| Document ID | CPENG 06 |
| Product | Security Gateway |
| Version | For Both R80/R81 |
| OS | Gaia |
| Platform / Model | All |
Topology

VM Details Image
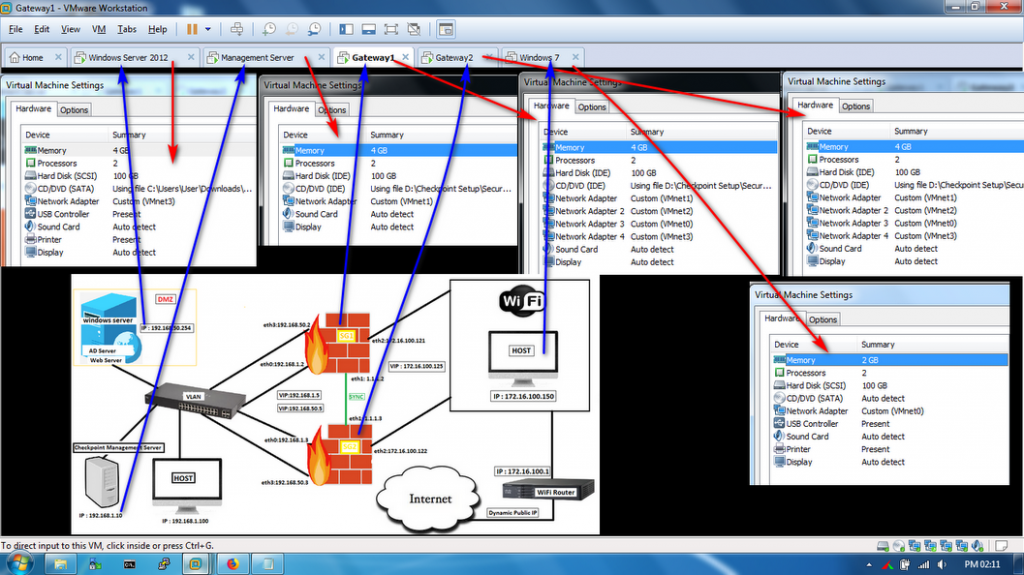
As on above diagram we have an existing Cluster Setup where I am going to do this LAB.
For Configuration of Cluster Setup kindly visit the below link to configure the cluster First :
Cluster Configuration Link
http://checkpointengineer.com/checkpoint-cluster-configuration-r80-20-r80-30-r80-40/
NOTE: We can configure using Cluster or a Single gateway (Distributed Setup) or a standalone setup.
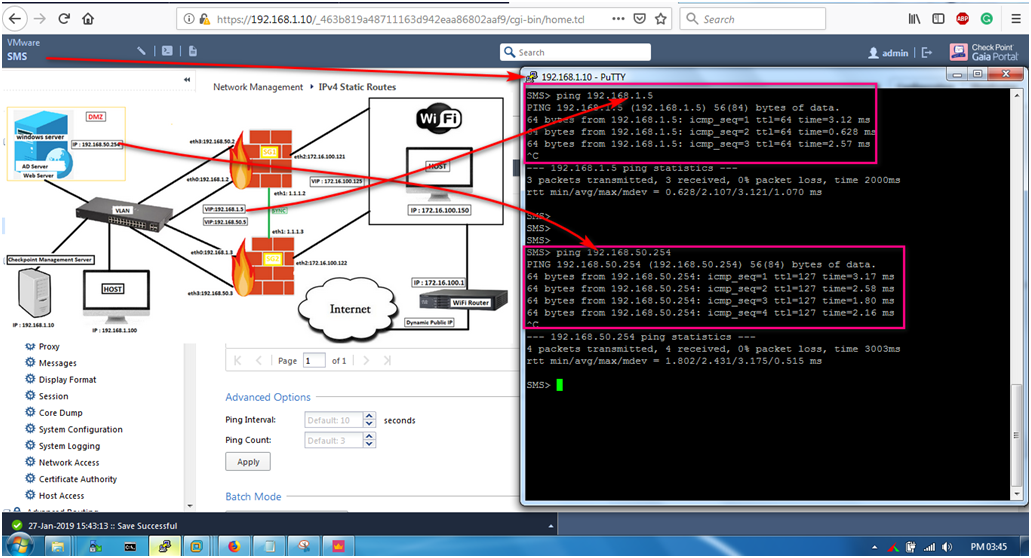
As per the above diagram we have total four different networks which required 4 VMnet (Vmware Networks) .
VMnet1 : 192.168.1.0/24
VMnet2 : 1.1.1.0/24
VMnet3 : 192.168.50.0/24
VMnet0 : (Auto Bridge) 172.16.100.0/24
We only focus on AD integration in this post.
Now we are build a ADserver using Windows Server so we basically we give a dedicated location (DMZ network) as 192.168.50.0/24 and assign IP address of ADserver as 192.168.50.254/24.
IP Address Details
Gateway 1 (Active) IP : Internal (eth0) –> 192.168.1.2/24 | External (eth2) –>172.16.100.121/24
Gateway 2 (Standby) IP : Internal (eth0) –> 192.168.1.3/24 | External (eth2) –>172.16.100.122/24
Cluster VIP (Virtual IP) : Internal –> 192.168.1.5/24 | External –> 172.16.100.125/24
Sync IP : Active Gateway (eth1) —> 1.1.1.2/24 || Standby Gateway (eth1) —> 1.1.1.3/24 (NO VIP Required)
DMZ Network(AD Server)
Gateway 1 (Active) IP : Internal (eth3) –> 192.168.50.2/24 | External (eth2) —>172.16.100.121/24
Gateway 2 (Standby) IP : Internal (eth3) –> 192.168.50.3/24 | External (eth2) —>172.16.100.122/24
Cluster VIP (Virtual IP) : Internal –> 192.168.50.5/24 | External –> 172.16.100.125/24
Management Server IP : 192.168.1.10/24
AD Server IP : Internal IP —> 192.168.50.254/24
Route
Internal LAN (192.168.1.0/24) —-> Default Gateway (VIP : 192.168.1.5/24)
DMZ Network (192.168.50.0/24) —–> Default Gateway (VIP : 192.168.50.5/24)
Gateway IP (172.16.100.121/24 & 172.16.100.122/24) —> Default Gateway (VIP:172.16.100.1/24)
Host Machine (Where VMware is installed) —> 192.168.1.1/24
VMNet Details
VMnet0 : Auto-Bridging : External : 172.16.100.0/24
VMnet1 : Host-Only : Internal : 192.168.1.0/24
VMnet2 : Host-Only : Sync : 1.1.1.0/24
VMnet3 : Host-Only : DMZ Network : 192.168.50.0/24
After configure this above we see that Ad Sever (192.168.50.254) have Default Gateway (192.168.50.5) so ADserver is able access to the Cluster Gateway but the MGMT server not able to reach to the ADServer because MGMT Server did not not have any route to reach so we are going to add a static-route default nexthop gateway address for Management Server.
STEP 1 : Add static-route default nexthop gateway address for Management Server as 192.168.1.5/24.
GAIA WebUI of Management Server (192.168.1.10) —> IPv4 Static Routes —> Add Gateway —> IPv4 Address : 192.168.1.5/24.

