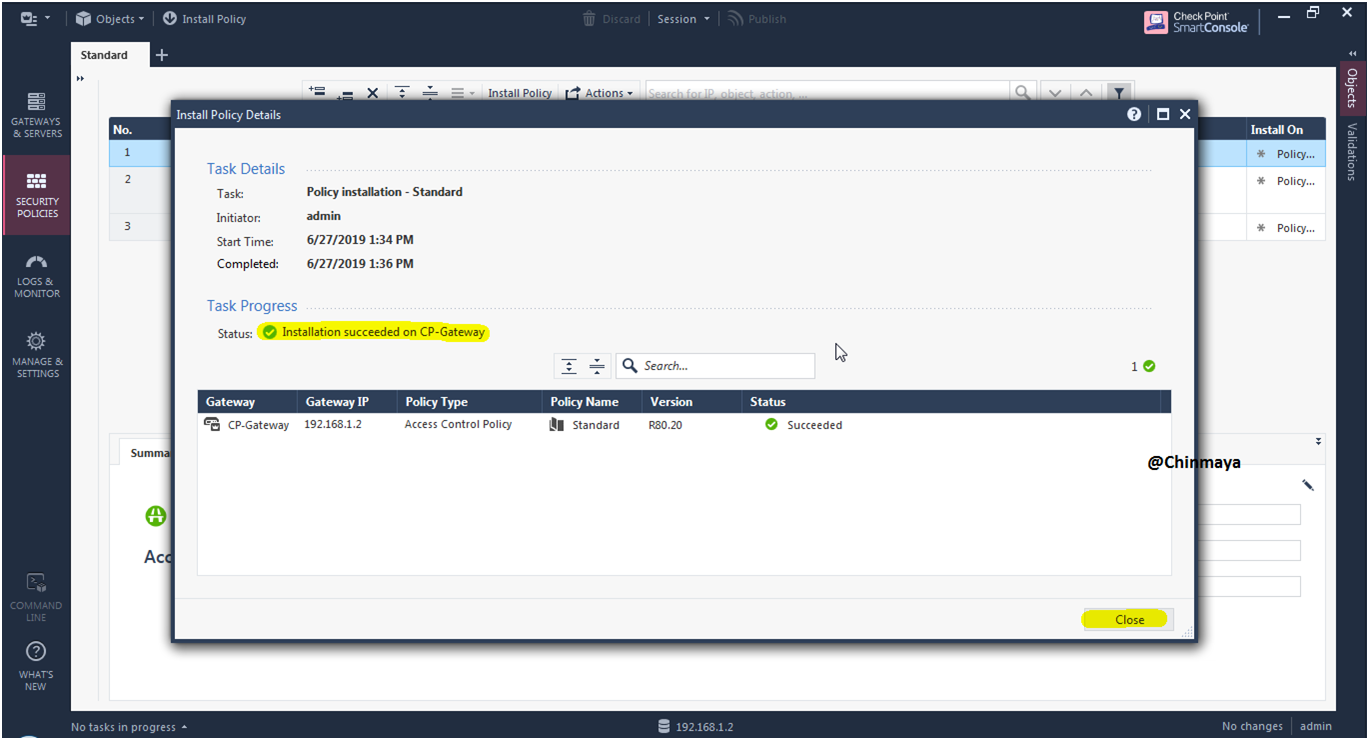
STEP: Install the Policy.

NOTE : Its mandatory to install the prerequisite package before install the Endpoint Client so without the below install package we cannot install the Endpoint client and its only relevant if you have WINDOWS7 OS.
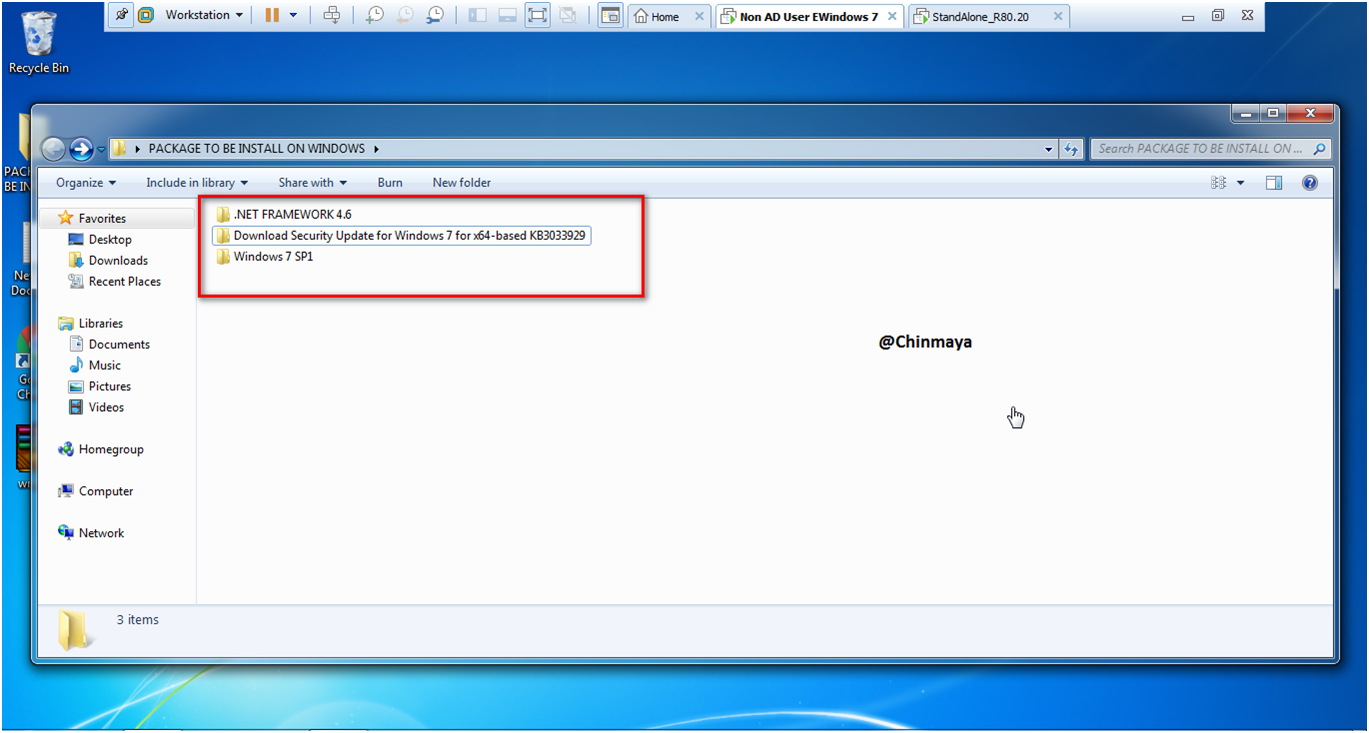
Hope you download the windows 7 pre-requisite package and install.
Let’s Start to install the Endpoint Client.
We need to transfer the Laptop package from Physical Machine to the VM host machine (windows 7 test machine).
NOTE: Make sure you already install the VMware installation tool because we need to transfer client package to the Windows 7 machine.
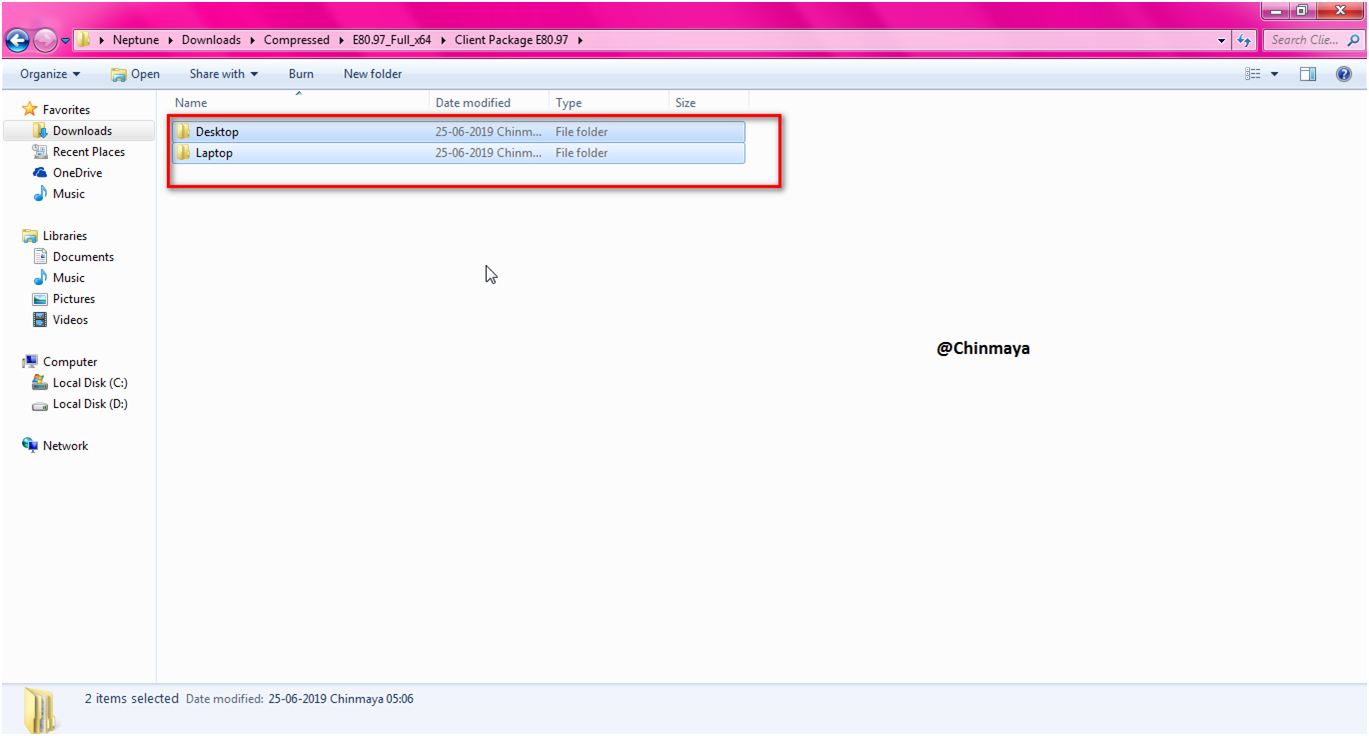
Coping to the VM windows 7 host machine.
After copy from the physical machine then Transfer that EPS folder to the “C drive” for installation.
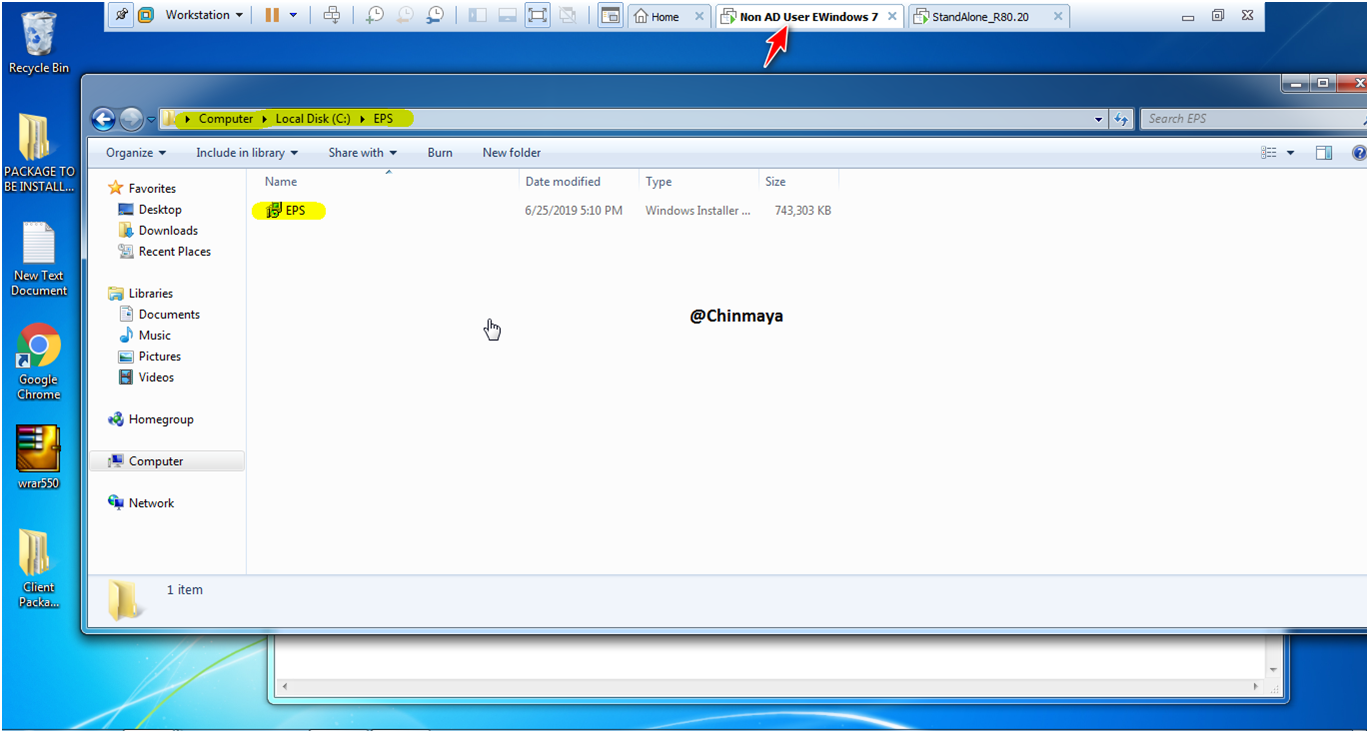
STEP: Go to the “C Director”
command : cd c:\ c:>dir (To check the folder EPS)

STEP: Go to EPS directory.
c:\>cd EPS
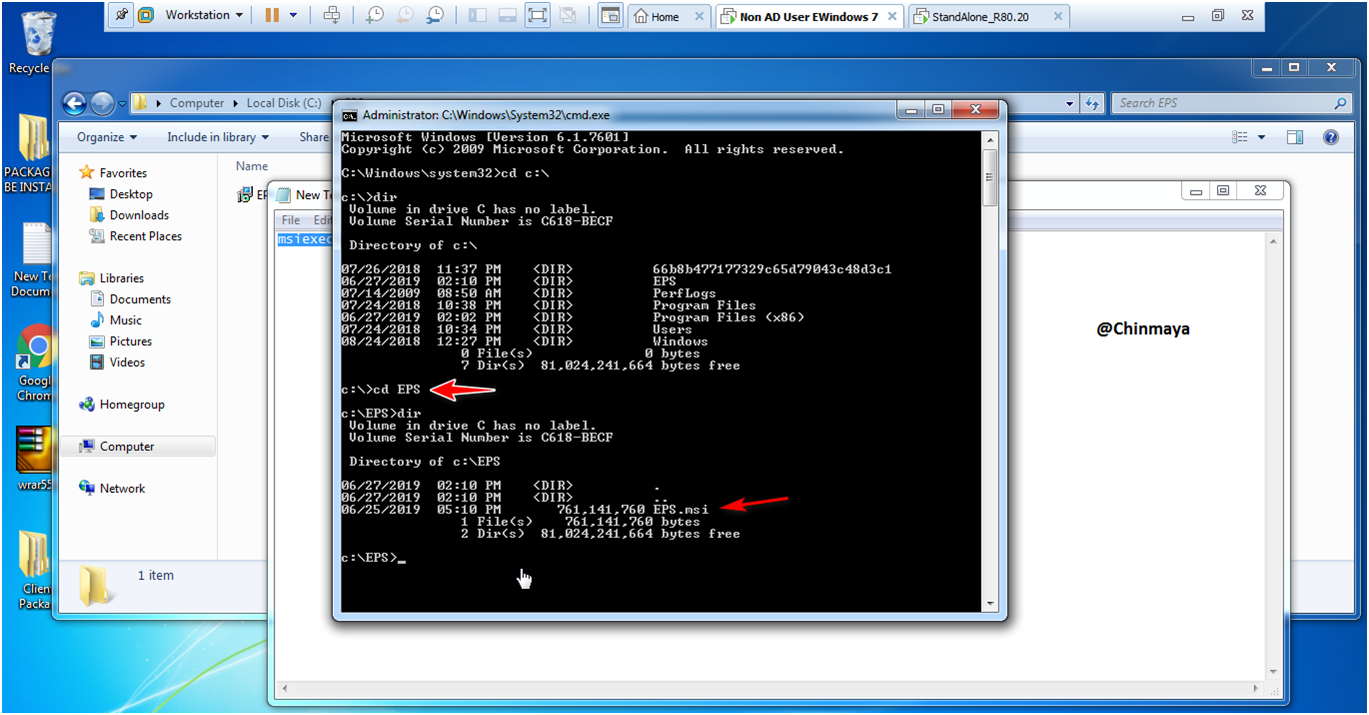
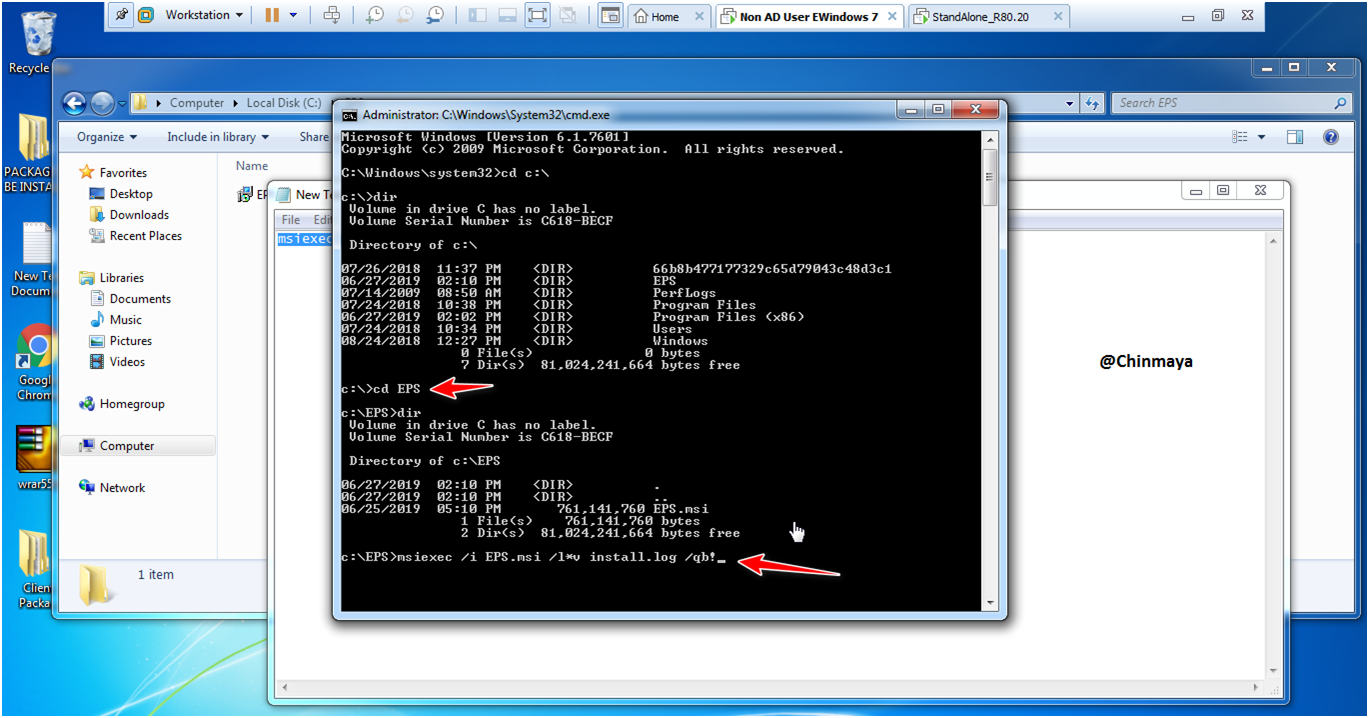
STEP: Run the below command to install the EPS package.
c:\EPS>msiexec /i EPS.msi /l*v install.log /qb!
So basically this command is help to generate the logs in case if you fail to install the client so we need to further investigate the issue.
If this command give you some popup then put ” c:\EPS>msiexec /i EPS.msi “
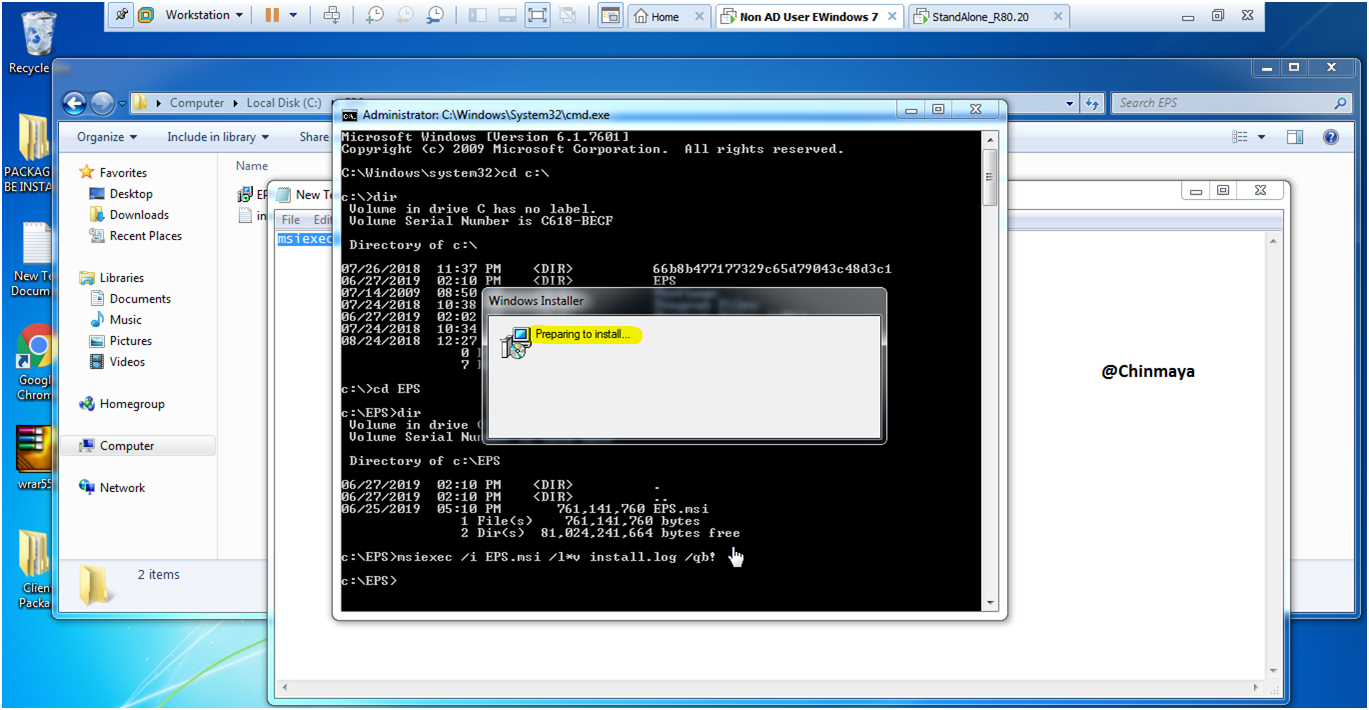
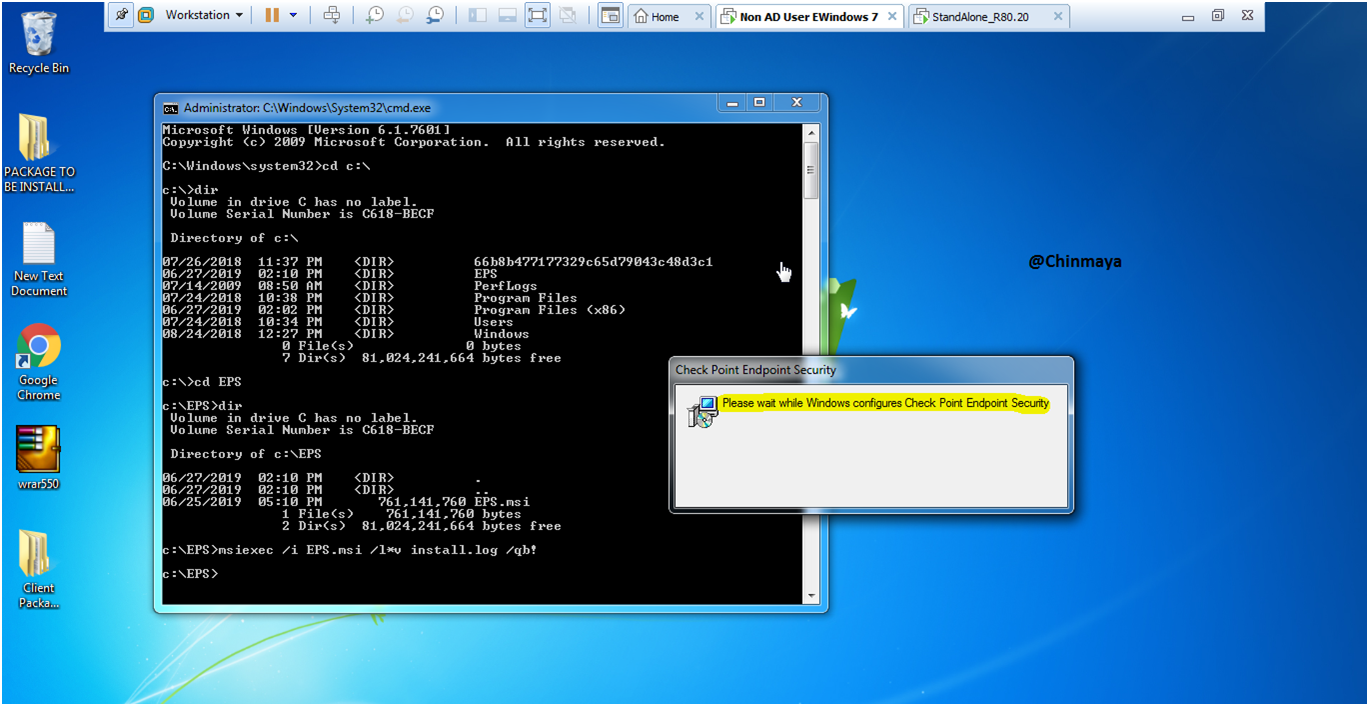
See on below checkpoint logo with showing “Installing Endpoint Security”.
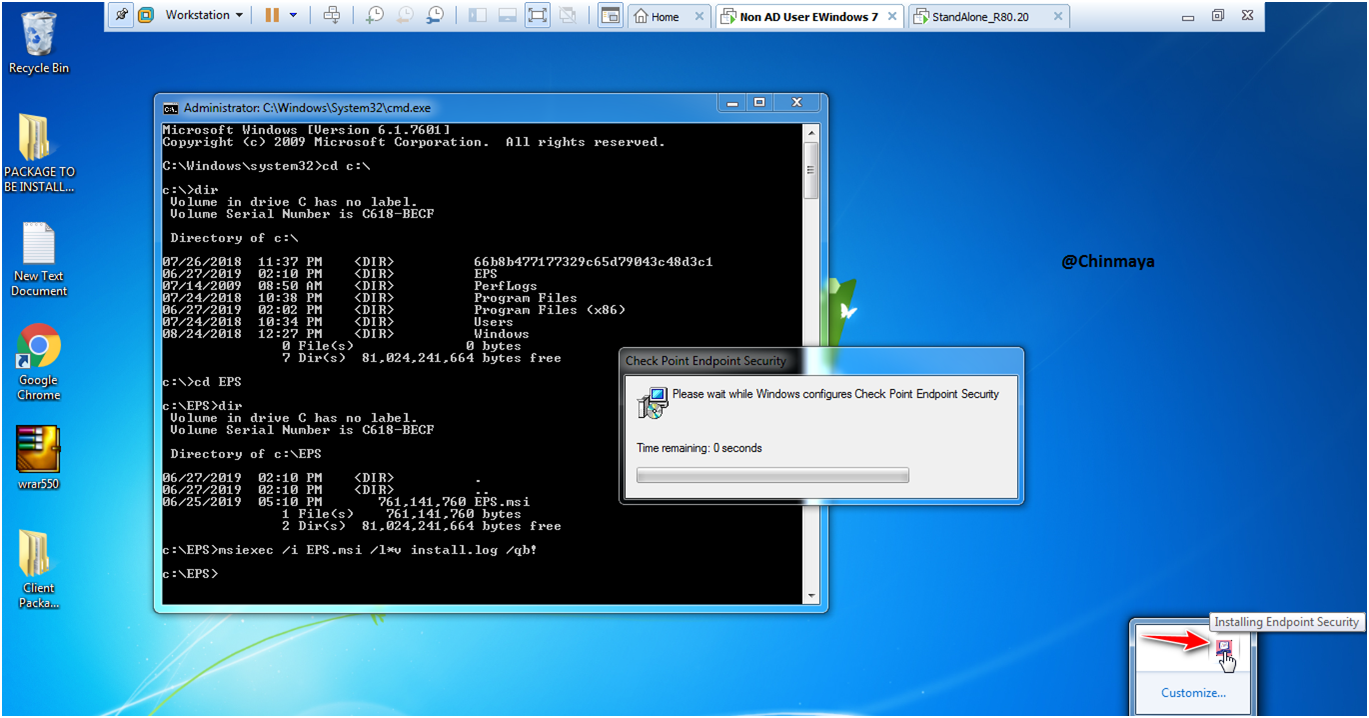
STEP: Click “Yes” to reboot the Machine.