Default Gateway address is reflected after configuration.
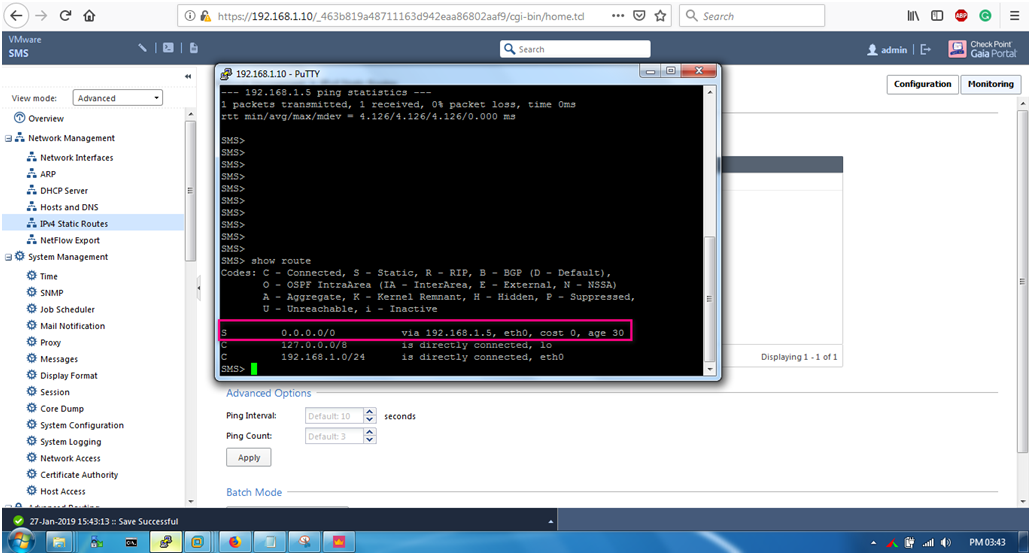
STEP 2 : Verify by using “CLI”.
Command : Clish> show route
We can see that “s (Static) 0.0.0.0/0 via 192.168.1.5, eth0,cost 0,age 30”
STEP 3: Check the MGMT Server IP address . Now we are going to open the SmartConsole with Management Server IP (192.168.1.10/24).

Check the enabled BLADE and as we can see that “Identity Awareness” is not enabled yet so for AD Server integration with Checkpoint then we required to enable this BLADE. but before we enable the Identity Awareness BLADE we need do configure some additional step.

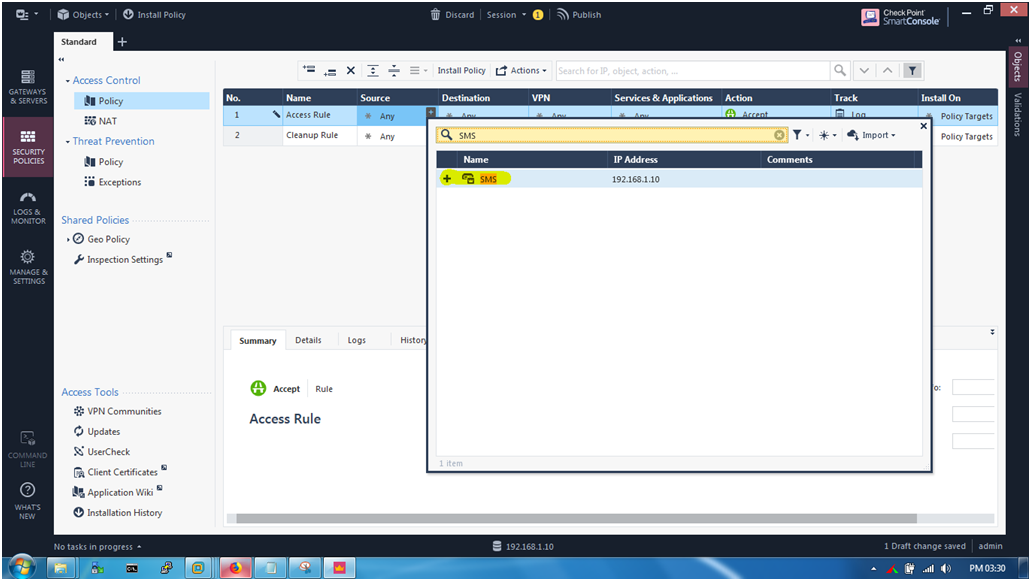
STEP 4: We are going to add source as management server.
Source : “SMS” object.
Destination | VPN | Services & Applications : “any” (Later on we can define Destination as : Ad Server and define the services as well)
Action : “Accept”
Track : “Log”
STEP 5: Installed the security Policy.
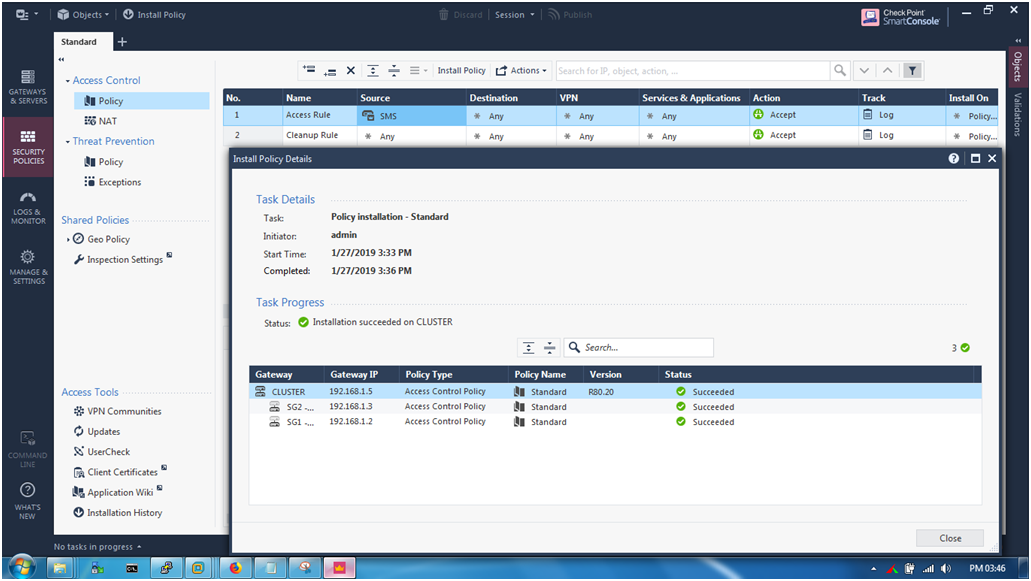
Security Management Server SSH.
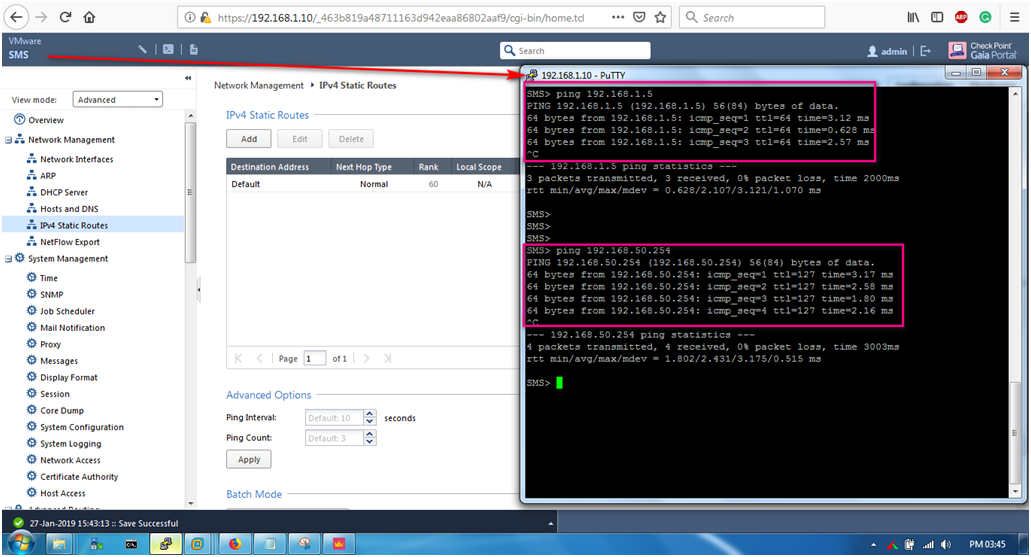
STEP 6: Now we are going to ping the ADServer and Default Gateway.
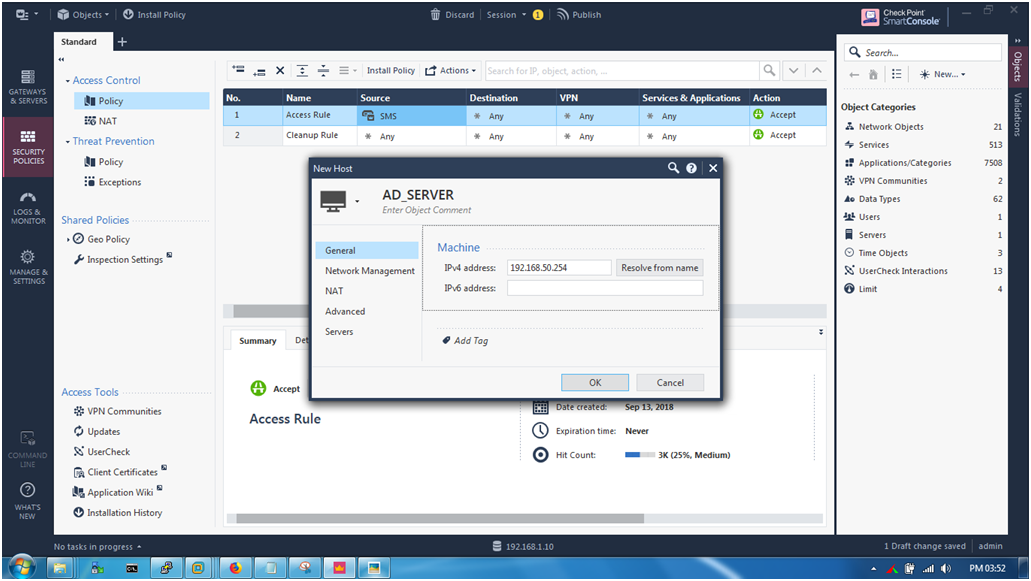
STEP 7: Create a Host object for ADServer , I create a Host object and name as “AD_SERVER”.