STEP: Wait some time show the below Endpoint Agent icon then click the icon for more details.
NOTE : It take some time so wait some time.
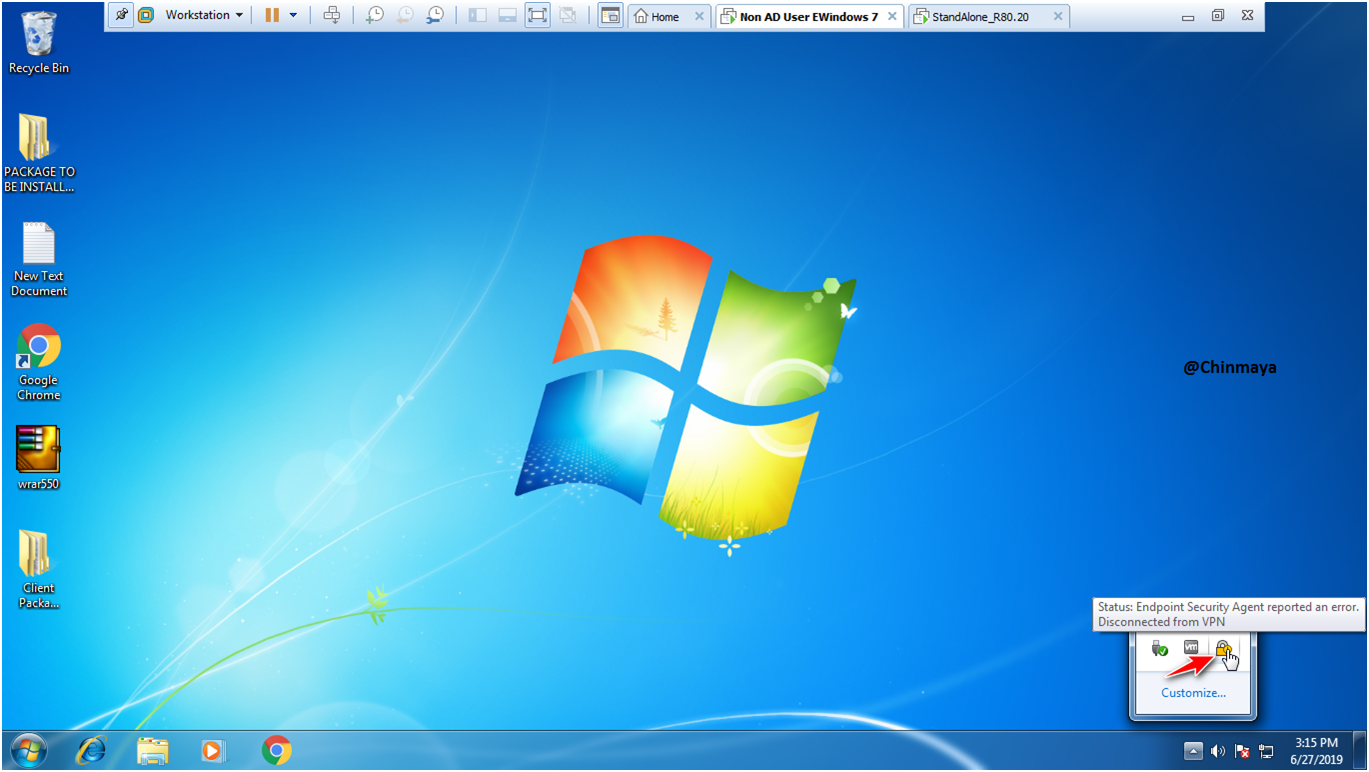
STEP: So on below we can see that
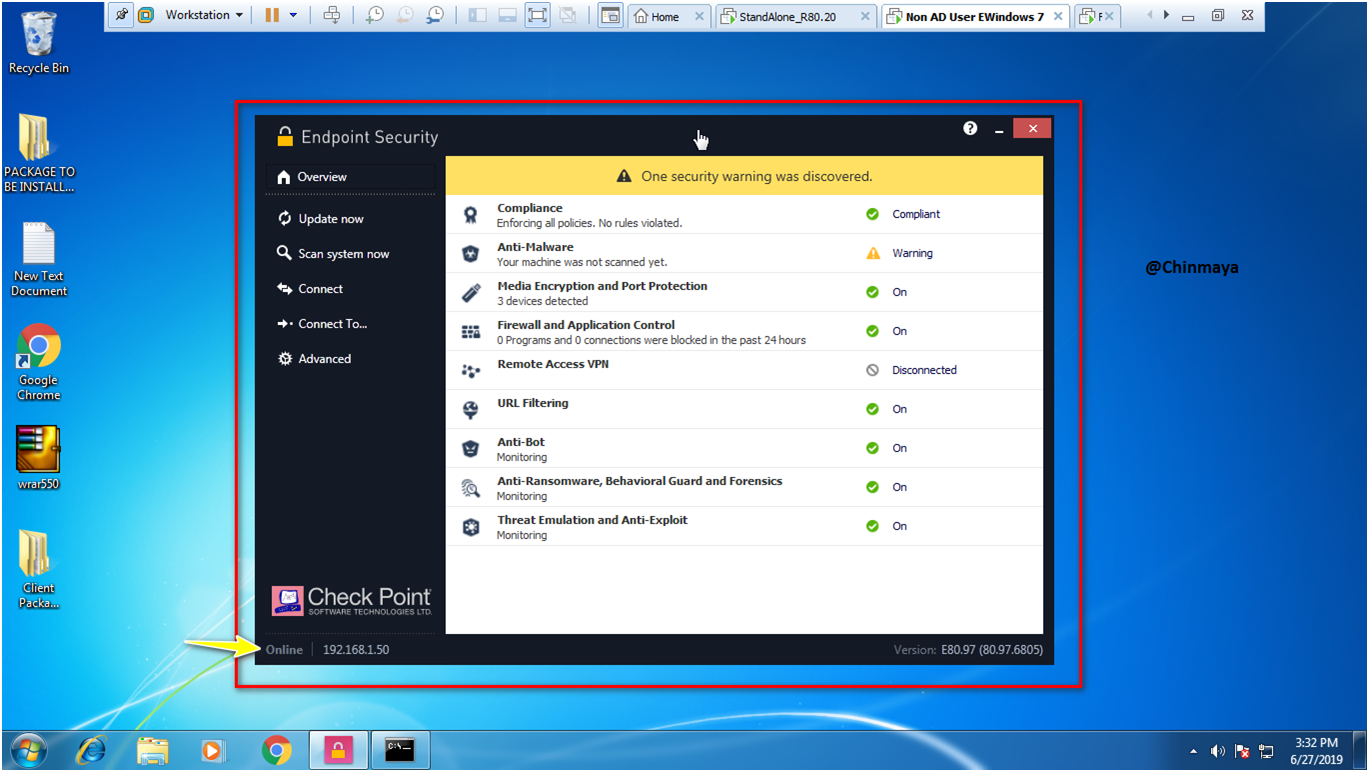
1.Remote Access VPN status showing “Disconnected” so as of now we not required to use these blade so we need to disable this blade.
2.Anti-Malware status showing “Warning” means still the machine is not yet scanned so we need to start the scan to make status “ok” (on).
NOTE: On below its showing “Online” means the Endpoint Client able to communicate to the Endpoint Server.
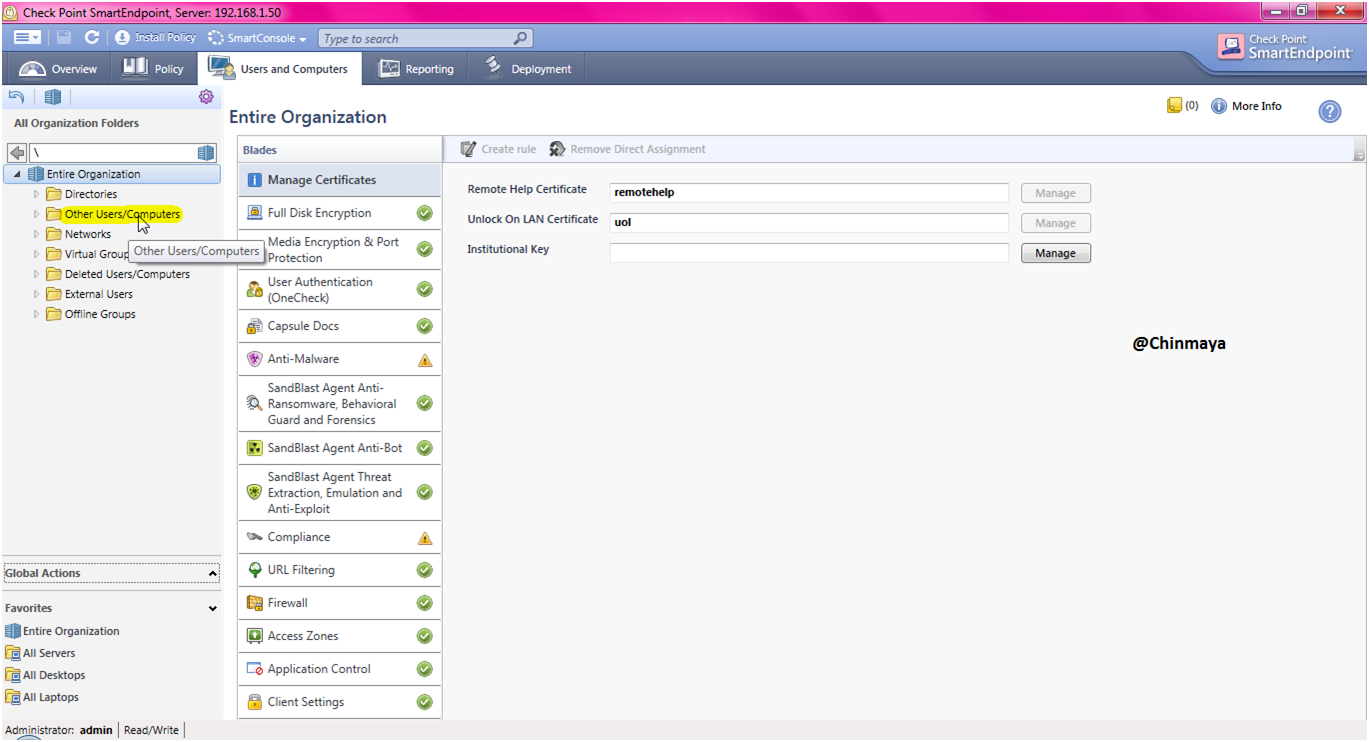
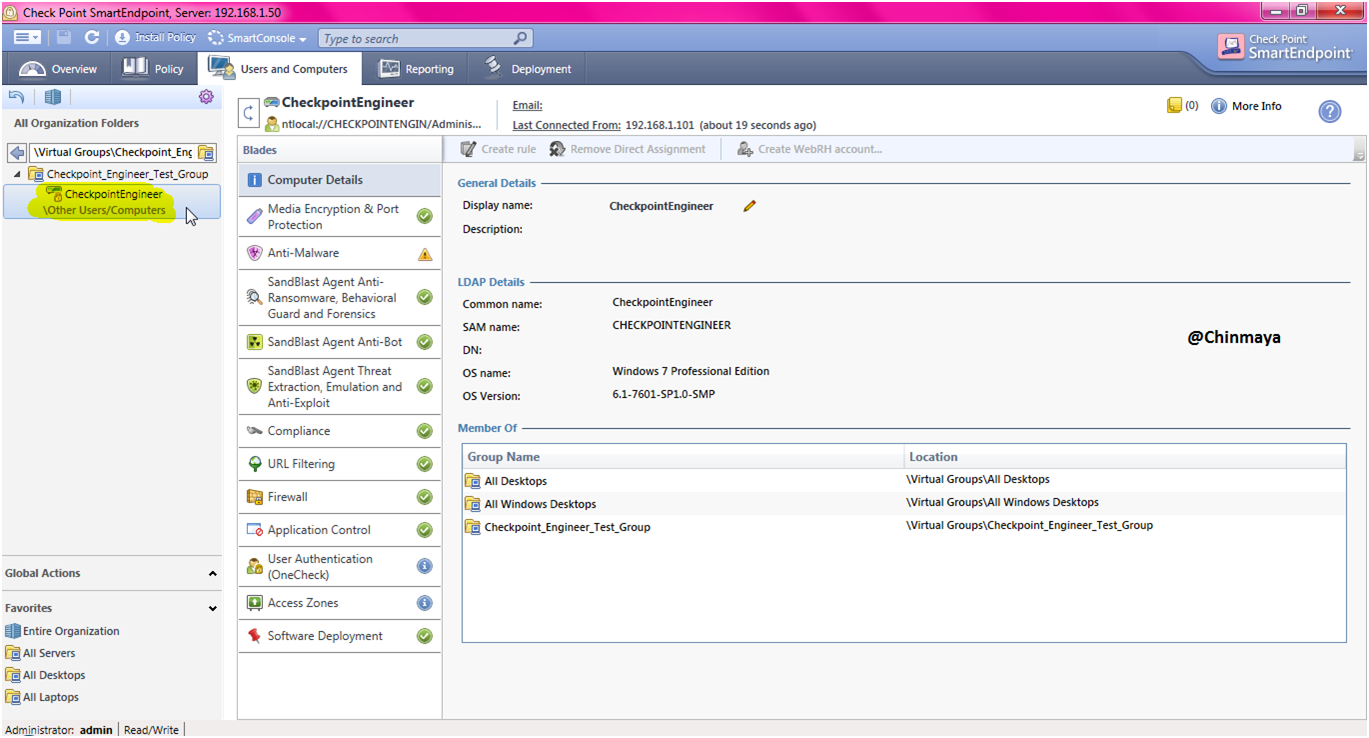
STEP: Open the Endpoint console , as the Agent showing “Online” means we able to see the “Hostname” on “Other User Users/Computers”
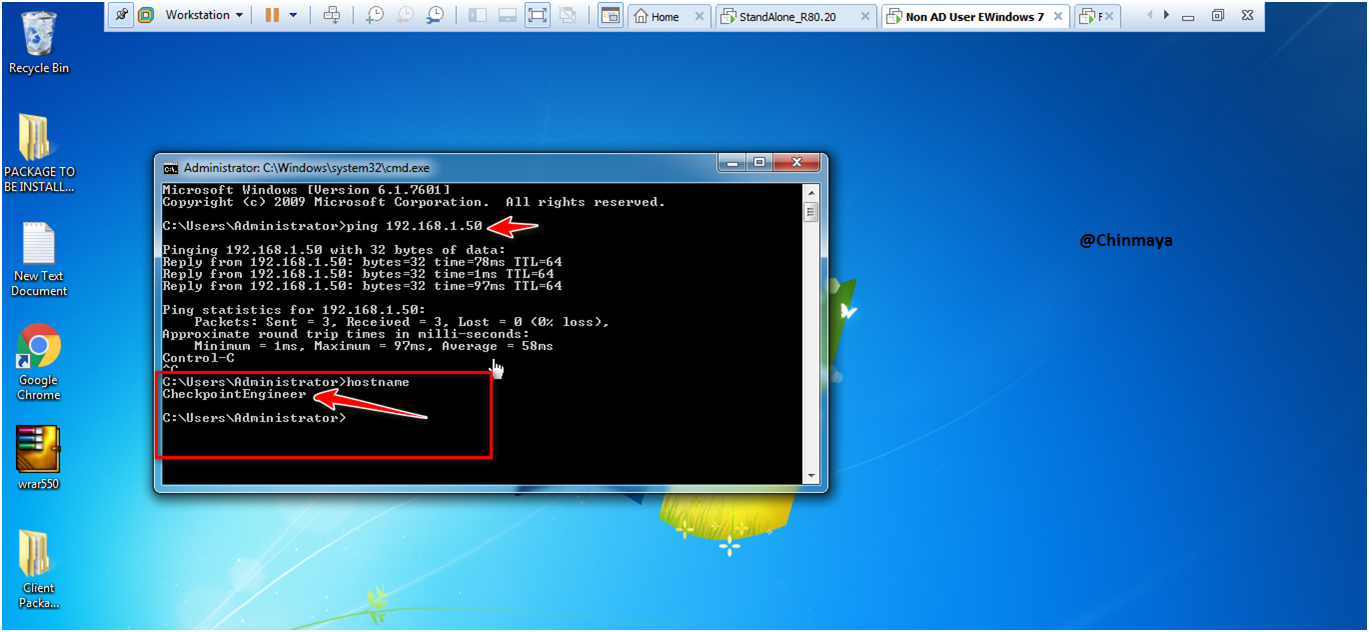
Showing Hostname as “CheckpointEngineer”.