STEP 8: On Hostname “AD_SERVER” assign IP address as “192.168.50.254/24” and click “OK”.
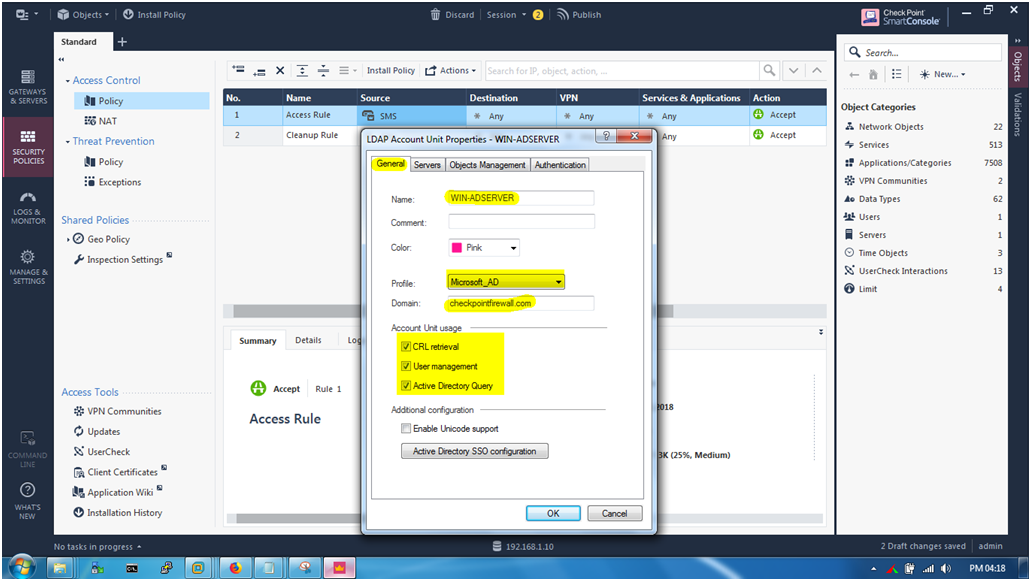
STEP 9: Creating a LDAP Account Unit.
SmartConsole —> More —> Server —> LDAP Account Unit

STEP 10: On LDAP Account Unit Properties.
General
Name : WIN-ADSERVER
Profile : Microsoft_AD
Domain : checkpointfirewall.com (As the same domain we assign in our ADServer)
Account Unit usage —> Select : CRL retrival | User management | Active Directory Query
STEP 11: On “Server” tab click “Add”.
Server —> Add

STEP 12: Now after clicking “Add” option follow below configuration.
HOST : AD_SERVER (Select ADServer Host Name)
PORT : 389
Username : Administrator
Login DN : CN=Administrator, CN=Users, DC=checkpointfirewall, DC=com
(DEFAULT : CN=Administrator,CN=Users,DC=domain,DC=local)
Password : Use the Administrator password
And Leave all by default Like
Default Priority : 1
Select “Read data from this server”
Select “Write data to the server”
Then Click “OK”
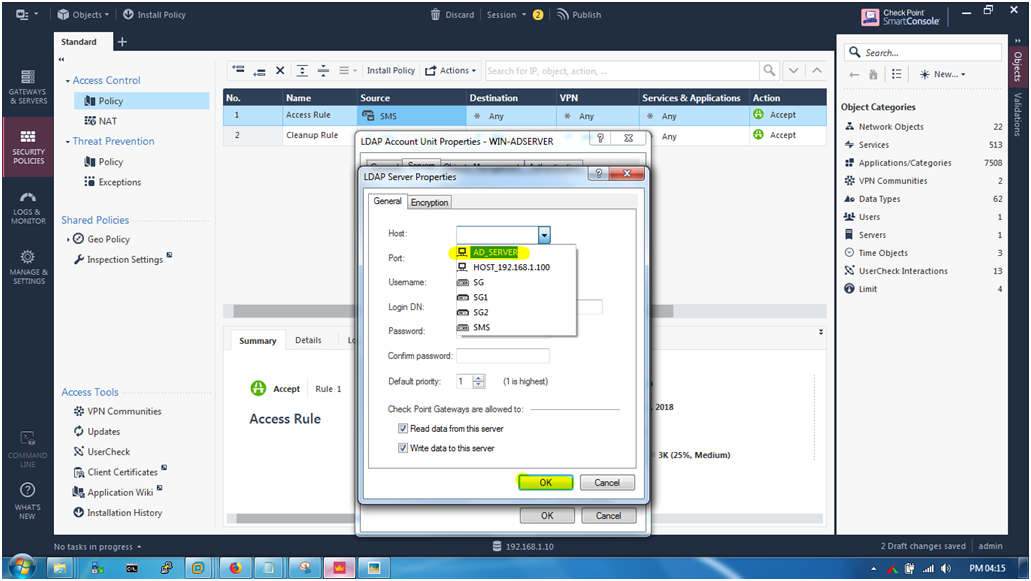
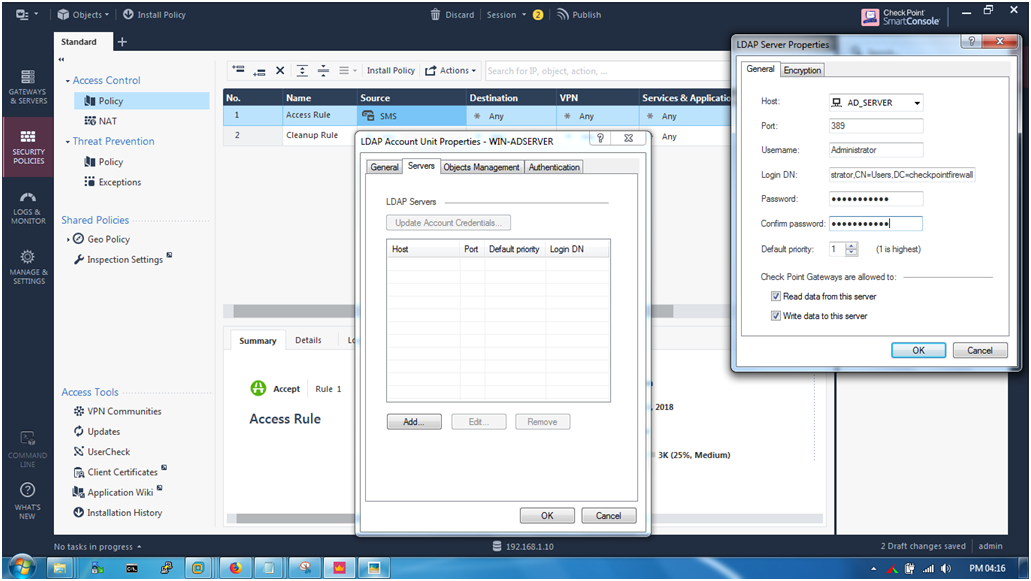
Don’t click “OK” first we need to login with Windows Server first then we going to fetch.