STEP: Check the Hostname of the Windows 7 client machine. (Showing CheckpointEngineer)
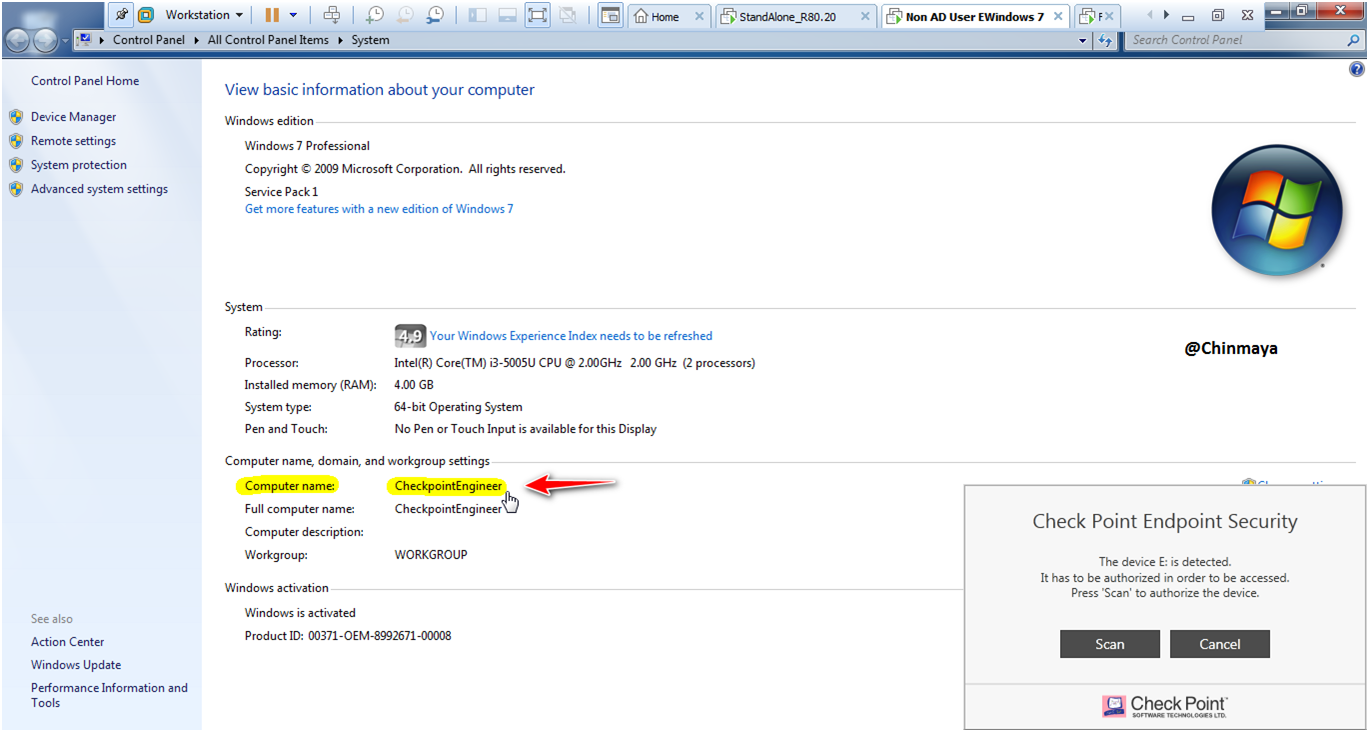
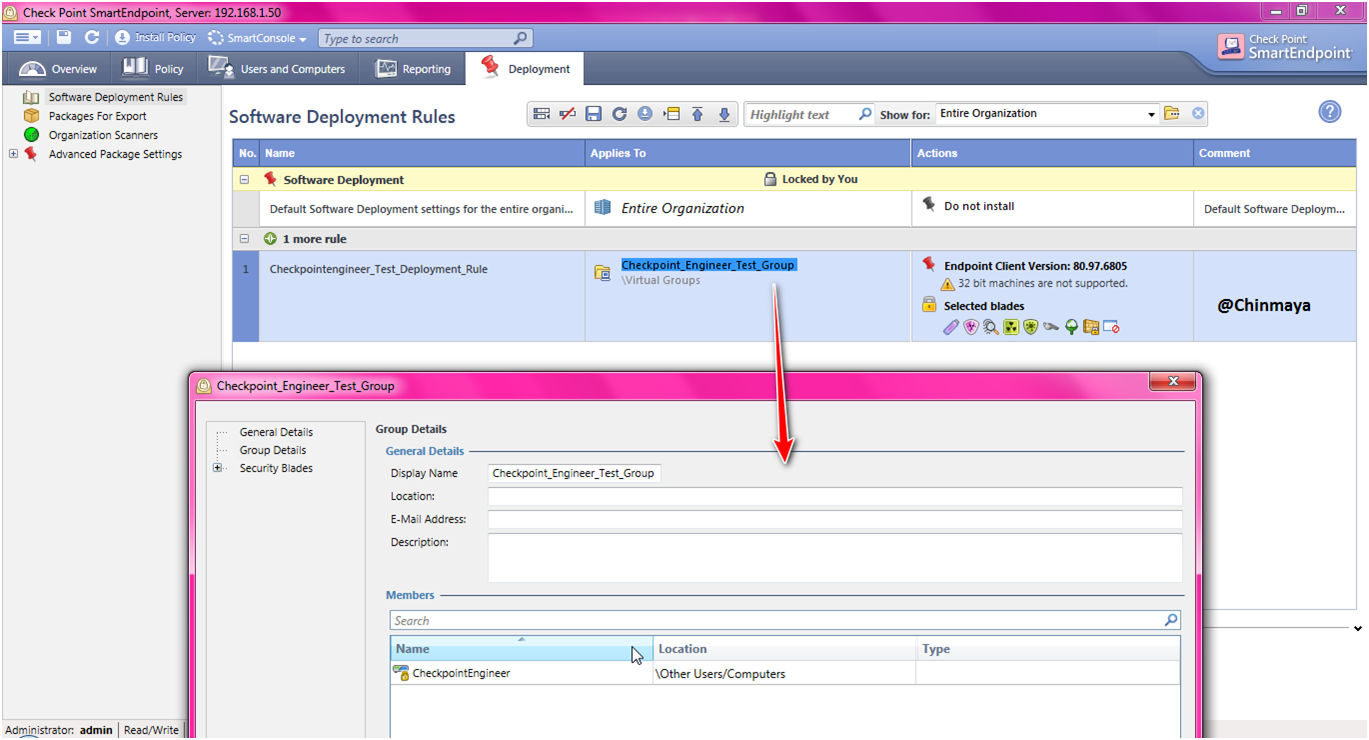
STEP: Now we are going to added the host “CheckpointEnngineer” on virtual group “Checkpoint_Engineer_Test_group”.
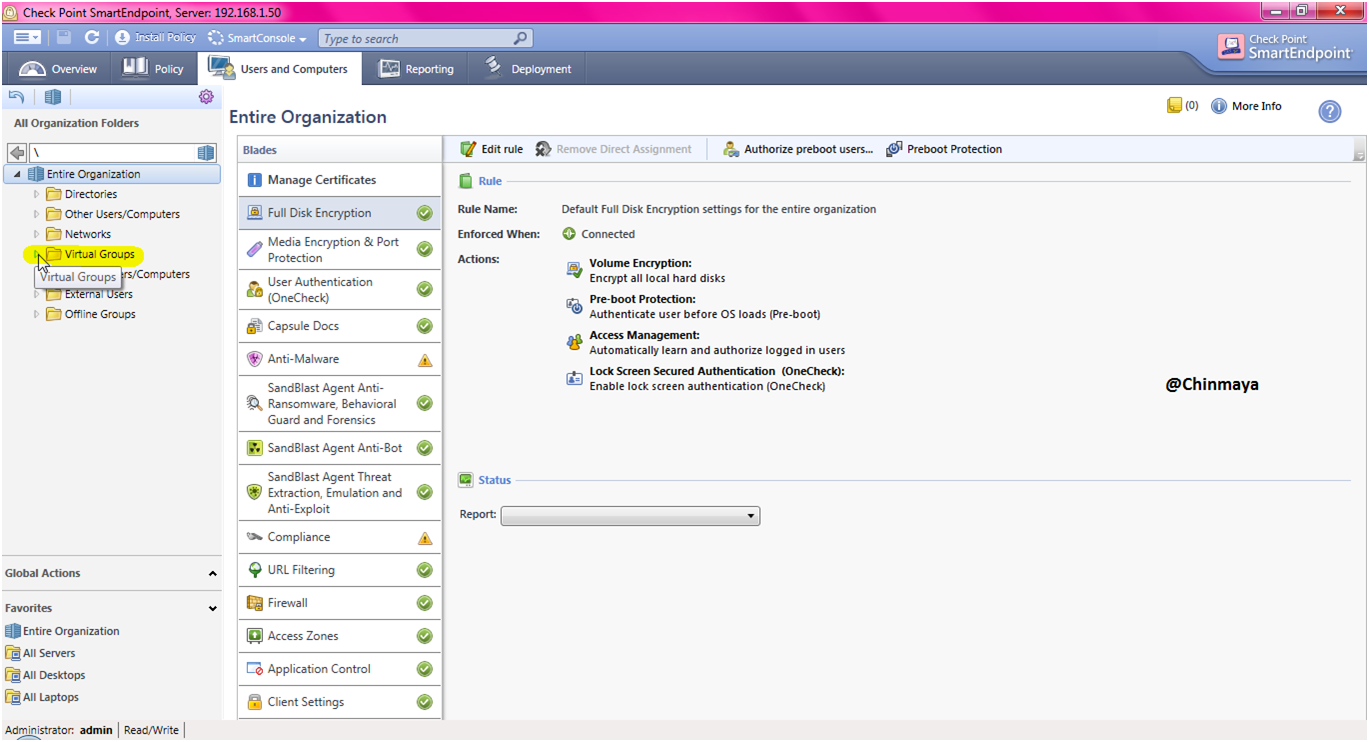
Open the “Virtual Groups”.
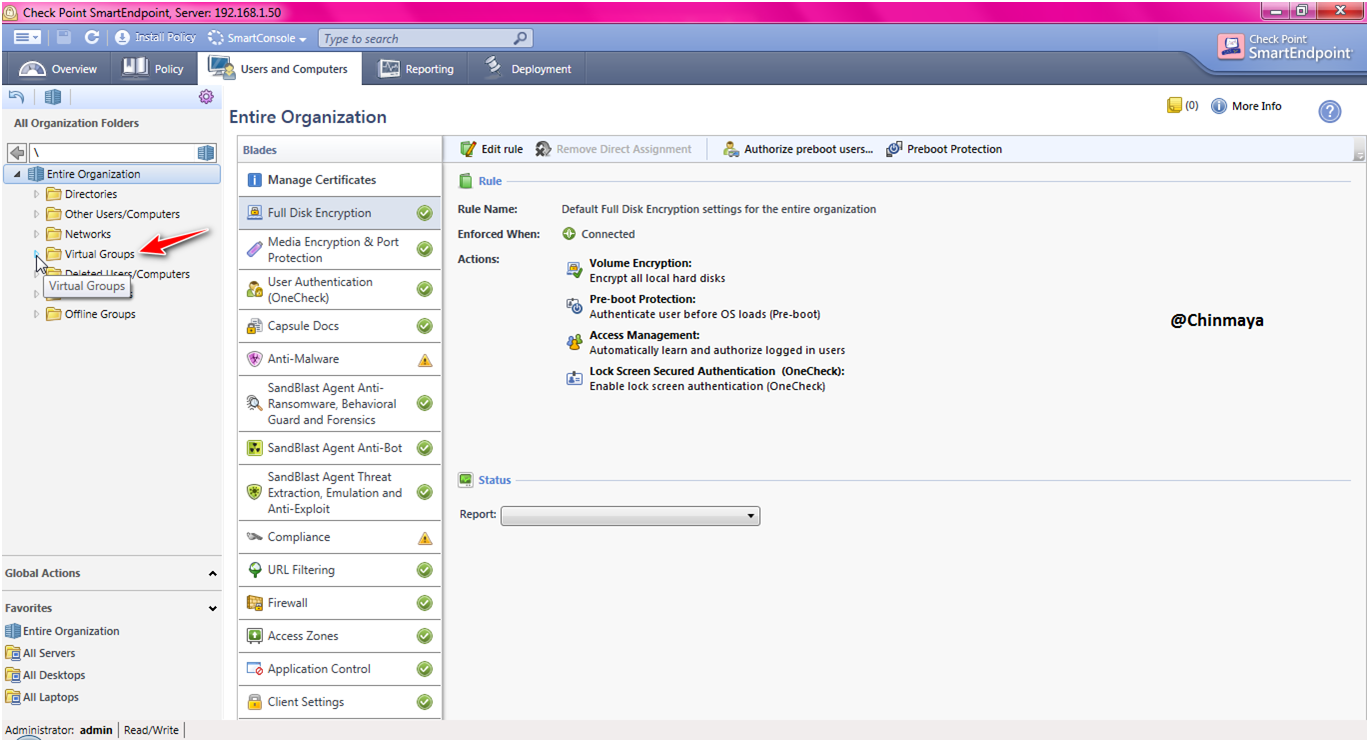
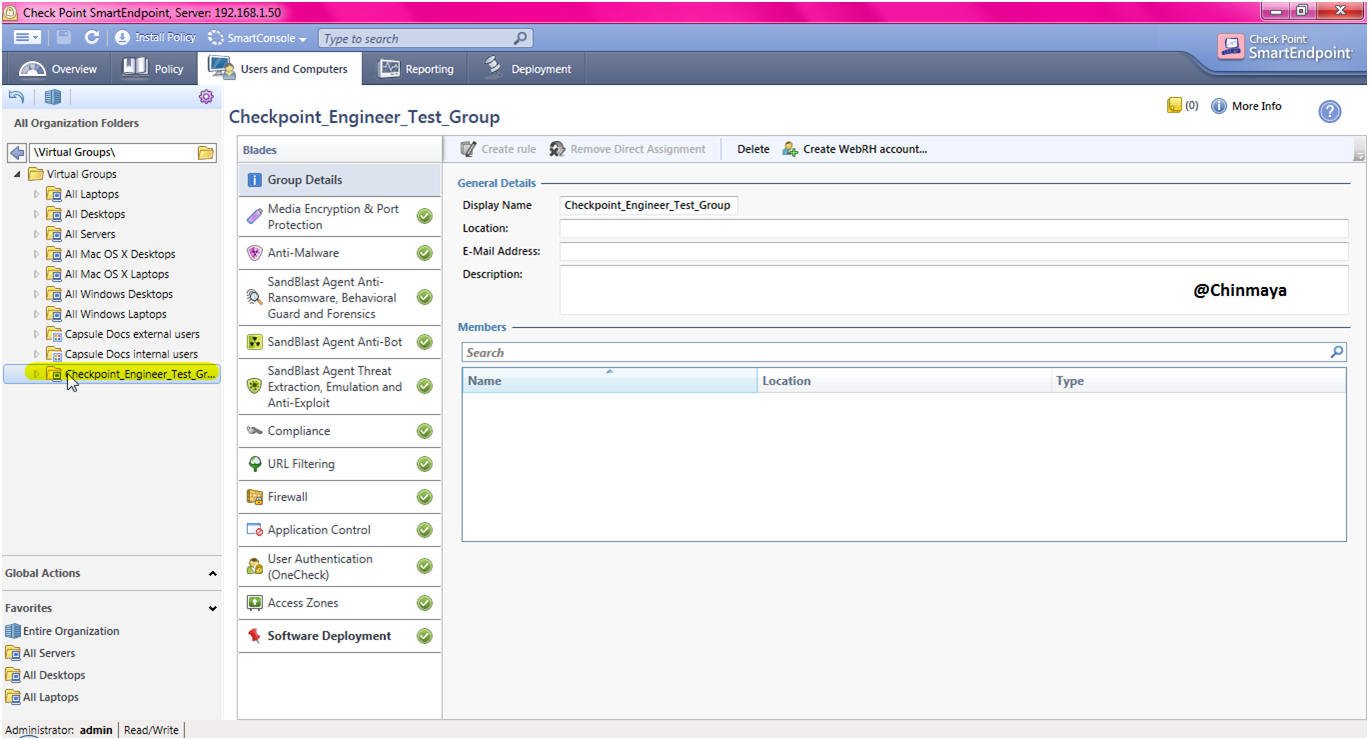
See there is no any host added on this group still. We are going to add the host machine.
Go to the “Other User Users/Computers”

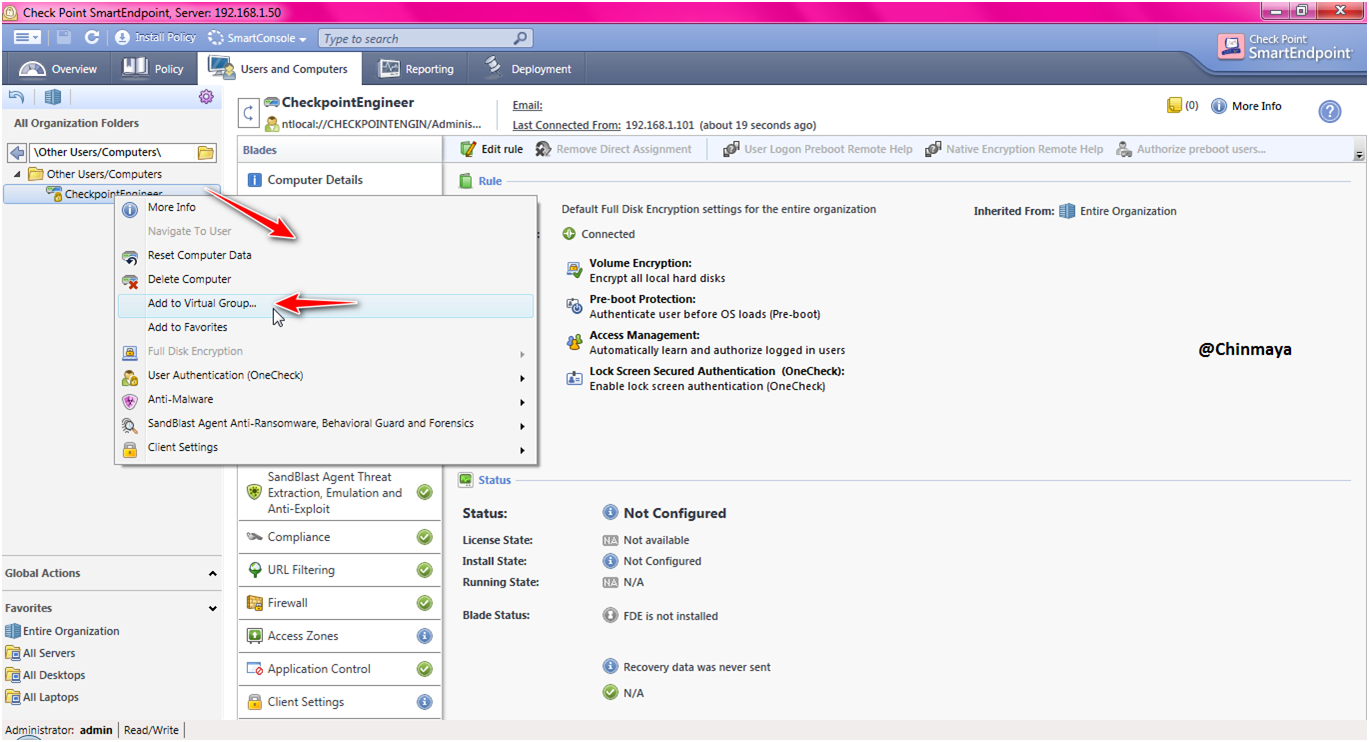
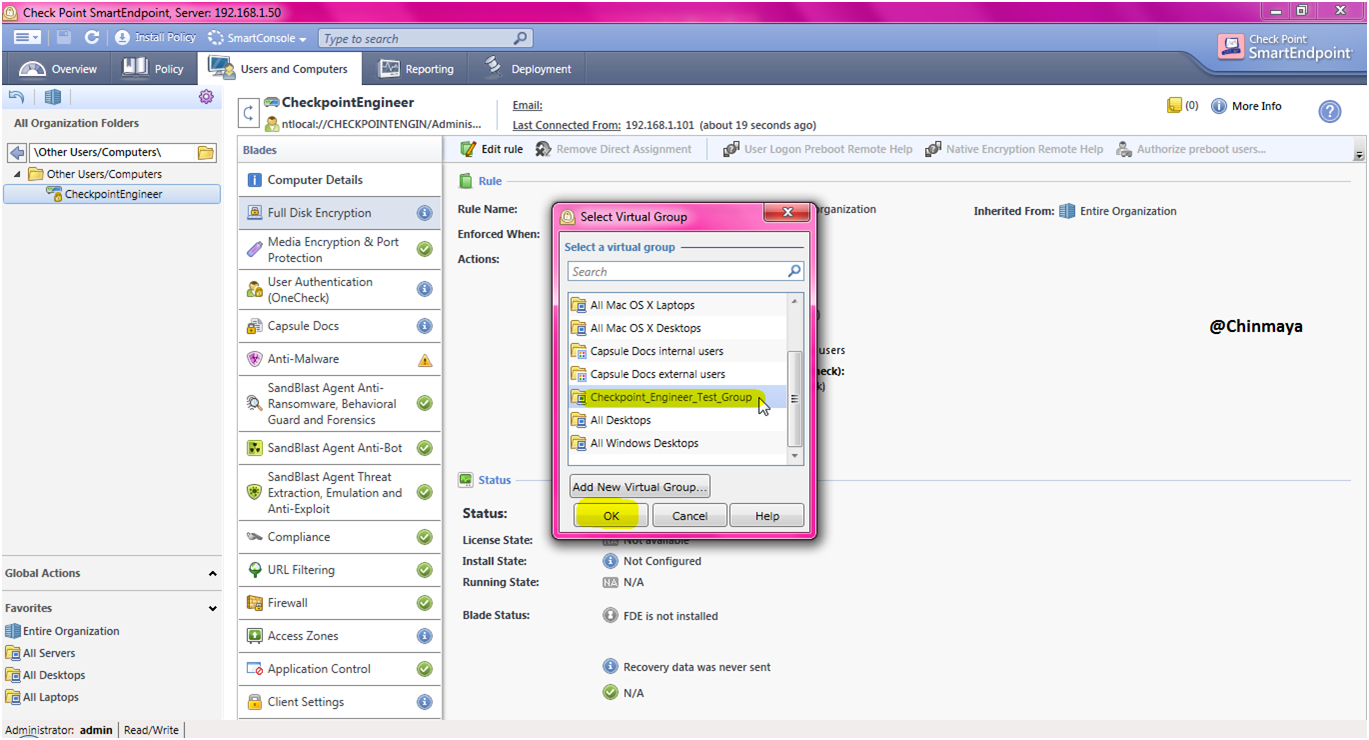
STEP: Right click on “CheckpointEngineer” and then “Add to Virtual Group..” then select the virtual Group “CheckpointEngineer_Test_Group” and click “Ok”.
HostName ---> Right Click ---> Add to Virtual Group.. ---> ---> OK
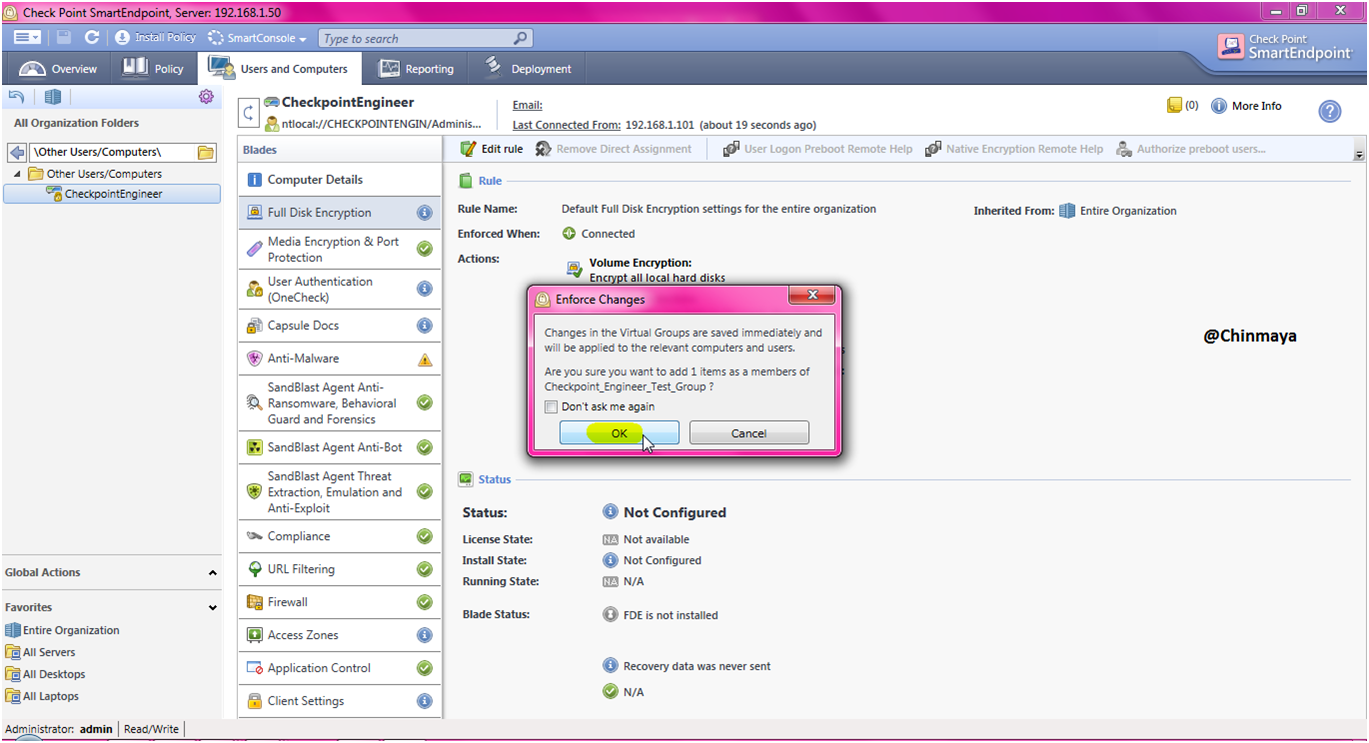
Host_Machine (CheckpointEngineer) is added on the group (Checkpoint_Engineer_Test_Group) successfully.
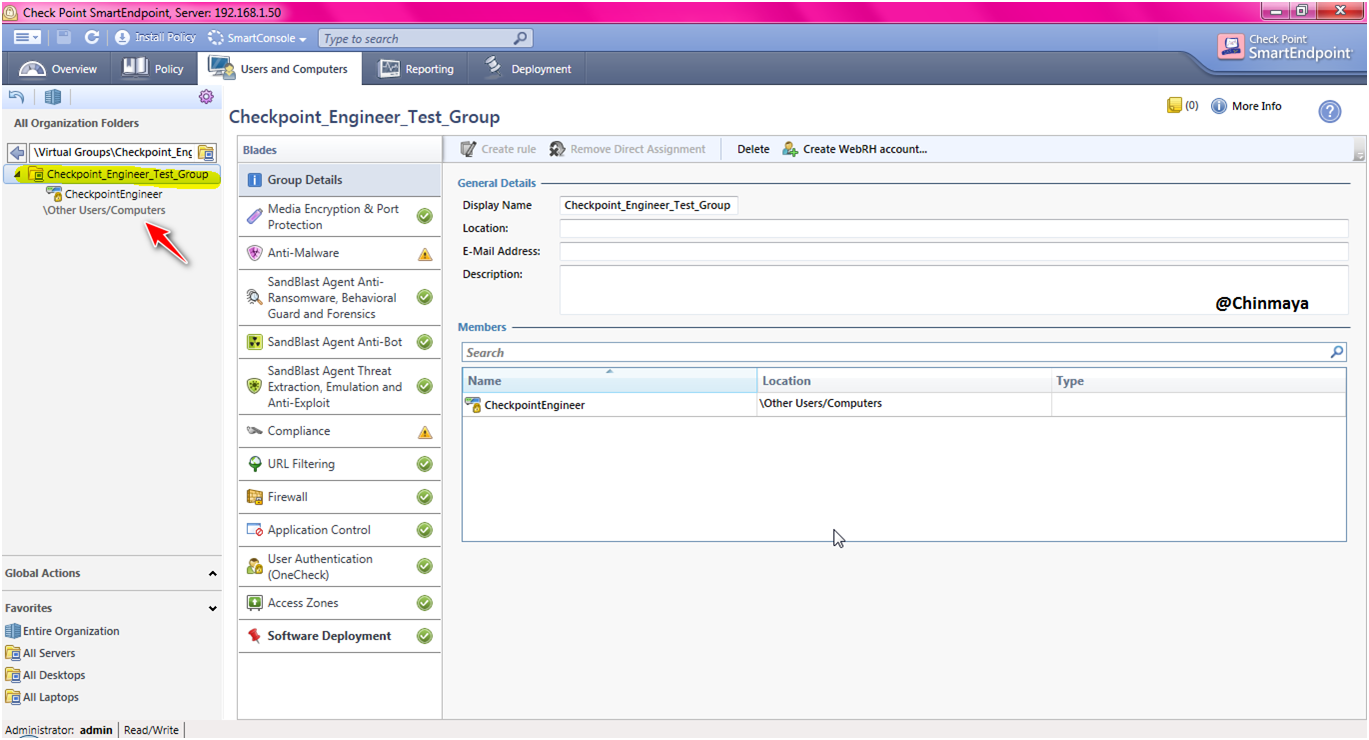
STEP: Go to “Deployment”
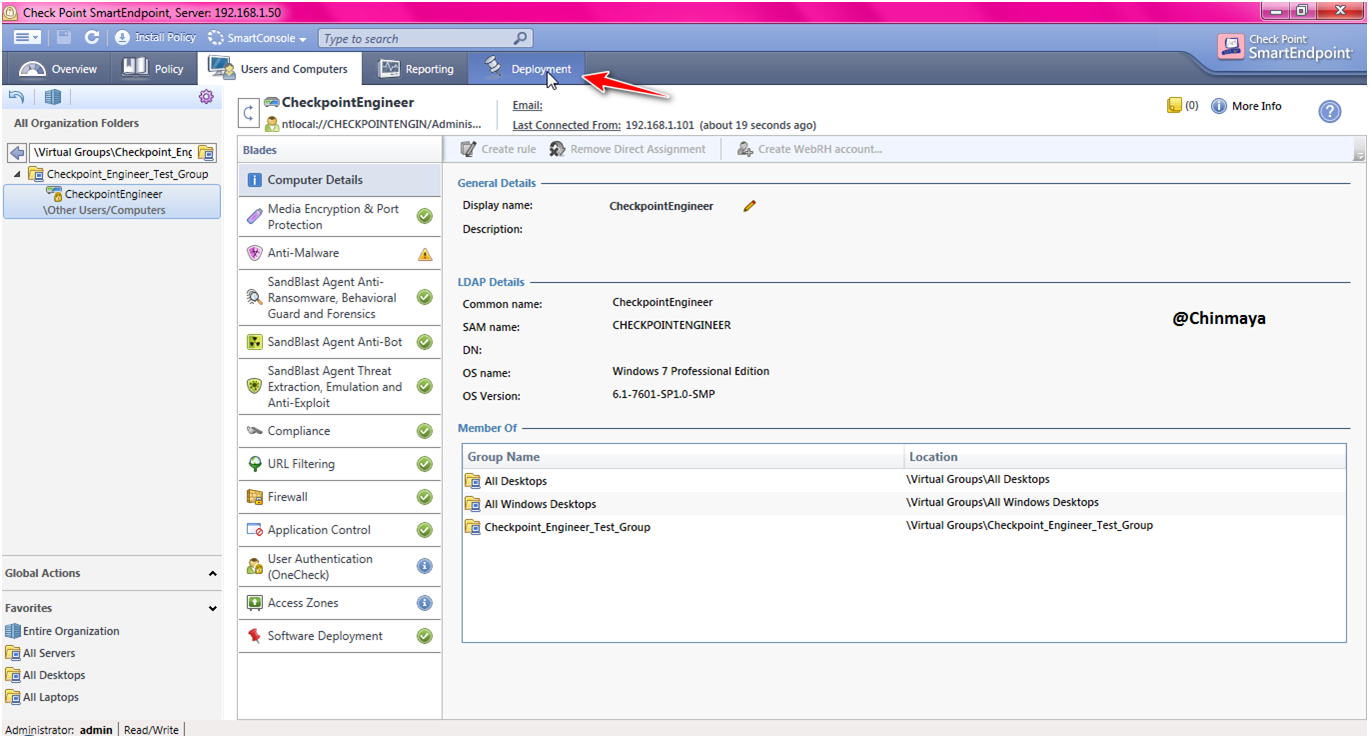
STEP: I am going to disable the “Endpoint connect VPN” , “Capsule Docs” because till we not required also disable the Full Disk Encryption for Disk Encryption, I will create a separate post.
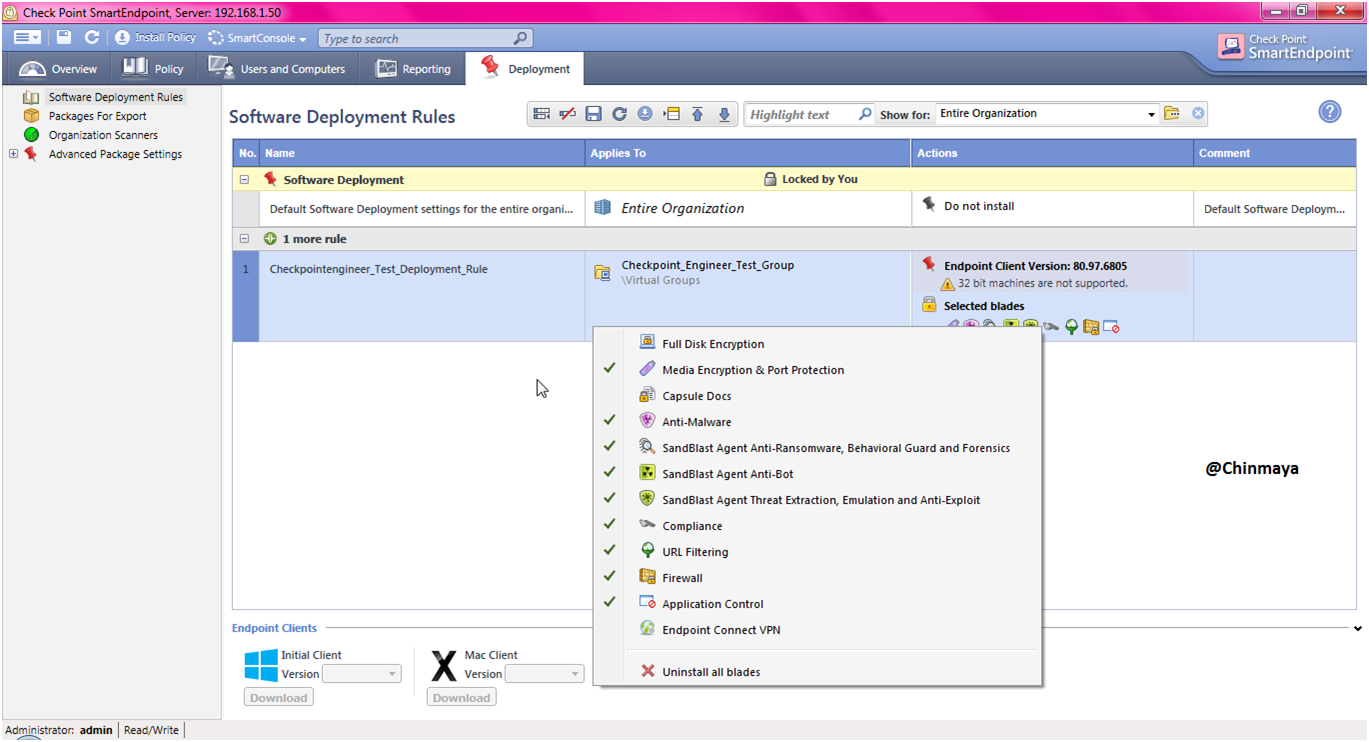
STEP: Save and install the policy.

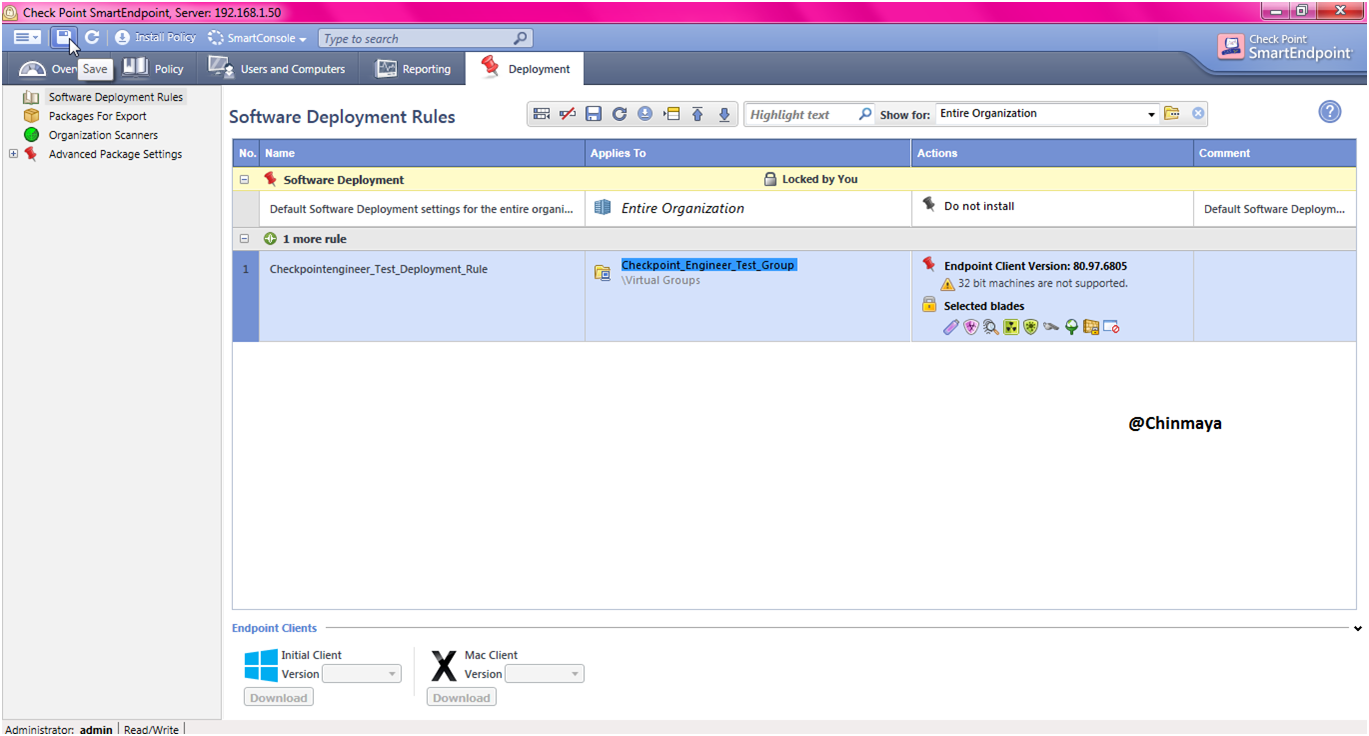
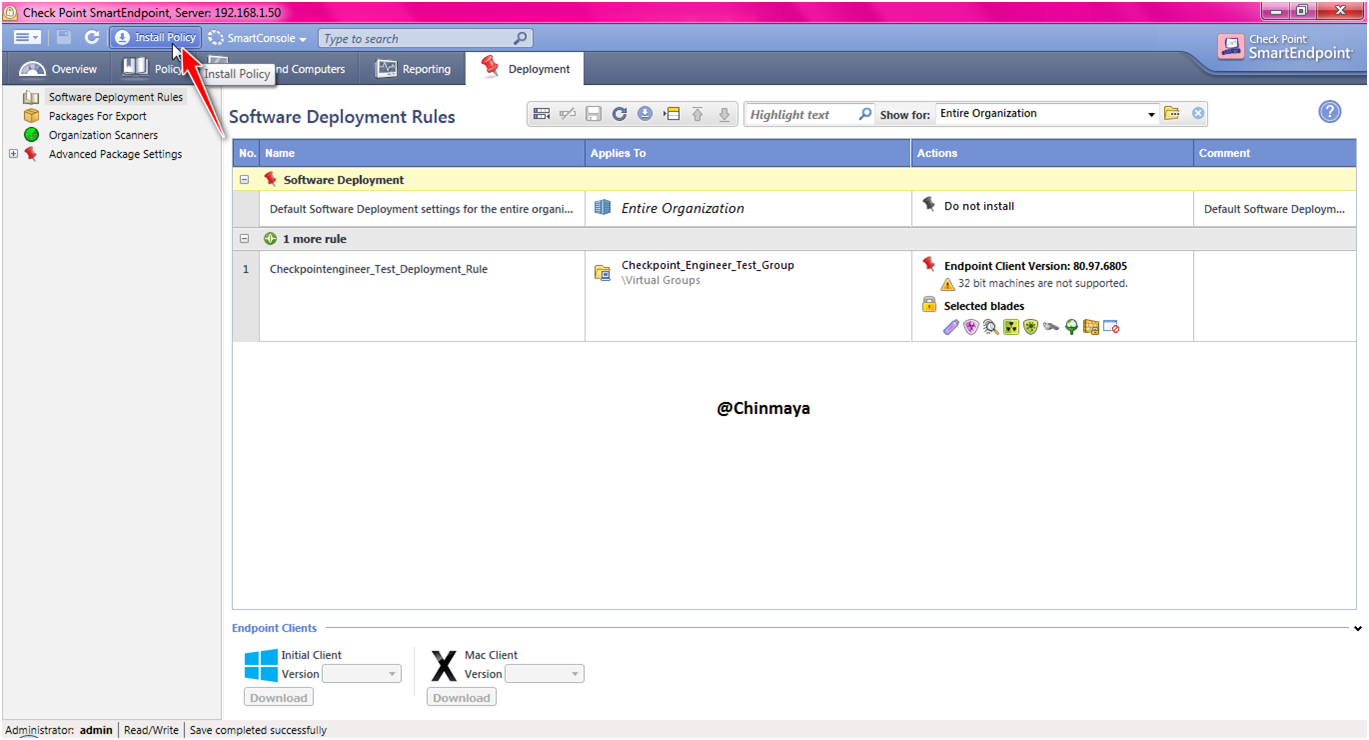
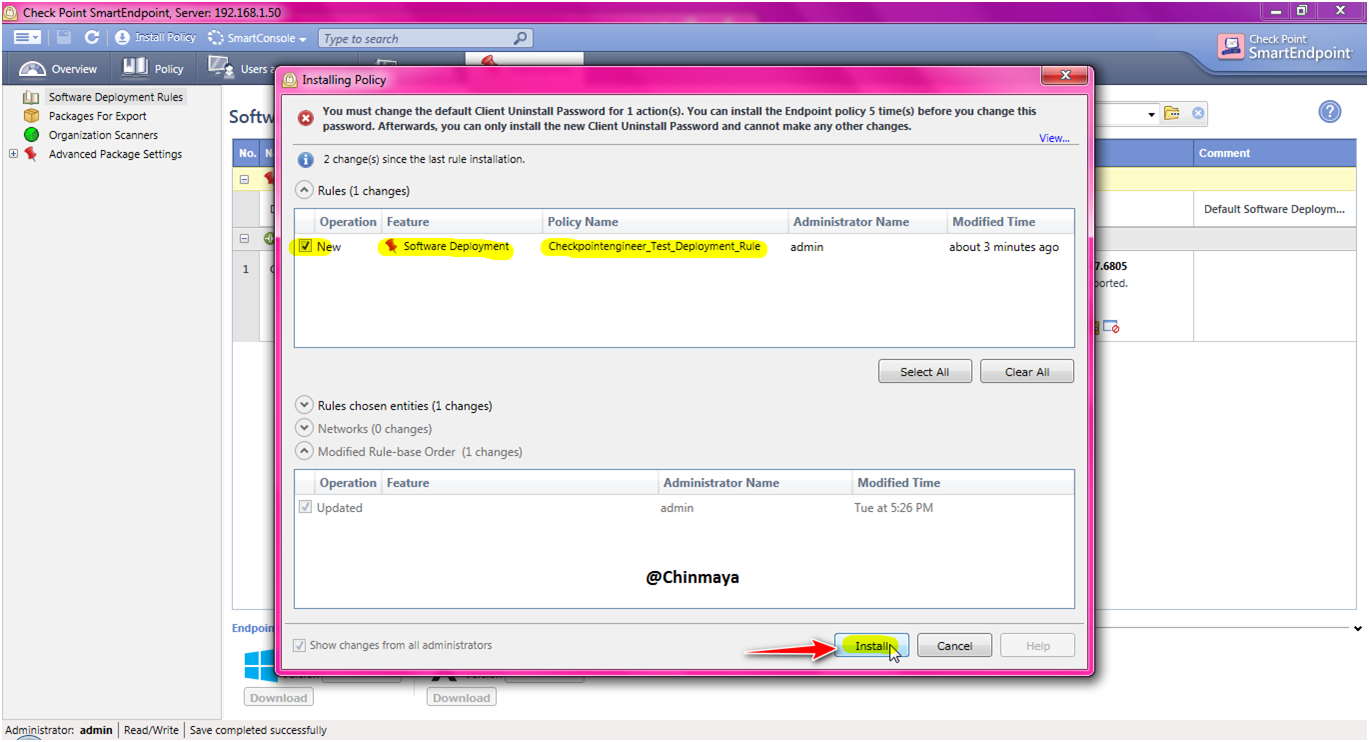
STEP : Select only that policy that you want to install , like some time you see a multiple policy so you need to mark those policy that you want to install.
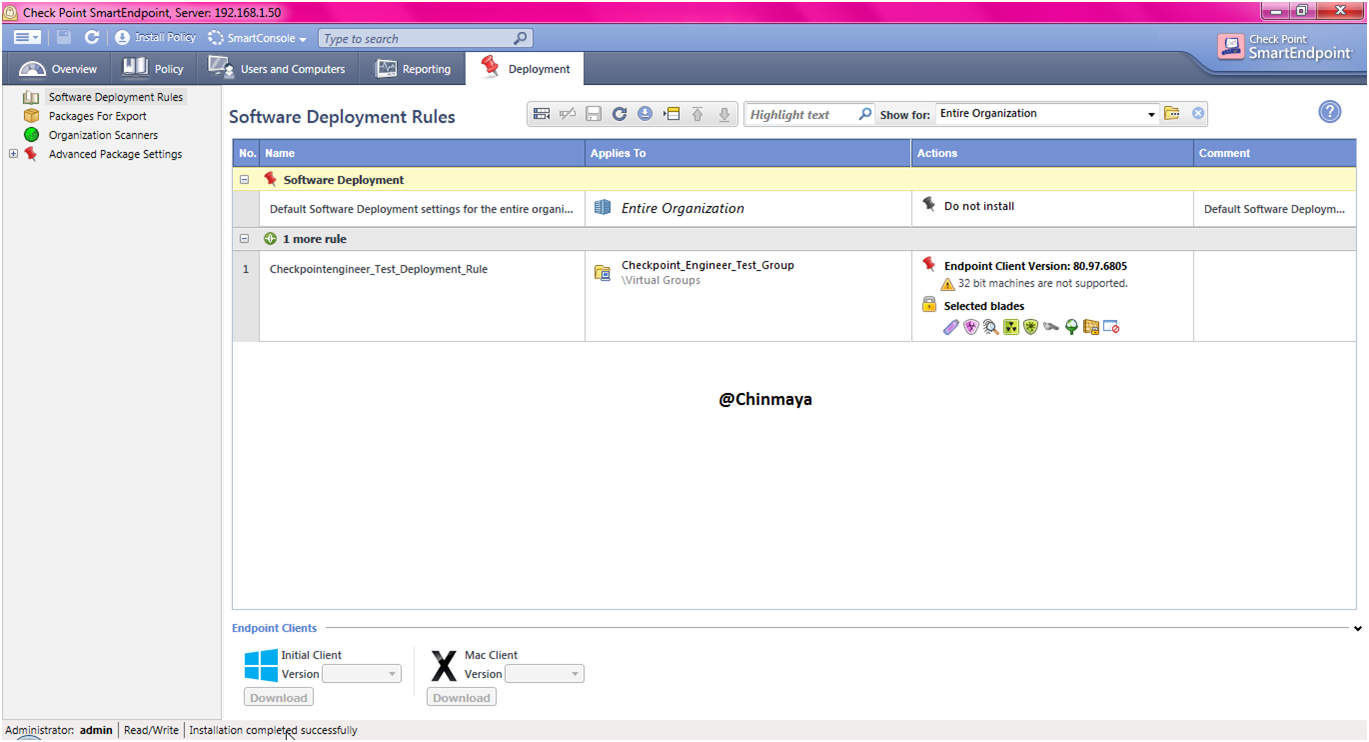
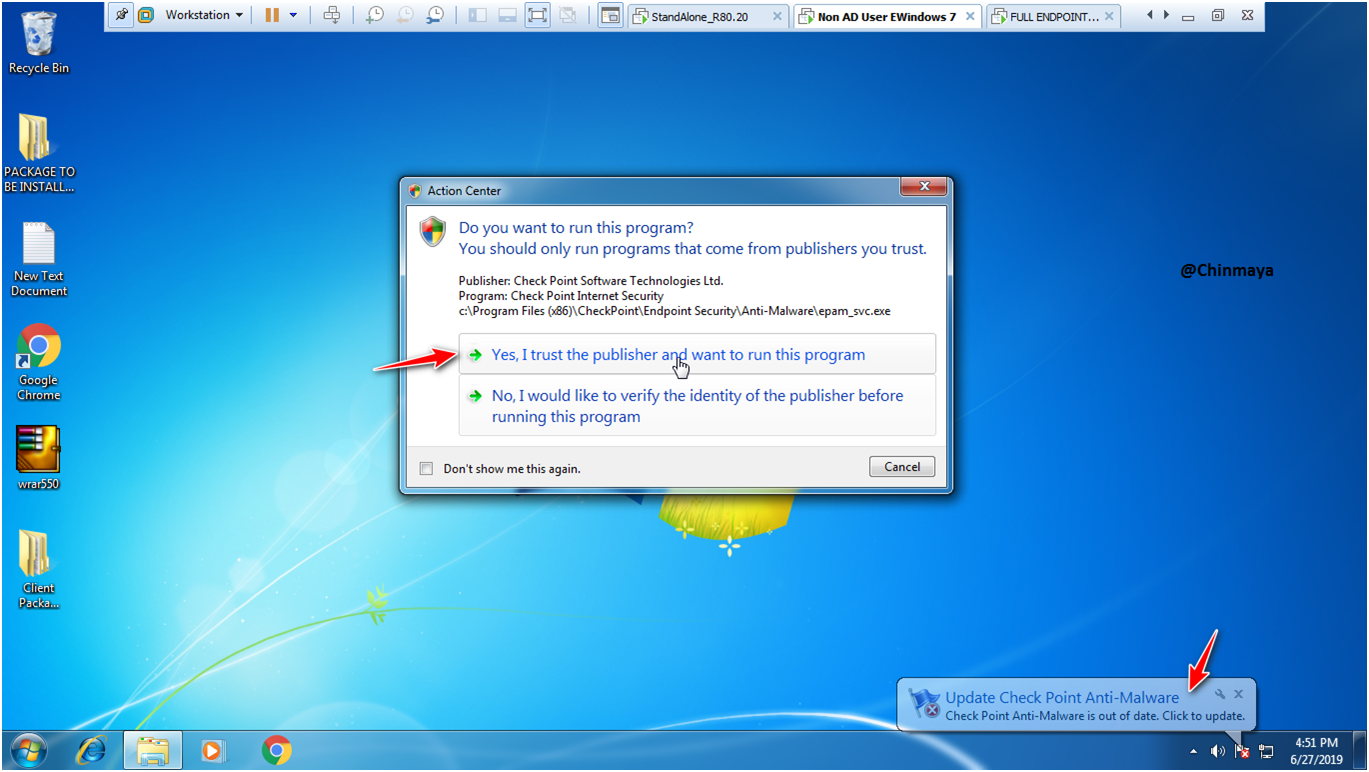
STEP: Open the Endpoint Agent and then click “Update now”.
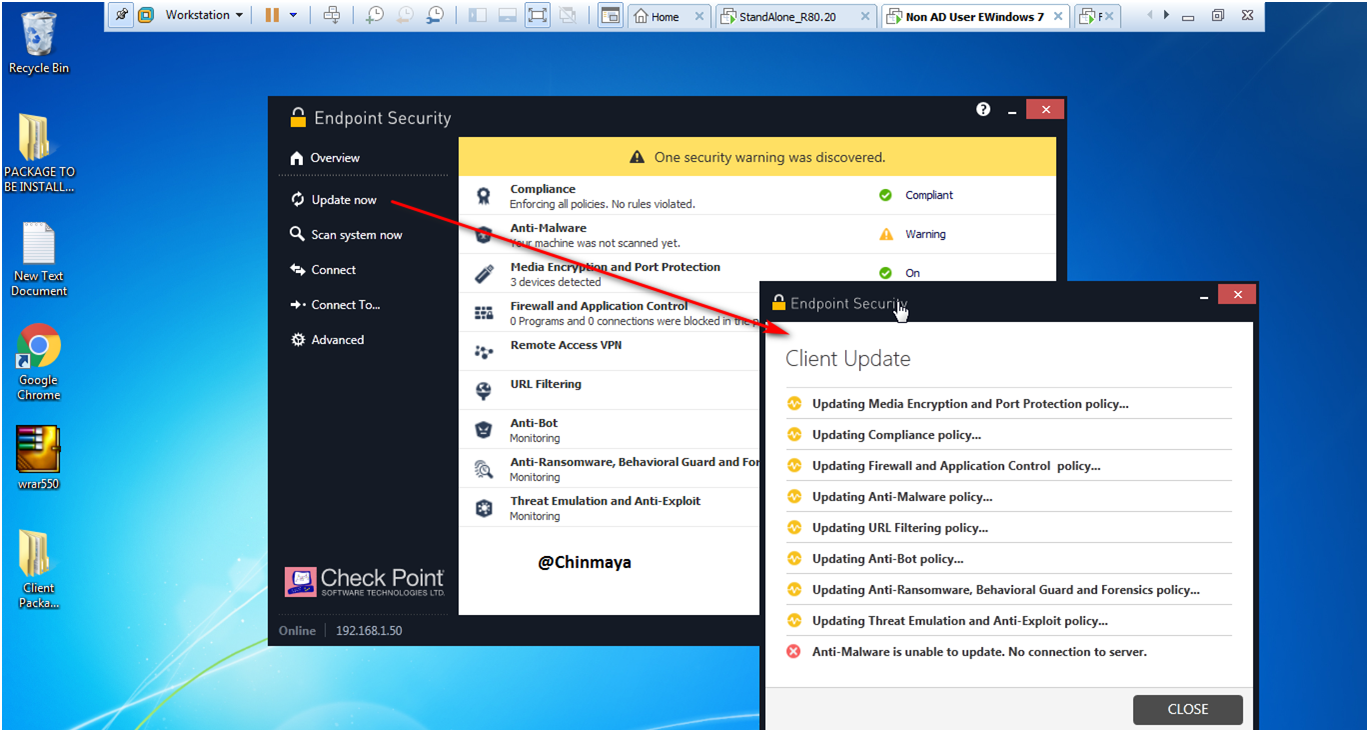
STEP: Wait some time and you able to see one popup “Endpoint Security Upgrade” click “Upgrade Now ” icon to install or else you can postpone it.
So basically this is the first time policy update including blade. I am not going to upgrade the Endpoint Client Version so for version upgrade I am create a separate post.
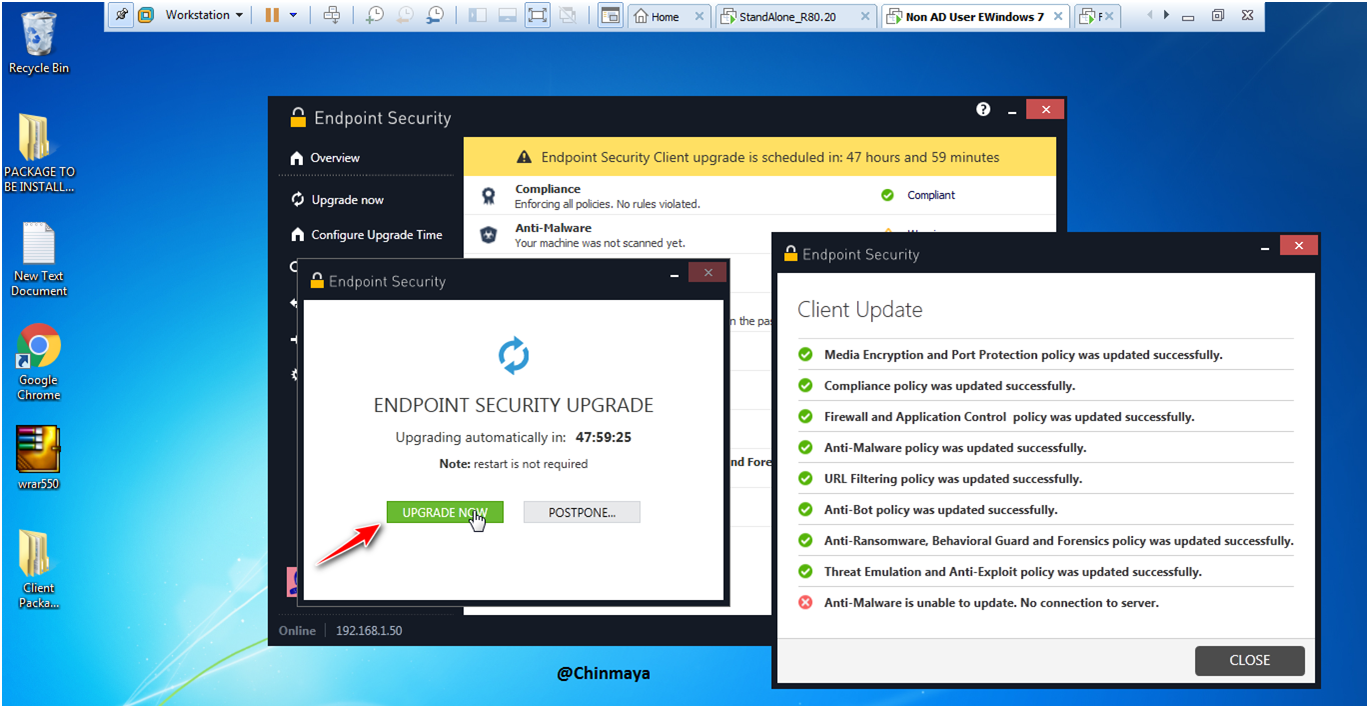
Upgrade in process
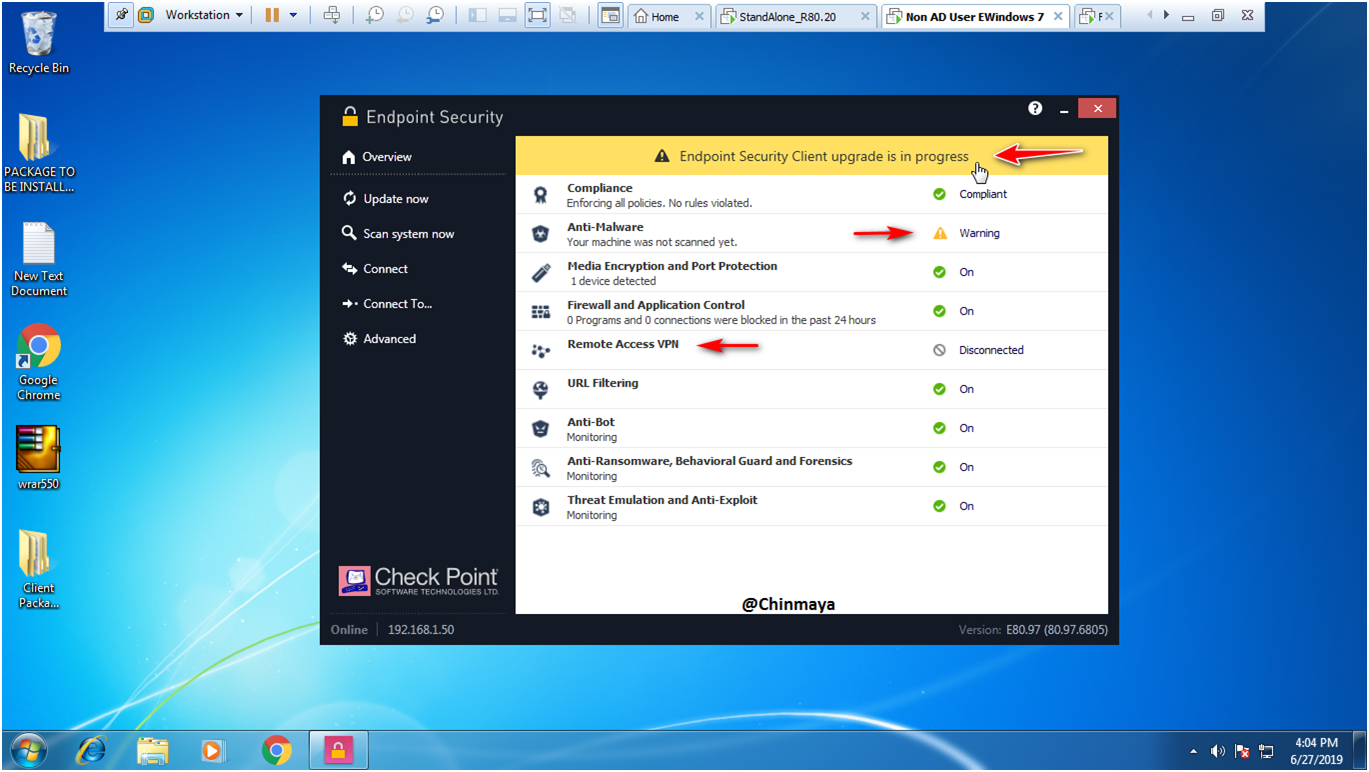
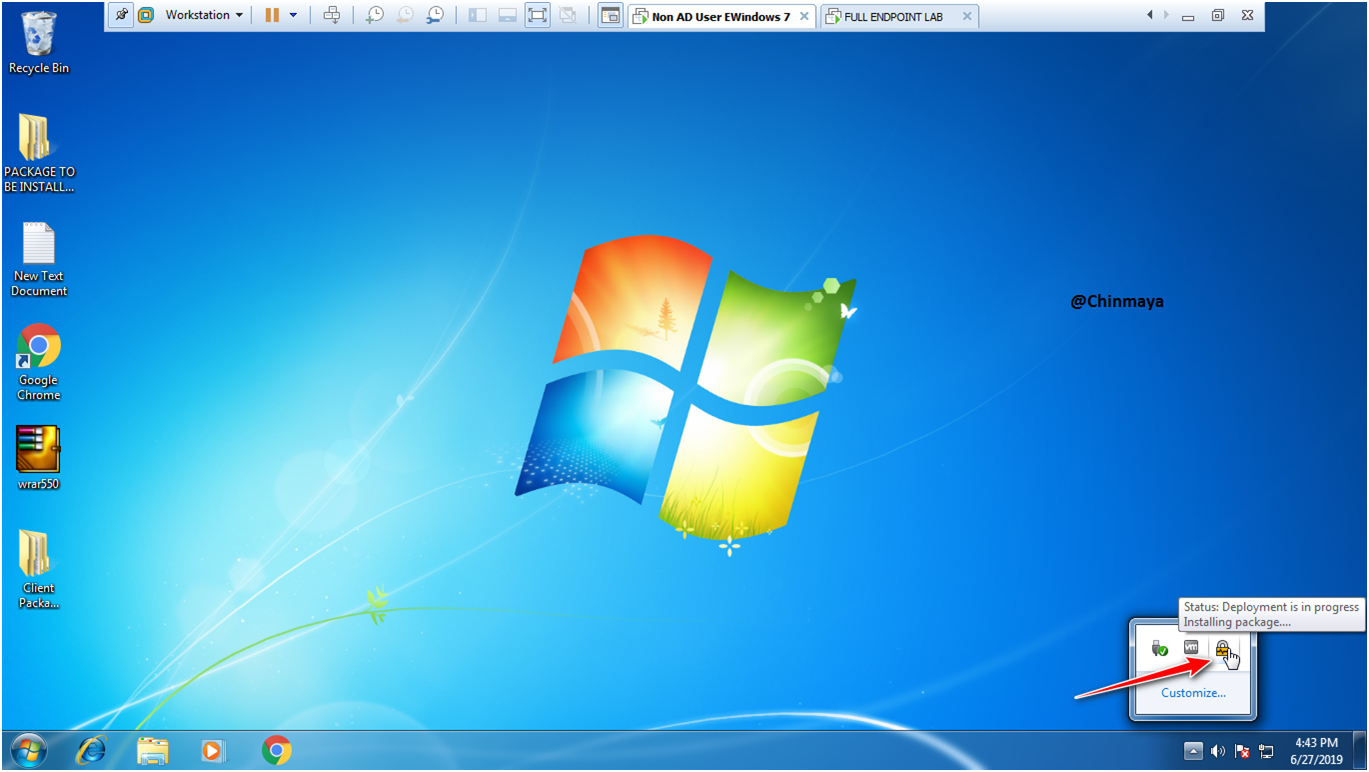
STEP: Now we see the Endpoint Agent is update successfully.
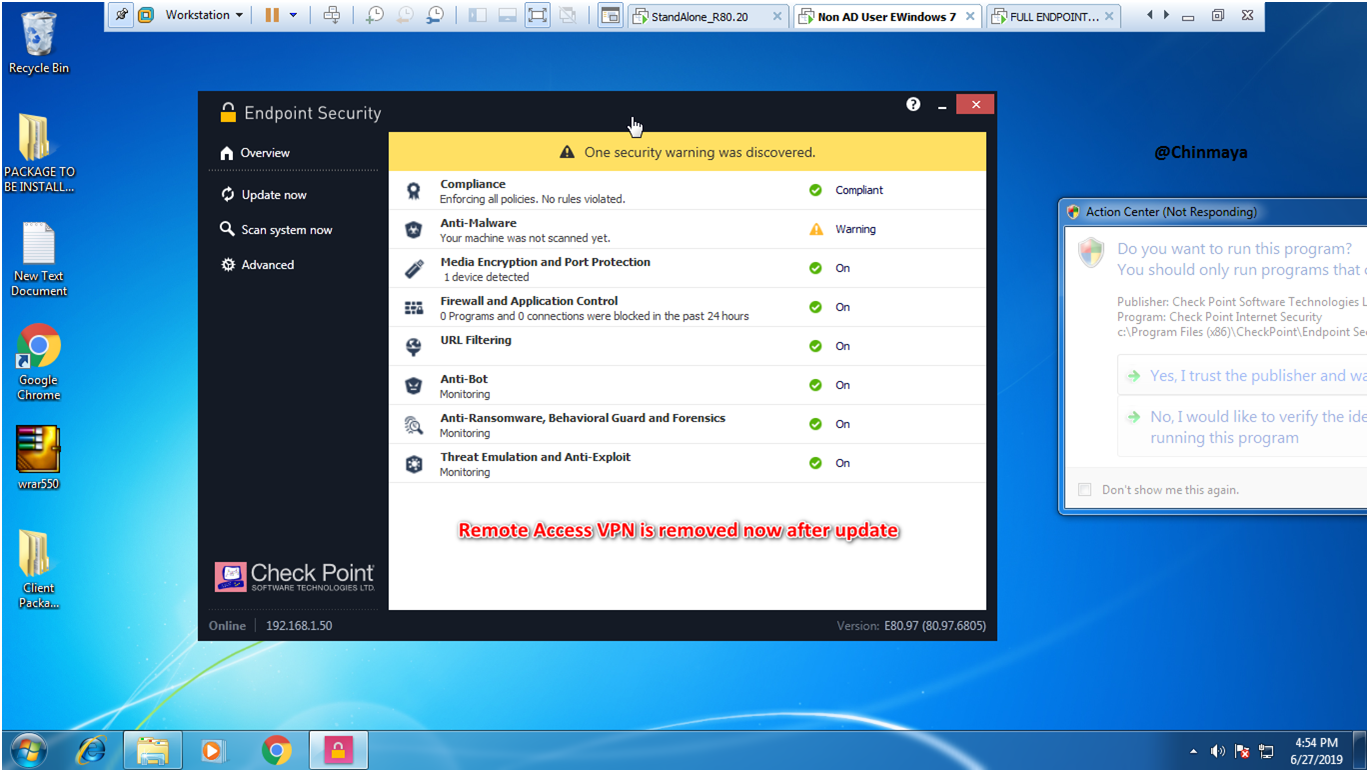
STEP: Click on “Update now” .
We still see one error “Anti-Malware is unable to update. No connection server”