STEP 13: Open the Ad Server.
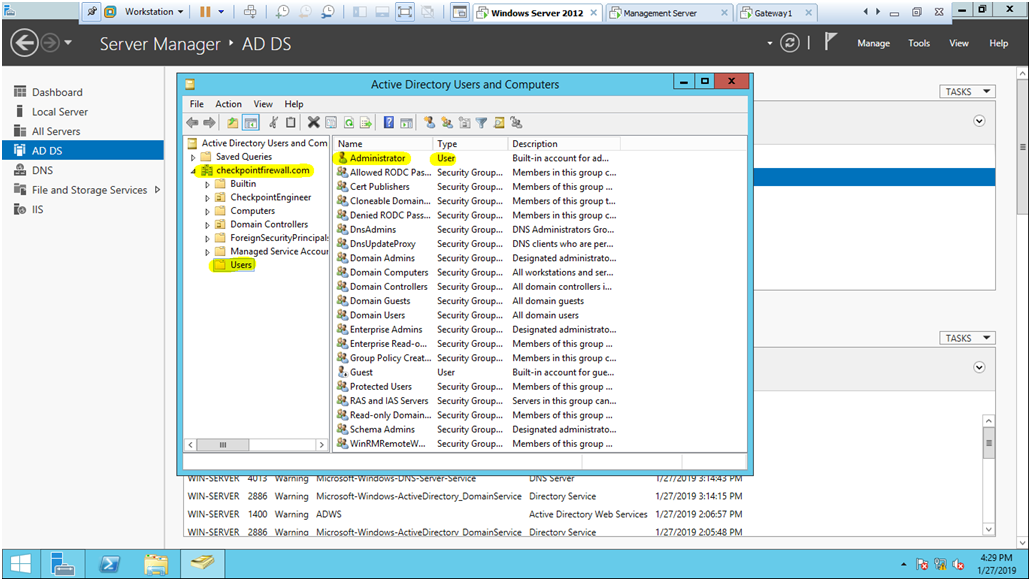
STEP 14: Open the “Active Directory Users and Computers” and check the Administrator name so on my case user Administrator as Administrator only.
Windows Server —> AD DS —> Administrator.
STEP 15: Go to the “Object Management” Tab and Now we click the “Fetch branches”
Fetching Branches is under process
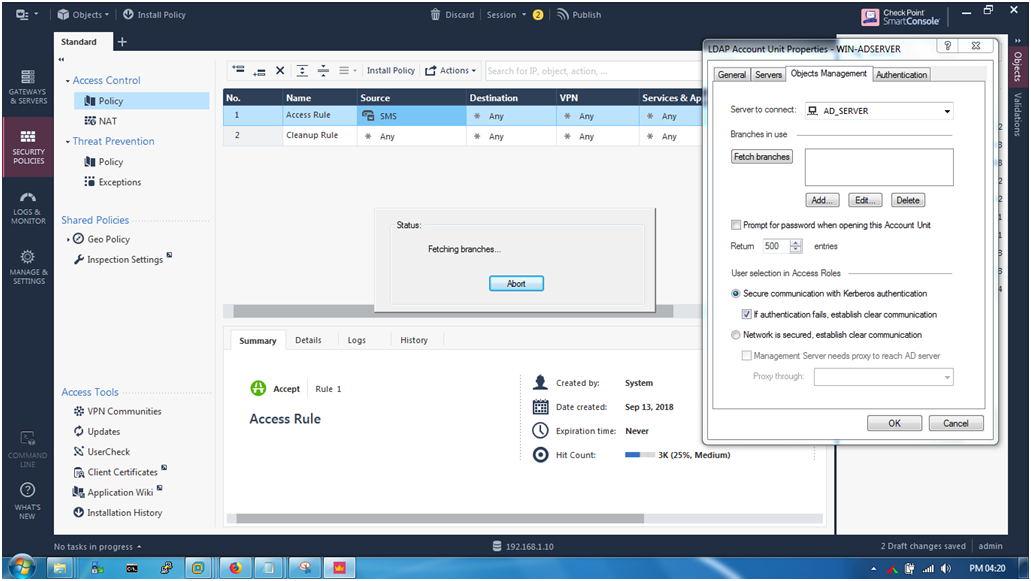
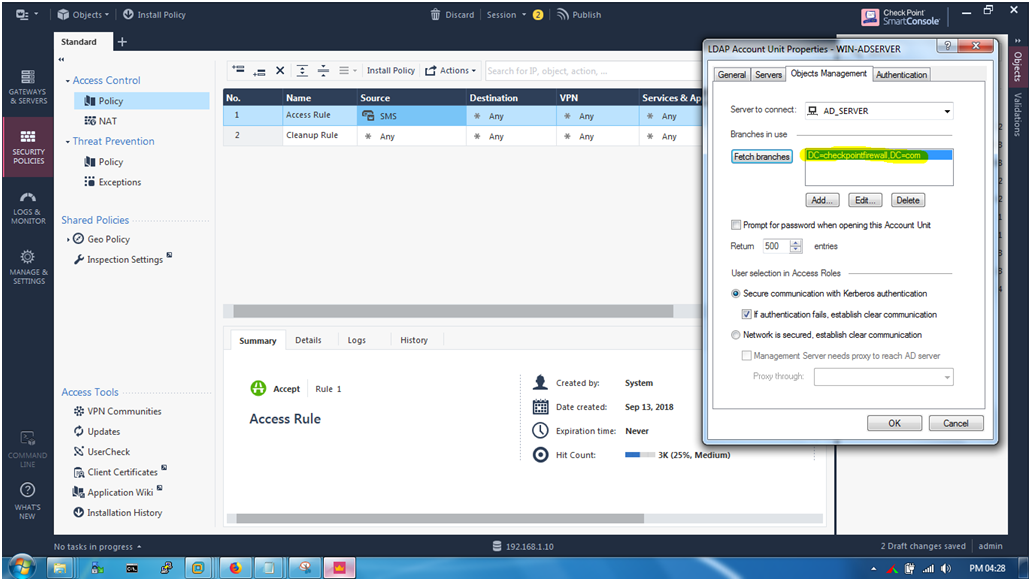
STEP 16: Fetch braches is done successfully , we see that (DC=checkpointfirewall,DC=com).
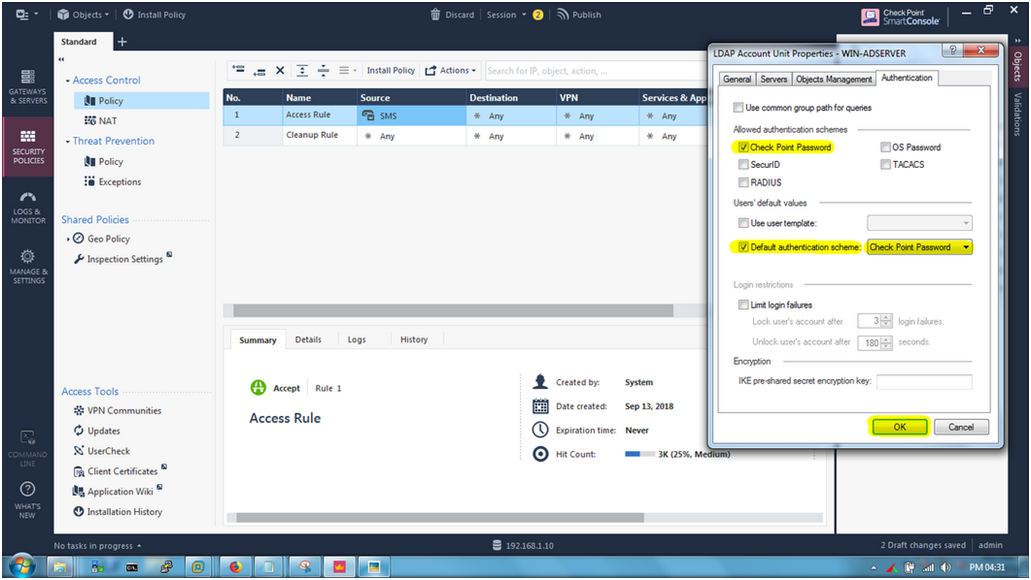
STEP 17: Go to “Authentication” tab and select allowed authentication schemes “Check Point Password”.
Default authentication scheme : “Check Point Password”
And Now we click on “OK”.
STEP 18: Enabled the “Identity Awareness”. Once you enable that BLADE then one Pop UP will come , so select or mark the “AD Query” and click “Next”.