STEP: Open SmartEndpoint console ---> menu ---> Tools ---> "Anti Malware Updates"
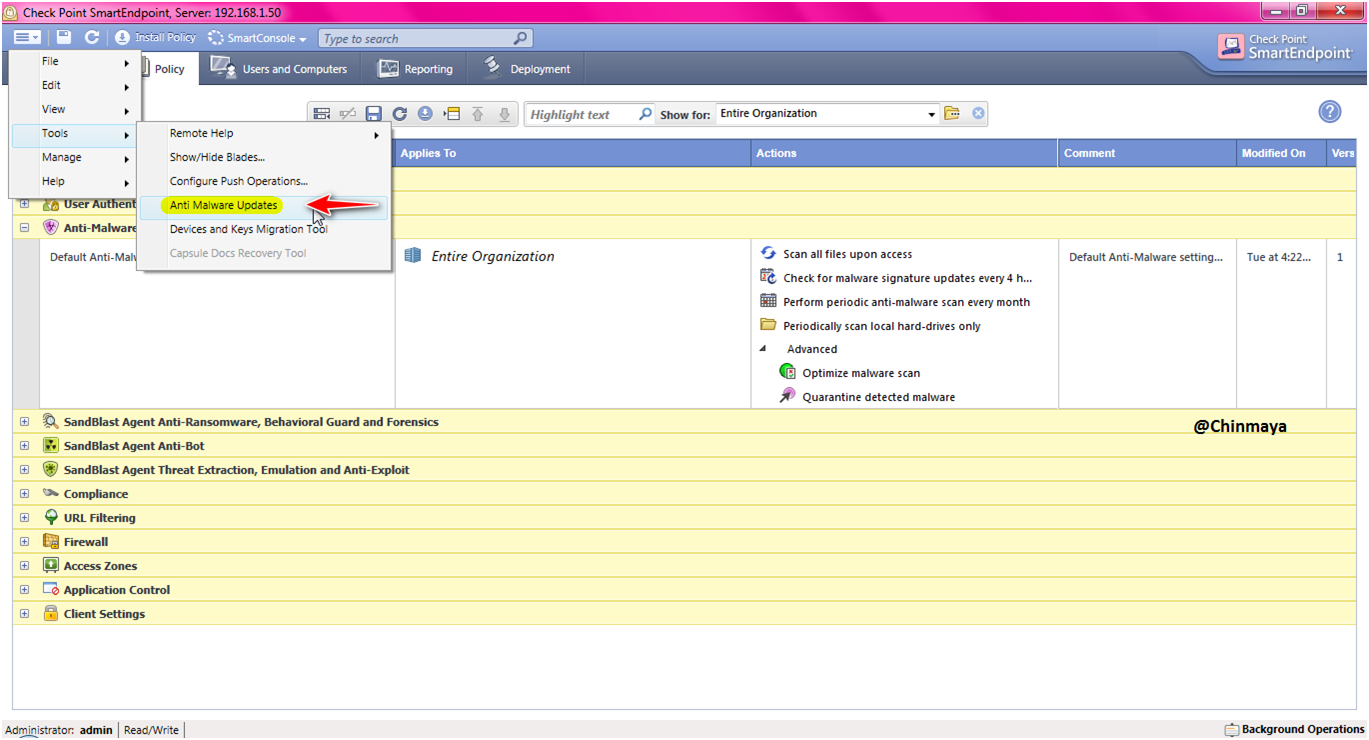
STEP: We see the below error.
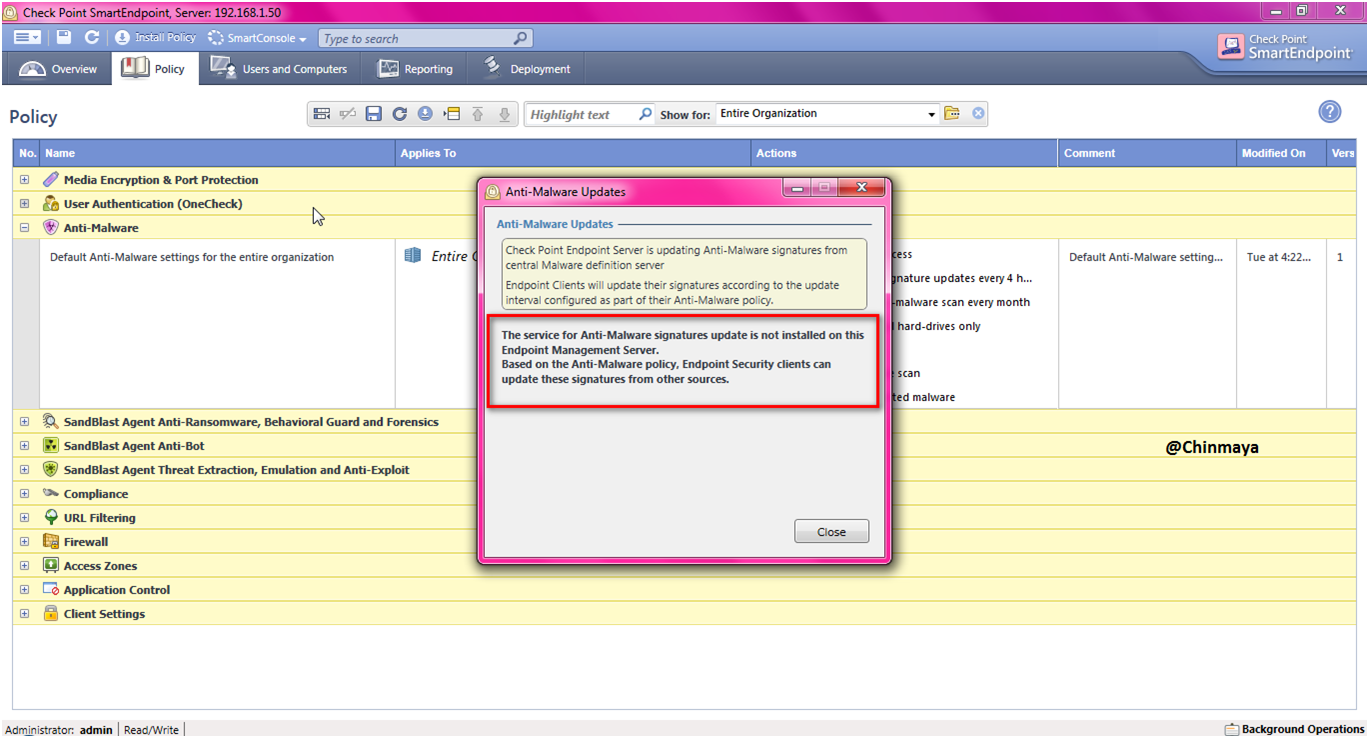
STEP: First we need Create a separate policy for Anti-Malware.

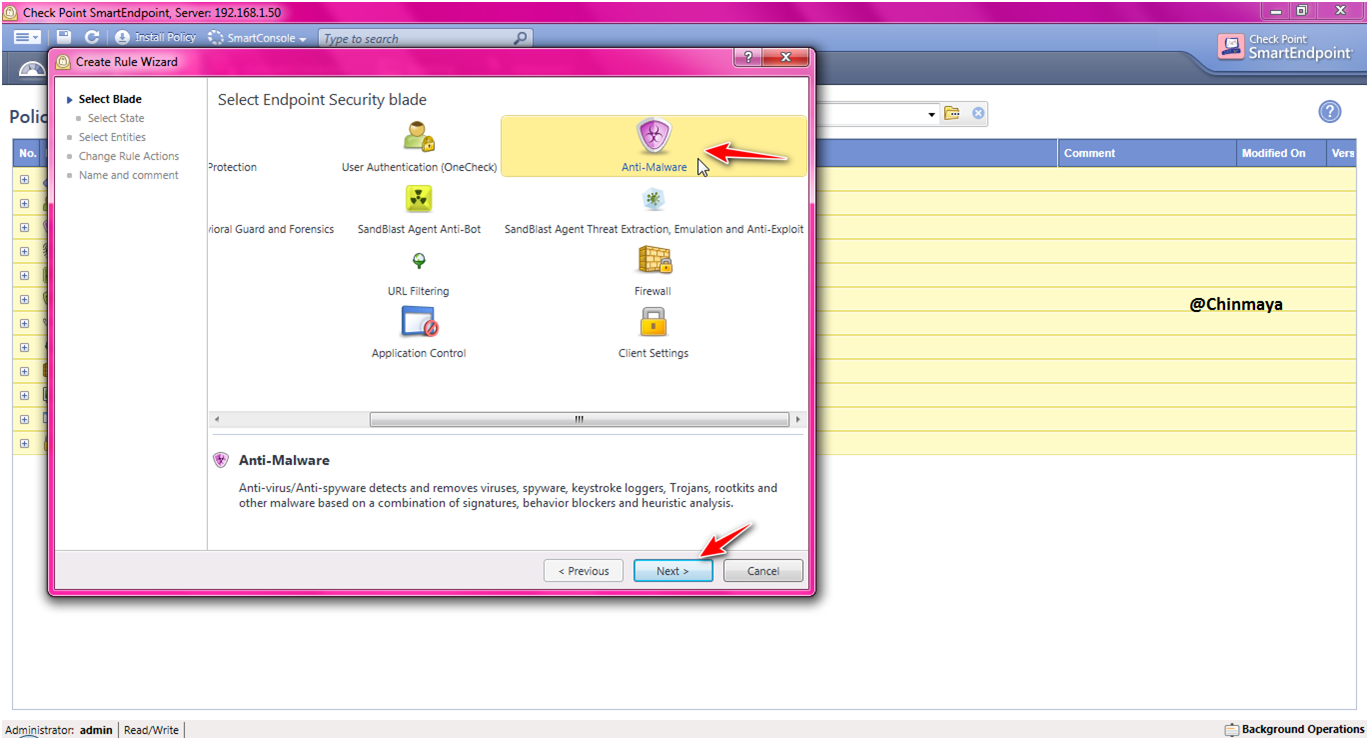
STEP: Select “Anti Malware” and click “Next”.
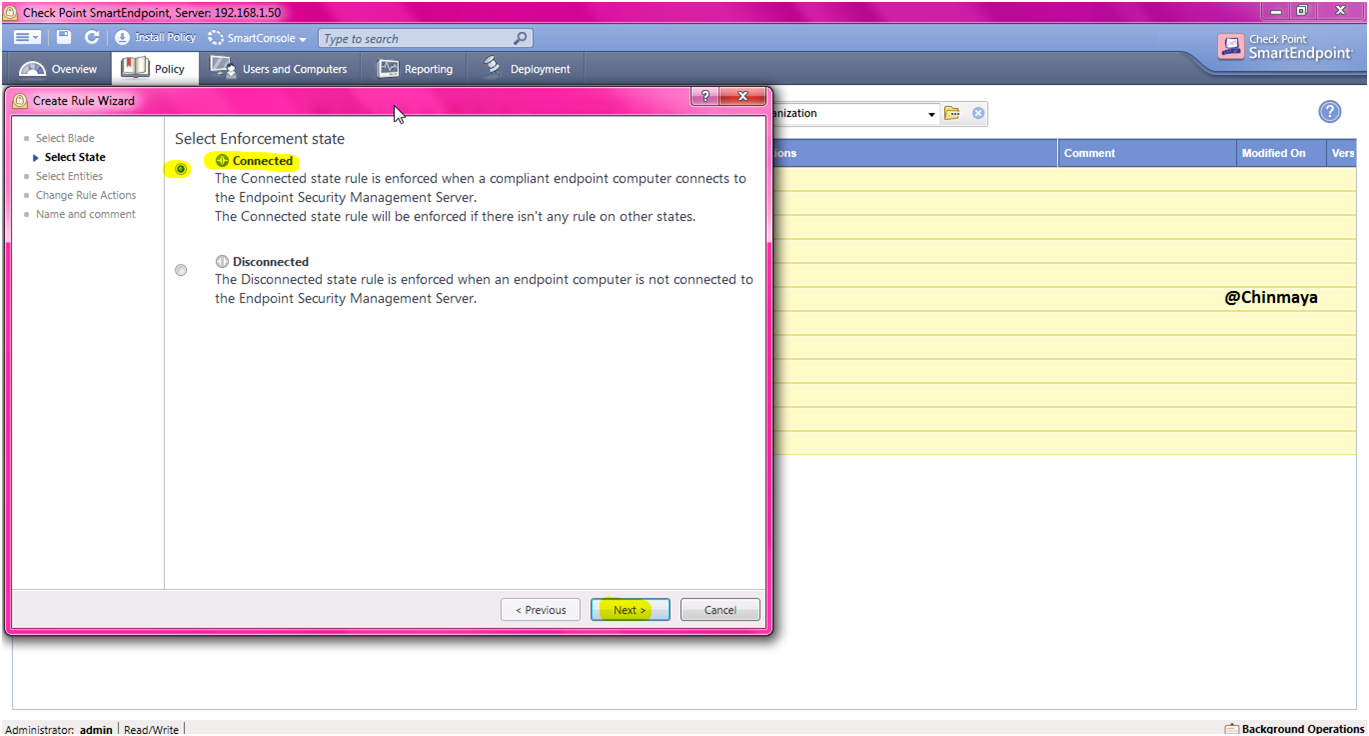
STEP: Select “Connected” and click “Next”.
STEP: Select the Hostname (Windows 7) and click “Next”.

STEP: Action leave “By Default” and click “Next”.
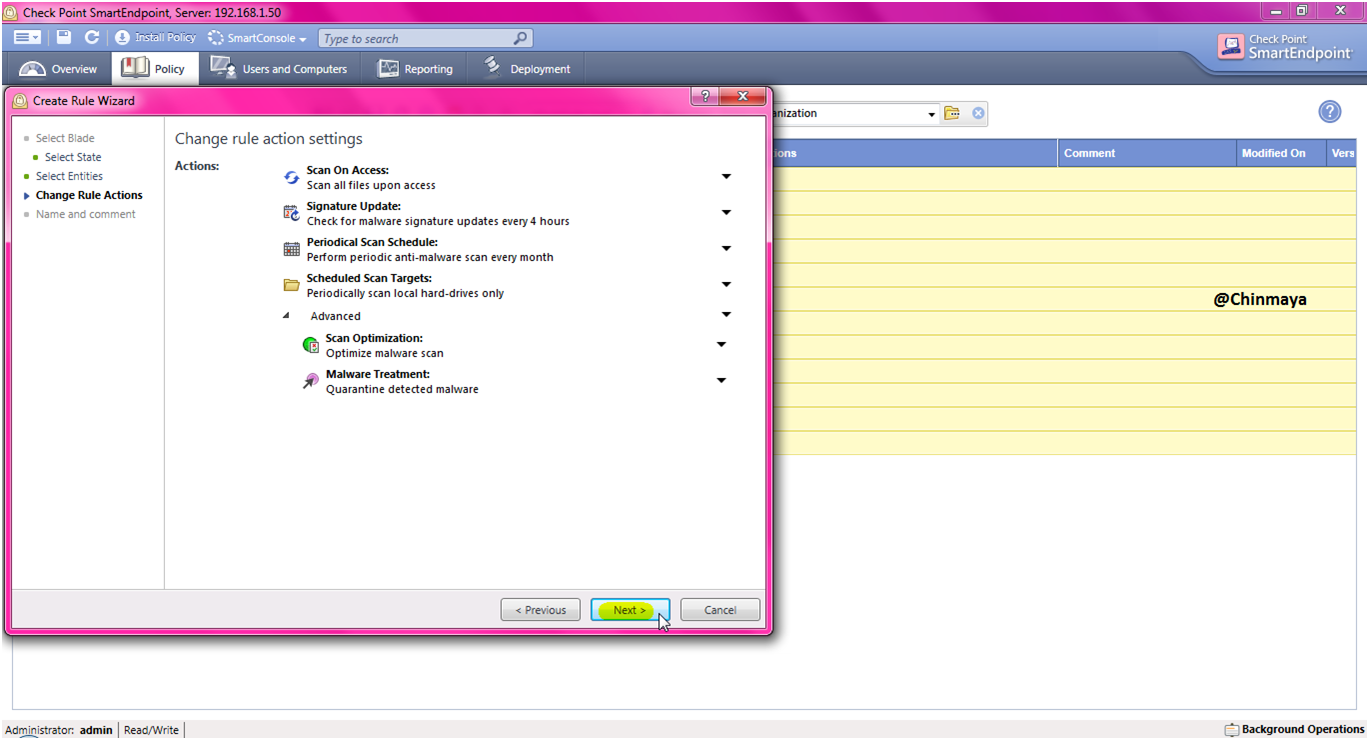
STEP: Give a policy name “CheckpointEngineer_Test_Policy” and click “Finish”.

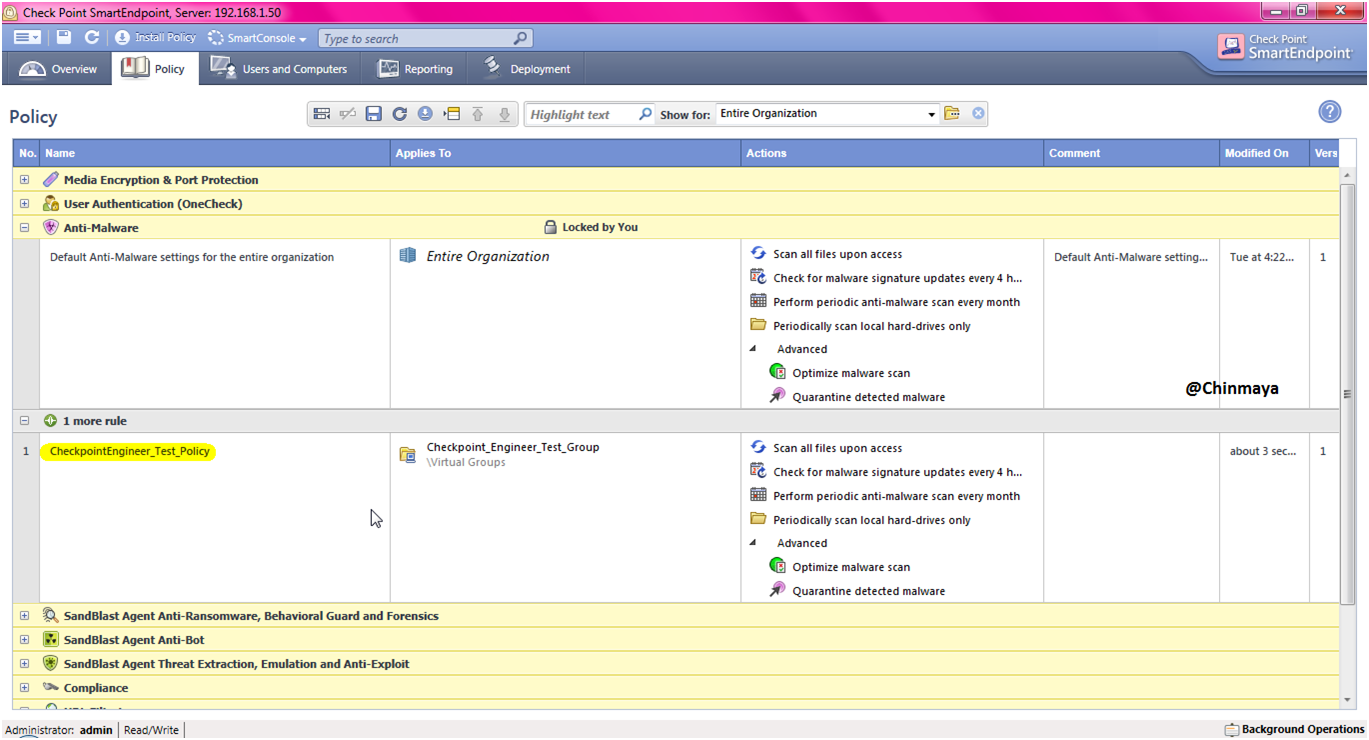
On new policy showing “Check for malware signature updates every 4 hours”.

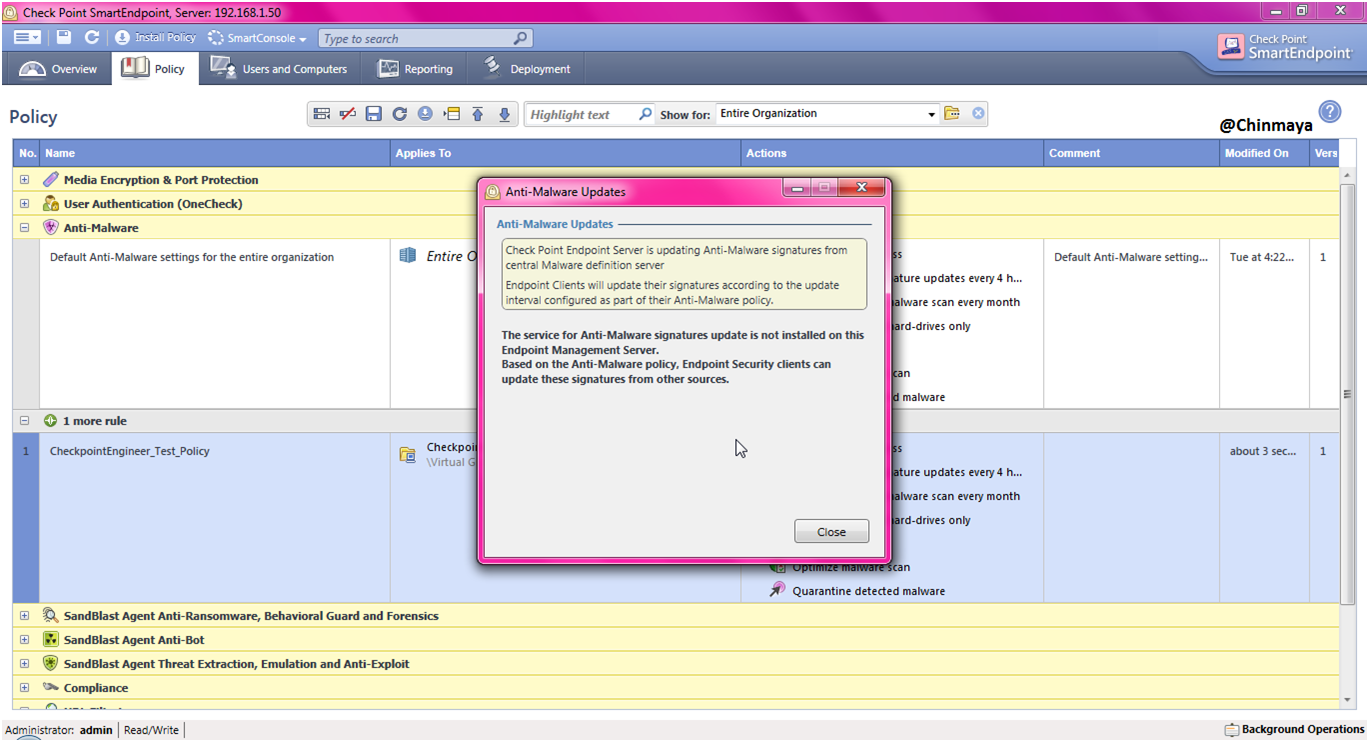
STEP: Now again I am try to update the Anti Malware Updates. Let’s see

STEP: Still showing the same error.
NOTE : Still I am not give internet access to the Endpoint Server but as per the error its seem to be a different issue.
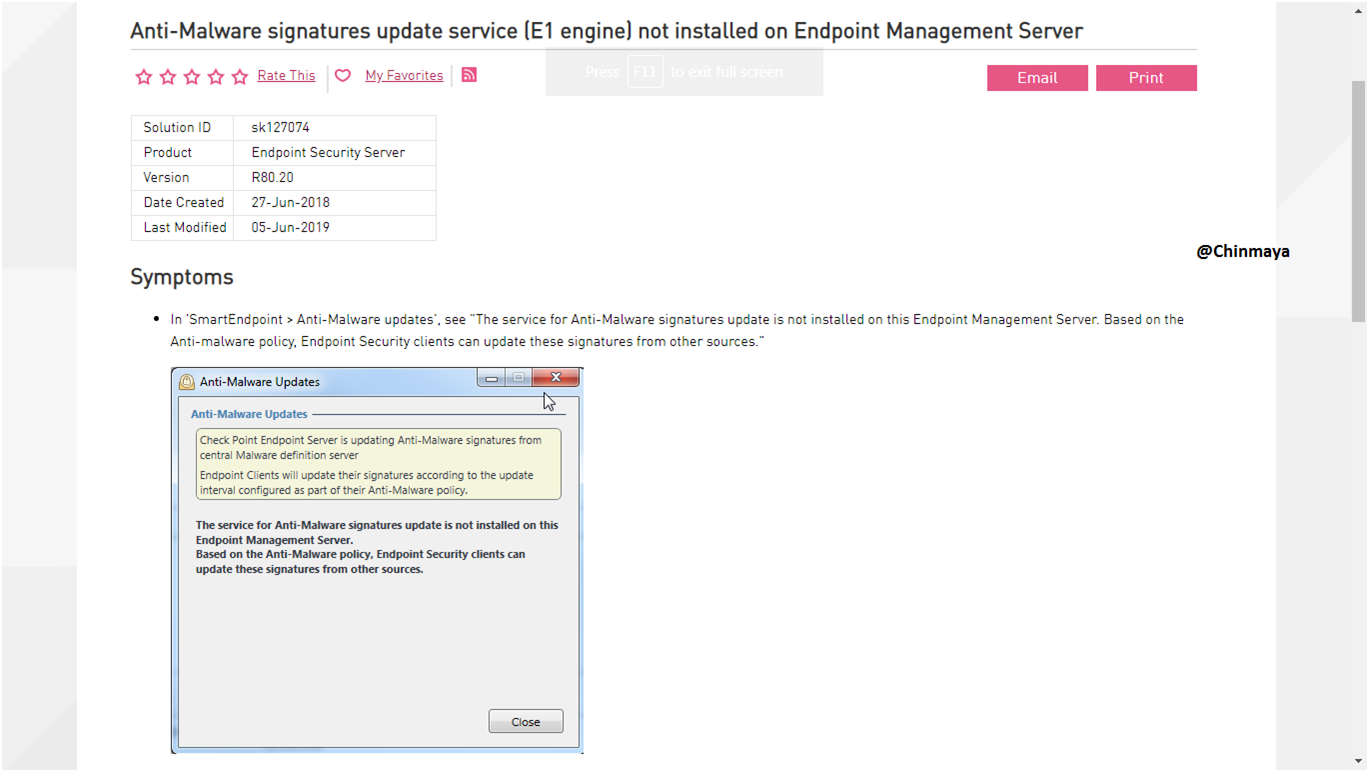
STEP : Refer sk127074 for the Anti Malware update issue.
As per the sk127074 we need to install the dedicated HotFix.This Anti-Malware not required reboot.
NOTE: It will always be good to update to latest Jumbo Hotfix Take then install the Anti-Malware Fix.
STEP: Download the package.
File Name:Check_Point_EP_AM_updater_T16_sk127074_FULL.tgz
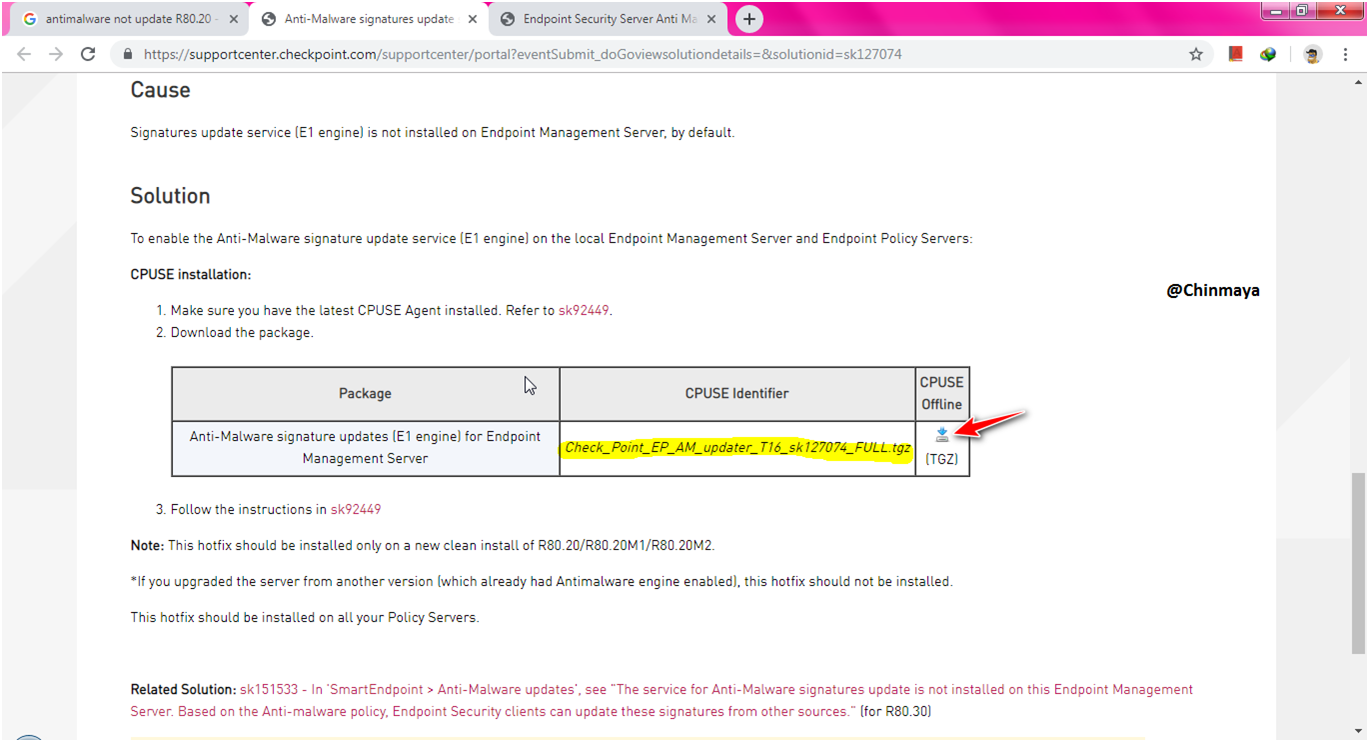
STEP: Note down the MD5 value and after download this package verify the MD5 using any MD5 verifier tool.
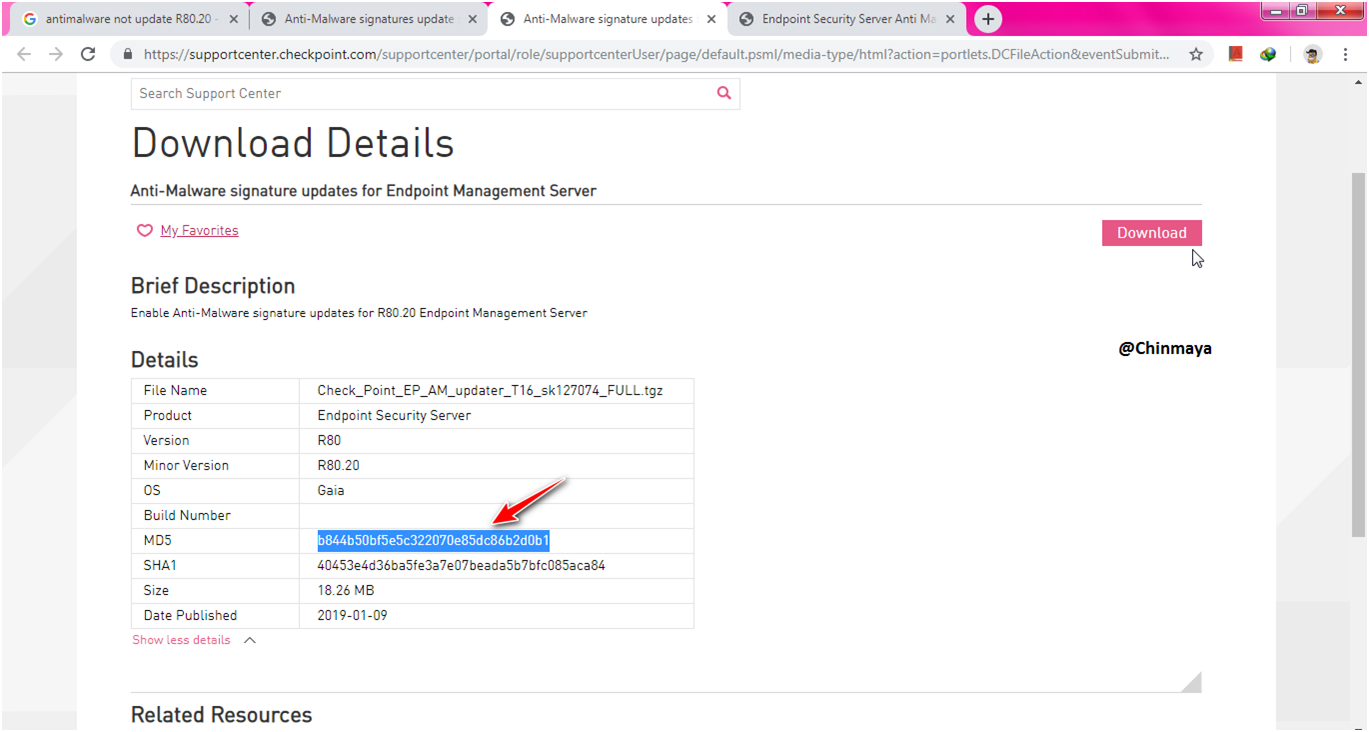
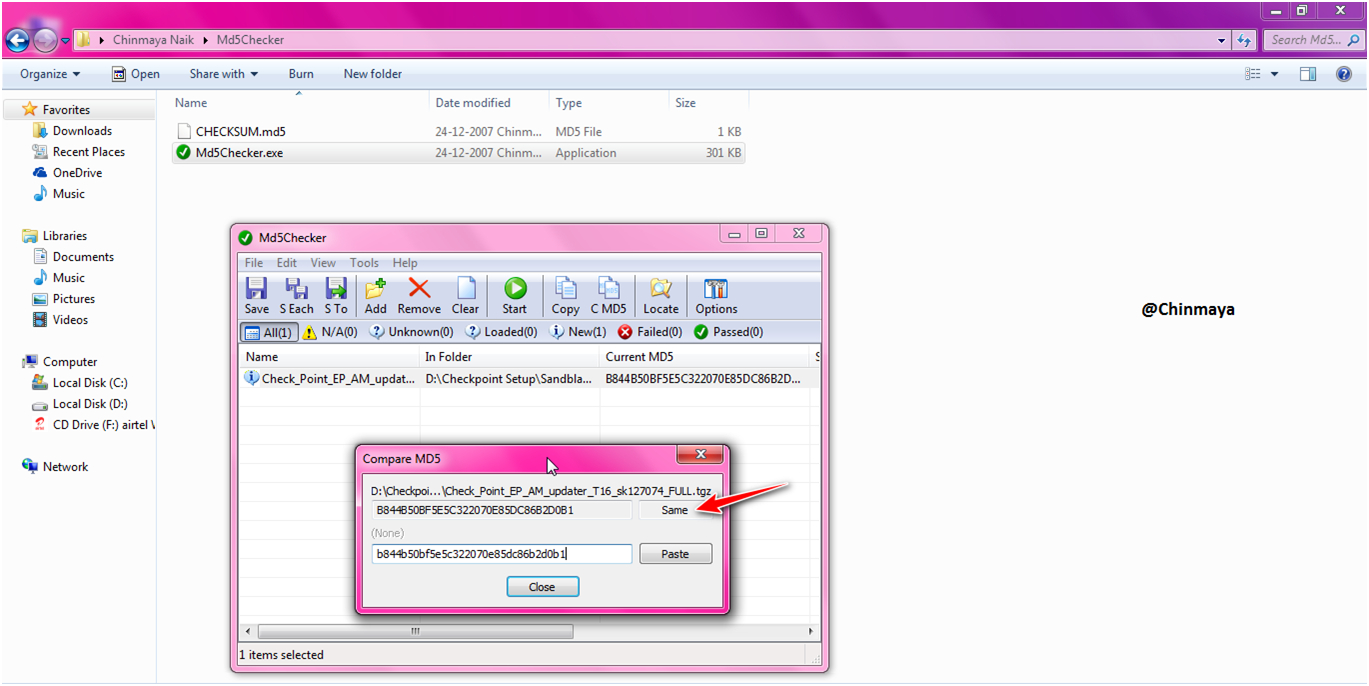
STEP: I am using MD5 checker and its showing “same” so no issue with downloaded package.
STEP: Login to access the GAIA WebUI to install the HotFix using CPUSE.
STEP: GAIA WebUI ---> Status & Action ---> Import Package ---> "Select the Anti-Malware Package"
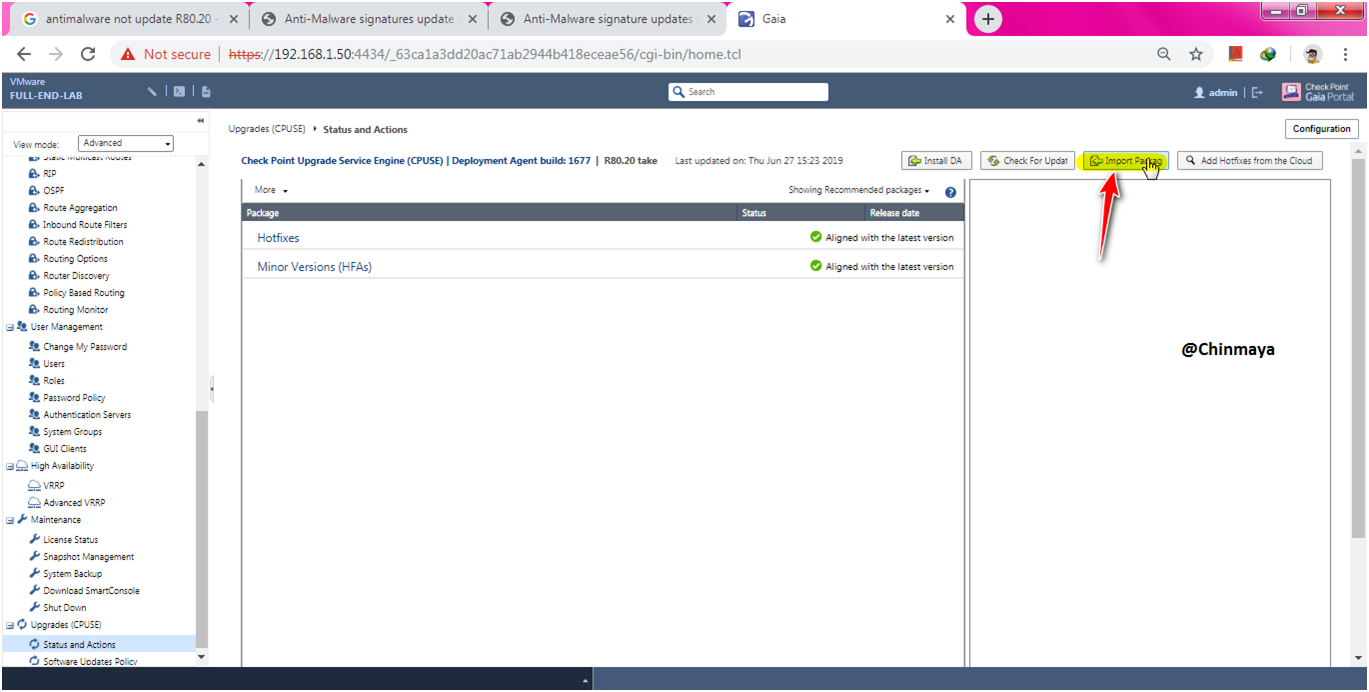
STEP: Browse the “Anti-Malware” package.
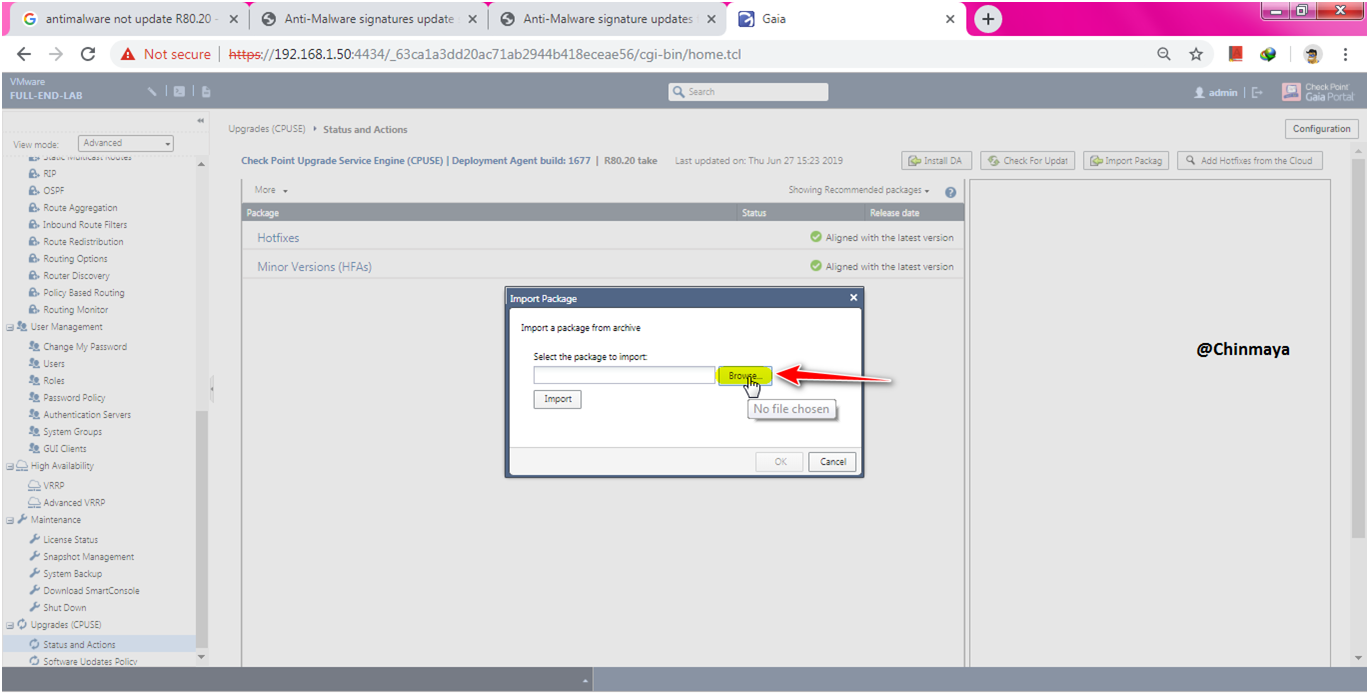
STEP: Click “Import”.