STEP 19: Select the Active Directory. So assign the domain name that will automatically come for select.
Give Username as : Administrator and Password as : ****** and Click “Connect”.
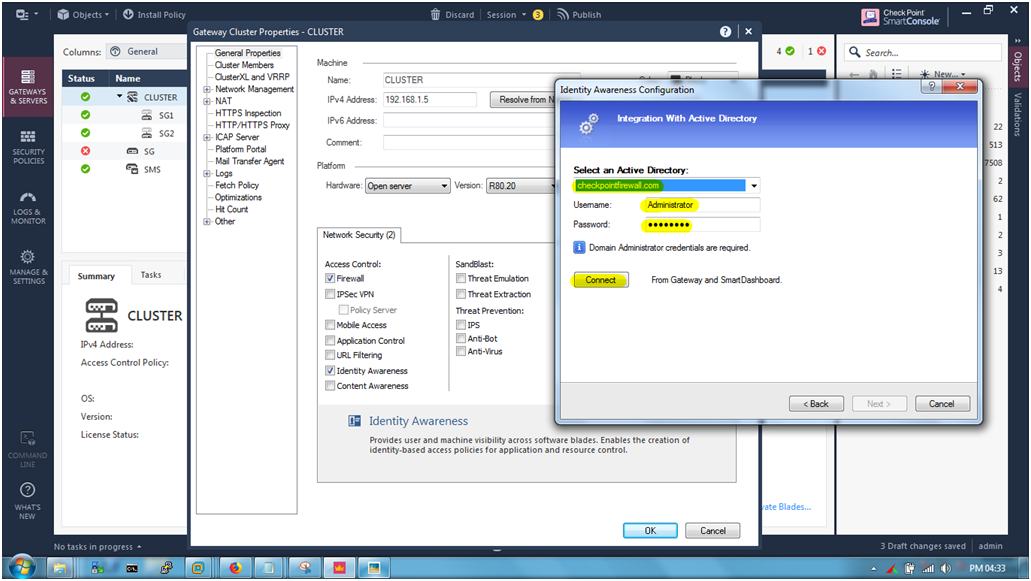
Once its connect to to ADServer then we able to see the message like “Successfully Connected” and click “Next”.
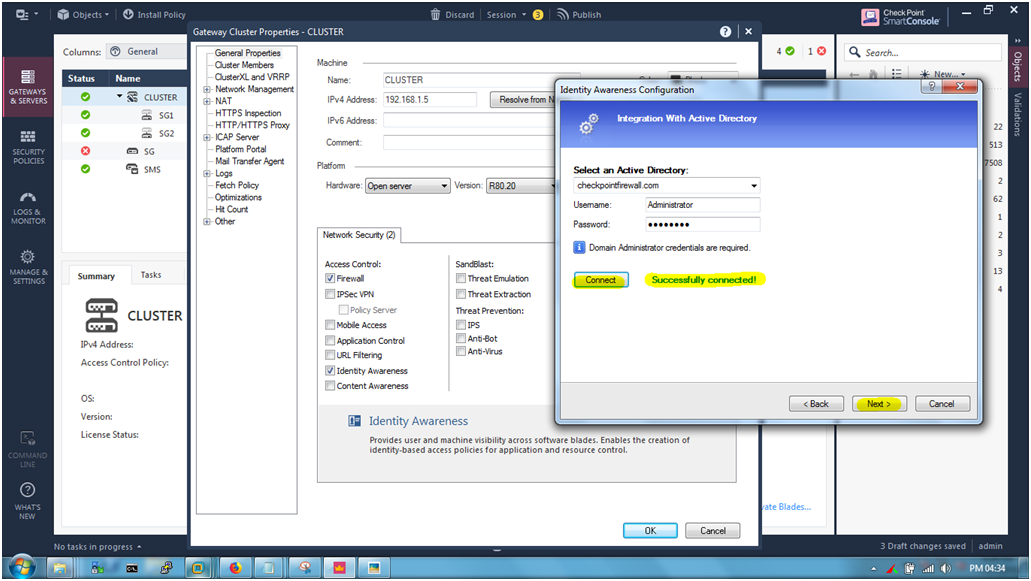
STEP 20: Click “Finish”.