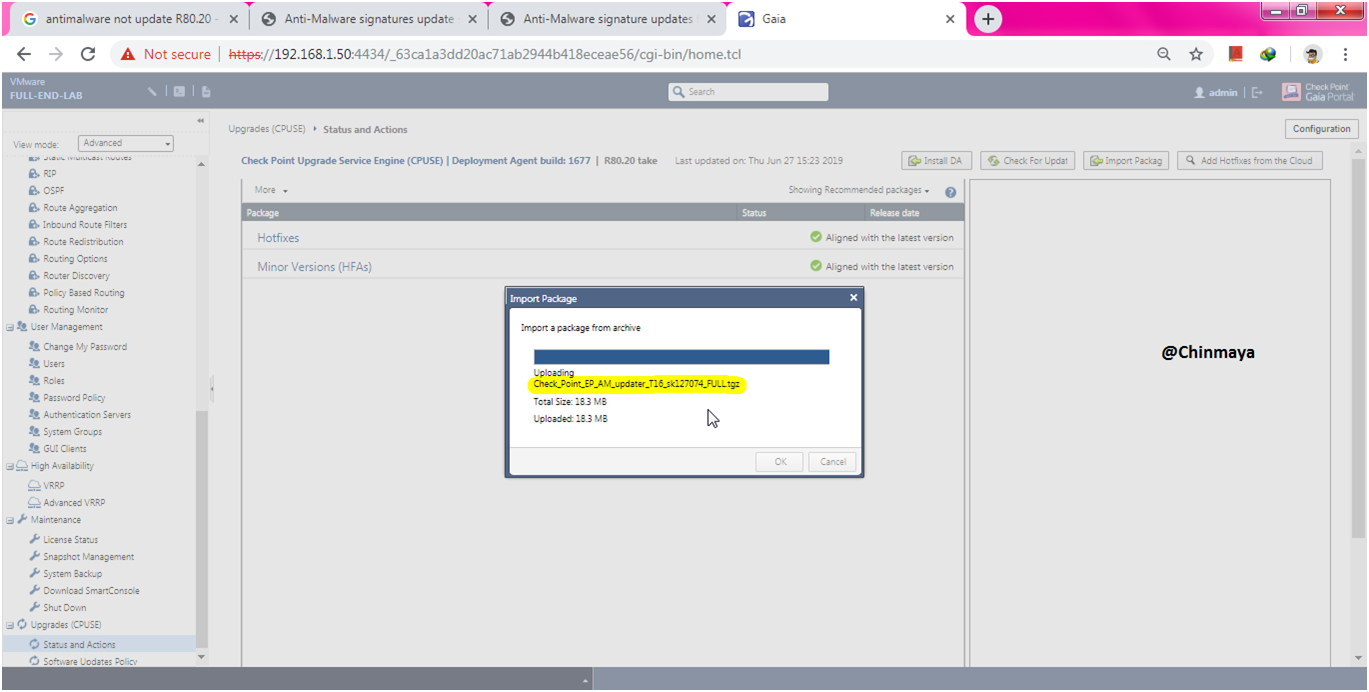
Package Import Successfully.
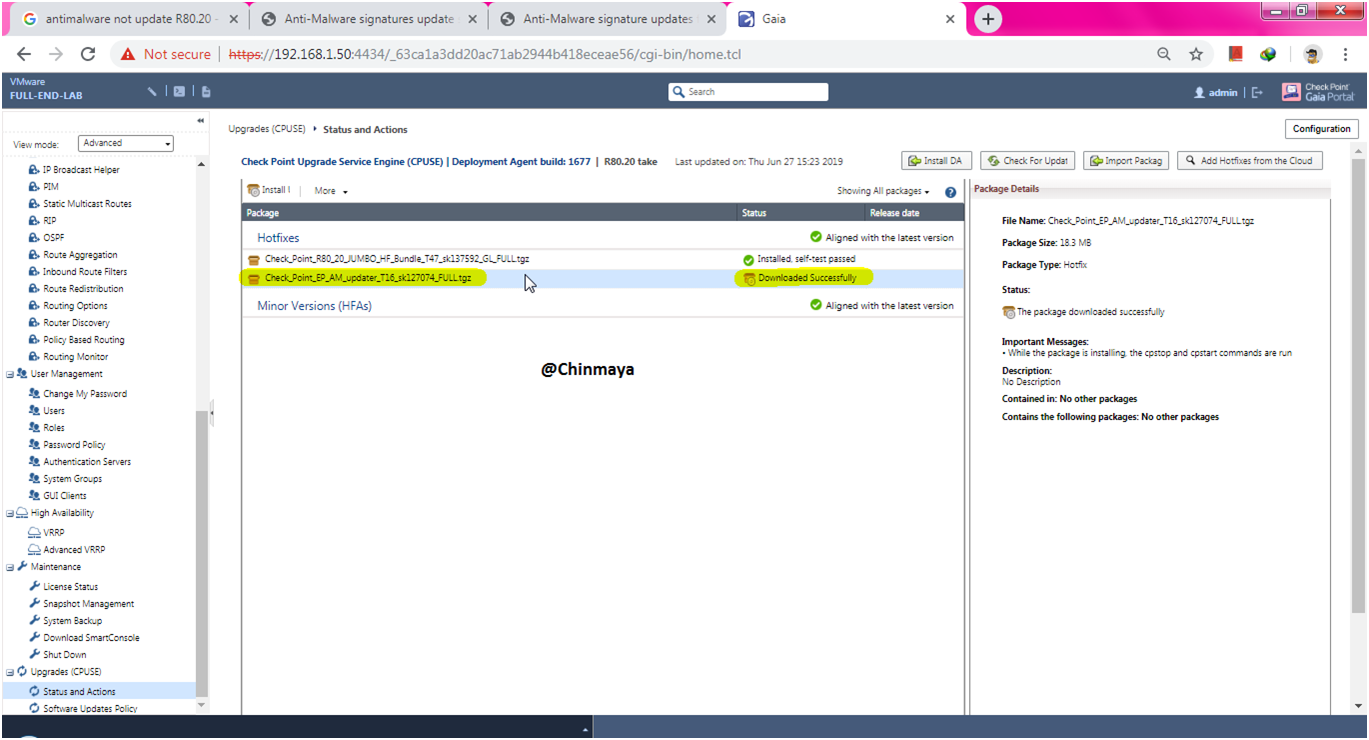
STEP: Right click and verify.
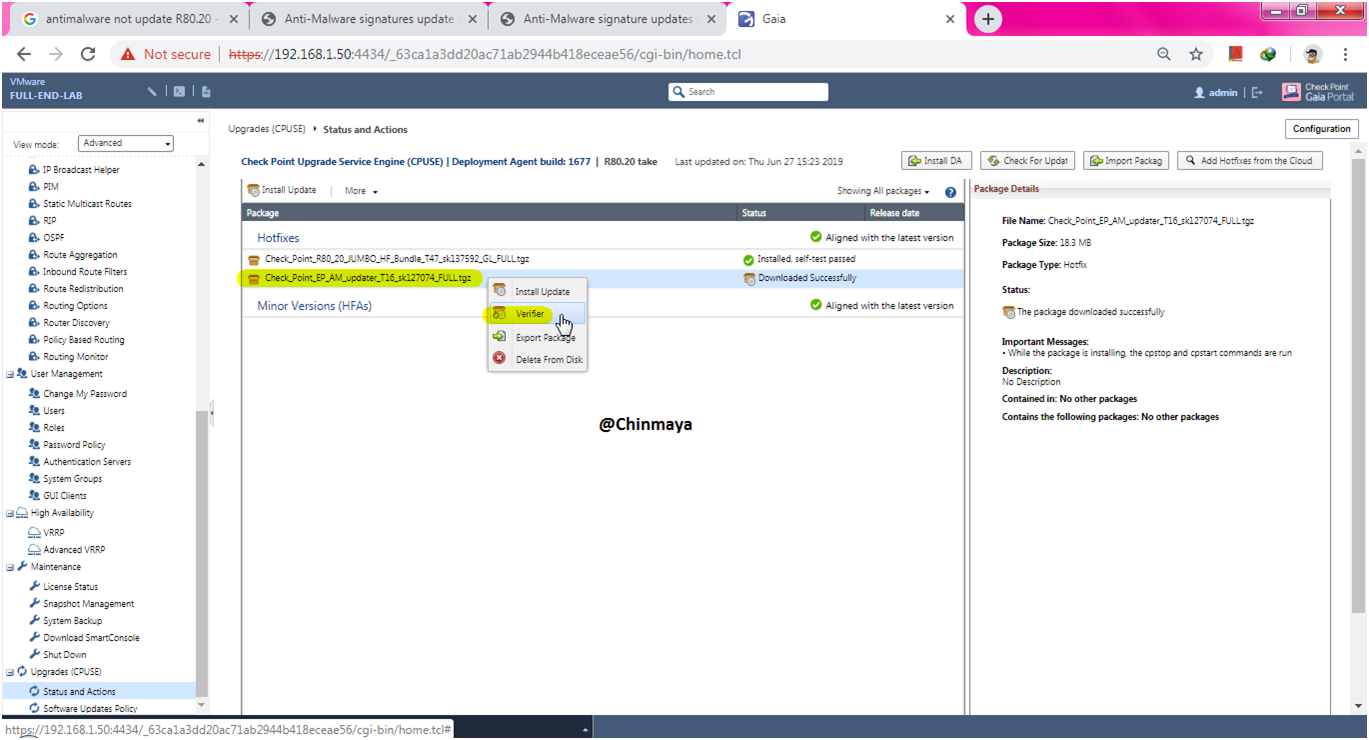
Verify successfully.

STEP: Right click package and click “Install”.

Install the successfully.