STEP 21: Click “OK”.

STEP 22: Click on “Server” for verify the LDAP account unit is there or not.
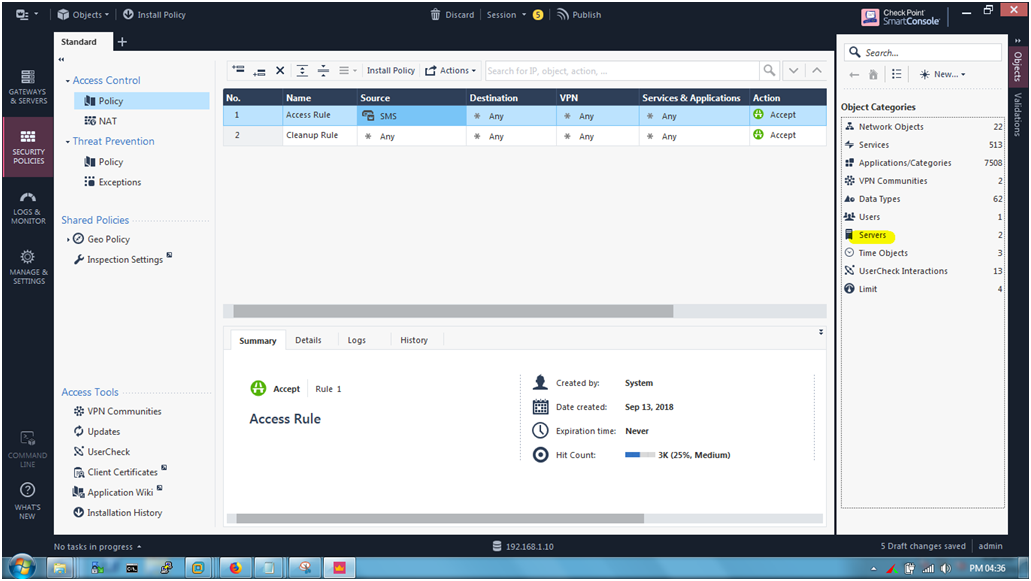
STEP 23: Click the LDAP Account Units.
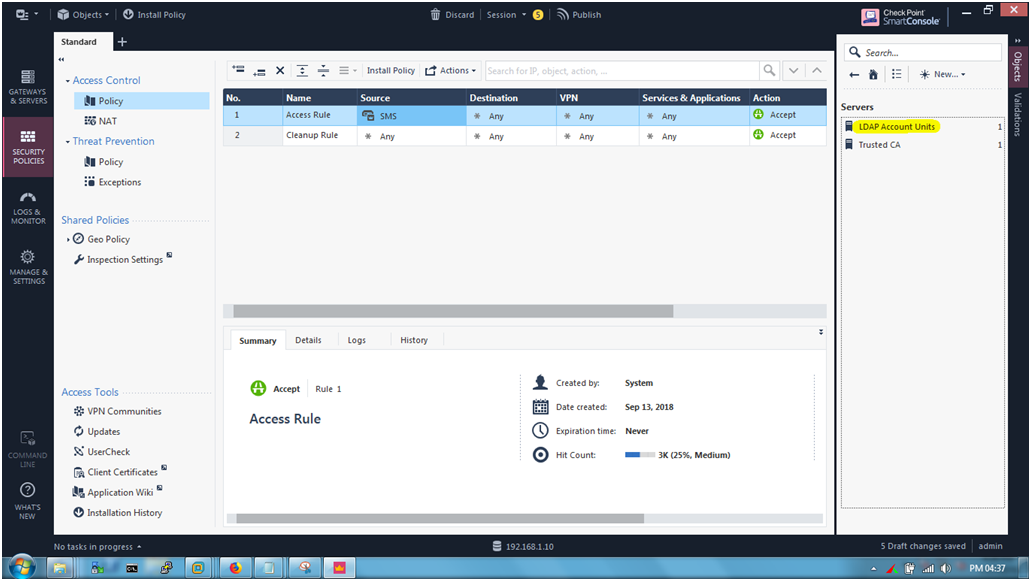
Showing Account Units.
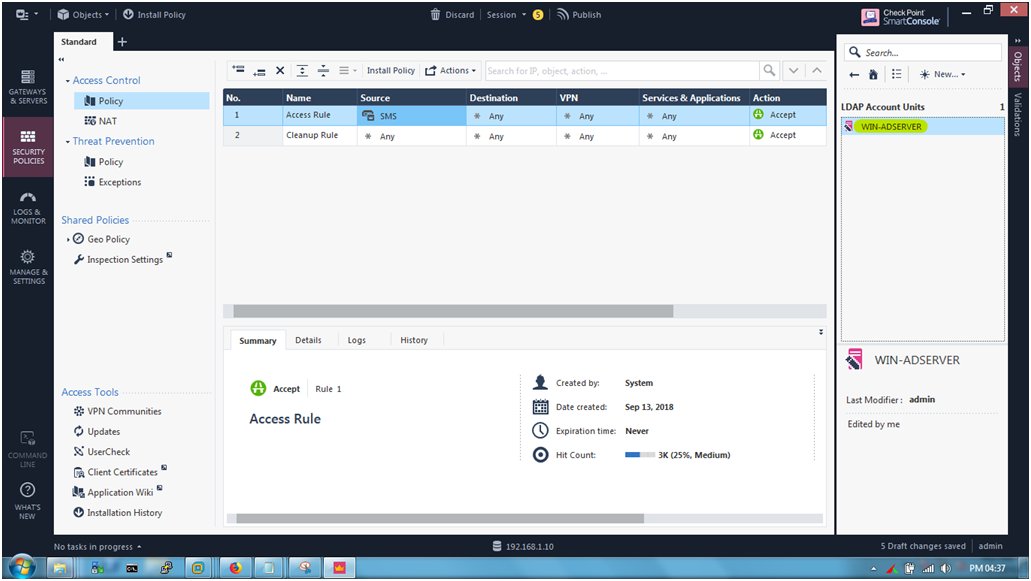
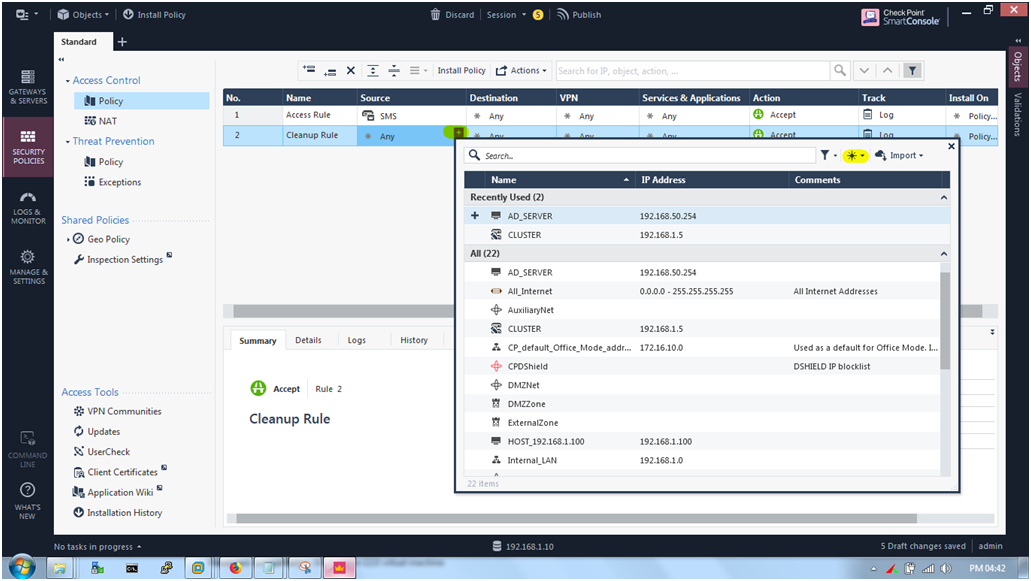
STEP 24: We are going to create Access Role.
Go to Source Section and click —> “+” icon —> “*” icon —> Access Role.