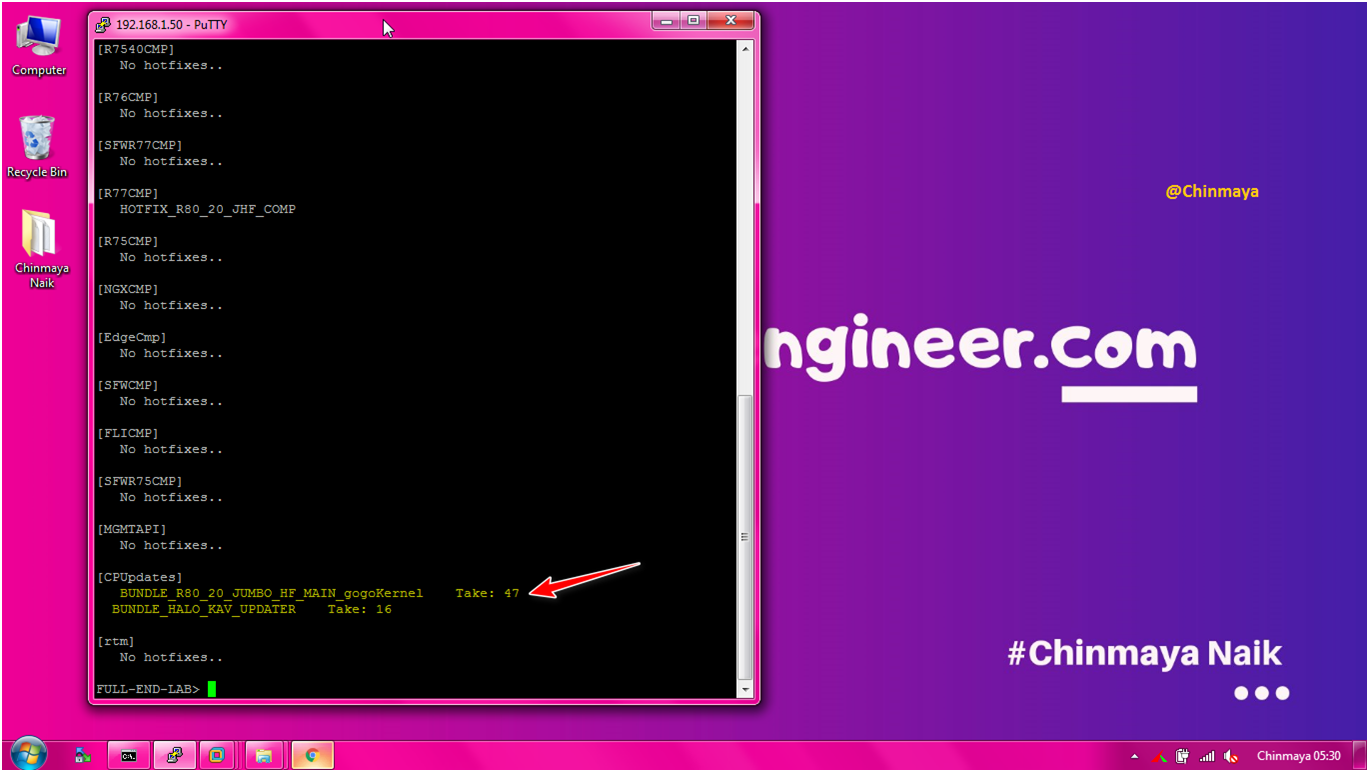
STEP: Verify the HotFix installation via CLI.
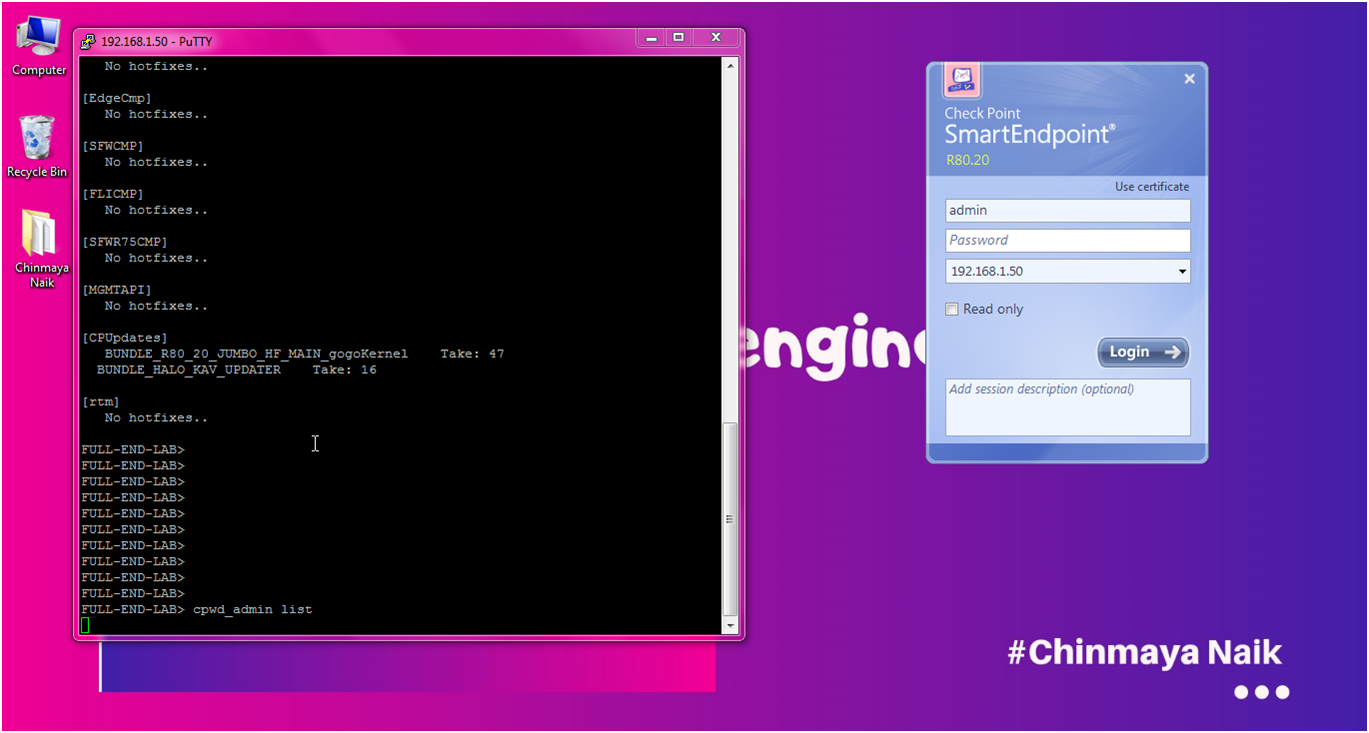
STEP: Give credentials and login to Smart Endpoint.
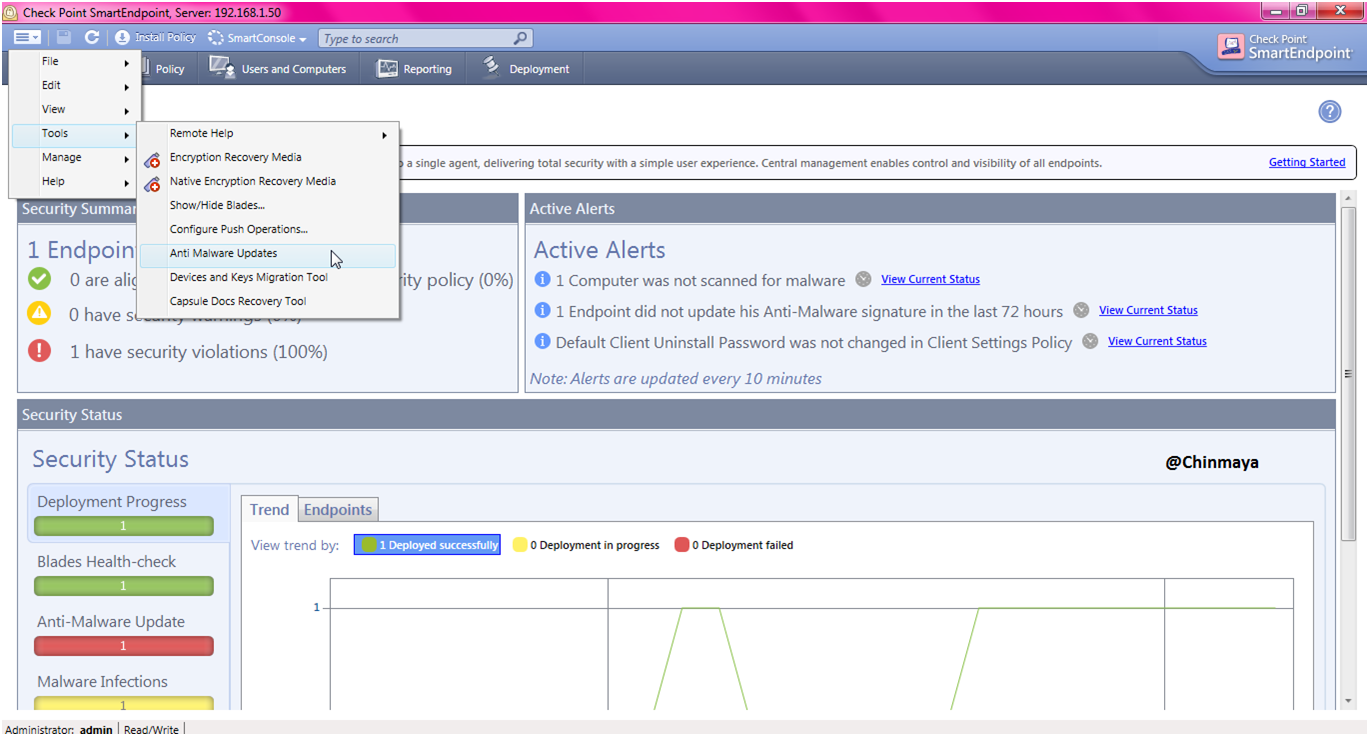
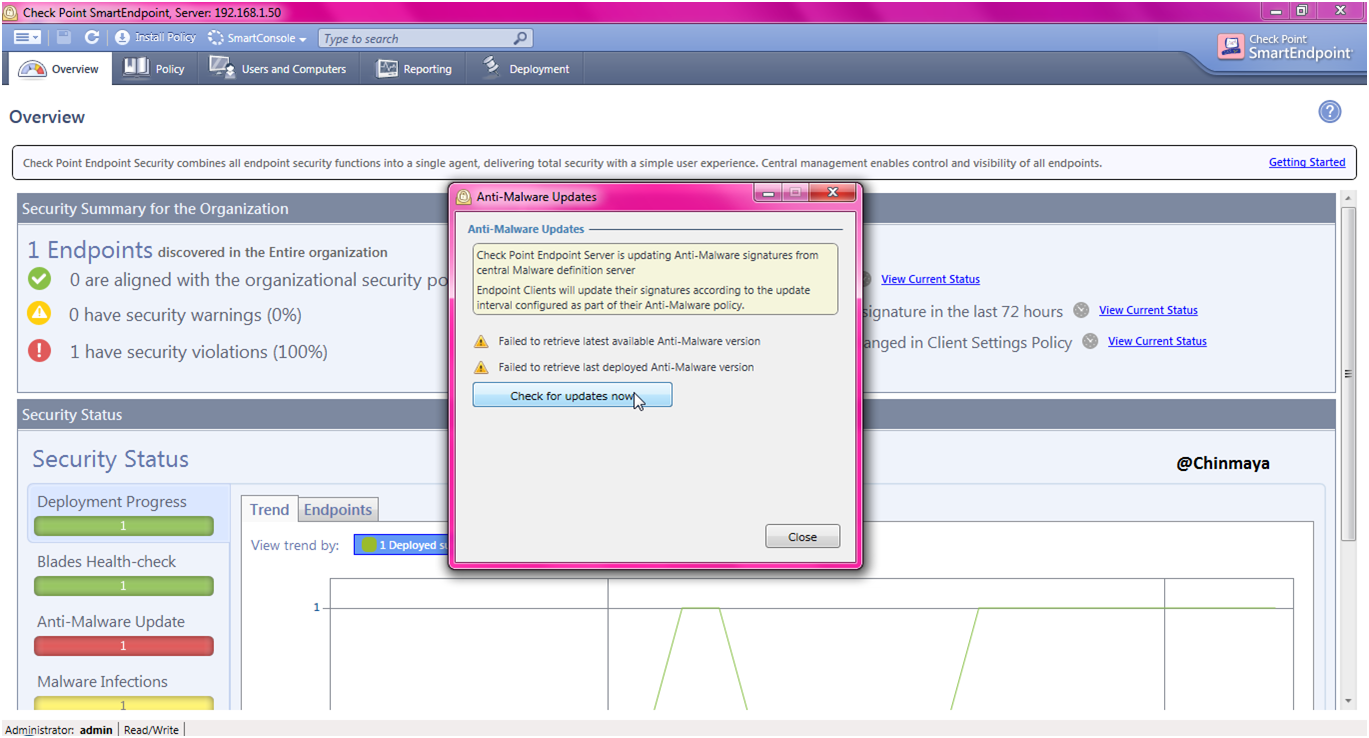
STEP: Now we see the different error.
This is basically error for not having internet access for SmartEndpoint. So we need to create a rule to access internet for SmartEndpoint.
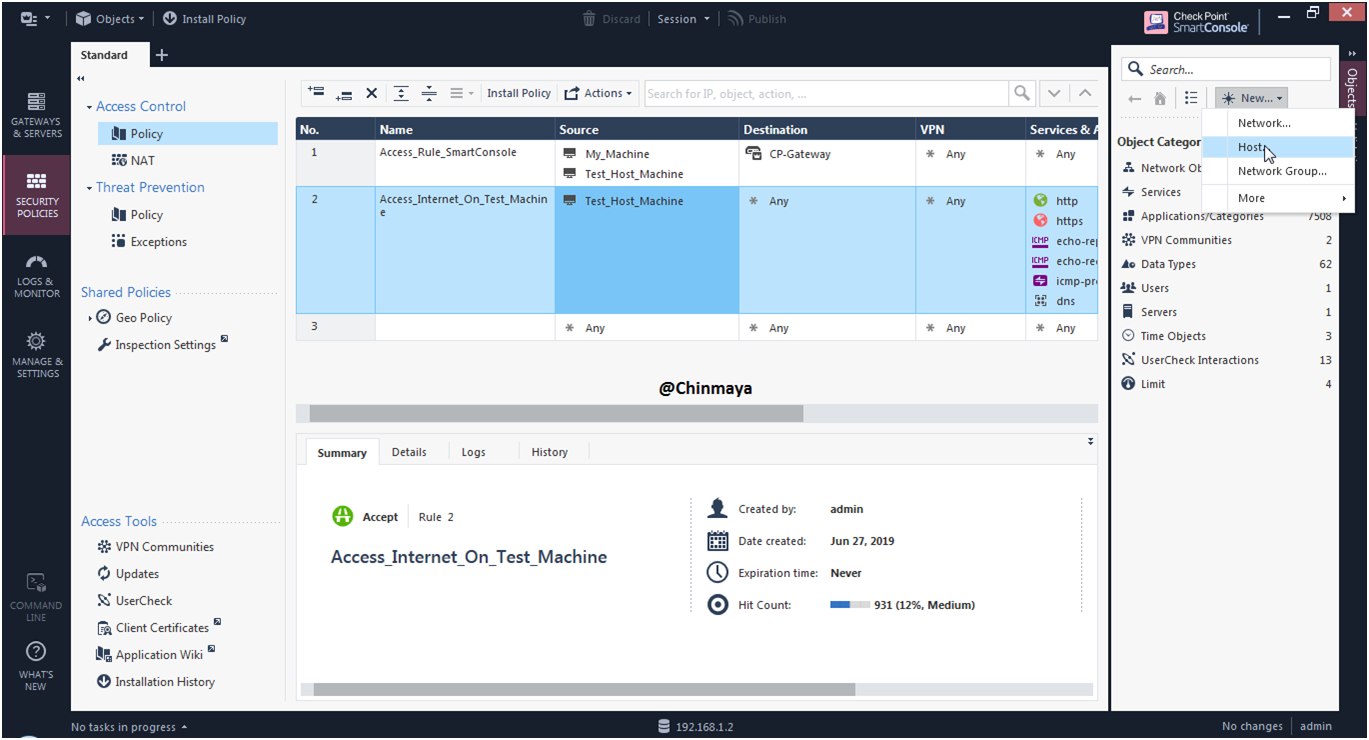
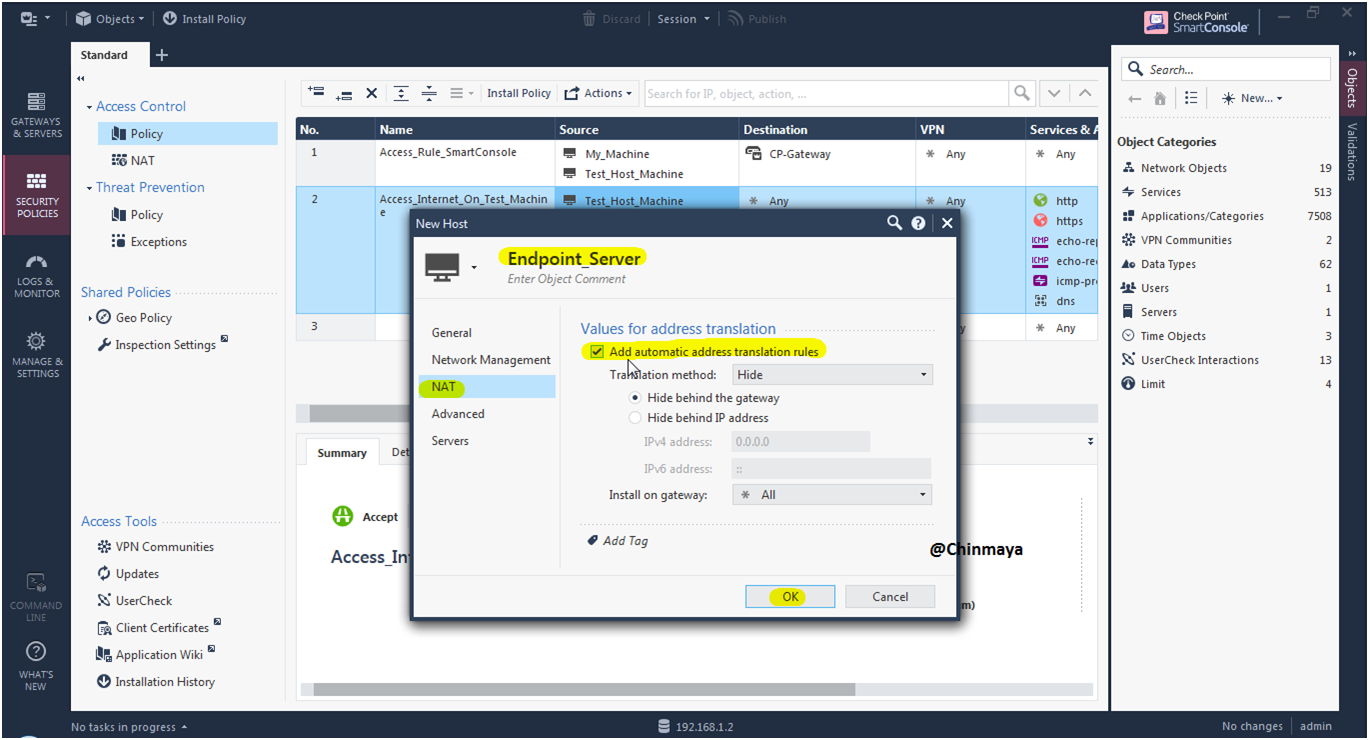
STEP: Create a Host object for Endpoint Server .
Name: Endpoint_Server IP : 192.168.1.150 (/24)

STEP: On net section Select “Hide NAT”.
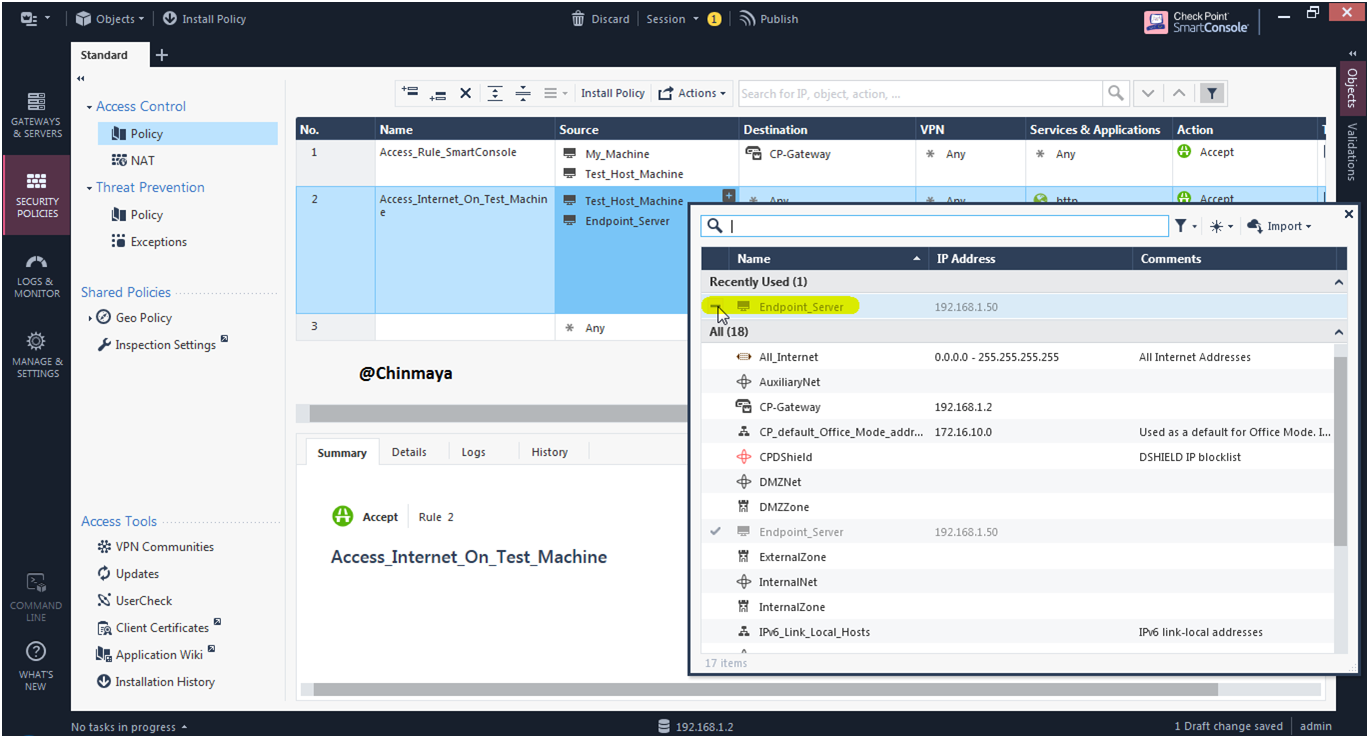
STEP: Below is the rule that I added for Endpoint Server to access internet.
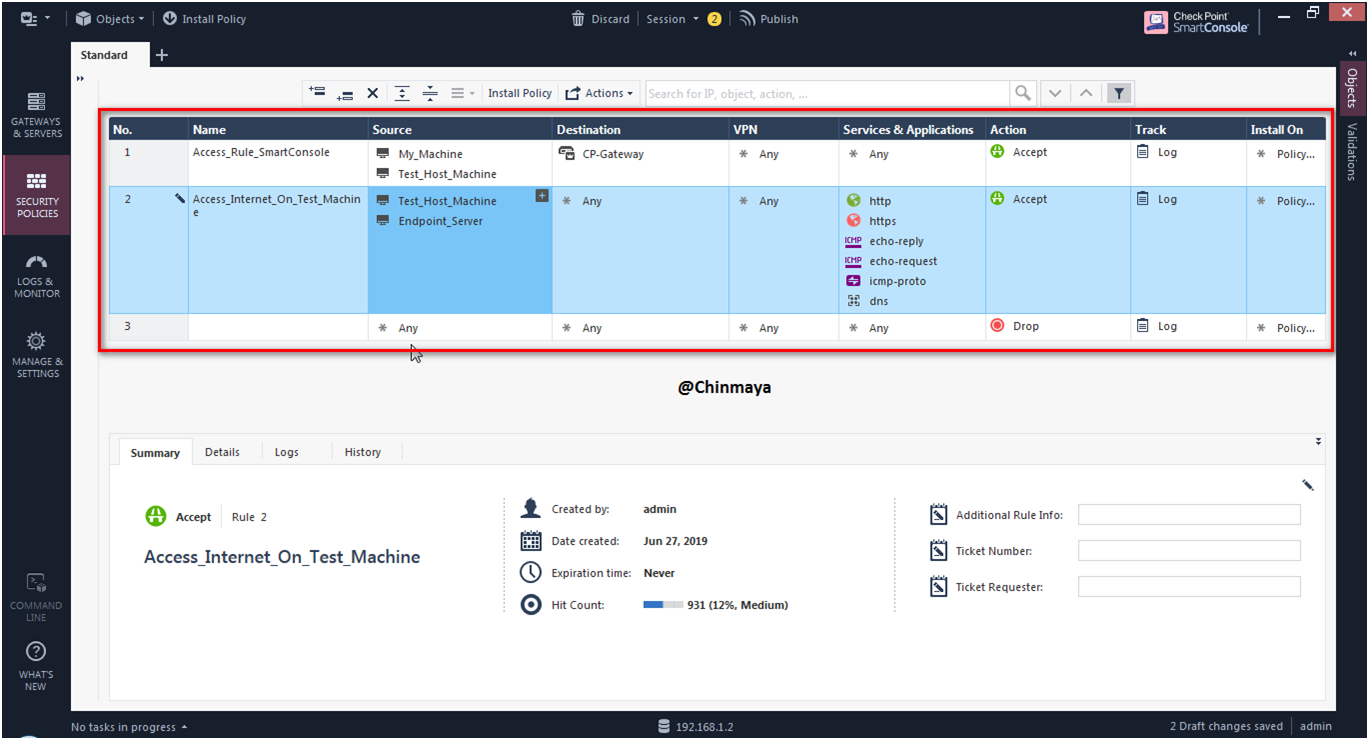
STEP: Install the policy .
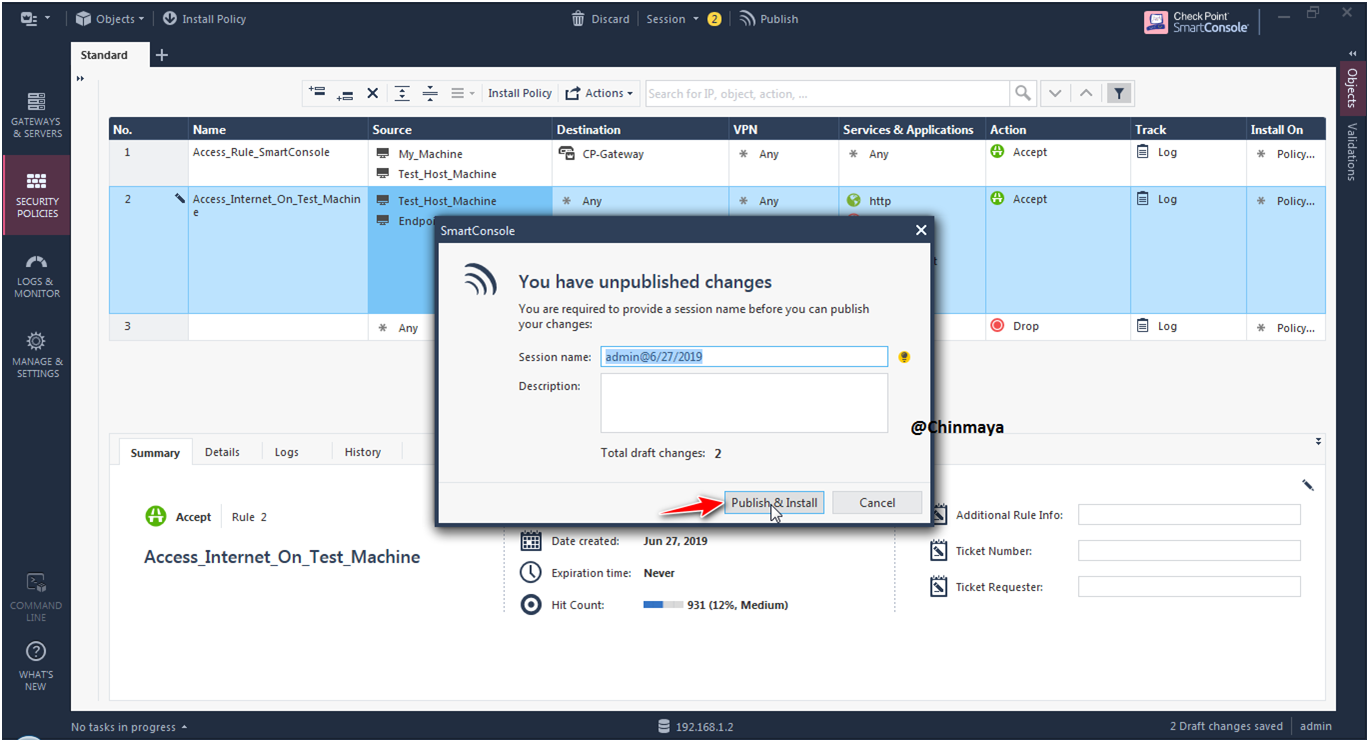
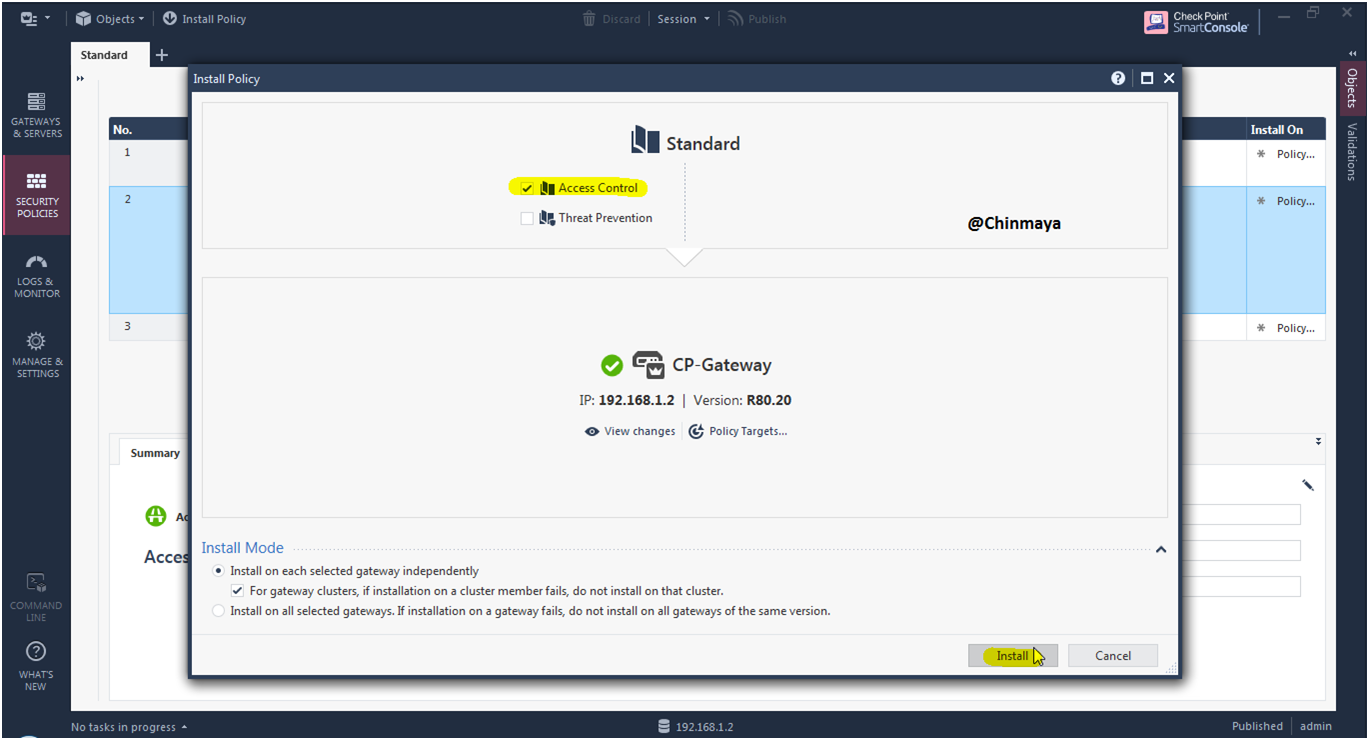
Installed successful.

STEP: Assign the DNS address to the Endpoint Server (Mgmt) and also add default gateway.
Command:
Endpoint_Sserver_Clish> set dns primary 8.8.8.8
Endpoint_Sserver_Clish> set dns primary 4.2.2.2
Endpoint_Sserver_Clish> set static-route default nexthop gateway address 192.168.1.2 on
Endpoint_Sserver_Clish> save config
We able to ping the default gateway 192.168.1.2 and also DNS 8.8.8.8 successfully.
STEP: SmartEndpoint ---> Menu ---> Tools ---> Anti-Malware Updates

Now its start processing.

DONE…..






Leave a Reply