STEP 25: After clicking “Access Role” Assign a name as “Test”. Then Go to “Specific users/groups” (For selecting particular user).
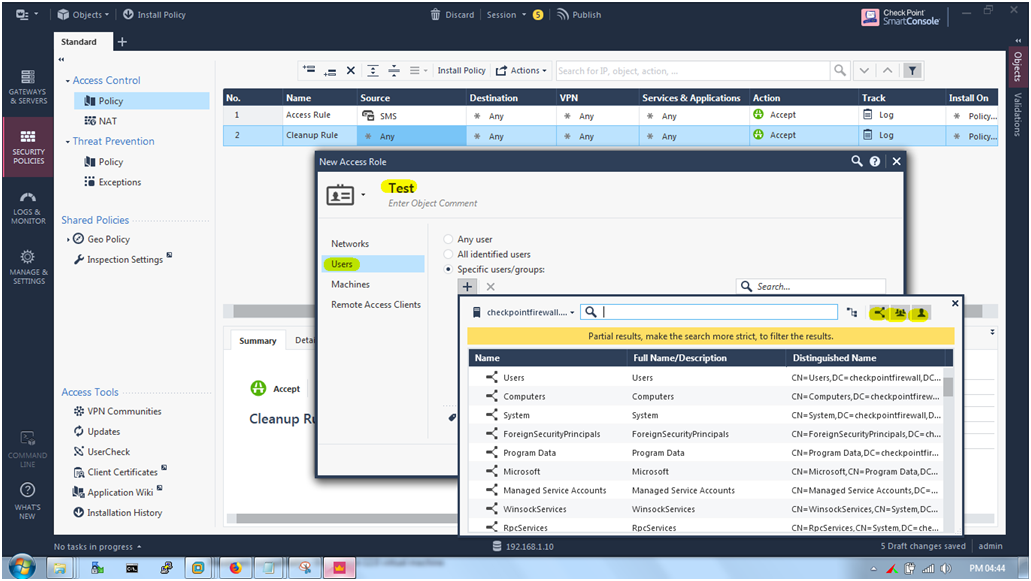
STEP 26: Select the User icon to see all user that we already created on Ad Server .
I am select the users “Chinmaya Naik”.

Selecting “Chinmaya Naik”.

STEP 27: Name “Chinmaya Naik” is selected now click “OK”.

After Click “OK” we able to see the access role name as “Test” is added on the Source.
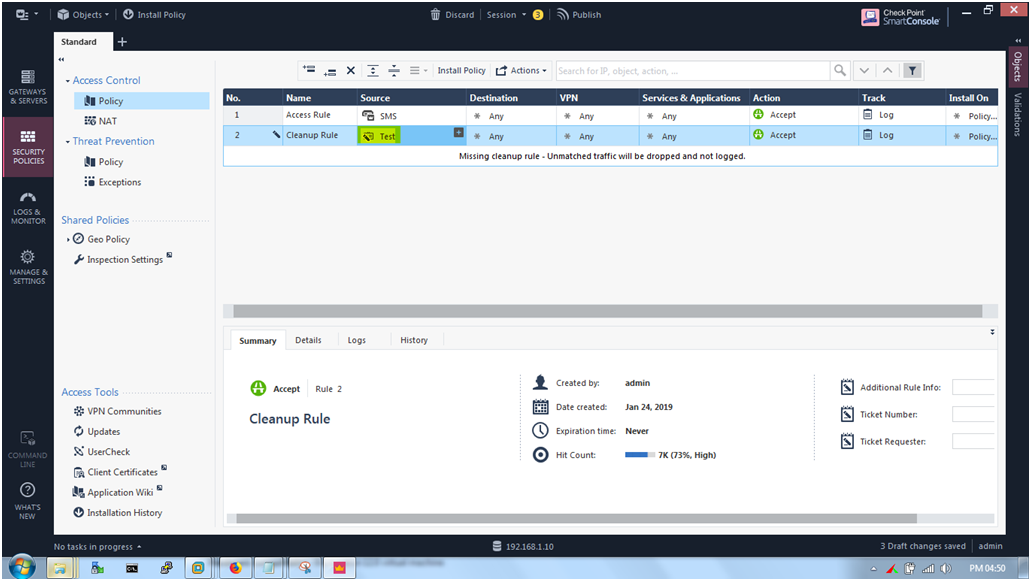
Now Finally we integrate the AD Server in to the Check Point






Leave a Reply